Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Did you know that human error is by far the leading cause in data breaches? Up to 95% of all data breaches are caused by misconfiguration, secret leakage, and bad digital hygiene. Hackers don’t often find their way into systems by brute-forcing weak systems or finding software exploits. The vast majority of access malevolent entities gain is enabled by simply knowing where to look to find your secrets and errors.
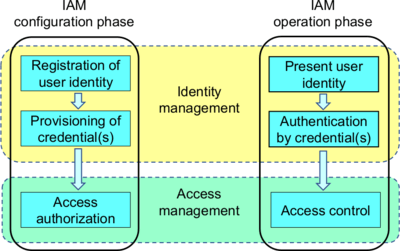
How do you prevent this from happening to you? Among others, by understanding Identity and Access Management (IAM) and how you can make it work for you.
Identity and Access Management is at the core of cybersecurity. You cannot have cybersecurity without authentication and authorization, as the people that need access must be granted that access. Managing who has access to what is at the core of every connected security system.
If Identity and Access are managed properly, it can prevent incidents like one where an ex-Cisco employee caused an estimated $1.4 million in damage a whole 5 months after he resigned. There is no reason for anyone to have access to your systems after they leave the organization, especially 5 months later.
There are also ways to limit the scope of damage someone can cause, be it through malice or error. If a least privilege access policy was employed at Sage the damage that could be caused by a single rogue employee from accounting would be greatly reduced. But that isn’t sufficient on its own. Even with limited access, users must be continuously monitored, and extra steps need to be taken to mitigate risk.
Our list of best practices is far from exhaustive. But it should give you a strong starting point and help shape your IAM strategy.
Indisputably on the top of the list is doing everything you can to prevent credentials and code secrets from leaking. There are tools out there that can detect when credentials are being used by unauthorized personnel. They may detect it by location, habits, actions, and many more. But knowing a breach has occurred after the fact is small comfort.
Ideally, your secrets will not leak, to begin with. Through education, A strong security-focused culture at the workplace can help prevent secret sharing and hardcoding secrets. Tools such as secret vaults help protect API and encryption keys and multi-factor authentication (MFA, which we’ll discuss later on) can help too.
However, no matter how strong the work culture is, or which tools you employ to reduce secret sharing, human error will eventually get the better of anyone. That is where tools such as SpectralOps secret scanner come in. If an error has been made (and it will be made) a secret scanner will catch it before it is exposed. Secrets hide in many places, and it is impossible to scan them all manually. The only way to guard secrets against leaking is with a secret scanner.
By the way, if you prefer open source tools, you can also use Teller to scan for your secrets and connect it to any key vault and run it straight from your command line.
The use of third-party tools can greatly increase the efficiency with which you manage IAM, but it doesn’t come without potential pitfalls. It is important to have a multi-cloud solution to not drown in notifications from various sources, and it keeps your IAM tools and platforms decoupled.
It is also imperative to make sure those third-party tools are, themselves, secure. Open-source security tools have their place, but they too have their potential pitfalls.
Single Sign-On might not be the first tool you reach for when thinking about security, but when it comes to IAM it is essential. SSO makes monitoring users far easier, with a centralized authorization service granting access to all your resources and platforms.
SSO also increases security. If a user only needs to remember one password they are far less likely to squiggle them on sticky notes attached to computer monitors. Make it easier for your personnel to maintain security and they will make it easier for you.
Multi-Factor Authentication (MFA) is an additional layer of protection that stops a leaked password from granting access, but it also helps enforce secret privacy. An employee is less likely to share their password if they need to authenticate using an additional device like their phone. This not only helps ensure access control but also identity management. You can know with a much higher rate of confidence who the user is. This leads us nicely into:
When a breach does occur, the less access is granted to the credentials used, the less damage can be done. By limiting access to those who strictly need it, you’re helping manage the scope of potential breaches. Nobody needs access to everything and your IAM policies should reflect that.
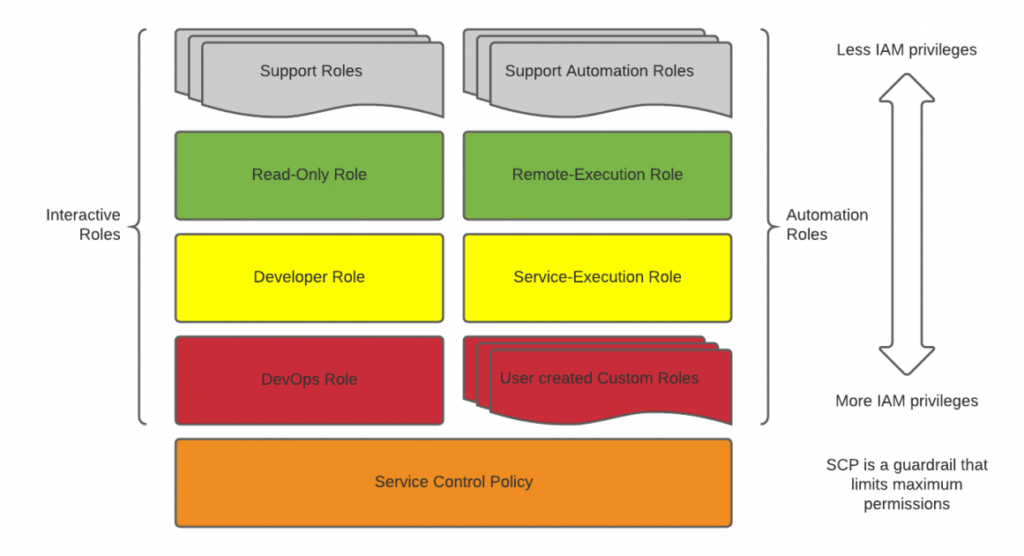
This doesn’t apply only to non-technical personnel. Developers tend to be granted complete access with the thought that unrestricted access will increase the opportunity for creativity. This is not the case. Restricting access to those who need it can even bolster collaboration, and help ensure a cohesive product. When a developer has an idea for an improvement on an area they don’t have access to, they will have to approach the knowledgeable people in that area. An overall excellent result.
There are many benefits to monitoring user activity. Monitoring can help make sense of which resources are used and to what extent. Moving licenses from those that don’t use them to those that need them can help save on operational expenses. When it comes to cloud security, identifying which access privileges get used can help with enforcing least privilege access control policies. If someone isn’t using a resource, they don’t need access to it.
Be sure to monitor continuously as the needs of your users change throughout the SDLC. Update access privileges as needed. Even if someone requires access at a certain point of the SDLC it doesn’t mean they always need access. Limit where it doesn’t reduce productivity and you’ll gain security and free up resources.
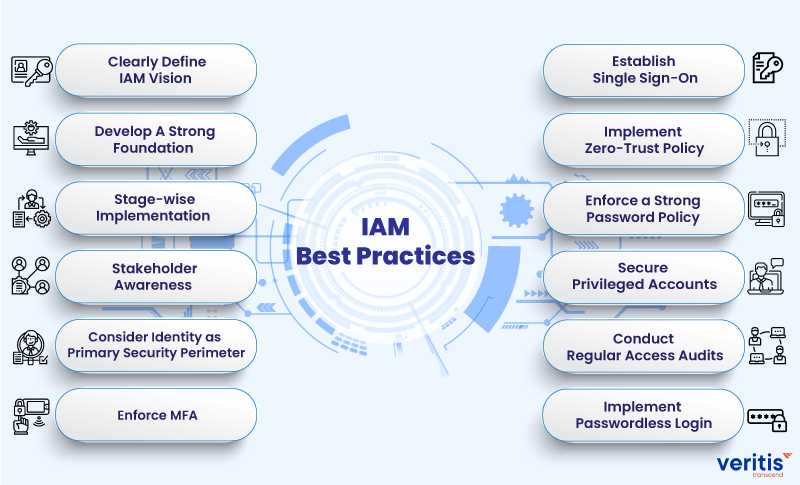
Start by making sure users get access to what they need and only what they need. Preventing unnecessary access credentials is key to mitigating data loss in case of a breach.
Enable MFA and SSO to ensure access is strictly tied to identity. Without knowing who has access to what you can’t enforce security.
Continuously monitor usage to gain knowledge of how your users behave and what they are using. Knowledge is power. To make the right decisions you need to know. Don’t guess.
In addition, make sure secrets don’t leak by choosing the best secret scanner for your needs. You should be prepared to mitigate human error. Simply because human error is the largest player in access breaches across potential attack vectors.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions