Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
On the one hand, your sales department is pushing for new features at an alarming rate, forcing you into faster deployment processes. On the other hand, you have the looming threat of millions of dollars in damages if your security is breached. Software development is all about finding the middle ground – if you can’t compromise on either side, what should you do?
Supply chain attacks increased over 600% in 2022, with insecure code and software tampering taking the top spots as the most common causes. The pressure of velocity can create security blindspots like these in your software supply chain that can only be detected, protected, and fixed by essential CI/CD security tools.
We’ve compiled this comprehensive guide to help you identify the tools you need for an effective security stack without sacrificing your capital. Let’s look at what CI/CD security tools are, the benefits, key features, and the top ten choices.
CI/CD (Continuous Integration/Continuous Deployment) security tools are designed to integrate security checks and validations into the CI/CD pipeline, ensuring that security vulnerabilities are identified and addressed before the code is deployed to production. The primary goal is to shift security left in the development lifecycle, so potential issues are spotted as early as possible. Here are some commonly used security tools that can be integrated into the CI/CD:
Coverity is a SAST solution that scans source code to identify defects that could lead to security vulnerabilities or negatively impact code quality. The analysis runs automatically in the background, providing developers with real-time results without the need to keep checking on it.
By inquiry. Coventry Scan is a free version for open-source projects.
“[It] helps development and security teams address security and quality defects early in the software development life cycle (SDLC).”
Spectral is a developer-first secret detection and static code analysis tool that uses AI to reduce false positives while maintaining a high true positive detection. Spectral provides real-time feedback early in development, enabling shift-left security and data loss prevention.
By inquiry, with a free trial.
“Spectral is a reliable gatekeeper for our secrets. [It] is easy to set up and use, and it provides valuable insights into sensitive issues.”
AppKnox is a mobile application security testing solution that performs SAST, DAST, and API scans. It helps teams develop applications at speed without compromising on security, thanks to the automated scanning features that remove the need for manual intervention.
By inquiry.
“When it comes to the application security testing, the static, dynamic, and API scans are very easy to configure, and the time that takes to complete a testing is quite reasonable compared to other security testing tools.”
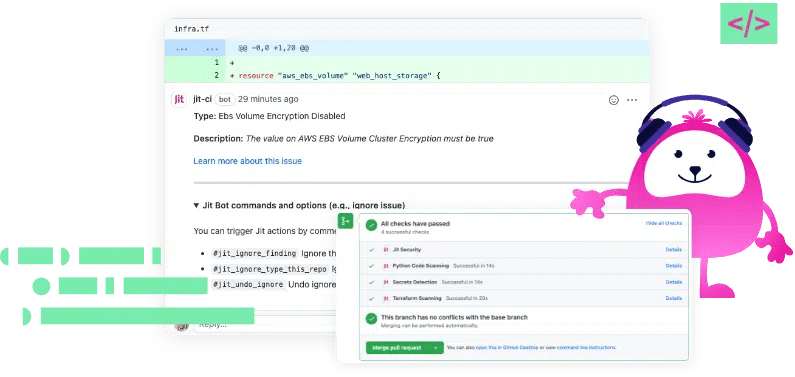
Jit is a DevSecOps orchestration platform that integrates with tried and tested open source security tools like OWASP ZAP and Semgrep. It automates and unifies the execution of all tools to enable a consistent and simple DevSecOps experience.
By inquiry, with a free trial.
“What I really like about Jit is that they bring in the OSS tools I already like and use into a single solution, and help me [use] them much quicker.”
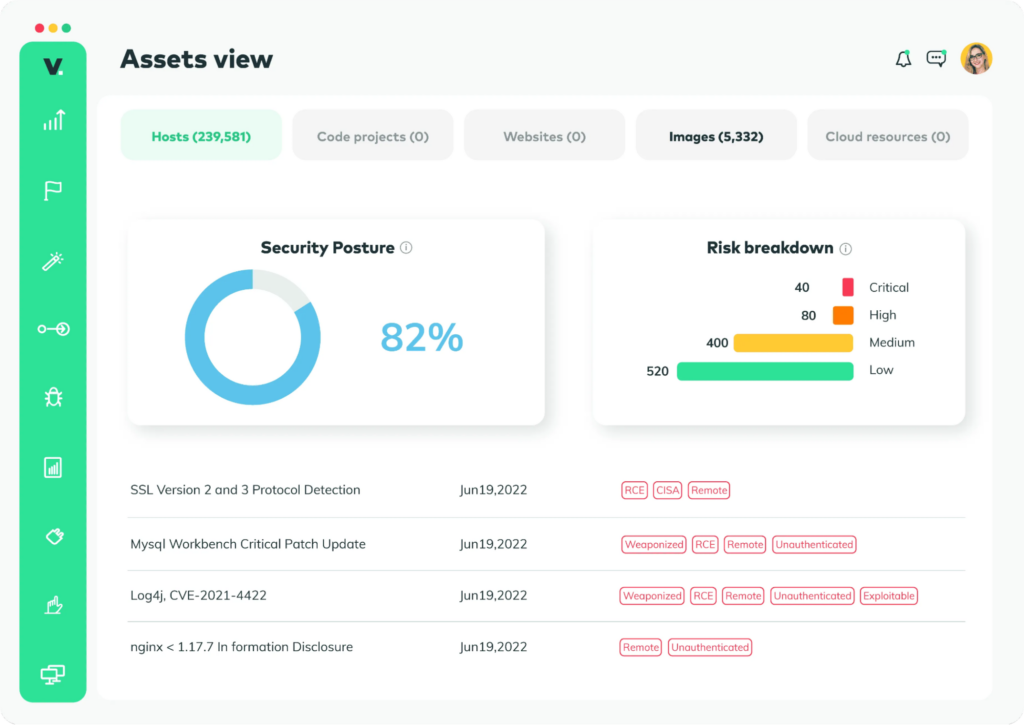
Vulcan Cyber is a vulnerability management platform that drives remediation processes forward via actionable insights and remediation orchestration in real-time. It ensures vulnerabilities are identified and quickly fixed as code moves from development to production.
There’s a Free version, a Standard version at $1700/m billed annually, and a Scaled version by inquiry.
“The support is great, and the whole onboarding process only took a day. […] We connect our various scanners and handle the reporting and escalation within Vulcan.”
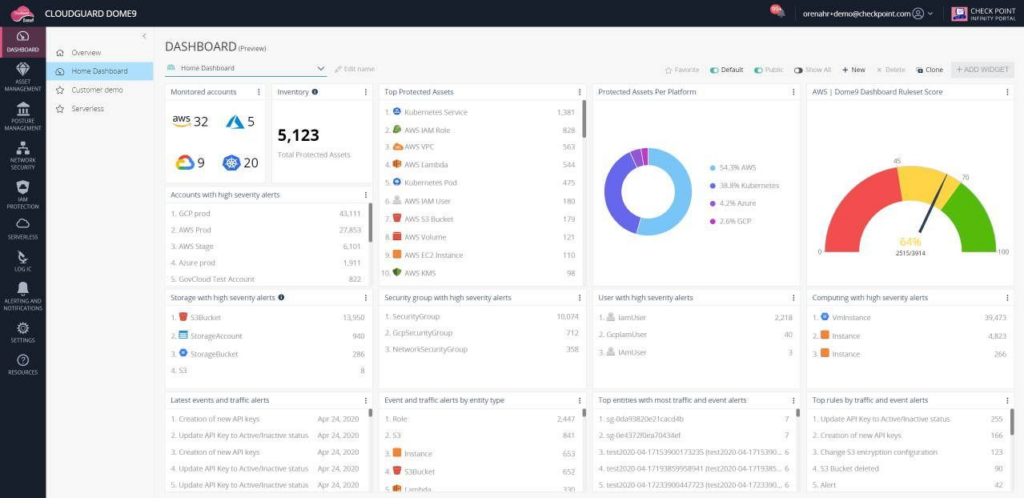
Check Point CloudGuard is a multi-cloud security solution that protects all your assets, workloads, and network. It provides the context and visualization you need over cloud traffic, alerts, and assets via a unified platform and automates remediation at speed and scale.
By inquiry.
“It provides cyberattack intelligence in advance to enhance effective actions before the company data is compromised. The multi-service platform provides powerful security to both on-premise and cloud set databases.”
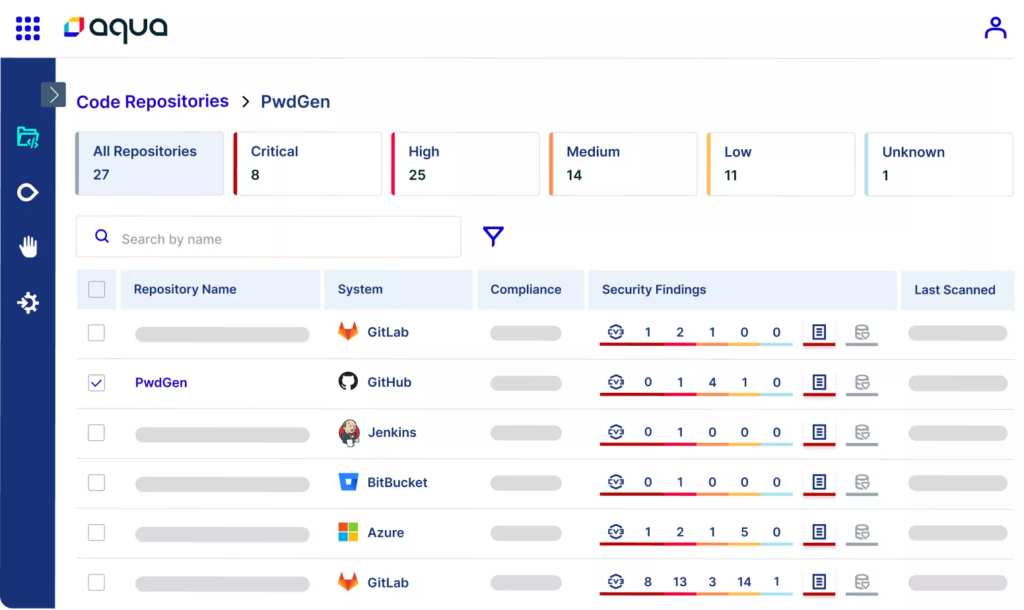
Aqua Security provides a wide range of solutions for container-based applications and an automated secure deployment approach for DevOps. The cloud-native application protection platform (CNAPP) protects the application lifecycle from code to cloud and supports security requirements throughout the CI/CD pipeline.
By inquiry.
“After some growing pains, due to the size of our organization and the number of images we scan, it has been easy to implement Docker image scanning into our build process.”
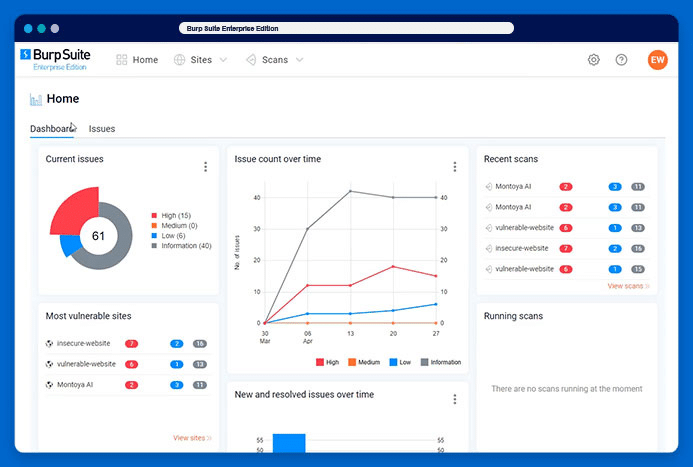
Dastardly is a free DAST web application scanner for your CI/CD pipeline. It acts like a hacker or pentester to find and fix vulnerabilities and bugs in your code. The parent company, Burp Suite, is a web application security testing tool used by over 16,000 organizations,
Free.
“I can easily run an automatic scan to find the common bug in the website, and it provides a detailed report of the scan and gives fewer false positives.”
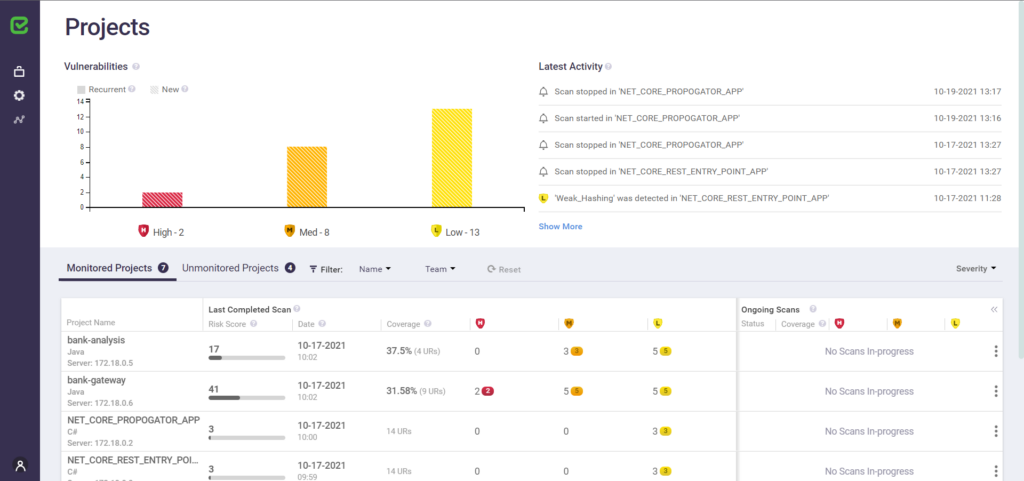
Checkmarx’s cloud-native AppSec platform combines a wide range of application security testing tools to help developers strengthen the security posture of applications. The suite includes SAST, SCA, DAST, and more, and the centralized platform consolidates risk ratings, findings, and guidance into one dashboard.
By inquiry, and you can request a demo first.
“It categorizes the vulnerability based on the risk associated. Can be easily integrated with your CI pipeline to have you code scan with every build.”

SonarQube is a tool that integrates into your CI/CD pipeline to ensure the quality and cleanliness of your code. It automatically reviews code using a continuous inspection approach. SonarQube supports 30+ languages, frameworks, and IaC platforms and has an extensive rules database for each language it supports.
Free trial and pricing is by inquiry.
“SonarQube is an excellent tool for maintaining code quality and enforcing code quality rules organization-wide. It has a free and open-source version which can be self-hosted.”
Security automation is the next step that brings Sec into DevOps. We’ve reviewed the benefits of CI/CD security tools in bolstering your security and reducing manual labor and costs, and highlighted our top picks for CI/CD security.
It’s important to understand that while CI/CD security tools provide valuable insights and catch many issues, they don’t replace the need for manual code reviews, thorough penetration testing, and other security best practices. The idea is to integrate security seamlessly into the DevOps lifecycle, allowing for rapid but secure code releases.
When choosing your security stack, you must include a SAST tool that will cast a wide net. Spectral offers secret detection, source code analysis, and security assessment, all rolled into one. Try Spectral for free today.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions