Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Updated 03.2024
The flip side of ubiquitous digital transformation and increased reliance on remote work due to the pandemic is that malicious actors get more opportunities to strike. Security perimeters are no longer distinct, and the range of potentially vulnerable enterprise assets is dynamically swelling.
As a result, companies big and small are sailing into the perfect storm of cybercrime. Ransomware raids, data breaches, supply chain attacks, and phishing scams have skyrocketed over the past two years and aren’t going anywhere anytime soon.
According to security analysts’ recent findings, at least half of all reported cyberattacks on organizations originated from an unknown or crudely managed asset. To emerge unscathed, businesses need to know what components of their digital postures are the most enticing when put through the prism of an attacker’s mindset. Such visibility is key to hardening the sensitive areas.
This is where attack surface management solutions kick in. Both traditional industries and digital-to-the-bone DevOps environments can get a lot of mileage out of such services. That being said, let’s dive into the fundamentals of their operation and the benefits they provide.
An attack surface is the entirety of an organization’s Internet-facing digital assets that may be exploited as entry points in a cyberattack. These entities run the gamut from hardware, applications, software as a service (SaaS) deployments, and cloud resources – to websites, subdomains, IP addresses, social media accounts, and vendors’ infrastructures.
Framing this multitude of assets as an easily discoverable and clear-cut ecosystem is a fallacy. Known assets are only the tip of the iceberg. There tend to be troves of attacker-exposed items that companies are clueless about.
Some of them, such as abandoned microsites and applications, stem from shadow IT and phased-out technologies that are still in use across an organization. Merger and acquisition (M&A) scenarios are catalysts for the emergence of uninventoried subsidiary assets, too.
Furthermore, numerous enterprises now hinge on the remote work model to survive the pandemic-borne crisis and stay competitive. This leads to an increase in hard-to-supervise devices operating beyond the security perimeter.
The booming use of IoT in the workplace and production facilities poses an extra challenge. The likes of Internet-enabled security cameras, motion sensors, smart HVAC controls, and voice-based digital assistants propel various aspects of making business, but many of them are ridiculously easy to compromise.
All these nuances make it difficult to accurately inventory and stay current with the attack surface, even more so in light of the ever-reshaping territory of corporate assets. With the right approach in place, though, it’s not an unfeasible objective.
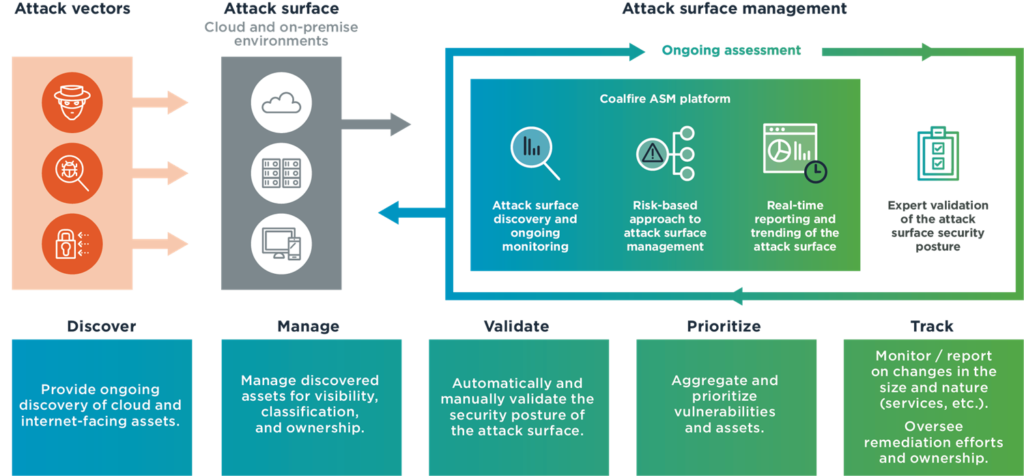
Attack surface management (ASM) is a set of practices aimed at discovering, categorizing, and evaluating the security condition of an organization’s assets. As a general rule, it spans the following four components:
Importantly, ASM is a continuous, systematic process that enables proactive defenses against various forms of exploitation. It provides precious all-embracing visibility of an organization’s assets so that security teams know exactly what to safeguard. These hallmarks make it a critical building block of a holistic security strategy and DevSecOps done right.
The major caveat in terms of asset discovery is that a view from the inside of a corporate security perimeter doesn’t give you a complete picture of what needs to be protected. The only genuinely informative reconnaissance approach is to follow an external adversary’s train of thought. An attack surface management solution worth its salt can bridge the gap.
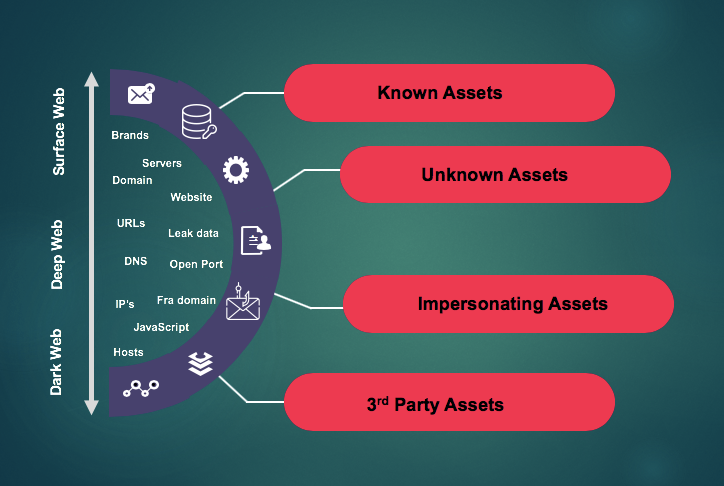
In addition to identifying infrastructure elements that lay in plain sight, the tool automatically pinpoints all the unknowns, including shadow IT, M&A artifacts, IoT devices, cloud footprints, as well as rogue assets like typosquatted domains, malware, and proprietary data leaked on the dark web.
ASM rates the discovered assets according to a relevant risk scoring system to help prioritize the fixes. This assessment also points security teams in the right direction with implementing extra protection-hardening mechanisms, such as network segmentation, role-based access control (RBAC), or the “zero trust” security model.
To maintain the CI/CD pipeline, DevSecOps deployments spawn new IP addresses, servers, and public code repos that sink into oblivion after project completion. ASM helps keep a record of these abandoned assets and alerts distributed development crews to the risk that emanates from them. This is a prerequisite for shifting security as far left as possible in the software engineering workflow.
Most attack surface management tools scour popular code repositories, such as GitHub, GitLab, and BitBucket for long-forgotten data that threat actors might weaponize. They also look for credentials, private keys, and other sensitive information exposed on Amazon S3 buckets as well as publicly accessible FTP and RSync servers.
Besides data exposures on the open and deep web, ASM can reveal documented vulnerabilities and code misconfigurations that may turn applications into low-hanging fruit. This tactic prevents technical debt from accumulating, which poses a hard-to-overestimate benefit in the context of DevSecOps.
There is no such thing as a one-size-fits-all ASM tool. The right solution has to be well suited to your company’s needs while providing all the generic features. Therefore, a crucial element of the decision-making process is to figure out if the following criteria are met:
If the precision of identifying, mapping, and contextualizing your org’s attack surface is front and center, then Randori Recon is your best bet. It is a mature product boasting automatic asset discovery from the attacker’s perspective. The solution prioritizes your digital resources using the innovative Target Temptation system so that you know what to protect first.
Pros:
Cons:
Pricing: Depends on company size.
For many development teams, being able to concentrate entirely on writing code is wishful thinking. Blind spots, configuration slip-ups, exposed credentials, and vulnerable infrastructure components create too much noise to stay on task. With SpectralOps close at hand, IT professionals don’t have to go the extra mile assessing the software development lifecycle (SDLC) for security gaps.
The solution leverages AI to automatically monitor, categorize, and protect assets throughout the CI/CD routine. It identifies exploitable API keys, credentials, tokens, secrets, and misconfigurations in real time; detects supply chain loopholes and proprietary code across multiple public sources; and gives you the freedom to build custom detectors and enforce your own mitigation policies.
The platform is programming language-neutral, supports more than 500 stacks, and boasts a competitive list of integrations with popular dev services, including Azure DevOps, AWS CodeBuild, Jenkins, and CircleCI.
In the event of a data breach attempt, SpectralOps instantly gives your crews a heads-up via Slack, Jira, or another notification service of your choice so that you can forestall the worst-case scenario. By and large, it’s an unrivaled tool to take your DevSecOps to the next level and keep it that way.
Pros:
Cons:
Pricing: Company-specific. A free trial is available.
Although this risk-based ASM tool has only been around since April 2021, it already has a decent track record of unveiling and monitoring companies’ external-facing assets. Backed by Coalfire’s two decades of background in risk management and penetration testing, it combines a complete spectrum of services to find weak links in on-premises and cloud infrastructure segments, classify the detected vulnerabilities in terms of visibility and ownership, prioritize them, and oversee remediation efforts.
What sets Coalfire Attack Surface Management aside from counterparts is that it involves human validation of a customer’s security posture, whereas asset tracking and monitoring are fully automated. Among other things, the solution is a good choice for regulatory compliance.
Pros:
Cons:
Pricing: Depends on the scope of a customer’s infrastructure.
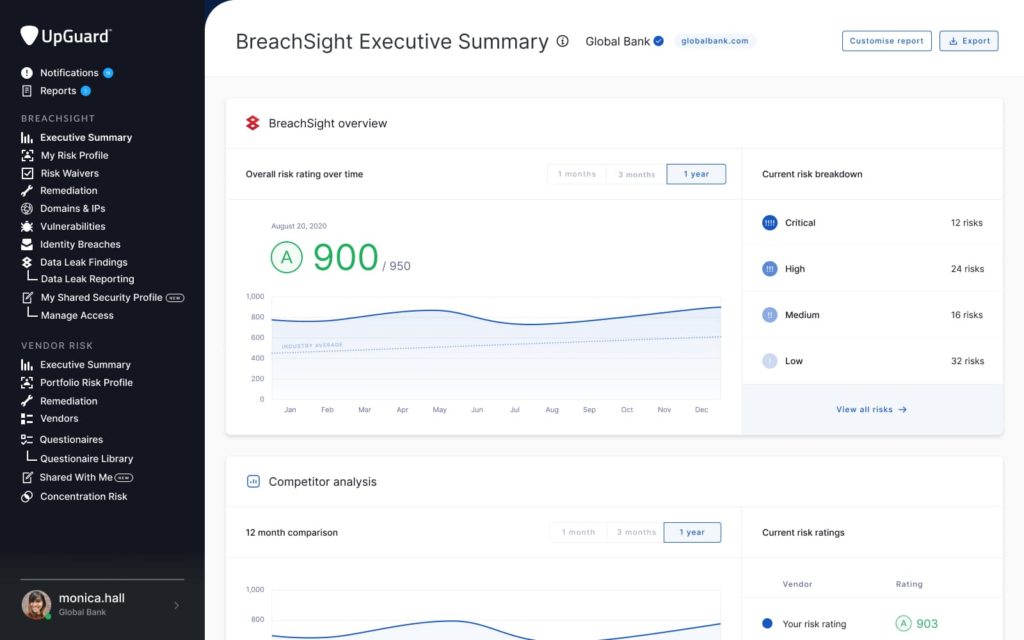
UpGuard stands out from the crowd in several ways. In addition to delivering the classic set of ASM features, it’s equipped with a revolutionary data leak discovery engine that crawls the open and deep web for data surreptitiously exfiltrated from a customer’s ecosystem, including credentials and identity documents. Another perk is the one-of-a-kind risk scoring and security ratings system that uses battle-tested proprietary algorithms to evaluate the state of an org’s digital posture several times a day.
Pros:
Cons:
Pricing: Annual subscription is worth $5,249 (Basic plan for small businesses); $15,749 (Starter plan); $36,749 (Professional); $83,999 (Corporate).
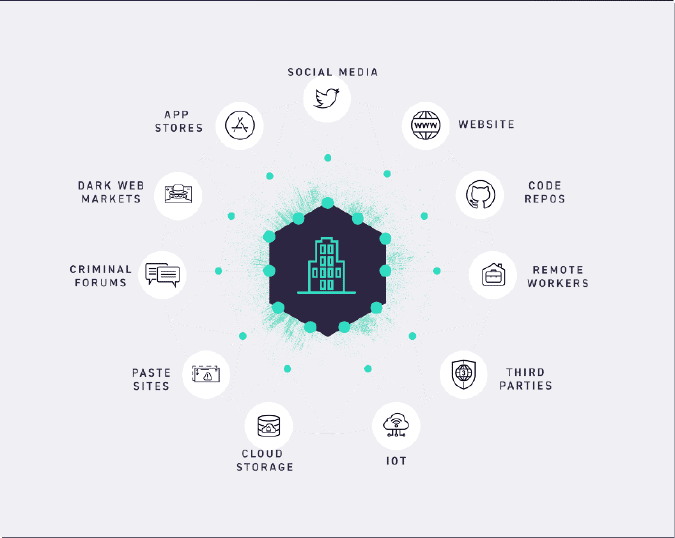
Built around a real attacker’s outside-in perspective, SearchLight efficiently detects data leaks, impersonated domains, exposed sensitive code, vulnerabilities, misconfigured devices, open ports, certificate issues, and other exploitable entities. It is also exceptionally good at dark web monitoring and threat intelligence, including vendor infrastructure screening, exploit monitoring, and malicious actor tracking.
Having identified key assets and risks, the solution works in concert with the company’s security team by providing rich attack surface context and playbooks for taking immediate action.
Pros:
Cons:
Pricing: Scales with your organization. A free trial is available.
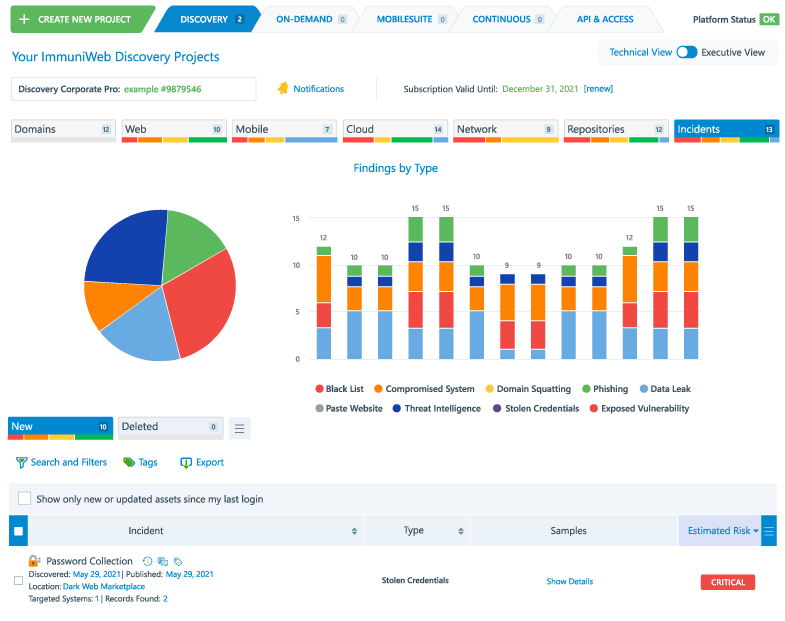
Another heavyweight tool in the ASM arena, ImmuniWeb® Discovery harnesses a fusion of AI and open-source intelligence (OSINT) to zoom into enterprise assets like hackers do. It continuously uncloaks, maps, and categorizes an organization’s digital footprints, including misconfigured IT assets, leaked data, and malware-riddled systems. The solution provides vendor risk scoring to pull the plug on supply chain attacks.
Pros:
Cons:
Pricing: Ranges from $499 (Express Pro plan) to $3,995 (Ultimate subscription) per month.
Although CyCognito is generally dubbed a startup (it’s only been around since 2017), it yields positive security dividends for orgs by accommodating the full ASM cycle within an easy-to-use platform, from automated reconnaissance with an adversarial stance to remediation assistance.
One of the areas where this tool excels is in determining the business context, such as the owners of assets, the criticality of data they store, and the attack vectors they expose. This type of profiling makes risk prioritization more accurate. It’s also noteworthy that CyCognito uses machine learning and natural language processing to uncover third-party assets and those amassed as a result of M&A or joint ventures.
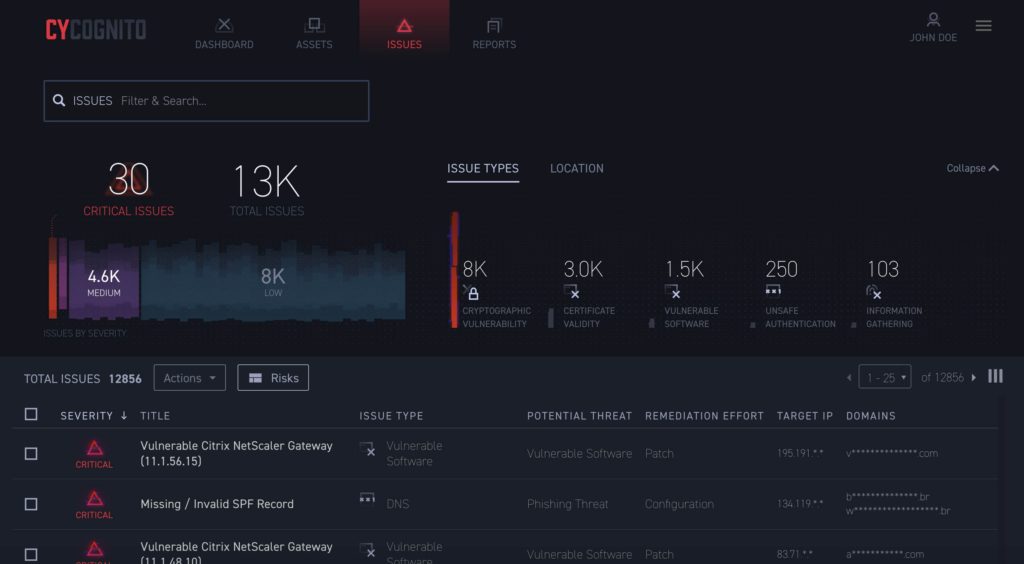
Pros:
Cons:
Pricing: Monthly fee starts at $11 per asset.
Focused on web based attack surfaces that are introduced through third party applications, Reflectiz can quickly detect and visualize web based attack surfaces. Reflectiz also comes with built in privacy compliance, or rather non-compliance detection baked into its attack surface management solution.
Pros:
Cons:
Pricing: Free to start
To be a moving target in today’s rapidly expanding threat landscape, every company needs to know what to protect and how. An effective attack surface management tool can provide all the actionable insights you need. It inventories, classifies, prioritizes, and continuously monitors your external-facing assets so that you can close all the gaps before malicious actors piggyback on them to infiltrate your infrastructure.
Since code security is integrated into the fabric of a tamper-proof SDLC, it’s in your best interest to thoroughly check your development projects for weak links and exploitable misconfigurations. SpectralOps is an ideal fit for that. With this solution’s unparalleled capability to pinpoint vulnerable codebase fragments and public blind spots without noise, your teams don’t have to sacrifice productivity and get the green light to meet important deadlines.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of