Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
With the increasing threats of cyber attacks, safeguarding sensitive data and digital assets has become one of the key considerations of modern organizations. According to The State of Security 2023 report, cyber attacks happen every 39 seconds, and a critical security issue can cause a median of 14 hours of downtime.
As a result, organizations are turning to security automation tools to effectively mitigate software risks and respond to security incidents promptly. These tools can help businesses improve their applications’ overall security by automating repetitive security tasks, accelerating incident response times, and enhancing overall operational efficiency.
In this article, we will discuss the benefits, features, and types of security tools, plus we’ll review the top ten security automation tools used in the industry.
Security automation tools use AI, ML, and RPA to automate security processes, streamline workflows, and improve incident response in cybersecurity operations. They handle tasks such as log analysis, threat detection, and vulnerability scanning, freeing up security teams to focus on critical activities. These tools enhance efficiency and help organizations safeguard sensitive data and digital assets in today’s evolving threat landscape by reducing supply chain risks, eliminating manual work, and accelerating threat response.
Security automation tools are essential components of cybersecurity operations that automate and optimize incident response, threat intelligence analysis, and SOC tasks, enabling organizations to enhance their overall security effectiveness and efficiency.
Here are a few different types of tools your organization might need:

Security automation tools offer numerous advantages for organizations seeking to enhance their cybersecurity practices. Some of them are:
Automating security orchestration is crucial as it allows security teams to reduce the need for routine manual tasks, streamline incident response workflows, and integrate threat intelligence effectively.
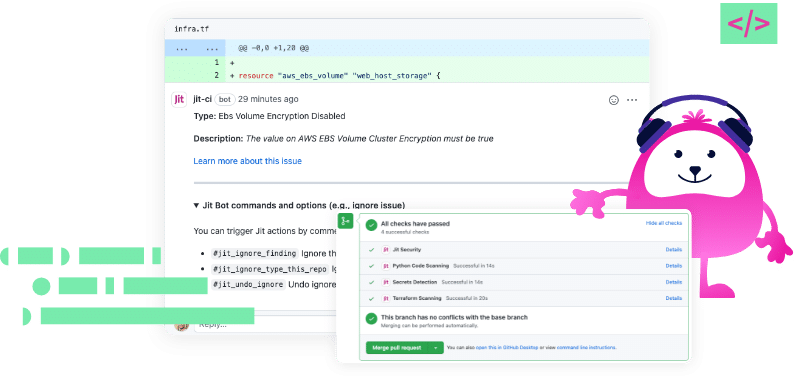
Jit is a continuous security platform that provides security-plan-as-code (SaC) for your DevOps pipeline. It acts as an orchestration layer that makes installing, viewing, and managing all open source security tools for your software easier. With this orchestration layer, you can cover your application’s major security areas, including code, pipeline, infrastructure, and runtime app security.
Main Features:
Best for: Jit automates selecting, implementing, configuring, and managing the Application Security toolchain.
Pricing: You can get started for free and need to contact customer support for custom pricing options.
You can use Sluth to automation IaM Policy creation and allow granular permission to your resources for both human and programmatic access levels.
Main Features:
Best for: Automating granular permissions for the entire development stack.
Pricing: There’s a free 30 day trial, then pricing is by inquiry.
When you automate identity and access management (IAM), you can efficiently manage user identities, control access to critical resources, and ensure compliance with security policies.

Memcyco provides a Proof of Source Authenticity (PoSA) suit to ensure the authenticity of digital assets. It safeguards companies against impostor attacks like brand identity theft and phishing scams by providing an authentication watermark on company websites or emails, contributing to establishing customer trust.
Main features:
Best for: Protection against brandjacking frauds.
Pricing: By inquiry.
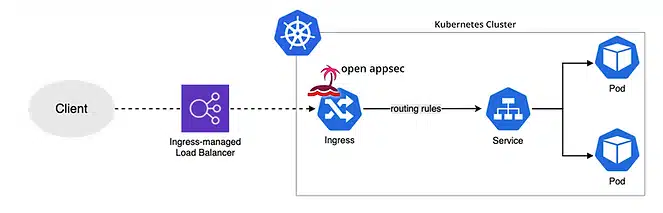
Open appsec is a classic vulnerability management solution. However, its continuous analysis of HTTP/S requests to websites or APIs makes it crucial for detecting threats, attacks, and vulnerabilities in your security perimeter.
Main features:
Best for: compliance minded companies looking to ensure they are protected for OWASP top 10.
Section 03: Static Application Security Testing
SAST is a security testing technique that helps identify vulnerabilities and weaknesses in software applications before deployment. By analyzing the application’s source code, SAST tools can detect security flaws and provide developers with actionable insights to mitigate risks.
