7 AWS Security Tools for 2023
AWS (Amazon Web Services) allows businesses to quickly and securely build and scale applications. Hence, there is exponential growth in AWS usage among businesses and organizations.
Part of the Spectral API Security Series
The COVID-19 crisis brought many new buzzwords into our lives. One of the brand names that will forever be associated with the 2020 pandemic is Zoom. A video conferencing service that became one of the main tools used by citizens of the Earth to stay connected over the Internet.
Becoming a household brand name wasn’t enough for Zoom. The next step was becoming an integral part of websites and applications by offering an API and an SDK. For many developers, this offered an opportunity to build products with video streaming or conferencing, as well as plugins for the popular video call service, such as transcription and interactive Zoom game add-ons.
The Zoom API reference is comprehensive. But does the Zoom API do what you need it to do for your app? And if it does, do you need to make a JWT app or an OAuth app? If it doesn’t, will the SDK provide the features you require? Let’s break it all down.
Zoom API was enabled a while ago, but the current design with the app creation workflow was made available on June 9th, 2019. Since then the Zoom API has been updated and maintained frequently. The Zoom API documentation is top-notch, and you would be hard-pressed to find a better-documented API.
The Zoom API is RESTful, which means you access it via URL by sending it your credential token, and possibly some parameters, and getting back the information you requested. REST APIs are stateless, meaning that they do not maintain knowledge of your identity, and do not maintain the current state of your work. Each request is made as if it was your first request.
When approaching the Zoom API, you likely have some idea of what you want to do with it. You might have a scheduling application already in place and want to launch Zoom meetings from within it. Or you might be building a new application that could benefit from Zoom integration. The Zoom API will allow you to access all the basic functions you have available through the Zoom UI via code, or more specifically, HTTP requests.
The full list of API functions is documented well, but to give you a rough idea: You can create, get, list, and update things such as meetings, users, rooms, groups, and many more. If it is an action you would like to do with Zoom, it is likely the API has you covered.
The Zoom API allows your software to interact with the Zoom service. It uses Zoom users, meetings, authentication, everything. Think of it as a shortcut. Instead of having your users manually log in to zoom, open meeting links, etc, you can do it for them.
An SDK is a step up from that. Instead of using the Zoom service, the SDK uses Zoom technology and servers.
If you are creating an application that needs a video connection or screen sharing technology, you can use the SDK to build it. However, this comes with a cost. Since Zoom cannot charge your users for using their servers, they are going to charge you per minute of video.
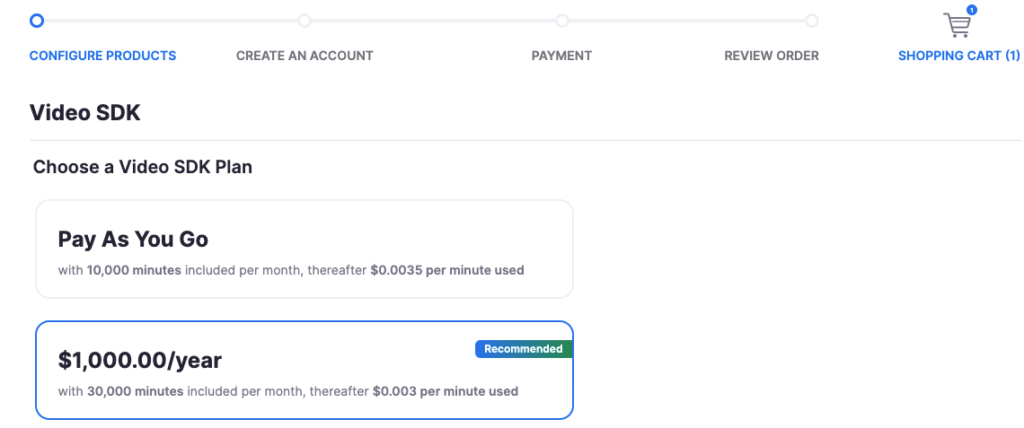
Before starting development make sure that you are using the right interface. Do you need a fully integrated video experience for your users? SDK might be what you are looking for. Are you looking to manage Zoom meetings, users, and accounts? The API will probably do.
While Zoom has become a synonym for online video meetings in 2020, it would be prudent to investigate alternatives. GoToMeeting also has an API, though many of the access points are deprecated, pointing to it still being a work in progress. There is also Jitsi, the leading open source platform. Although in order to read the full API you must shoot them an email. Neither service has as extensive an SDK as Zoom.
There are two methods of token authentication when interfacing with the API: JWT and OAuth.
JWT allows server-to-server authentication. This means that your JWT token will be an authorization granted to the account making the request.
OAuth on the other hand, allows users to authorize your application to use their data. If you are making an application strictly for internal usage, JWT might suffice. However, if you wish to build an app publishable on the Zoom Marketplace OAuth is likely the way to go.
Since OAuth gives you overall access to a larger portion of the API, I will be using OAuth for my examples.
Navigate to the Zoom Marketplace. Your first step would be to sign up.
Once you are signed up, navigate back to the Zoom Marketplace, you will have to sign in here again.
Then click Develop and Build App, or navigate here.
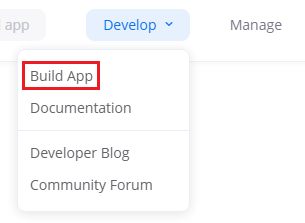
This will bring you to the choose your app type page. Click create on the OAuth app, which will give you a prompt with some options.
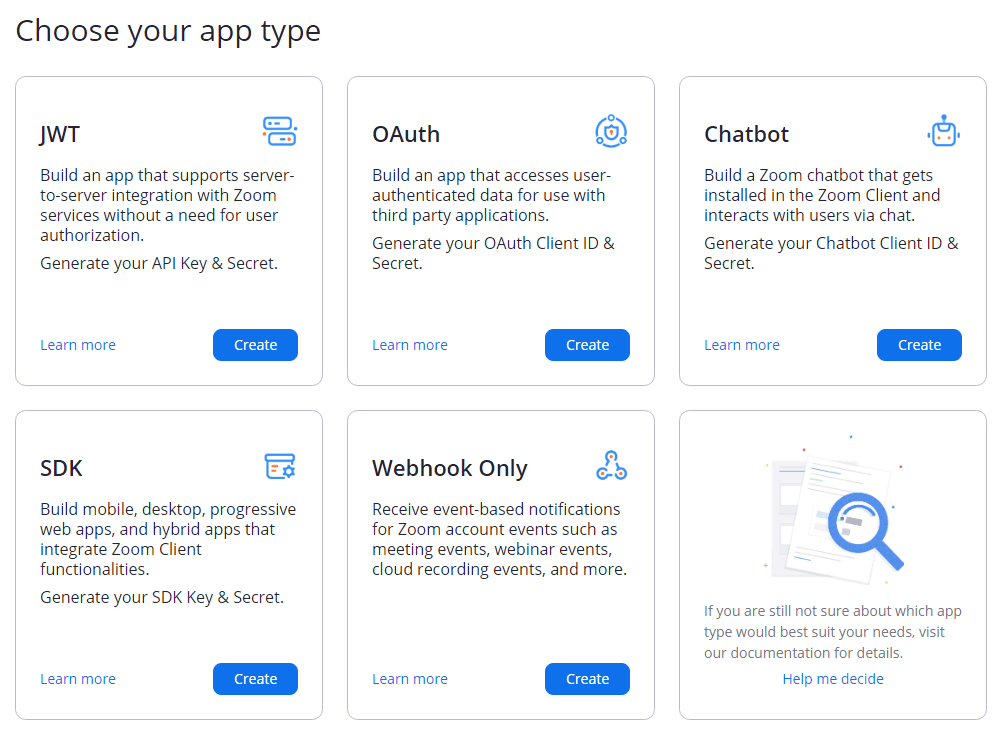
Pick any name for the app. Make sure to use an Account-level app, as it is more comprehensive. Lastly, uncheck the option to publish to the marketplace. Publishing requires more settings to install, and we just want to familiarize ourselves with the API at this point.
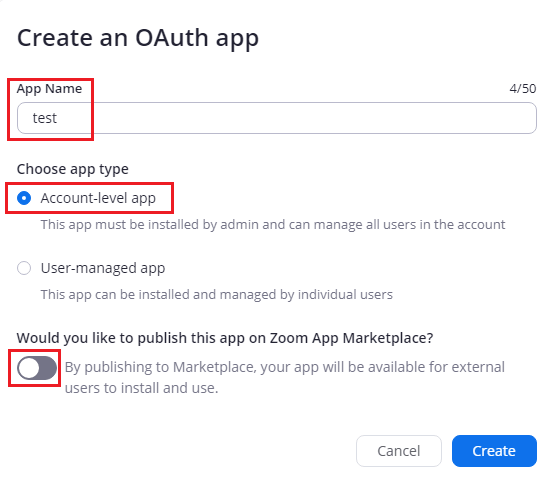
Next, you will get to the App settings. Here you will need to go through several pages to set up and publish your App.
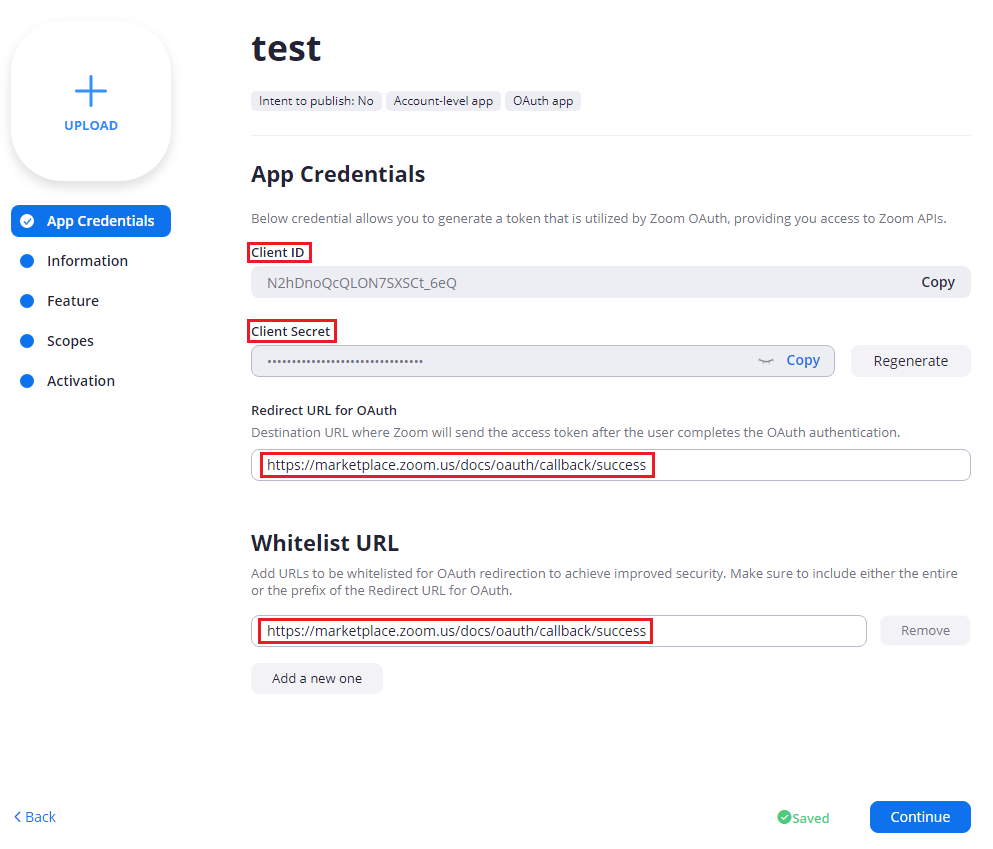
The first page, App Credentials, is where you can find your Client ID and Client Secret. The Client ID is not necessary to keep secret, but the Client secret, as its name suggests, should not be exposed. It is very important to NOT put your secrets in plain text when using a cloud repository.
Also on this page, you will need to put the following address in both the Redirect and Whitelist fields. This is due to how OAuth works. It must redirect somewhere on success.
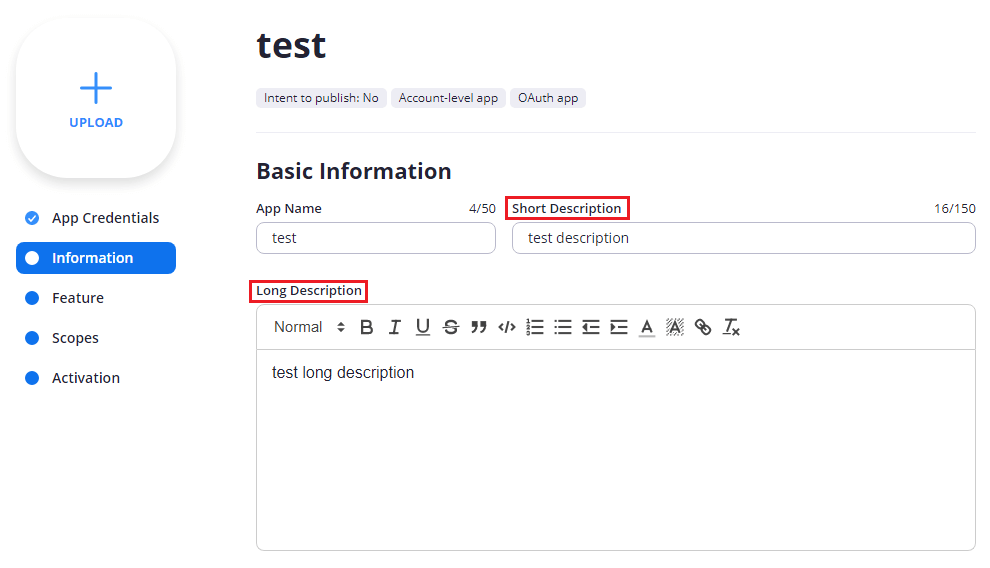
The next page asks for some basic information. Make sure to fill in Short and Long descriptions, and then scroll down and fill out Developer Contact Information Name and Email Address.
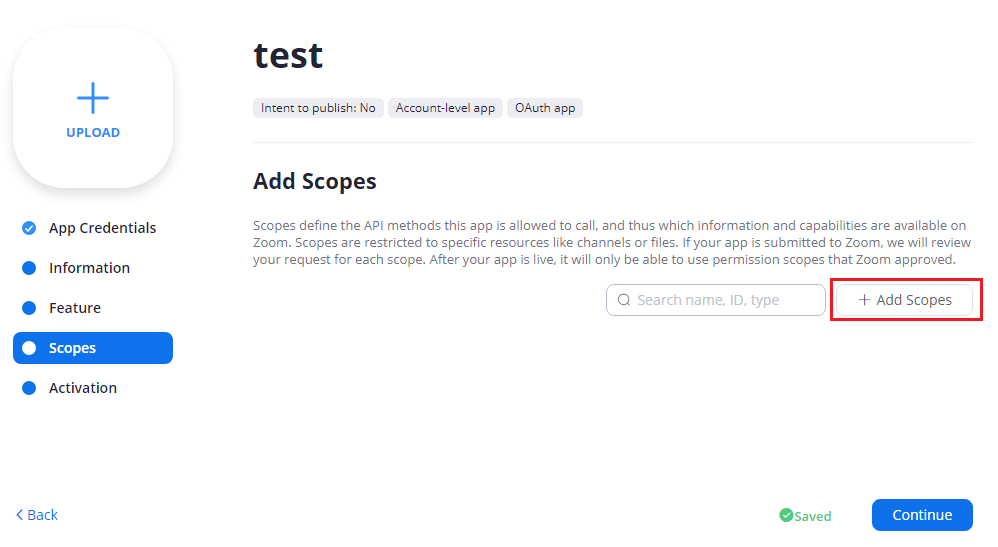
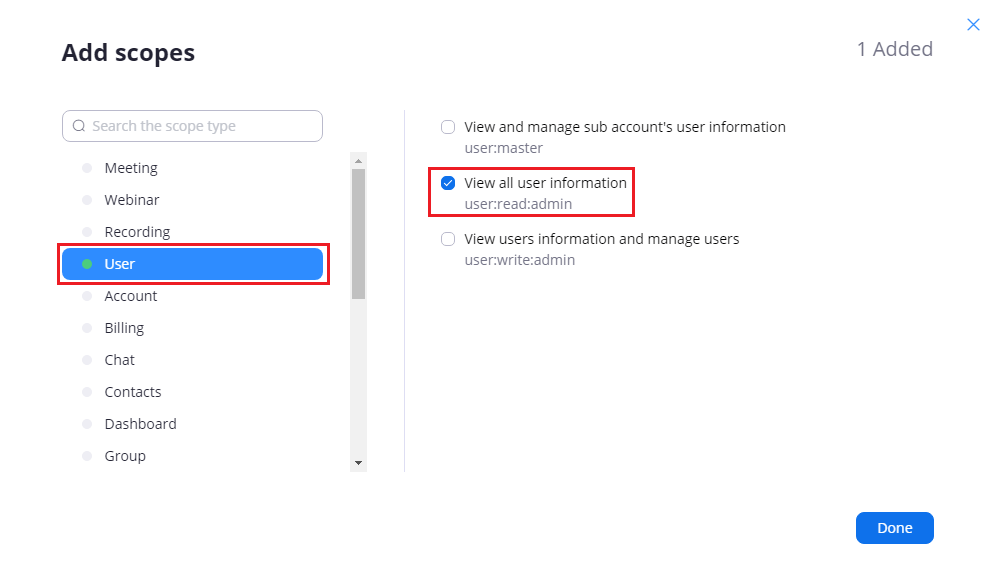
The Feature page can be skipped, and on to the Scopes page. Here you will need to assign which scopes you require for the App. This is the scope for which the App will ask users for permissions. Click Add Scopes. For this test we will need a user:read:admin scope, so go ahead and add that one.
This is everything you need to do in order to install the App, which will allow local testing. But for this tutorial, we will navigate to the API Reference and use their built-in form to run a test.
In the API Reference, under Users, there is a List users page.
At the bottom of the page you will find a form that will allow you to get a user list. First, you’ll need to Get Access Token.
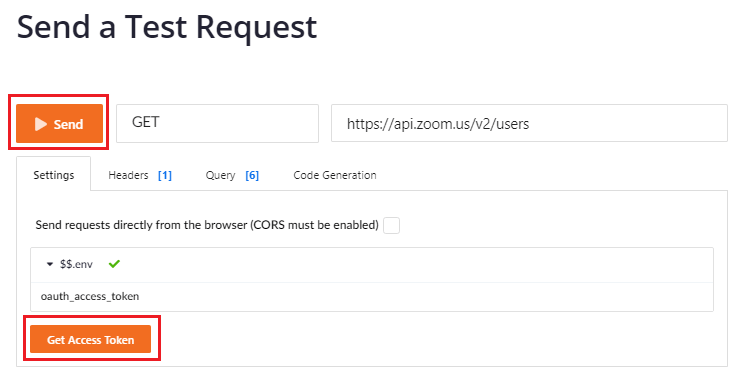
This will prompt you for your Client ID and Client Secret. Copy them from the App Credentials page. If you lost that page, you can find it from the App Marketplace page by clicking manage, or following this link.
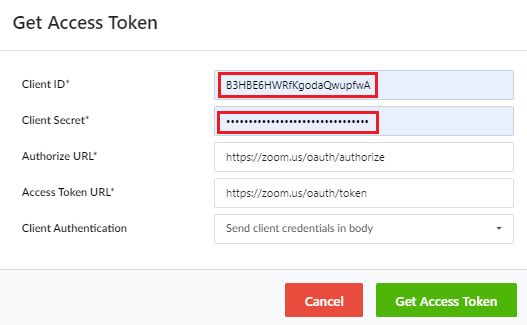
Once you click the Get Access token button, you should be prompted to Authorize the app. Authorize, and then click Send to perform a GET on the address https://api.zoom.us/v2/users. This is filled out automatically in the form, but when running your local test, this is where you will need to send the request.
Once completed, you will get a response with the information you requested. It will look like this, but without the information removed of course.
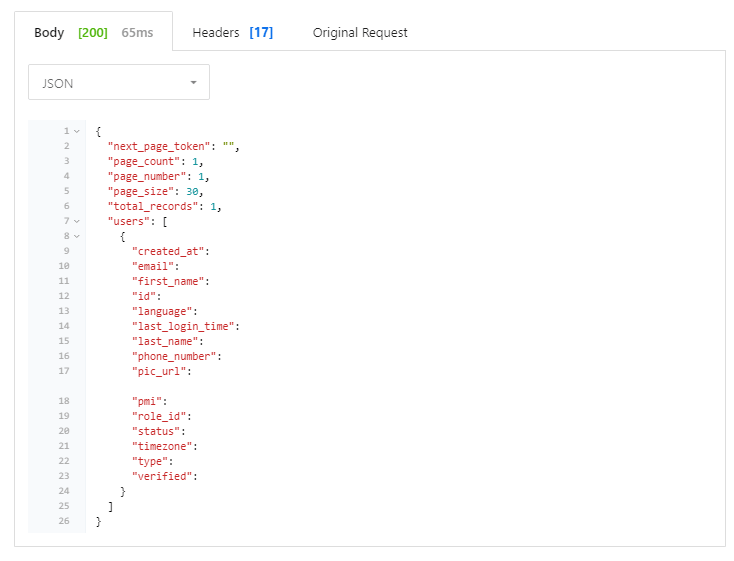
This should have given you a good overview of the Zoom API, how it is used, and whether it is what you need. The API is great for making a connection between an application and the Zoom service. The SDK is a good solution for people needing a more involved solution for their video services.
It’s important to remember to keep your Zoom API keys safe. When writing code that interacts with an API, never leave your tokens in the code in plain text when uploading code into the cloud. It can result in those keys being compromised.
This is especially true for languages such as Java, which can be decompiled, or when storing your code in a public repository. In some cases, even a private repository is not safe enough. Keep your secrets safe and make sure they are encrypted.

AWS (Amazon Web Services) allows businesses to quickly and securely build and scale applications. Hence, there is exponential growth in AWS usage among businesses and organizations.

What if the very core of your company—the digital ecosystem you painstakingly built—is under attack? If an invisible enemy gets illegal access and begins manipulating data

What would happen if a malicious actor managed to access your API without authorization and compromise sensitive user data? The repercussions can be horrendous. You could