Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Rapid digitalization and increasing remote business operations place a significant burden on developers, who are continuously pressured to push out software faster. As a result, CI/CD security risks being overlooked, although it is an essential part of modern software development practice.
While it accelerates product releases, CI/CD is vulnerable to cybersecurity issues such as corrupted code, security misconfiguration, and mismanagement of secrets. By applying best practices to secure your CI/CD pipeline, you can ensure code quality, manage risks, and maintain integrity.
Owing to the critical role that the CI/CD plays in managing the software lifecycle, it follows that securing the CI/CD pipeline should be your top priority. But how do you secure a CI/CD pipeline? Let’s answer that question in this blog post.

The State of the Software Supply Chain Report shocked the world in 2020 when it found that next-generation cyber attacks aimed at actively infiltrating open-source software supply chains have surged by 430%. It also found that 51% of organizations need more than a week to remediate new zero-day vulnerabilities. Against this backdrop, the impact of CI/CD on DevOps can be powerful: it helps developers release code 83% faster, freeing them up to focus on more testing, including security. But what about CI/CD security itself?
CI/CD security is about identifying and mitigating security risks within your software delivery pipeline so that you churn out high-quality products that are reliable and risk-free. Every organization or product has a unique CI/CD pipeline based on its key processes and tools. But the underlying idea of hardening CI/CD security is to avoid data leaks and application disruptions.
At its core, a CI/CD pipeline comprises critical development components like source code, application code repositories, containers, and build servers, making it a prime target for attackers. Even if a single component is compromised, it could give attackers a way to exploit your resources. Moreover, implementing security measures becomes challenging as the pipeline grows in complexity, with multiple production environments coming into the picture.
Without CI/CD security implementation, attackers can take advantage of its vulnerabilities to cause major attacks. Some of the security risks that pipeline security lapses can create are:
CI/CD pipeline is a core tenet of DevOps practices that focus on streamlined collaboration between development and operations. Although it brought revolutionary benefits in speeding up product launches, it fell short in a vital part of software development: security. This is where DevSecOps evolved as a unique and timely concept. It is a ‘shift left’ approach of integrating security at every stage of the software development process to build applications with security at their core, rather than treating security as an afterthought once applications have been delivered.
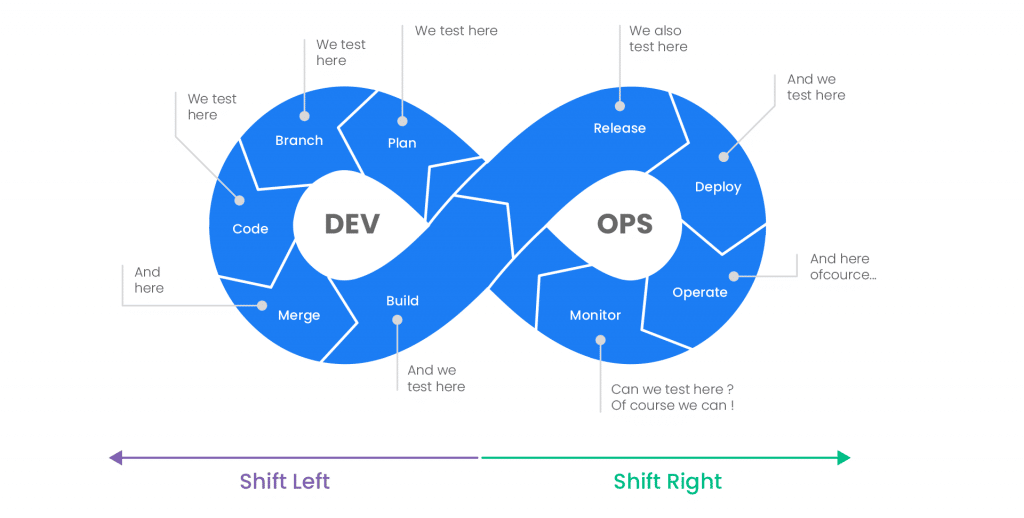
Adding security within your CI/CD pipeline is of utmost importance in the wake of increasing cyberattacks. About 66% of organizations have experienced a cyber attack in the last 12 months, according to a Ponemon’s State of Cybersecurity Report. It further disclosed that 45% of attack victims blame insufficient security measures for the attacks. Add to that IBM’s concerning find that it takes a business 197 days on average to discover a data breach and an additional 69 days to tackle it.
The SolarWinds incident is considered one of the most significant cyberattacks in recent times, and its sophistication is baffling. Attackers designed a custom malware to observe each step of the build cycle to detect and exploit vulnerabilities. This 2020 attack caused data breaches across thousands of organizations, including the US government agencies. The scariest part? It started with a small mistake: a poorly-selected password exposed on a public GitHub server by a SolarWinds intern. Had SolarWinds used a secret scanner, it could all have been prevented.
Implementing CI/CD security hardening measures in such a scenario seems like a bargain compared to the financial and reputational loss that cyber-attacks cause.
A CI/CD pipeline covers different stages of the development process, which demands comprehensive security hardening measures. Below is a list of best practices that can help you manage and mitigate CI/CD security risks end-to-end.
Misconfigurations are one of the leading causes of cyberattacks, as miscreants actively seek them to intrude into your systems. Organizations are yet to buckle up in proactively finding and fixing such issues. A recent report found that 63% of third-party code templates contained insecure configuration as of 2021.
You can significantly reduce malicious attempts against your applications by consistently detecting and remediating misconfigurations. Using strong coding, development policies, and automated tools to block risks introduced into the pipeline and ensure the integrity of each workload, you can spot pipeline weaknesses.
Organizations typically adopt IaC (Infrastructure-as-Code) and PaC (Policy-as-Code) strategies to manage misconfigurations. We will discuss these in detail in the latter part of the blog. As a DevOps principle, you must limit access to configurations. You can do this by exercising the least privileged access controls over critical functions like committing code changes to repositories, creating containers, and deploying code.
You can significantly enhance the security of your application by detecting bugs in your code in the early stages of the development cycle. This is done by establishing a robust code review practice within the pipeline to improve the quality of your code.
While it is crucial to follow secure coding principles to avoid defects in the product, it is also entirely plausible that attackers may find a vulnerability and exploit it to execute a malicious code. That’s why you must monitor, locate, and flag suspicious coding patterns. You can do this through strategies like pattern matching or by using automated code security tools to identify regular expressions or sequences of characters.
By using pull request checks in your repositories with a configured code scanning mechanism, you can identify a defect in a pull request, review the highlighted piece of code, and initiate remediation. Further, you can also use code scanning to identify open pull requests and add alerts.
Automation has become a necessity in the modern application development landscape. It facilitates faster product development, which gives organizations a competitive edge. The same applies to security management as well. You can significantly improve your pipeline security posture by implementing automation. IaC (Infrastructure-as-Code) and PaC (Policy-as-Code) are two widely used DevOps practices.
IaC is a process of ensuring secure configuration by automating infrastructure provisioning instead of the error-prone manual process. With IaC, you essentially codify the infrastructure state, creating templates of configuration requirements to manage, monitor, and distribute resources easily. In addition to boosting your team’s productivity, IaC facilitates code tracking and review to avoid code corruption.
With security becoming a key concern, the concept of PaC was introduced. Similarly to IaC, this is where you automate the implementation of security and compliance regulations by codifying policies, rules, and workflows. Since you save policy code in a version control system, you can easily track changes made to security mandates.
DevOps relies heavily on automation to accelerate development, configuration, testing, and deployment to release products faster. Such a rapid pace is achieved by using several tools and frameworks that don’t just expedite the process but also identify and resolves errors, vulnerabilities, and defects at speed. They also automate key processes like monitoring, testing, and infrastructure management to reduce the scope of inaccuracies. There are many types of CI/CD tools that you can use to strengthen your pipeline, such as:
CI Tools: Continuous integration tools enable you to integrate your code into a shared repository to automate builds, testing, and reporting. They facilitate multiple code integrations and automate verification processes to review and identify code issues.
CD Tools: Continuous deployment and delivery tools enable automated testing and manual reviews before pushing the software to a production stage. Using CD tools, you can speed up software releases and improve the quality and reliability of the product.
Configuration Management Tools: These tools help you track and manage changes orderly. They empower you to automate the approval and rejection of changes made to the configuration.
Traditionally, developers would leave testing till the fag end stages of the software development. However, this was a tedious approach since every identified defect forced them back to square one in order to tackle it at the roots. Implementing a continuous testing strategy is a more effective way to harden security for your CI/CD pipeline. It means infusing software testing at every stage of the development cycle and adopting a shift-left process.
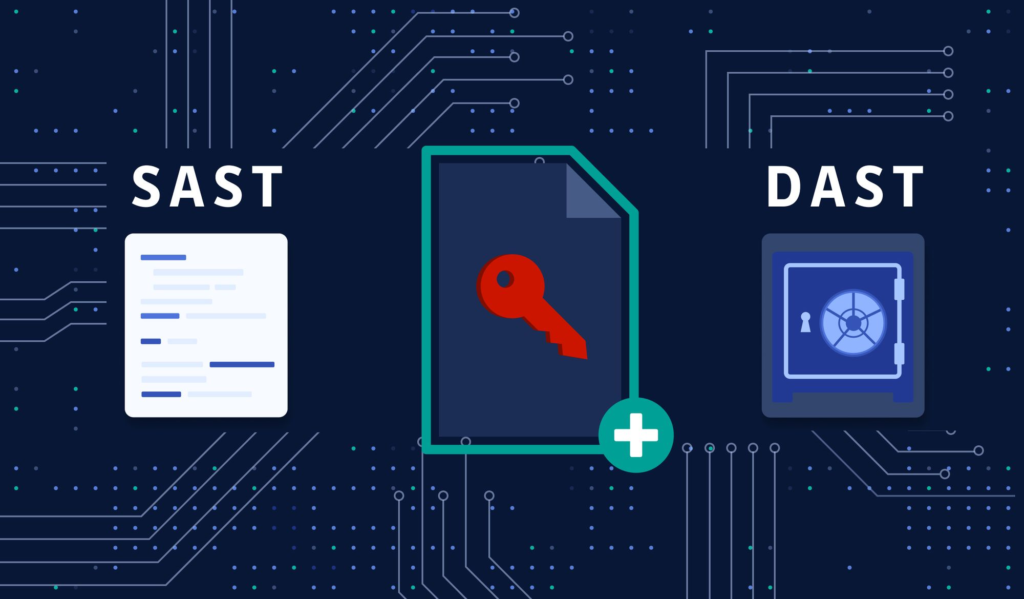
Some of the testing practices that you can employ include:
SAST: SAST (Static Application Security Testing) is the solutions category with some of the most powerful tools to integrate into your software development lifecycle when talking about shift-left security. It will have scan access to the application’s source code and binary code. You can test frameworks, designs, and implementation methodologies with static analysis. It gives you real-time reviews to quickly improve your security posture.
DAST: DAST (Dynamic Application Security Testing) is a methodology where you scan the application and its associated structures without any visibility into source code, technologies, or frameworks. For that reason, it is also known as ‘black box security testing’. It highlights security risks like SQL injection and cross-site scripting.
Penetration Testing: Penetration Test is a testing exercise where you trigger a fake cyber attack to understand application weaknesses like backdoors or endpoint vulnerabilities. It highlights threats such as authorization issues, business logic loopholes, and workflow gaps.
In addition to automating security management, you should also automate security procedures, including data security. It is primarily because product releases are associated with new databases, data models, or new data sets. When pulling data from production to run tests and validate features, you must protect sensitive data like personally identifiable information violating data governance policies.
You can employ multiple strategies to automate data security. Here are some examples:
While the development and testing teams need real data in production, they can refrain from accessing the same in other stages of the process. Data masking helps with that. It produces fake-looking realistic versions of sensitive data so that you can continue with training or testing without impacting the actual data. Data masking works by changing the values of the data but presenting it in the same format. This way, you can automate data obfuscation and, thereby, CI/CD pipeline.
Synthetic data is another way to reduce the risk to your data where the AI algorithm creates an entirely new sequence of characters. This means no part of the original data is used, leading to zero risk of disclosure.
Service virtualization is another data security strategy that reduces dependency on sensitive data to conduct tests. It creates simulated behavior of application components that are unavailable due to data governance guidelines, maintenance issues, or third-party dependency.
CI/CD is arguably the most crucial DevOps practice and forms a focal point of your entire software development process. It comprises critical application components like source code, repositories, and container frameworks so understandably, attackers consider CI/CD a hot target to breach your application. Which makes the security hardening of the pipeline a no-brainer. While we discussed the key aspects of securing your CI/CD pipeline, robust monitoring and auditing are equally critical in ensuring your pipeline is secure and working as it should be. That’s why Spectral focuses on helping developers to improve the observability of their environment.
Our solution flags to developers when there are any misconfigurations or exposed secrets in code, helping them to keep tabs both on the code they write and on code from open-source libraries imported into an application–which, as we’ve seen, can be a major source of security risks to the CI/CDpipeline. Learn how Spectral helps to secure your development pipeline in three simple stages.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Part of the Spectral API Security Series Yelp.com is one of the most influential crowdsourcing sites for businesses. The company is worth just over one billion