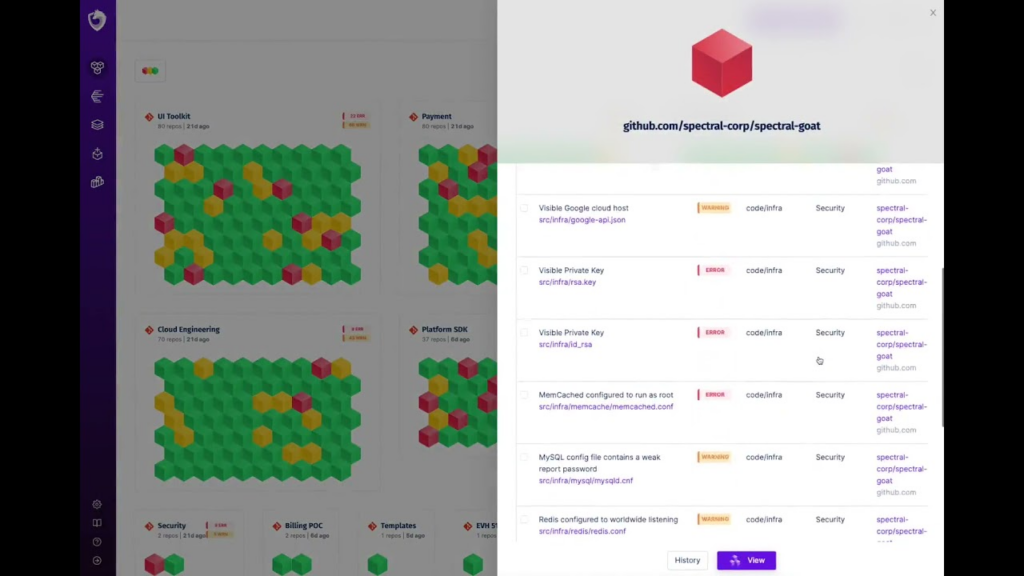
Spectral is a robust cybersecurity solution that acts as a control plane over source code and other development resources. It helps developers improve their CI/CD by automating the processes of secret protection at build time. Furthermore, you can use Spectral to monitor and detect issues in API keys, tokens, credentials, and security configurations in real time to avoid threats before they cause significant damage.
Main features:
Best for: Protection against exposed API keys, tokens, credentials, and high-risk security misconfigurations.
Pricing: Offers a free trial, then you can contact customer support for pricing options.
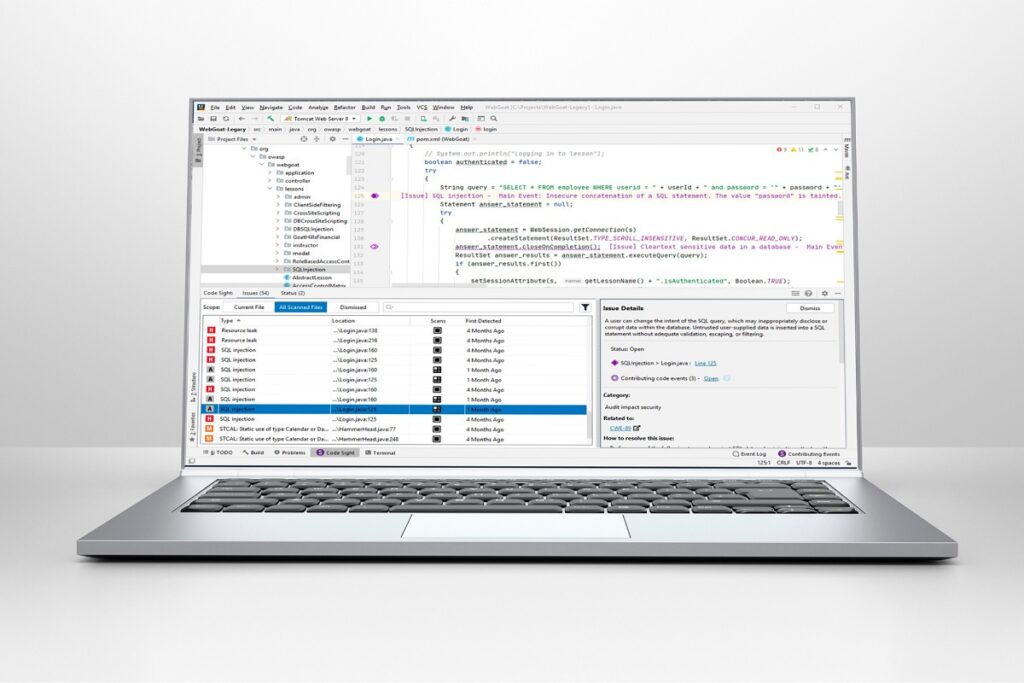
Coverity, by Synopsys, is a robust static analysis tool that assists organizations in identifying and resolving software vulnerabilities during the development phase. In addition, it is widely used to manage risks and ensure compliance with security and coding standards.
Main features:
Best for: Perform static analysis to improve security and reduce risks associated with the software development life cycle.
Pricing: By inquiry.
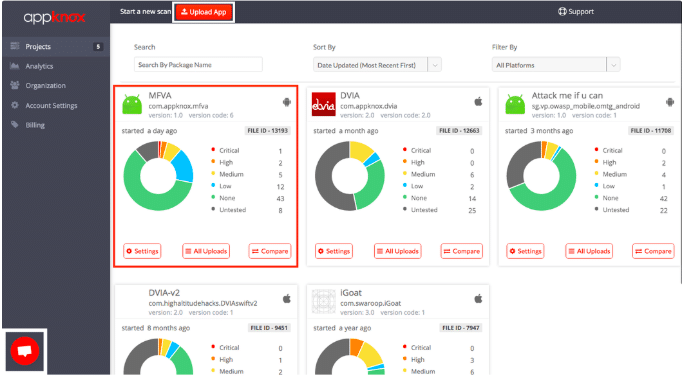
AppKnox is a mobile application security platform specializing in identifying and addressing security risks within mobile apps. With AppKnox, you can cover SAST, DAST, API testing, and penetration testing for mobile applications.
Main features:
Best for: Enhancing mobile application security, identifying vulnerabilities, and ensuring compliance with security standards.
Pricing: By inquiry.
Observability is a critical practice in modern systems and software engineering. It focuses on gaining insights into complex systems by collecting, analyzing, and visualizing data from various sources. Monitoring allows developers to understand the behavior of their systems in real-time, detect issues, and resolve them rapidly.
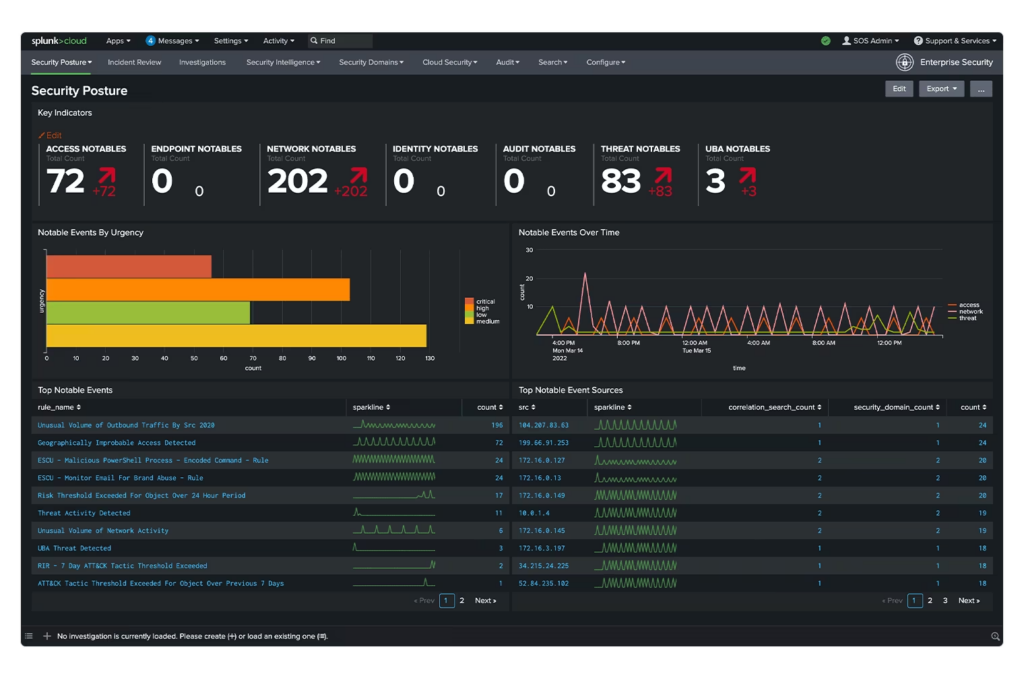
Splunk is a unified security and observability platform that provides a wide range of products to improve your organization’s digital resilience, allowing you to adapt to any change that comes your way. Splunk Enterprise and Splunk Cloud Platform are the two most-used tools for searching, analyzing, and visualizing data to get valuable, actionable insights.
Main features:
Best for: Data analytics and monitoring to gain valuable insights, detect anomalies, and drive data-driven decision-making.
Pricing: By inquiry.
SolarWinds is another popular monitoring and observability platform used in the software industry. SolarWinds has two products for observability: SolarWinds Observability and Hybrid Cloud Observability. You can also use these products in various security-related areas like networking, database management, system management, etc.
Main features:
Best for: Full-stack hybrid and multi-cloud observability and database performance management.
Pricing: SolarWinds Observability pricing starts at $5 per month, and Hybrid Cloud Observability pricing starts at $5.50 per month per node. You can get details pricing on their website.
Trellix offers various products to help organizations improve their security and resilience. Trellix XDR is one of the cutting-edge products they introduced with an XDR (extended detection and response) architecture to detect, respond and prevent threats easily.
Main features:
Best for: Small and medium-sized businesses seeking an intuitive and flexible website-building platform.
Pricing: By inquiry.
Security automation tools are an excellent solution for threat monitoring and detection since they help developers automate repetitive tasks, accelerate incident response, and improve the overall security posture of their applications. For example, Spectral automates the processes of secret protection by monitoring and detecting API keys, tokens, credentials, security misconfiguration, and other threats in real-time.
Get started with Spectral today by creating a free account.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions