Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
In the world of software development, you’re often racing against deadlines and demands from all directions. Product, marketing, service, and support all seem to have something critical and urgent for developers to code at all times. So it’s not unusual for cyber security to take a back seat to delivery even when it means exposing your code and company to the risks of a costly data breach.
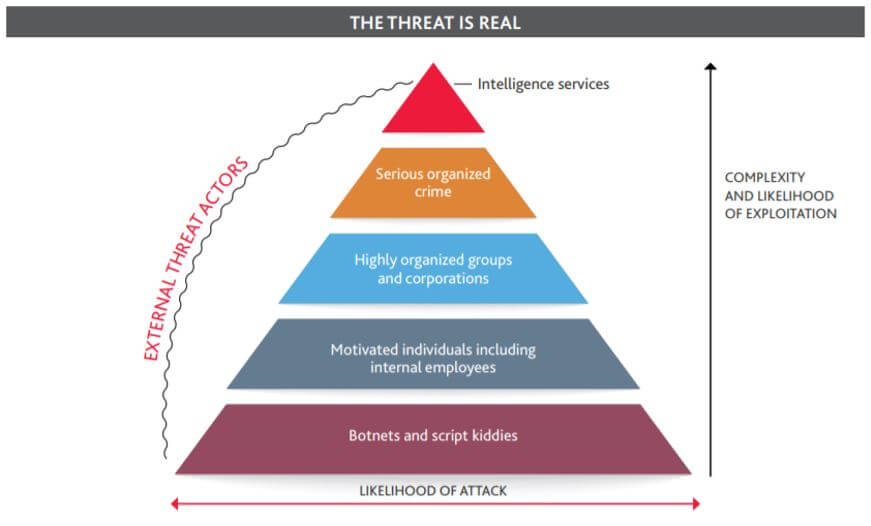
In reality, creating and maintaining an effective cyber security strategy is not that difficult, even in a small organization. Before we discuss the building blocks of an effective cyber security strategy, let’s take a moment to define what it is and why you must have one in your organization.
A cybersecurity strategy is the organization’s plan for minimizing cyber risk and securing its assets from digital threats. Cyber security strategies are typically developed with a 3-5 year vision but should be updated and reevaluated frequently.
A good cybersecurity strategy is not set in stone. It’s a living, breathing document. It must adapt and adjust to the current threat landscape and adopt tools and best practices to protect the business from internal and external threats.
To be effective, your cyber security strategy should rely on the right set of tools and processes to proactively detect, classify, and mitigate cyber threats.
Simply put, you cannot afford not to have an effective cyber security strategy. With new breaches, code, and credential leaks published almost daily, a critical breach event in any digital business today is not a matter of “if” but instead of “when” and “how bad.” The 2021 security data breach report revealed that 1,767 reported breaches exposed a total of 18.8 billion records during the first six months of 2021.
Moreover, as privacy regulations often make you liable, if you didn’t do everything in your power to protect your data and your clients’ data from exposure, you may be held legally responsible for the damage caused by the data breach. In addition, the proliferation of cloud-based applications and CI/CD tools combined with a lack of understanding of the shared responsibility model create fertile ground for malefactors to grow their attacks.
A solid cybersecurity strategy is the only way to achieve cyber resilience and protect your business from irreparable consequences.
A cybersecurity strategy is the organization’s blueprint to ensure cyber protection. It also instructs the different parties and teams on what to do in case of a breach. In addition, it serves as a guide for the key stakeholders and customers that understand the importance of cyber defense.
The concept of creating a cyber security strategy document may seem daunting at first, but when broken down into steps, it’s a lot easier to approach. So how do you get started?
The first building block of an effective cyber security strategy is a comprehensive inventory of all digital assets, personnel, and vendors. Order and organization are critical. Having an up-to-date list of assets makes it easy to evaluate internal and external threats and weaknesses. It also helps discover long-forgotten or neglected issues in your IT infrastructure.
Start by mapping your data, assets, and threat landscape.
This is the most basic and most crucial step in crafting your cyber security strategy. Don’t skip it.
The next thing you want to do is recruit the rest of the company to help you keep your company safe.
If you want an effective cyber security strategy, you need everyone to be on the same page. Therefore, consistent communication with every employee, manager, and vendor is a must.
Before you go too deep down the risk assessment rabbit hole, make sure you have the cooperation and collaboration of data owners and other departments you may need on your side. Similarly, you should ensure you have the resources to implement your cyber security strategy and policy.
To ensure you’re not missing anything and to comply with industry standards, it’s better to start building your cyber security strategy with the help of a proven cyber security framework. These frameworks are blueprints of policies, goals, and guidelines that explain all cybersecurity activities within an organization.
When choosing the right framework for your company, remember that you can adjust the blueprint to fit your business goals. Your risk inventory will come in handy at this point and will help you pick the appropriate framework.
Here’s a quick overview of the most prevalent cybersecurity frameworks:
Now that you’ve picked your cybersecurity framework, it’s time to personalize the policies to fit your cybersecurity strategy needs and your business goals.
To realize your cybersecurity strategy, you will need to create and enforce security policies. Security policies serve as the company-wide rulebook of your cyber security strategy.
However, there’s a difference between having a security policy and enforcing it. The cyber security policy is for the employees as much as it’s for CISO. Essentially, it helps employees understand their role in the cyber security strategy.
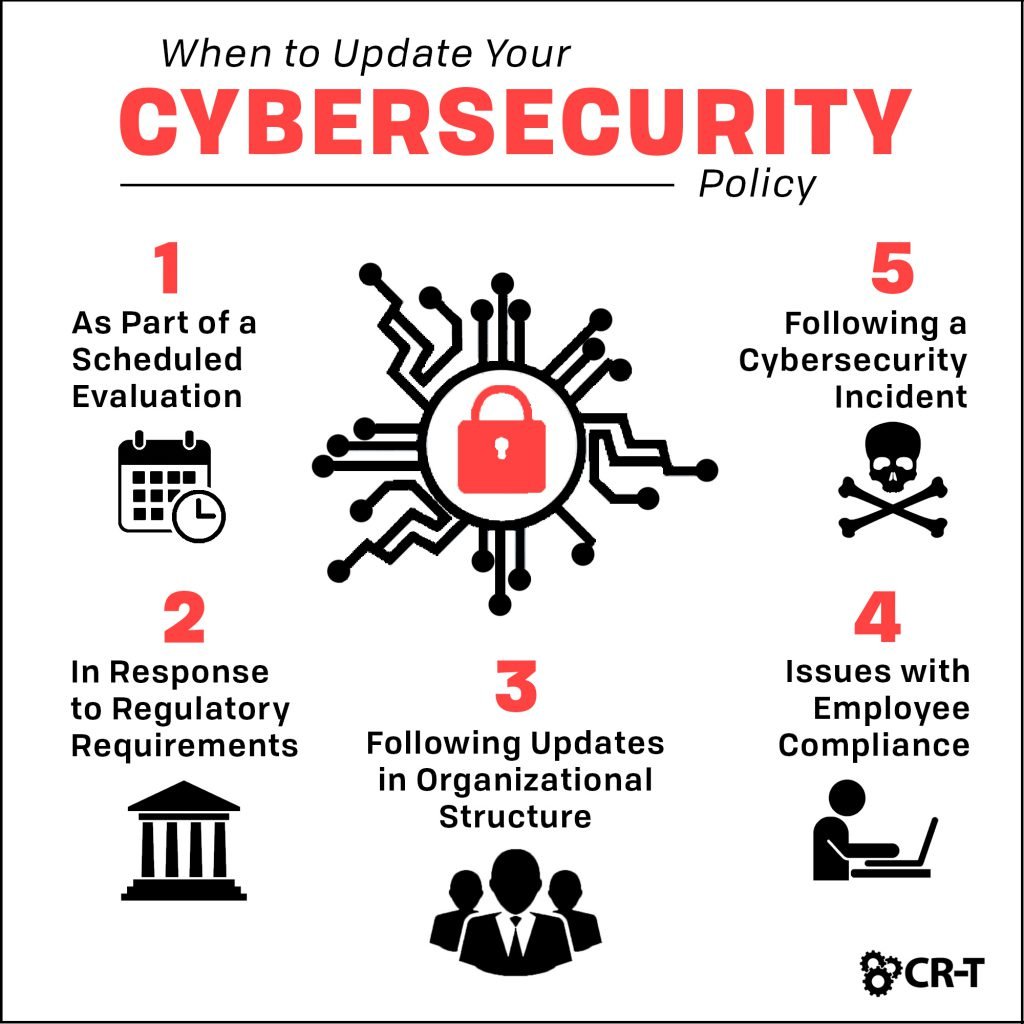
Having a cyber security policy in place helps with the collaboration and communication aspect of the strategy.
When developing your cyber security policy, consider the following:
Having a cyber security plan and policies is excellent, but how can you protect what you can’t see? Especially in your software development lifecycle? The best thing you can do for your company’s cyber security efforts is automating the threat detection process, especially when it comes to code security threats.
Code secrets, PIIs, and credentials are particularly hard to detect in code through conventional means and code reviews. As such, they demand an automated secret scanning tool that integrates seamlessly in the CI/CD pipeline. Spectral secret scanning does just that.
SpectralOps‘ advanced AI-backed technology uses over 500 detectors to discover and classify your data silos and uncover data breaches before they happen. With SpectralOps’ top-notch technology, you’ll be able to monitor and detect real-time threats from security misconfiguration, credentials, API keys, tokens, and more.
If you’re serious about your cyber security strategy, ensure it includes multiple lines of defense. Threats to your code and data can come from internal and external sources. So don’t just pick one or two defense tactics or tools, but rather layer access control with monitoring and automated scanning.
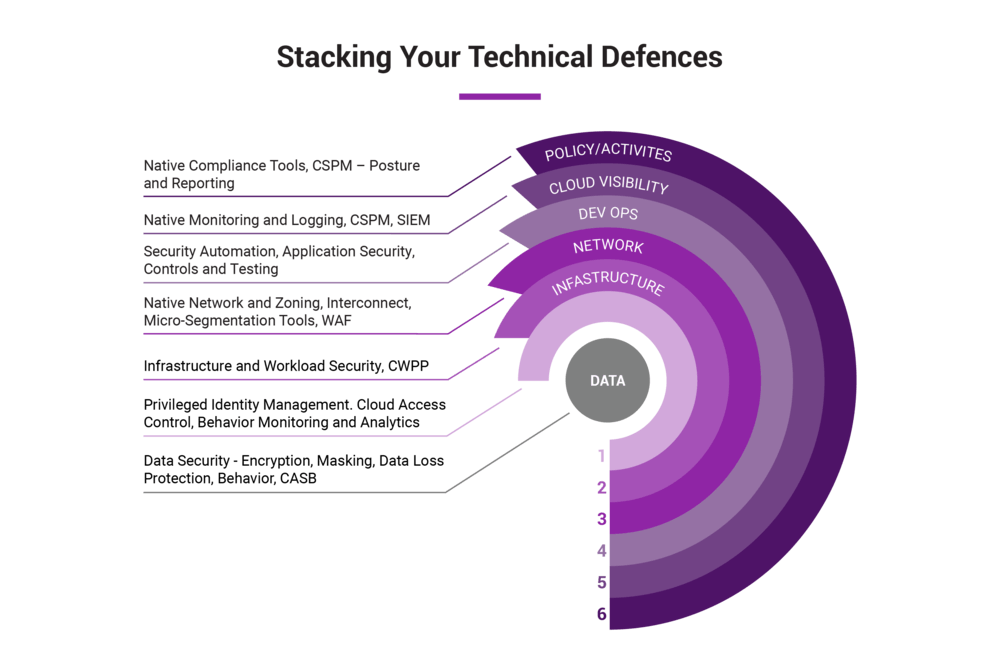
Abusing access privileges is one way for attackers to penetrate the corporate work environment after finding a vulnerable entry point. This threat is ubiquitous since the increase in remote work in the past two years.
Every subsequent step in your cyber security strategy trickles down from the risk inventory you conducted earlier. Revisiting the user directory regularly to manage user segmentation and privileges is imperative, much so in a cloud-native or hybrid environment.
Make sure the list of users is always up to date, and if employees switch roles or leave, you should be there to limit their access.
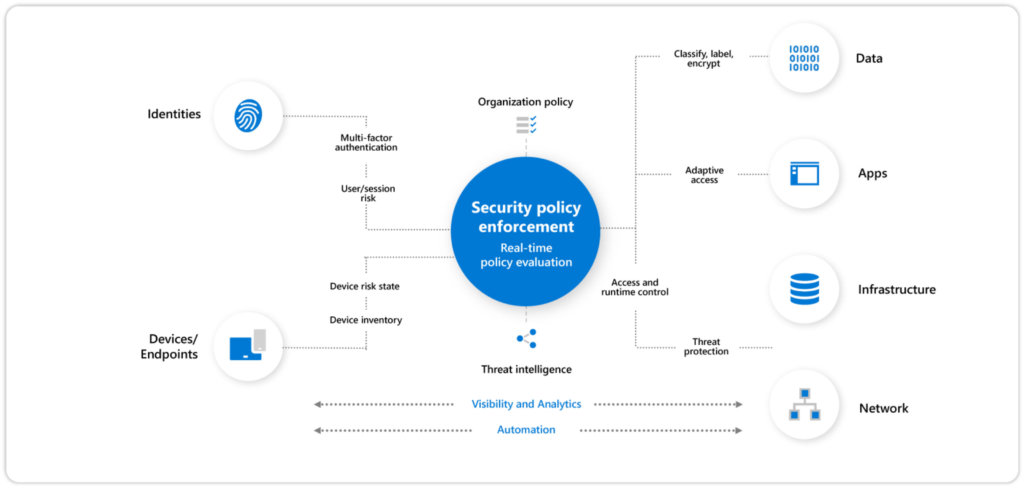
A good cyber security strategy is robust, comprehensive, inclusive, and automated. We recommend starting with the seven building blocks listed above if you care about protecting your data and CI/CD pipelines. Don’t forget to review and adjust your strategy to meet the ever-growing threats.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions