Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Docker has revolutionized how developers work by offering a powerful platform for creating, shipping, and running container applications. It helps developers conquer the complexity of application development and significantly increases software shipping frequency.
Despite setbacks in recent years, Docker brings home $50 million in revenue every year, driven by the ongoing demand for new applications. It’s also spearheaded by the surge in software supply chain attacks, which amplify the need to safeguard containers against security threats. Container vulnerabilities can lead to unauthorized access to applications or data, potentially costing millions of dollars in damages.
So, in this article, we will discuss the top ten Docker vulnerability scanners you can use to address the security concerns associated with Docker containers.
Docker vulnerability scanners are tools designed to automatically scan Docker images for security vulnerabilities, such as outdated packages or known security flaws. These scanners analyze the contents of a Docker image, including its dependencies and configurations, and identify potential risks that could lead to a security breach within a containerized application environment.
While Docker vulnerability scanners can help detect many security issues, they have limitations. For instance, they might be unable to identify unknown vulnerabilities or risks from custom application code or libraries.
So, you need to combine Docker vulnerability scanners with other effective security practices, such as adopting secure software development life cycle (SSDLC) methodologies to ensure a well-rounded security approach.

There are various types of Docker vulnerability scanners available to address different aspects of container security:
Docker vulnerability scanners offer several valuable benefits to users:
Docker Bench is a popular tool for checking the security configuration of Docker installations. It automatically assesses Docker hosts against common security best practices, providing valuable insights to enhance the security of their Docker environment.
Best for: Teams looking for a quick way to assess Docker security configurations.
Price: Free.
Spectral is a powerful vulnerability scanning platform that acts as a control plane over source code and other development resources. It helps developers monitor and detect issues in API keys, tokens, credentials, and security configurations in real time.
Best for: Protection against exposed API keys, tokens, credentials, and high-risk security misconfigurations.
Price: Offer a free trial. Contact customer support for customized pricing options.
Clair is an open-source tool that can perform static analysis for vulnerabilities in Docker containers. Developers widely use it to index their container images and match them against known vulnerabilities.
Best for: Static analysis of vulnerabilities.
Price: Free.
Anchore is another popular tool for container vulnerability scanning. It automates the container scanning process for development environments, CI/CD pipelines, registries, and runtime environments through a comprehensive set of APIs and a CLI tool.
Main features:
Best for: Automating container vulnerability scanning.
Price: Offers four plans: ‘Team,’ ‘Business,’ ‘Ultimate+,’ and ‘Premium’. The pricing structure is based on scanning stages, subscription tiers, environment size, SBOMs, and the number of analyzers used.
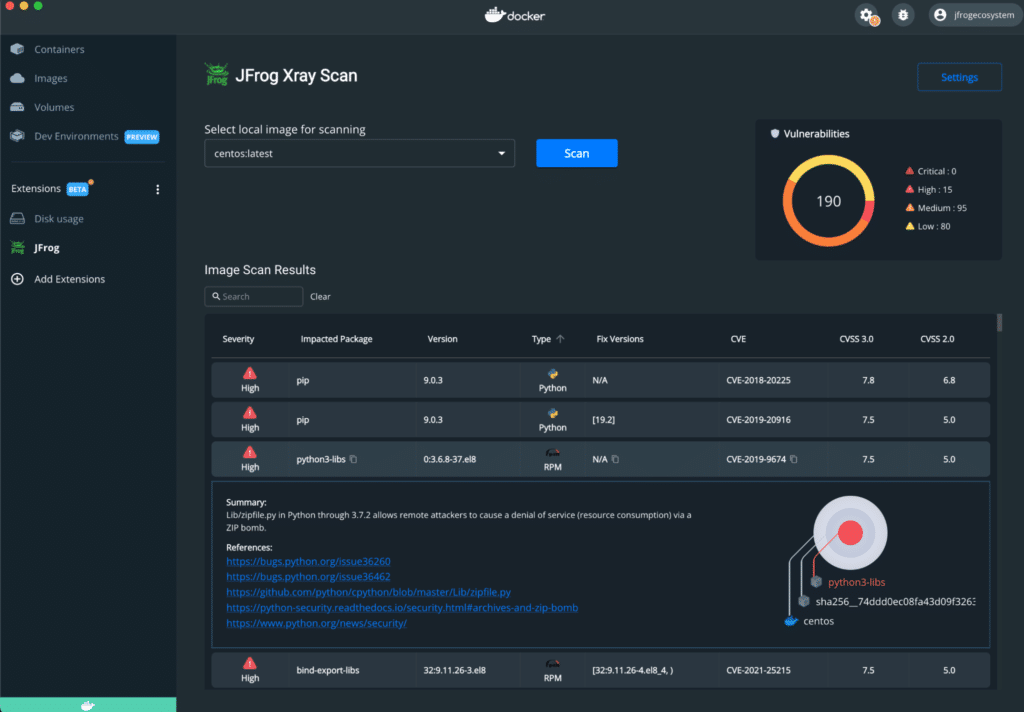
JFrog offers a powerful Docker vulnerability scanner covering the entire lifecycle of your Docker images. You can use JFrog to manage development, vulnerability analysis, artifact flow control, and distribution.
Best for: Companies already using JFrog products or looking to cover the full lifecycle of Docker images.
Price: JFrog provides several pricing options including Pro, Enterprise X, and Enterprise+. You can also get a custom plan based on your requirements.
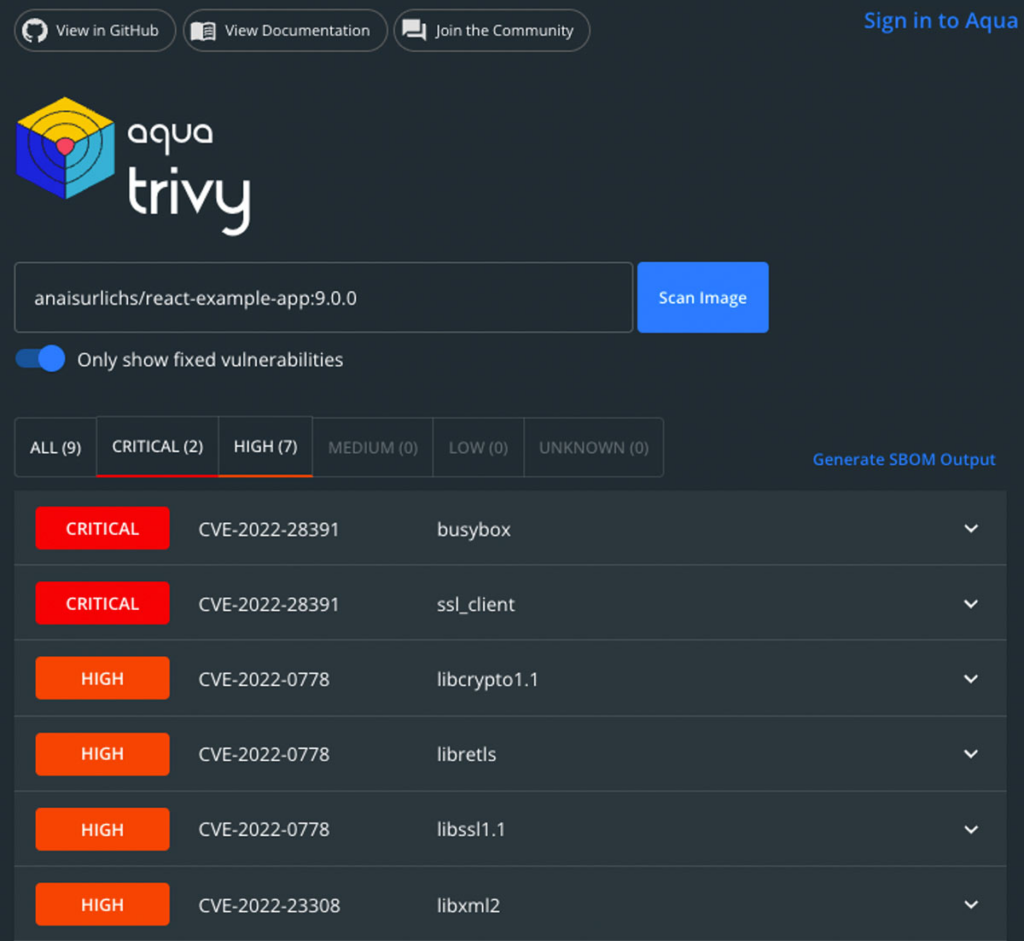
Aqua Security’s Trivy is another vulnerability scanner for Docker containers and Kubernetes clusters. You can use it to detect vulnerabilities in various operating systems and programming languages, including Oracle Linux and Red Hat Enterprise Linux.
Best for: Teams seeking an all-in-one open-source scanning solution.
Price: Free.
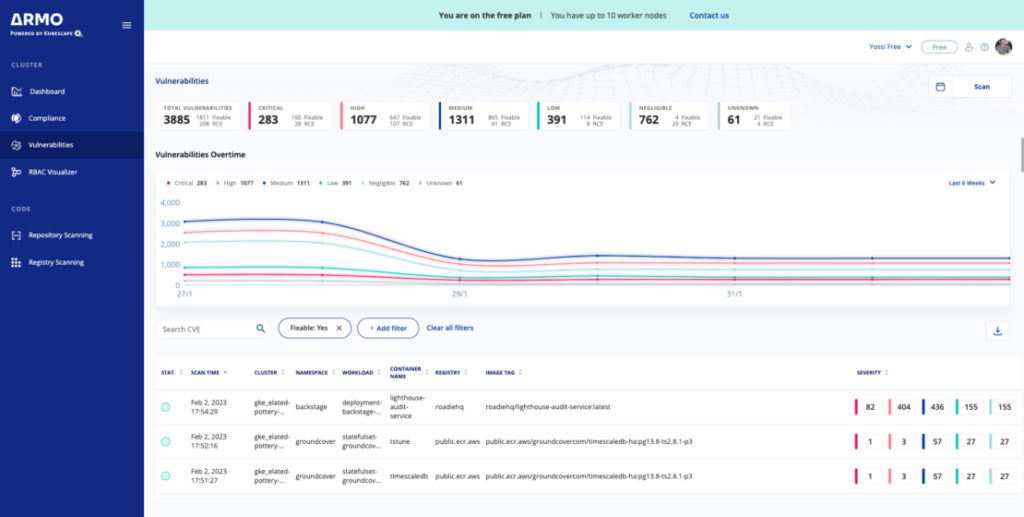
Armo is another popular security scanning tool for Docker images and Kubernetes clusters. With Armo, you can detect vulnerabilities in the early stages of SLDC or third-party registries.
Best for: Kubernetes and Docker image scanning.
Price: Offers three pricing options: Free, Team, and Enterprise. The Team plan costs $29 per worker node/month, while the Enterprise plan is customized based on your needs.
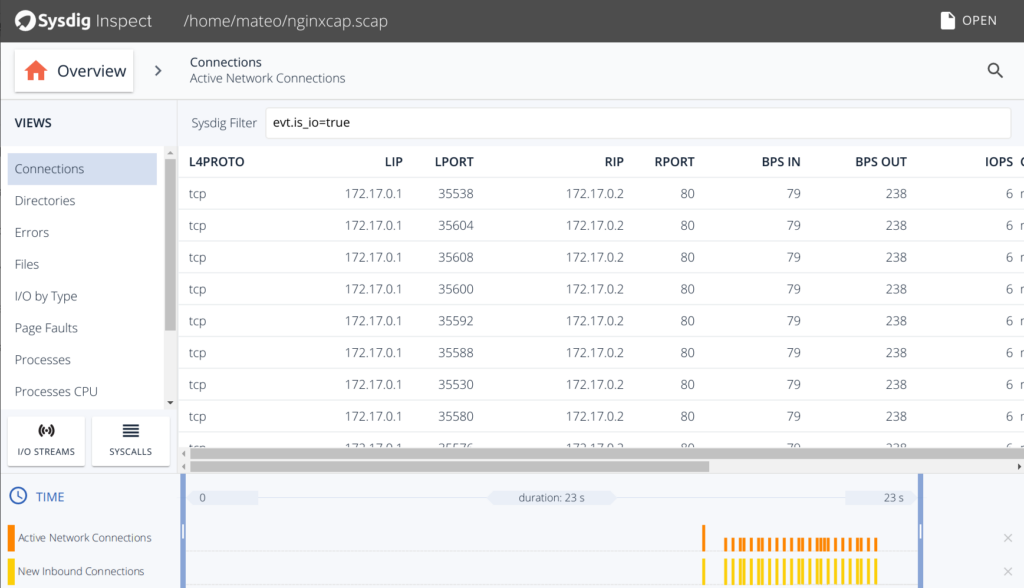
Falco is an open-source solution for runtime security for hosts, containers, and Kubernetes. It provides real-time visibility into abnormal behaviors, potential security threats, and compliance violations.
Best for: Teams seeking a behavioral analysis security tool.
Price: Free.
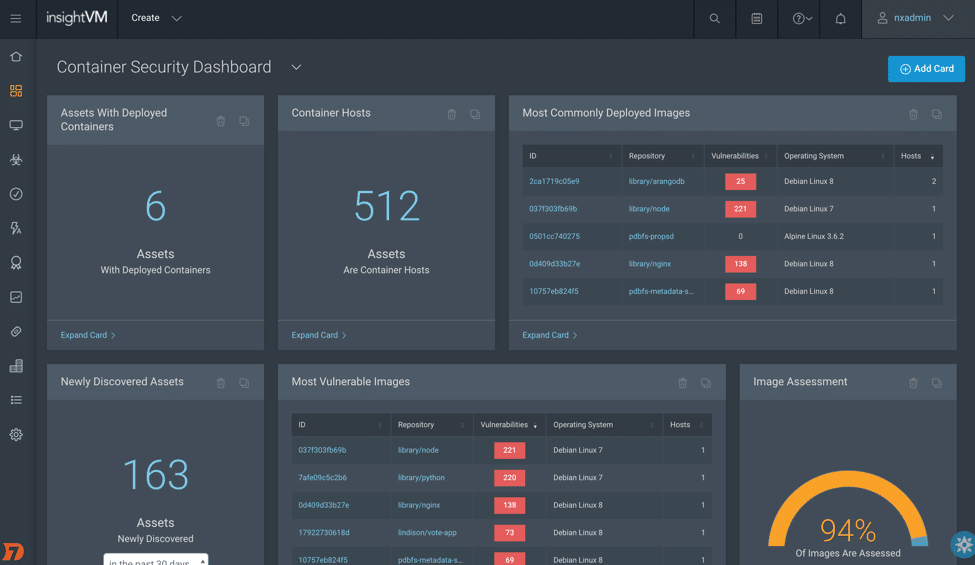
Rapid7 provides a range of tools for Docker vulnerability scanning and container security. Rapid7 InsightVM is widely used for endpoint scanning, risk prioritizing, and remediations.
Best for: Organizations seeking a complete cloud security package.
Price: Contact customer support for customized pricing options.
Docker Scan CLI is a built-in tool provided by Docker to scan Docker images. It relies on a vulnerability database to identify known security flaws. So, you need to ensure Docker and the database are up to date to get accurate results.
Best for: Teams looking for a simple way to scan Docker images for known vulnerabilities.
Price: Free.
With the increased usage of Docker, it has become paramount to safeguard Docker containers against security threats. By utilizing the Docker vulnerability scanners discussed in this article, you can identify and address potential threats before they become critical issues.
For example, Spectral helps prevent data leaks and protect your code, assets, and infrastructure, whether locally built or pulled from Docker Hub. Spectral secures your Docker containers and enhances your development process.
Get a free trial to learn more.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions