Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
If developers one day considered security a mere ‘good-to-have,’ that day is firmly in the past. As digital transformation accelerates, employee workstations become liabilities for enterprise assets and data, placing cybersecurity in the spotlight. On average, organizations face 130 security breaches annually, and every data breach costs a company around $4.24 million. For better or worse, remote work culture and corrupted credential are the top reasons for security breaches. The good news? They are easily preventable.
Ensuring that enterprises enforce a strong security stance and implement best practices to reduce risks is critical–and that’s where security hardening comes in. It locks down vulnerabilities to make the entire system resilient against attacks. This blog looks at what security hardening entails and its significance for modern businesses.

Security hardening reduces the attack surface and mitigates threats across applications, systems, infrastructure, and other assets. It is achieved by implementing tactics and using tools to harden systems by identifying and fixing broken ports, insecure permissions, poor access controls, and improper account functions within your IT environments.
In essence, security hardening is a method to harden the entire ecosystem by limiting how attackers can breach it. It is similar to locking all the doors and windows of your home at night to ensure there’s no way in for unwanted visitors.
For this to work, security hardening needs a systematic approach to investigate, identify, fix, and manage security concerns across your end-to-end processes. So we can classify hardening under various subsections, such as:
Each security hardening type has specific focus areas and unique tools, techniques, and frameworks for robust security.
DevOps has transformed software development by centering the process around quality and speed. It enables faster product releases, continuously improving the overall performance of applications. But DevOps engineers aren’t always aligned with security professionals. DevOps demands code commits and deployments in short tranches over a short time. In such a fast-paced development lifecycle, security can become an afterthought, leading to insecure code, vulnerabilities, misconfigurations, and other weaknesses in security.
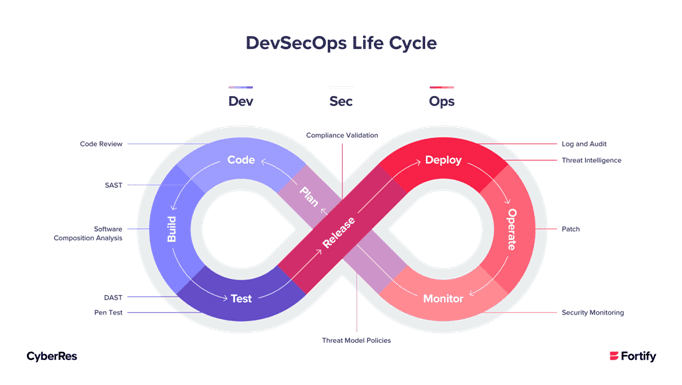
The answer is to automate security so that DevOps can integrate it across the DevOps pipeline without slowing it down. That’s what the concept of DevSecOps stands for: it puts developers in charge of handling security by proactively detecting and fixing security challenges as they appear throughout the DevOps pipeline.
The best way to include a security mindset in DevOps is through onboarding a highly efficient and reliable toolchain. DevSecOps refers to the below list of best practices:
The idea that “you are only as strong as your weakest link” has long been popular in security circles, and that’s because it’s true. Employees can (and often do) become your most significant security vulnerability, not out of malintent necessarily but because humans make mistakes.
So you must strengthen your human firewall through regular awareness training sessions on cyber security. While creating awareness regarding security threats is essential, the onus falls on employers to empower people with the necessary tools to identify and avoid malicious attempts proactively.
Phishing scams, for example, are evolving at an unbelievable pace. And they’re not just limited to emails carrying suspicious links; hackers also initiate brand impersonation attacks through text messages, social media channels, ads, and even fake apps that look legitimate. Attackers also impersonate individuals by resorting to deep fake using AI techniques to create videos and phone calls. Using the reputation of the company or person they are impersonating, attackers gain victims’ trust and trick them into handing over personal, corporate, and financial information. Because these attacks target humans rather than technology and initiate outside your security perimeter, you must educate your employees on spotting them. Identifying ransomware, setting up strong passwords, implementing multi-factor authentication, denouncing fraud attempts, and avoiding public WiFi are some measures they should keep front of mind.
Although it is universal knowledge that patching is the easiest way to fix most known vulnerabilities, developers often overlook its significance. Your operating system, applications, and systems like network equipment regularly need to be patched up to eliminate any security risk in your system. An efficient patch management strategy secures your system against attacks and ensures that you remain compliant with necessary regulations. Additionally, patching gives you access to upgraded features or functionalities, which can lead to better performance.
Automating patch management and software updates helps you eliminate human error or oversight by keeping track of missing patches and security gaps through end-to-end scanning. You can also leverage automation to deploy patches to systems and report patch deployment status, saving you time.

Passwords are meant to protect your systems and data, but picking easy-to-guess passwords defeats the purpose. Unfortunately, it is more commonplace than you’d think: poor password security contributed to 81% of all data breaches in 2021. An attempt to address this problem led to the emergence of a hardening sub-type called password hardening. It involves using techniques and tools to set passwords that can’t be breached. Some simple password-hardening tips include:
Data access is one of the primary motivations for malicious elements to launch a cyberattack, which makes data security a core tenet of security hardening. You can secure data by encrypting it while file-sharing or handling sensitive data. Data encryption translates data into code that can only be read using a secret key. You can also use data protection tools to encrypt access to devices, emails, or data itself.
Some of the best practices for ensuring enterprise-grade data security include:
Antivirus is a security practice of identifying and managing files infected with viruses to limit issues like data corruption, system crash, and forceful access to systems. Viruses are typically malicious code that seeps through your emails or file-sharing protocols, compromising your defenses. They can steal data, change permission controls, and infect your hardware. Using a resilient antivirus will help you flag the presence and attempts of malicious code.
But as viruses constantly evolve and are engineered to deflect security measures, you must regularly update your antivirus to ensure they are relevant to the threats of today.
Security hardening is tedious, exhausting, and time-consuming if done manually. Although security has considerable importance in guaranteeing the well-being of your enterprise, developers have their priorities. Below, we look at the limitations of security hardening:
For DevOps engineers, speed is of prime importance. With that in mind, implementing security hardening becomes impractical if it slows down the development process. That’s why the SpectralOps platform focuses on applying source code security quickly by offering seamless integration with CI pipelines. Additionally, with inbuilt support for servers and cloud providers including Jenkins and Azure, and custom hooks that automate early issue detection, you can identify vulnerabilities as early as in the pre-commit stages.

Unfortunately, security hardening doesn’t guarantee absolute security due to the hidden risks and shadow assets that waste your efforts. To tackle that, our solution monitors codebases, logs, and other assets to identify and fix hidden vulnerabilities. Our platform gives you access to 2,000 AI detectors for the broadest possible detection coverage to uncover your organizational blindspots, shadow assets, and supply chain risk in one dashboard.
The existing IT scene consists of distributed systems and environments, making unified monitoring challenging. In other words: the attack surface is expanding and you must know what’s happening across its entirety, but logs and other monitoring data spread across distributed systems make it challenging to gain a complete security picture of your environment. Spectral has an answer: it brings all your logs to one place to gain improved visibility into your security stance. Our shift-left approach to log shipping integration means they’re no longer scattered, making it easier for you to track sensitive data and prevent it from leaving your perimeter.
You’ll probably agree that security hardening is a necessity in modern times. With remote work becoming the norm and digitalization widening the attack surface, this is not the time for organizations to falter and make mistakes. They must prevent cyberattacks in the CI/CD pipeline and build secure applications while ensuring productivity remains on track. Yet, it remains a fact that security hardening measures tend to hold them back. To implement security standards and ensure compliance, you must regularly audit your systems for missing security configurations or patches. We’re here to help.
Spectral’s tool was built by and for developers, with developers’ priorities in mind. For example, we respect your CI, so we ensure that an average-sized repo takes the SpectralOps platform only seconds to scan. No configuration is needed because our solution runs secure by default–you can scan your GitHub, GitLab, Bitbucket, Npm, and more without granting Spectral any permissions of any kind. In other words: you code, we protect. To see it for yourself, create a free account today.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions