Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Updated 03.2024
A recent survey of nearly 2,000 IT professionals found that while most (85%) enterprises believe cloud technologies are critical to innovation, only 40% actually have a security policy in place. On top of this, almost half of the respondents using cloud infrastructure reported their engineers and developers circumvent or ignore cloud security and compliance policies, demonstrating the importance of automation and monitoring technology.
As expected, malefactors followed the corporate crowd. In 2020, cloud services saw a 600% rise in attacks on their services. In the last few years, cloud misconfigurations alone cost businesses almost $5 trillion and led to the release of over 33 billion user records. So it is no surprise to know that the cloud security market is expected to grow to a market size of over $68 billion by 2025.
Most organizations are more concerned with hitting product delivery deadlines than handling development security right from the very start, often relegating security toward the end of the production schedule. The rationale behind this false assumption is that dealing with security may cause production delays. While this assumption may have been correct years ago, new tools and services that smoothly integrate into the CI/CD pipeline have matured to a point where this is no longer the case.
Beyond baseless fears, the cloud infrastructure is a vast wonderland of powerful features and capabilities representing a complex weave of technologies that are impossible to secure without specialized solutions and solutions genuinely.
Before we list them, let’s review the most essential cloud security tool categories you need to know before you start.
Cloud security solutions break down into six primary categories that fulfill a particular role in protecting cloud databases, applications, and containers:
Table of contents
What do all these four-letter acronyms mean? And what type of solutions do you need to keep your cloud data and services secure? Let’s break it down.
Cloud Access Security Broker (CASB) tools encapsulate your on-campus or cloud-hosted security solutions. CASB can be both physical and digital solutions, which function as a stop-gap and gateway between users and cloud service providers.
This extends to IaaS, PaaS, and some (a limited amount) of SaaS environments. Boiled down, CASB plugs security holes by allowing organizations to extend their security policies beyond just the campus to the cloud and create cloud-only security controls as well. CASB tools are based on four base concepts:
If an organization’s highest priority is visibility into SaaS application usage and access, a CASB tool will be the ideal solution. These tools are the most mature and established in cloud security and comparatively broader than other cloud security tool types.
BitGlass is a newer CASB solution that helps users manage and secure cloud frameworks from both standard and Zero-Day malware and data leak threats. This includes real-time app management and threat detection for both managed and unmanaged cloud apps.
BitGlass also includes Data Loss Prevention and Access Control features to help ascertain what data is being accessed by which applications and manage the access controls accordingly.
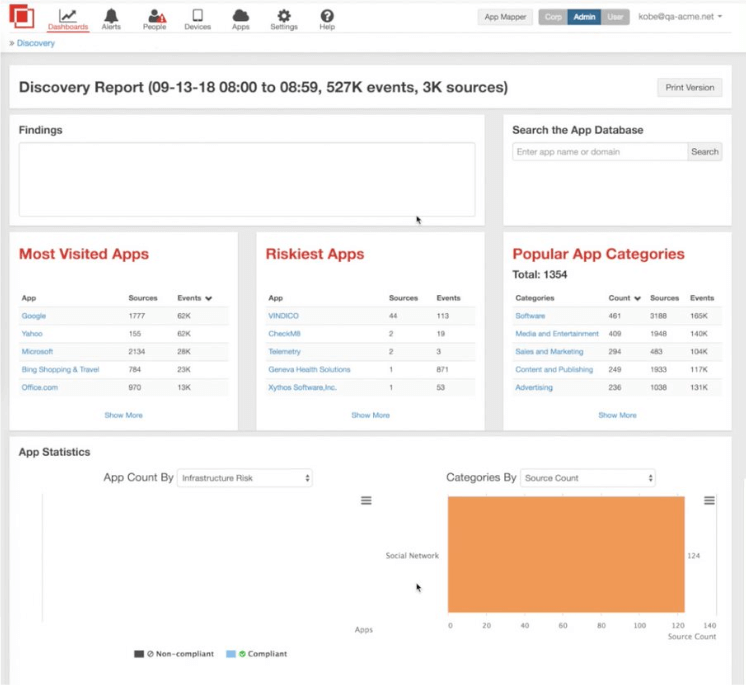
Cisco’s Systems Cloudlock offers an enterprise-focused CASB solution to safely transfer and manage users, data, and apps on the cloud.
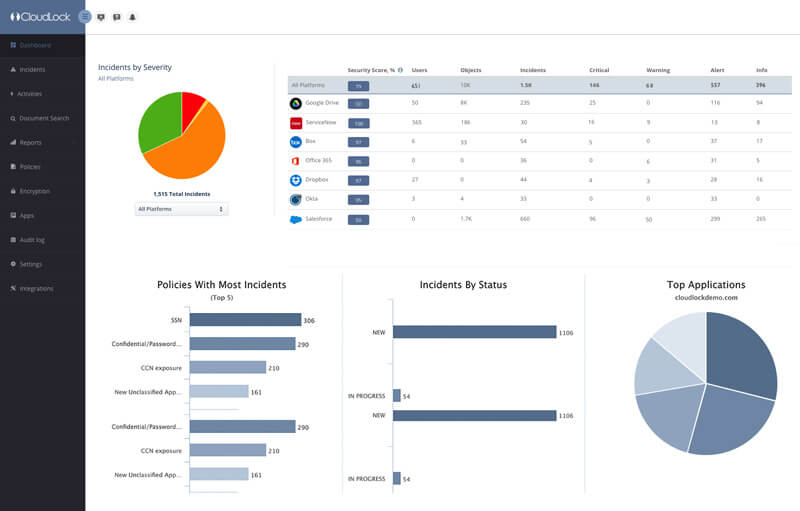
The ecosystem is API-based and assists with organizations meeting compliance regulations while combating potential data breaches. It features app discovery, secure and synchronized security policy adoption cross-platform, and active monitoring in real-time.
SAST tools employ technology to analyze source code and binary executables for patterns indicative of security vulnerabilities or suspicious activity.
The most popular use cases for SAST are:
Spectral specializes in discovering secrets, vulnerabilities, and configuration issues resulting from coding errors or lacking security practices. Spectral uses AI and Machine Learning algorithms to detect secrets and vulnerabilities with a high probability while reducing false positives. Unlike many other SAST tools, Spectral smoothly integrates into the CD/CI pipeline without slowing down the development pipeline.
You can also use Spectral to monitor public Git repositories used by employees to detect accidental or malicious commits of company assets to public repositories.
Spectral can also be used to monitor public Git repositories used by employees to detect accidental or malicious commits of company assets to public repositories.
This open source tool detects various security vulnerability patterns like SQL Injection, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), XML eXternal Entity Injection (XXE), etc.
Security code scan offers a CI/CD integration as well as a Visual Studio plugin.
SASE solutions offer a more generalized approach to cybersecurity for IT and cloud infrastructure. It is a newer approach that features advanced policy management and compatibility with enterprise and modern business needs alike.
SASE tools allow IT professionals to connect and secure their organization’s cloud resources without the need for physical hardware. SASE offers a multi-tier security approach for both businesses and customers, simplified by combining several standard cloud security features into a unified function.
Cato’s SASE tool is a cloud-based security tool featuring a combination of SD-WAN, a network security solution, and support for a variety of cloud applications and mobile devices.

Through a centralized hub, IT professionals can efficiently monitor, designate, and enforce security protocols across their organization’s network and assist with cross-team productivity. Cato SASE also provides a hands-off service that keeps dependencies and components up-to-date and is scalable without constant maintenance.
Perimeter 81 offers an identity-driven, edge-to-edge SASE platform that is easy to set up and functional without hours of configuration and tweaking. It allows organizations unified cloud management and several advanced security controls that cover both the cloud and on-campus network activities.
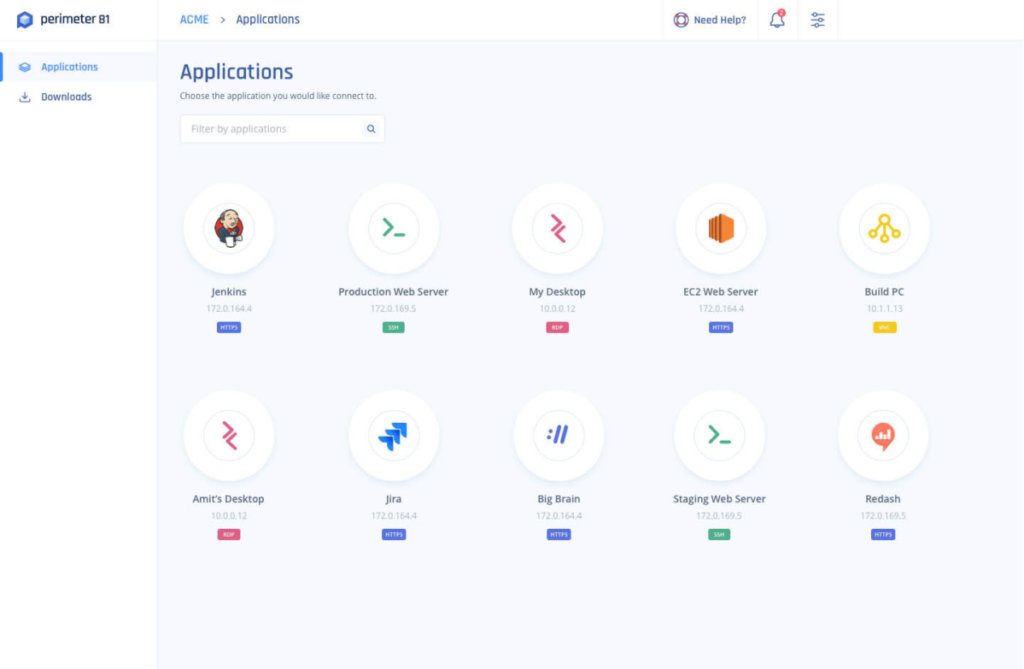
Perimeter 81 also offers a Sandbox to isolate potentially dangerous unknown files and DNS and SaaS security.
