Top 10 SBOM Tools in 2023
Imagine this: you’re a developer working on a critical software application that thousands of people use daily. You’ve spent countless hours writing and testing code and
Today’s threat actors often carry out cyber attacks with the primary objective of accessing and exfiltrating sensitive information from your IT environment. Efforts to obtain this “crown jewel” information usually involve complex multi-phase cyber attacks. But another way in which sensitive data ends up in the hands of malicious actors with a lot less effort is when an organization exposes sensitive data assets in a data leak incident.
Primarily, profit is the main driver behind the modern trend toward data exfiltration (Verizon’s 2021 Data Breach Investigations report found that over 80 percent of breaches were motivated by financial gain). Malicious parties know that they can sell sensitive data on the dark web or hold organizations to ransom for huge sums. In the modern data-driven economy, businesses collect and generate sensitive information in abundance, which puts a target on their backs.
It’s imperative to detect and remediate data leaks promptly because there’s a strong probability a data leak turns into a data breach if not dealt with. Since data leaks are not always obvious, it’s prudent to turn to a dedicated solution for identifying and remedying these leaks. This article provides a round-up of five top data leak detection solutions along with some additional insights on data leaks and data breaches.
Data leaks and data breaches are two terms often used interchangeably but there are some differences worth clarifying.
A data leak is the accidental or intentional exposure of sensitive data by an organization. Data leaks are often instigated by security errors or weaknesses overlooked by organizations, such as unpatched software vulnerabilities, misconfigurations, weak passwords, and insecure disposal of storage media.
A data breach is an incident in which an unauthorized party manages to access or steal sensitive information. The enormous costs involved in a data breach — $4.24 million by one estimate — make the possibility of a breach a particularly unpalatable occurrence for security and technology leaders. These costs include compliance fines, litigation fees, and more intangible costs like reputational damage.
The distinction here is important because a data leak can directly lead to a data breach. When a threat actor takes advantage of a data leak and accesses or downloads sensitive data assets, you have a breach on your hands.
The escalation from a data leak to a data breach can happen in minutes or hours especially given the sheer number of opportunistic threat actors constantly hunting for low-hanging fruit. Even if it takes days, many organizations face the awkward situation of only finding out about breaches when reading a media report after a threat actor posted their sensitive data assets on a dark web forum.
Data leak detection solutions help to accelerate the time taken to identify these leaks and potential data breaches. The following list of data leak solutions is presented in no particular order.
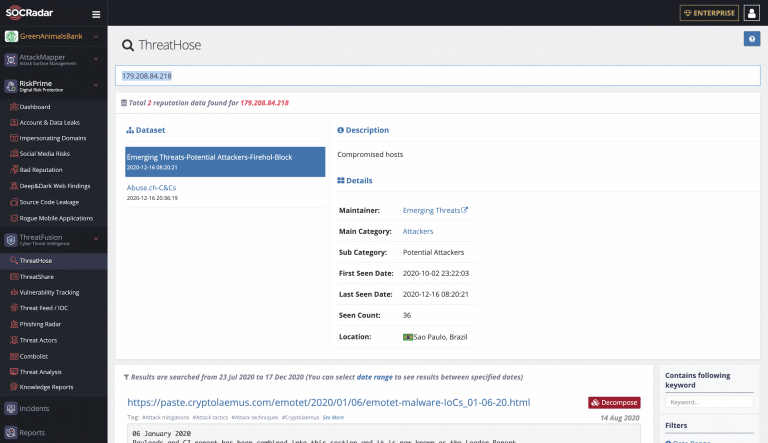
SOCRadar combines digital risk protection, cyber intelligence, and external attack surface management solutions into cloud-based platforms.
SOCRadar’s mission is to facilitate organizations in becoming more proactive against evolving cyber threats. The company was formed in 2018 and has since grown to work with over 150 customers. There is a free access tier for SOCRadar and subscription plans for very small teams available.
Read a full solution brief here.
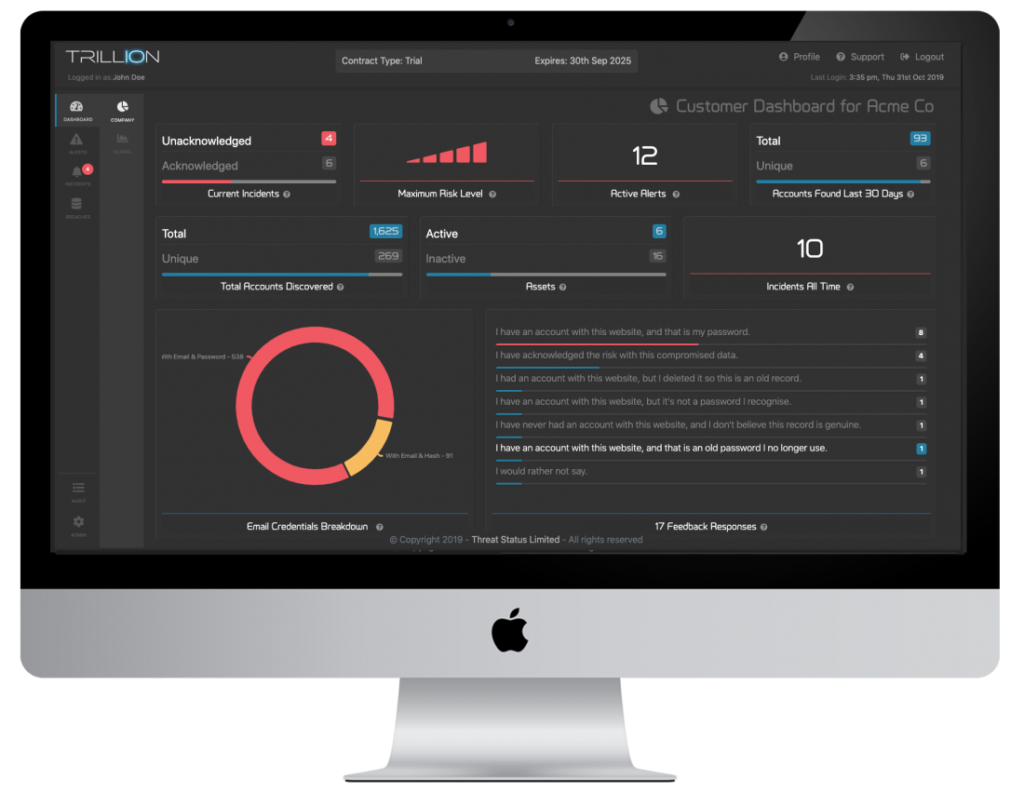
Threat Status has a SaaS platform named Trillion. The purpose of Trillion is to monitor for data leaks and breaches in third-party applications. A feature of Trillion named Honey Creds inserts small unique attributes into data for the purposes of monitoring your sensitive data assets for potential exposures.
Threat Status is a UK-based cybersecurity company. The solution is aimed at IT admin and security teams.
You can read a full datasheet on the solution here.
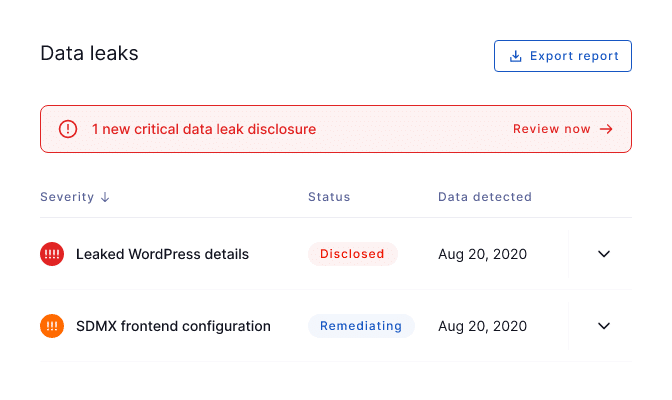
BreachSight is a fully-integrated attack surface management platform that helps prevent data breaches and discover leaked credentials. The platform comes with reporting, security risk scores, and automated notifications when employee credentials get leaked.
Upguard is a cybersecurity vendor specializing in third-party risk and attack surface management platforms. The company processes over 800 billion data points each day and regards its mission as “protecting the world’s data”. BreachSight has pricing plans aimed at small businesses right through to the enterprise level.
Get the lowdown with a full datasheet on BreachSight here.
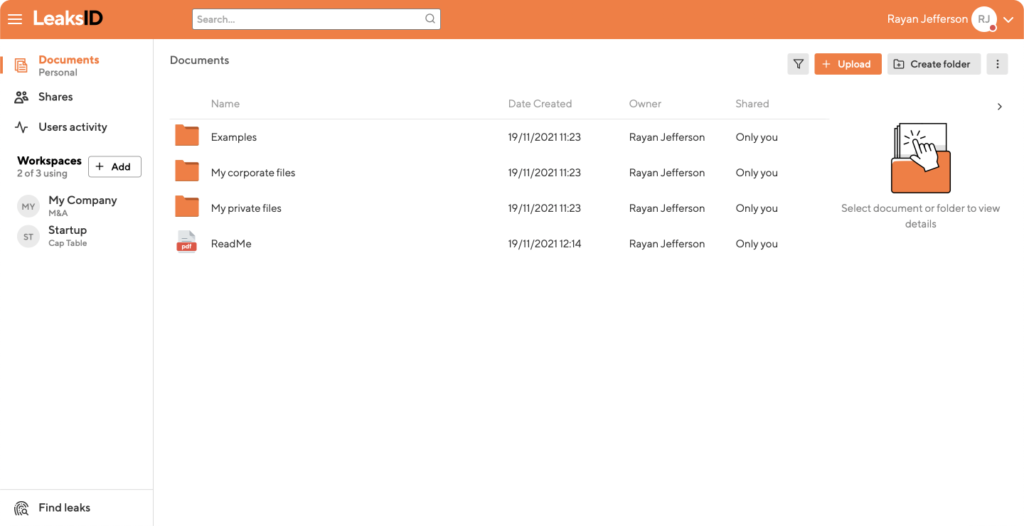
LeakdsID is a solution specifically focused on protecting sensitive documents against leaks from insider threats (both accidental and intentional). A patented algorithm adds anti-leak marks to sensitive documents to deter insiders from exposing those assets to potential breaches.
LeaksID is a solution launched by American cybersecurity company G-71 Inc with a mission to instill a culture of carefully handling sensitive documents internally. From printouts to screenshots to pictures of documents on smartphones, each of these risky insider activities creates a potential data leak.
Find a comprehensive introduction to LeaksID here.
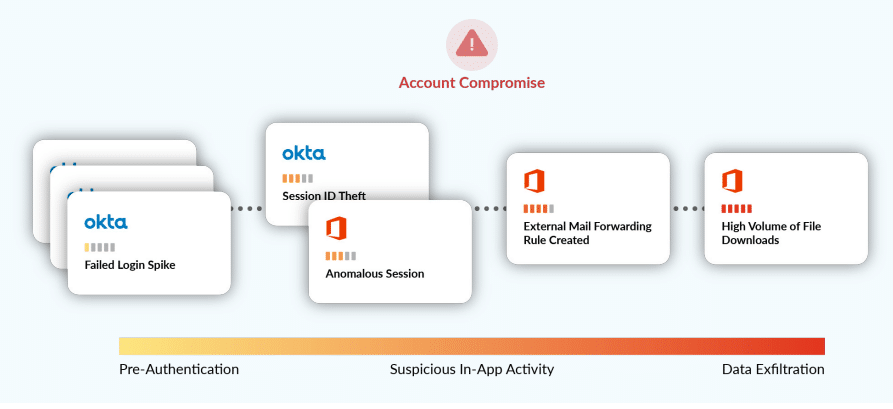
Obsidian is a cloud detection and response platform providing security analytics and visibility into leading SaaS applications used by many businesses, such as Salesforce, Office 365, and Google Workspace. The solution is a SaaS product that doesn’t require you to install any agent. The solution helps detect and mitigate account compromise and other data leaks in SaaS apps before your data can be exfiltrated (breached).
Obsidian is a California-based cybersecurity startup wanting to protect the SaaS applications that today’s businesses rely on most.
A full white paper outlining the Obsidian platform is here.
These top data leak detection solutions are clearly useful tools to have in your cybersecurity arsenal. Identifying data leaks in a timely manner can prevent security mishaps or intentional actions that expose sensitive data from escalating to full-scale breaches – not to mention all of the associated unwanted consequences of a breach.
But to really get to the root of data leaks, you need to have tools and processes in place that prevent these incidents from happening at all. A pillar of any good cybersecurity strategy is multiple lines of defense. Threats to your code and data can come from internal and external sources, so one solution or one type of solution (detection) is unlikely to suffice.
Spectral’s AI-powered technology gets to the root of data leaks by monitoring, classifying, and protecting your code, assets, and infrastructure for exposed API keys, tokens, credentials, and high-risk security misconfigurations. The scanner works in minutes and helps identify and remediate issues and risks in code and other assets that could lead to data leaks and breaches further down the line. Learn more about real-time data loss prevention today.
Imagine this: you’re a developer working on a critical software application that thousands of people use daily. You’ve spent countless hours writing and testing code and

DevOps is more than just a buzzword and the dev behind the magic is more than just a tech wizard who orchestrates software delivery single-handedly. Behind

Docker has revolutionized how developers work by offering a powerful platform for creating, shipping, and running container applications. It helps developers conquer the complexity of application