Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
You might think that a strong password policy will be enough to protect your code and cloud assets, but it is insufficient. Human error will always trump well-thought-out policies and security culture. Up to 95% of all security breaches can be traced back to human error. How do you fight human error? By understanding Identity and Access Management (IAM), its strengths and weaknesses, and then employing the right tools to handle those weaknesses.
Identity and access management (IAM) is a set of policies, tools, and applications that define and maintain who has access to what digital resources. In DevSecOps, this means access to code repositories, CI/CD pipelines, internal and external wikis, platforms as a service, internal networks, log, and even Slack. Nearly every resource you and your enterprise use must be restricted to the people that need access to them.
IAM aims to ensure that the right set of credentials is used and that the right people are using them. If credentials are stolen or even simply passed around, you can no longer know with certainty who accessed what. Your IAM strategy and implementation should make you confident that only the assigned access people get access. And for that, you need the right tools.
Identity and Access Management (IAM) tools are designed to manage identities (users) and access (authentication and authorization). The goal of IAM tools is to streamline the management of user accounts and privileges from all aspects.
In most cases, an IAM solution will let you define a policy. This policy will, in turn, determine the roles of users. Each role defined will have permissions set. These permissions allow access to specific resources.
Core features of IAM solutions usually include:
Some IAM systems are very complex, like AWS IAM, and require security experts to define and maintain the policies. Other systems are more straightforward and allow any technical person to set up their policies with an accessible interface. It is worth noting that this ease of setup might be a pitfall, as an ill-defined set of policies may cause security breaches.
A good IAM tool will let you instantly revoke access just as easily as it is to grant access. When someone leaves your organization, a quick and easy way to remove their authorization is imperative to the organization’s security and resource allocation.
IT departments rely on cloud service providers to supply usage data, but it is believed that most organizations underuse licenses, which results in waste. Salesforce (40%), Office 365 (38%), and Zoom (29%) are quite a lot of wasted resources that an organization pays for regardless. In addition, 88% of IT executives believe that a centralized tool is necessary to identify weaknesses in their resource allocation.
When talking about waste, even a single unused account can be significant for a small company. Overall, IAM will save money for organizations of all sizes that employ SaaS.
The vast majority of IT professionals feel that sanctioned usage of SaaS applications on their networks is a serious security risk. Yet only half of IT professionals feel confident in their ability to monitor authorized SaaS usage.
Using an IAM tool dramatically increases your ability to correctly and efficiently do your job, reducing offboarding a new developer from a 7-hour average to a few clicks of a button.
If you think that your organization is too small to need an AIM, you are probably wrong. If you do a count of SaaS your organization uses, you’re going to find that you have at least 4. And while that is not nearly the same scope as 100, it still warrants monitoring, proper allocation, and security.
Moreover, as organizations grow and employ more SaaS applications, it makes sense to have a tool to manage it all ahead of the deadline.
As most corporate resources and assets today are in one way or another digital, it’s no wonder there’s such a vast selection of IAM solutions and complimenting tools. Solutions range across verticals and target businesses of varying sizes, with a versatile feature-set to cater to different needs and requirements.
To help narrow down your search for the right IAM solution for your needs, we’ve listed the top 11 industry leaders in the identity and access management category today.
Auth0 is one of the world’s leading cloud authentication services. It provides your developers with an easy out-of-the-box experience in setting up authentication for your web application.
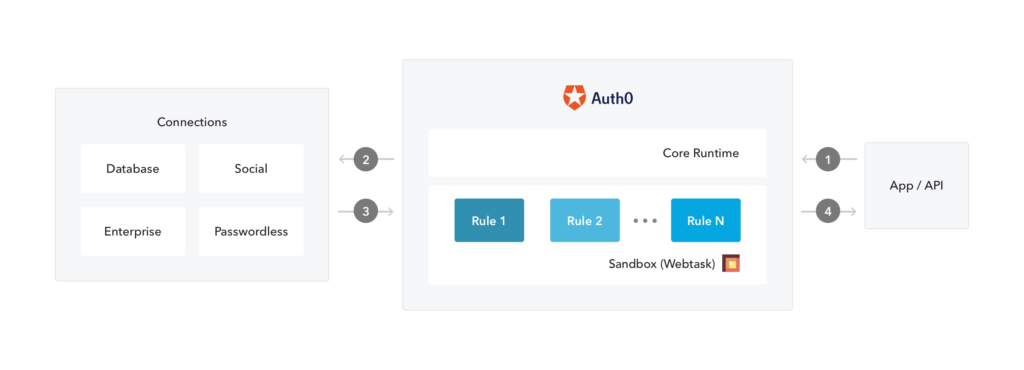
In addition to a super-easy login box setup, Auth0 also offers a feature-rich dashboard for managing users, SSO integration, multi-factor Authentication, additional security measures, and applications.
The solution is free for up to 7000 active users and requires no credit card to sign up. You get started easily by adding authentication to your app with a quick and detailed tutorial accessed from inside the dashboard.
It is worth noting that it is so easy to use that I was able to set it up in less time than it took me to write this paragraph.
While not strictly an IAM solution, we feel that Spectral compliments IAM in a very necessary way. Access can be provided manually or programmatically. Programmatic access is usually given through “Secrets” and “Keys”, which can get mismanaged. No matter how good the security culture is at your workplace, humans make errors. In the case of cybersecurity, even the most minor mistake can leak a seemingly innocuous secret that could eventually escalate to complete access.
This is why employing a secret scanner such as Spectral Ops alongside your IAM tools is essential to protect what we like to call “The Last Mile of Data Management“. Unlike other secret scanners, Spectral Ops uses an AI to reduce the number of false positives significantly when scanning code, properties, and configuration files.
Integrating Spectral Ops secret scanner into your CI/CD pipeline ensures the safety of your secrets. Without this security, even the best IAM policies will fall about eventually.
AWS, Google Cloud, and Azure each have their own integrated IAM services. Those services are intended for use along with their respective cloud computing solutions. As such, each caters to the specific structure of their platform.
When choosing among the three, look at pricing and offering well beyond the scope of IAM. If your organization is already employing a cloud solutions vendor, it is often (but not always!) the right choice to use the IAM offered by that vendor.
AWS is a market leader in all things cloud-related, and they are no slouch in the security and IAM departments either. When choosing AWS, organizations often do so for the peace of mind of using an industry giant.
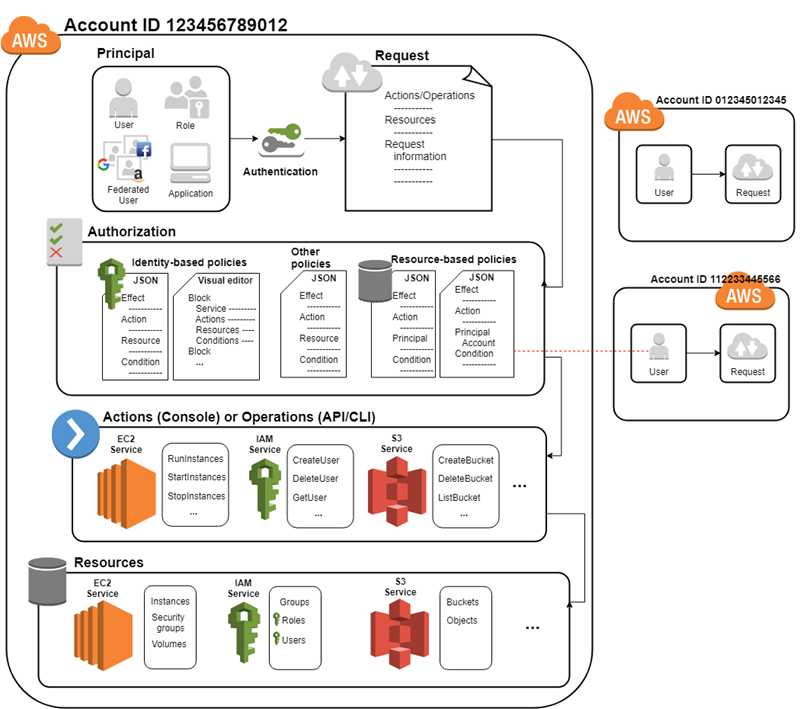
AWS has cloud solutions for all your needs, but doing so comes at the cost of complexity and a steep learning curve. Your security department will need to be well-versed in the world of policy management to make full use of AWS.
If your users already have an identity in your organization’s directory, AWS has you covered. And if you need proof, AWS knows what they are doing? They have this excellent talk about creating policies.
Microsoft’s identity and access management solutions can be a little confusing because the service is named, structured, and priced differently than most other services in the field. If you are coming from another set of security tools, there could be quite a learning curve. Microsoft has its own little ecosystem.
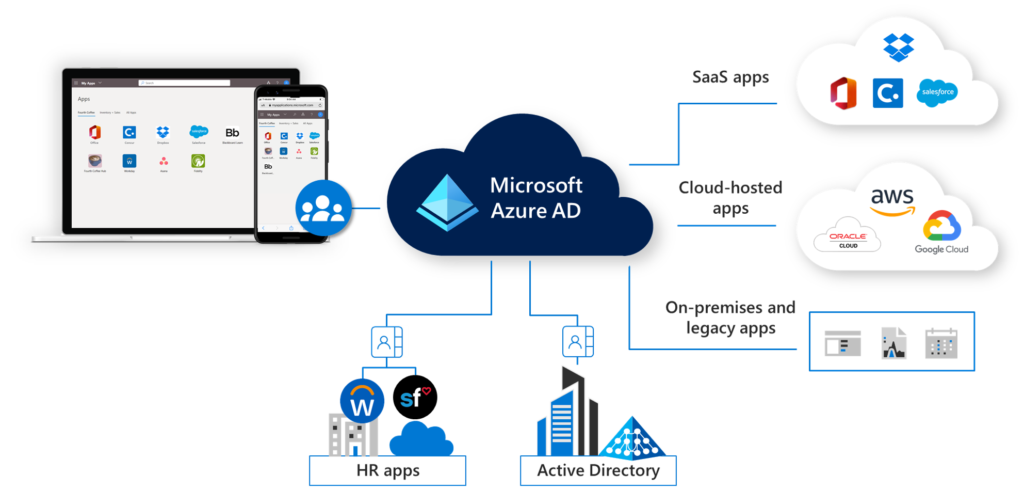
Azure is happy to integrate with On-premise Active Directories or use other SaaS identities. If your users are likely to have something like a GitHub or Office 365 accounts, then using Azure of the same company could be ideal.
Nearly a third of the emails in the world go through a google account. With 1.5 Billion active Gmail users, any organization can feel confident the vast majority of their cloud users have a Google account.
This means that it is fair to pick up Google Cloud as your IAM simply based on those numbers. But what does Google Cloud IAM do differently than Azure and AWS?
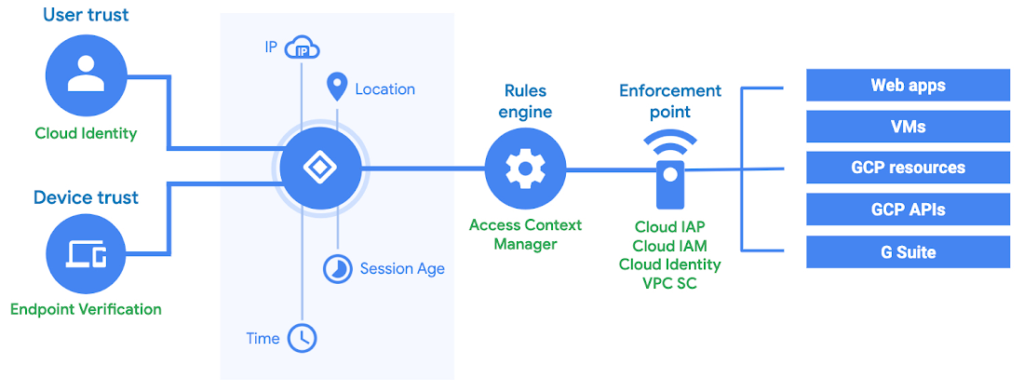
Google is built on top of User Groups and Google accounts. It is not required to have a Google Account for Google Cloud, but it helps streamline things. One strong feature of Google Cloud is role staging, which can be a boon when making changes.
One area in which you might want to make a straight-up comparison between the three giants is the limits and quotas.
You probably know that IBM are innovators in the world of AI, but they do more with it than train chess computers. IBM Security MaaS360® with Watson™ is a groundbreaking AI approach to endpoint security management and is a great addition to an IAM. But that is not all IBM does.
When choosing IBM for your IAM solution, you’re also getting their expertise in large-scale computing projects. IBM has solutions to a large number of potential problems that characterize large complex enterprises. If you know your enterprise has a problem, but you’re uncertain what it is, IBM can help you find and fix it.
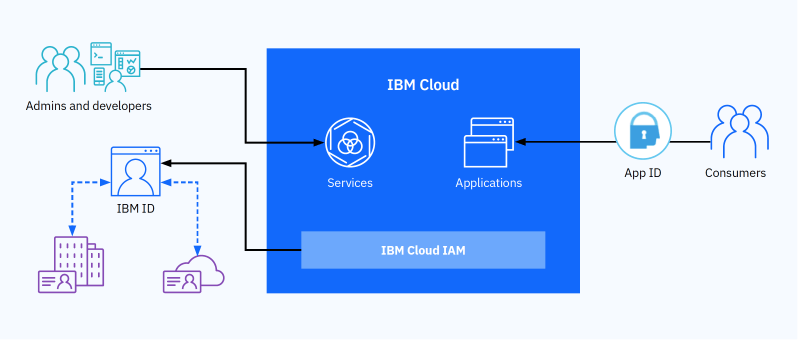
You’ll likely need to contact a sales team to get a quote, but they have this handy pricing calculator that should give you a good idea of what it will cost you.
OneLogin has a system that allows both SSO (Single Sign-On) when using external SaaS and integrates with any applications you may have using an accessible and well-documented API. It can be integrated easily with AWS, SalesForce, and many other platforms and services.

At the forefront of their design is user experience. The idea is to minimize the user’s pain while keeping workflows as easy as possible. One weakness, though, is that auditing and monitoring are not as detailed as some users may like.
This tool is on the more accessible side when it comes to using but may lack some functionality that more comprehensive IAM tools have.
Okta is a development tool for backend user identity and a workforce management solution. It is a flexible system that aims to be a one-stop solution for all IAM needs. Currently, Okta falls short on passwordless solutions, prompting users to change their passwords often. In addition, users also report some technical issues with logins.

You can choose whether you wish to access Okta using an SDK or an API based on your organization’s needs. Worthy of note is Okta’s database of 7100 services it can seamlessly integrate with for faster installation.
While Oracle doesn’t have the cloud presence of Google, Microsoft, and Amazon, it is still a giant in the tech industry. The Oracle system is flexible and is well suited for growing organizations that need to keep adjusting their policies as they grow.
Oracle’s product lineup is split into two main products. The 12c is a more basic product that should serve the needs of organizations with less complex systems. On top of IAM, it is also a Data management tool. The price of flexibility, however, is complexity, and this tool will take some time to learn.
As its name implies, Ping Identity is an identity-first solution employing a combination of MFA (Multi-factor authentication), device identity, and user behavior.
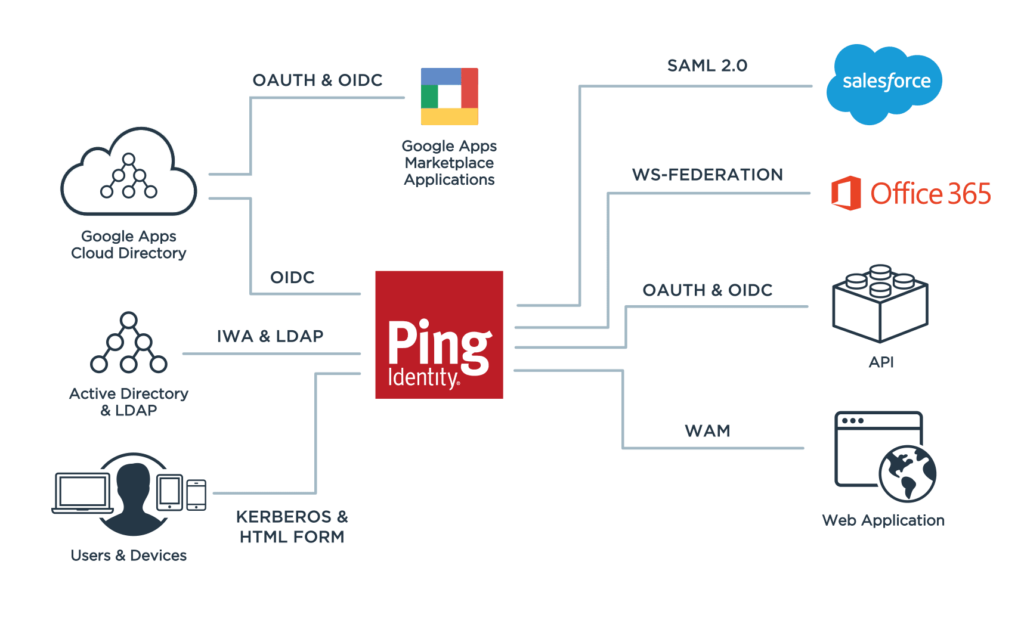
Ping Identity is no slouch in other areas of IAM such as SSO, Data Access Governance, and User Directories. The product is not without complaints, mainly about its high price point and API communications. That said, it seems users are satisfied with the product and would recommend it even with those shortcomings.
SailPoint’s product suite is IdentityIQ, which comprises four core features that combine into a single IAM tool: IdentityIQ, IdentityNow, Security IQ, and Identity AI.
Among the key features of SailPoints is data governance, making Sailpoint a good solution for companies that handle large amounts of data. However, it doesn’t allow for SSO and a steep learning curve.
We decided to include Slauth.io since it is bringing the shift left approach to IaM. Server IaM, that is. Slauth codifies the IaM process and automatically generates IaM policies for services as they become available for deployment.
Picking the right IAM for the job is not an easy task. There are many solutions out there, and most of them share a core set of features.
If you are already using a major cloud platform like Azure, Google Cloud, or AWS, you should probably start by seeing if their solutions meet your needs. If you’re developing an application, something like Auth0 might be the best choice.
Regardless of your choice of IAM, it is crucial to employ a secret scanner such as Spectral Ops. As without it, even the most robust IAM systems may fail due to human error. Any secret leaking means that all your security efforts were for naught, and you might as well not have had them.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Part of the Spectral API Security Series Yelp.com is one of the most influential crowdsourcing sites for businesses. The company is worth just over one billion