Netz: Scan the internet while drinking coffee
Netz lets you run internet-wide misconfigurations research easily and continuously. It supports infrastructure-as-code so you can put your plan in a config file, run the CLI,
The coming of the internet was a beautiful thing, bringing about accessibility to reach everyone across the globe. But this reach is a double-edged sword. If everyone is just a click away, so are bad actors who can reach back to attack the organization at its weakest spot, trying to access information that it strives very hard to protect.
Enter security hardening: the process of ensuring that the organization’s vulnerable spots are secured from attackers, be they across the world or inside the building. In this article, we give you a handy checklist that you, as a developer, can use to harden your application’s security posture.
The task ahead can be daunting if you consider security hardening an all-encompassing term. It can be applied to multiple aspects and areas of your environment: system or OS hardening, network hardening, device hardening, web application hardening, database hardening, and CI/CD pipeline hardening are just a few examples.
In this blog, we’ll provide a generic checklist that can be applied to most computing systems to help you secure your environment. This is by no means an all-inclusive list, but these items are essential for assessing how secure your environment is and how you can further harden it to prevent security breaches.
Every organization today uses source code repositories, cloud servers, distributed databases, and a software supply chain to get its technology products into the hands of users. The more the organization spreads its resources out, the wider its attack surface, and the more it is prone to vulnerabilities. These vulnerabilities can be spread across different parts of an organization’s technology stack and at multiple levels–from application to storage, networking, infrastructure, and everything in between. That’s why protecting every part of the system is essential.

Recent reports claim that about 20,175 new vulnerabilities were found in 2021, up from 18,341 in the previous year. Clearly, attackers are busy exploiting every possible vulnerability out there, and they are seeing more success than ever before. Here are some ways vulnerabilities in an organization can attract attackers:
Security hardening is the process of eliminating attack vectors by reducing the potential pathways bad actors have to break through into an organization’s systems. The wider the attack surface, the more the possibility of a break-in. Hardening of security helps to prevent these break-ins by strengthening and securing vulnerable spots.
Let’s look at some ways security hardening can be implemented:
But who is responsible for security hardening? Everyone is, in a way, responsible for ensuring they do their part in securing an organization’s systems–at least the ones they interact with daily. However, humans are not perfect, and the alternative is for developers and Ops teams to build smart defaults that protect the system from oversight by insiders. Hence how, as a developer, you play a key role in security hardening. But it is important to know how security hardening can be done in the real world. That’s why we’ve compiled a handy checklist for you.
Since security hardening is an essential aspect of protecting the organization from attacks and loss of information, this checklist aims to help you ensure that you have seen, fixed, and done what you can to help.
About 5,000 secrets are leaked every day as developers push to online repositories. These secrets are API keys, credentials, or access logins that are used to enter into an organization’s systems. One of the ways that these secrets are leaked is when developers leave secrets hardcoded in the source code they manage. Source code in online repositories is prone to attacks by bots that scour the internet to find them. A lot of developers use hardcoding of secrets mostly to save time, but in the end, it costs them a lot in terms of security. It is critical to ensure these secrets are hardcoded in the source code.

One method that is effective at keeping secrets hidden is by using vaults. SpectralOps provides such a vault that helps protect secrets by keeping them in a single place and encrypting them to control how they are accessed. We continuously map developer mistakes, access detail, and secret management detection with an ever-growing coverage using AI/ML and our proprietary tech. Check out an example here.
Another way for vulnerabilities to occur is when there are parts of a system that are not updated. Every day, new vulnerabilities allow hackers to penetrate previously secure places. Keeping every part of your system updated is a way to protect against such infiltration.
The parts of a system that need regular updates are operating systems, browsers, firmware, libraries, open-source tools, and vendor tools being used across the system. Automatic updates are becoming the norm as manual updates are often forgotten or postponed. Modern systems like Kubernetes are increasingly being updated automatically. This is a great way to bake-in security by default.
Updating a system involves checking what new vulnerabilities are cropping up regularly and protecting against these specific vulnerabilities. Vulnerabilities are also dynamic. What is not considered a vulnerability today would not always remain secure. Thus updating vulnerabilities also helps prevent them by acting fast before a system gets infiltrated. It is always good to be a few steps ahead of the game regarding security. Proactively updating and securing your system regularly is table stakes in today’s dangerous cyber world.
There is a lot of data that keeps moving across the cloud, devices, and internal systems of an organization. Data moves from the organization’s databases to a user and back, it moves from one process to another, and it also moves when called on by a developer. These are just a few ways in which data is utilized–it plays a central role in the daily operations of any organization today.
As a developer, you also play a key role: defining how data moves back and forth based on different commands set by the code you write. Open and unsecured data is easily accessible by anyone. Encryption of data helps to protect the data from being stolen. Encryption is essentially like putting a lock on the data, and only those with the key can unlock access to it. This layer of security keeps data from being viewed by prying eyes. And when it can’t be viewed, the chances of it being stolen fall drastically.

When encrypted, data (even if moving) is covered under layers that help it become invisible. Encrypted data is also easy to keep track of through logs. Every time data is requested, a log on where the access request has come from and the time of the request are recorded and stored. These logs are utilized for the examination and prediction of leaks.
Encryption also helps to put a time limit on the life of the data to control how long it can be accessed. A time can be set to the data given access, which helps to retract it when the time limit is exceeded. This ensures that data is accessed only when it is necessary.
As mentioned earlier, controlling access to different parts of the system is essential for security hardening. A great way to do this is to leverage access control tools like Active Directory or AWS IAM. They enable RBAC (role-based access control) to restrict access to specific people based on their role. A more nuanced option is to use ABAC (attributed-based access control) which looks at additional factors such as the IP address, device, team, time of day, and many more.
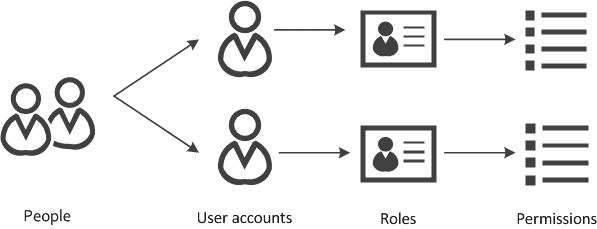
It is possible to design fine-grained access control policies to ensure exactly who can see what data and for how long. The idea is to restrict access to any part of the system to only as much as is required–this is known as the principle of least privilege. It greatly reduces the chances of bad actors taking advantage of a compromised system.
Security and monitoring go together. Real-time monitoring of activity across the system helps to spot attacks at an early stage or even before they occur. In the cat-and-mouse chase between security teams and attackers, monitoring is what gives you the ability to win.
Regular monitoring also helps to reduce redundancies in the organization. Not all resources are utilized, and not all tools are in use. When these resources and tools remain unused for a set amount of time, it is best to stop them until they are needed again. Simplify is the word of the day: aim to remove unnecessary software and redundant OS components, disable unneeded services, and turn off application features that are not needed. A simpler, more compact attack surface is more manageable and easier to monitor.
As developers ourselves, we know that developers are expected to address security challenges and a lot more without compromising on speed and productivity. Because Spectral was created by developers and for developers, our focus is on enabling you to code at speed while implementing all the security practices discussed in this blog to harden your software systems, keeping it safe from internal and external vulnerabilities. Learn how we can help you stay a step ahead.

Netz lets you run internet-wide misconfigurations research easily and continuously. It supports infrastructure-as-code so you can put your plan in a config file, run the CLI,

It seems like there’s a data breach disclosed every day. They come in a variety of forms and from all possible industries and verticals. However, some

Did you know that 65% of organizations believe they have to choose between innovation and security? This stems from the idea that developers need full access