CSPM tools are a good choice for organizations oriented around Infrastructure, Software, and Platform as a Service (IaaS, PaaS) and looking to automate security management. Unlike SSPM solutions, CSPM tools focus on controlling access to cloud infrastructure tools deployed and employed by an organization. These tools are relevant for organizations in the process of migrating their operations to a cloud service.
CSPM tools excel at helping organizations become and remain security standard compliant, with easy configuration and deployment. CSPM tools operate by consistently seeking out misconfigurations and making any necessary changes automatically. These solutions are ideal for enterprises focused on detecting, assessing, logging and reporting, and automating issue remediation.
Fugue is an enterprise-oriented, cloud-based CSPM solution designed with engineers in mind to offer overarching visibility on a company’s security posture. Fugue is focused on maintaining compliance standards and provides an API for straightforward implementation.
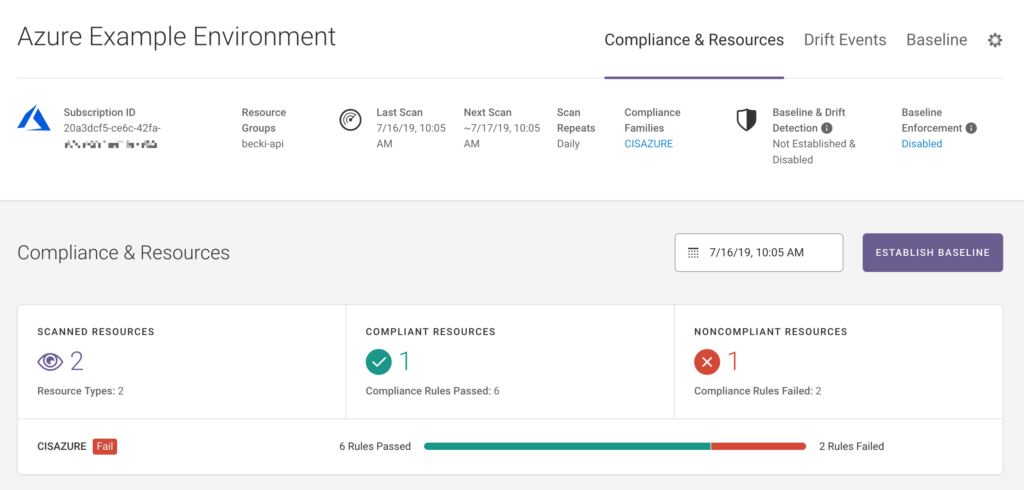
Fugue constructs a model of an organization’s public cloud infrastructure to offer full visibility and real-time detection of shifts or threats. The tool also includes reporting and data analytics capabilities from the first launch.
XM Cyber is a security tool focused on maintaining control over an organization’s security posture. It is designed to show a user the network as potential hackers would and offers remediation plans based on an asset’s priority within an enterprise’s cloud infrastructure. The CSPM also includes simulations of attacks to allow clients to find potential weak points.
CWPP security tools are enterprise workload-focused cloud platforms that offer protection to both physical and digital assets, including containers, virtual machines, and serverless workloads.
Due to organizations’ frequent reliance on legacy apps and frameworks, a complete move to the cloud is usually more trouble than it is worth. CWPP solutions bridge the security gap between legacy components and those on the cloud. They offer discovery and management of already-deployed workloads on your public and on-campus cloud ecosystems.
CWPP solutions are great for any organization that is not centralized in one location but is spread out geographically or digitally by design and needs to maintain universal security standards. They differ from other cloud security solution types in that they rely on gathering information from operating systems instead of APIs.
Illumio Core is a CWPP solution that emphasizes preventing the lateral movement of data. It allows for control over an organization’s data hubs and cloud environments to monitor and gain insight into application interactions within cloud environments.
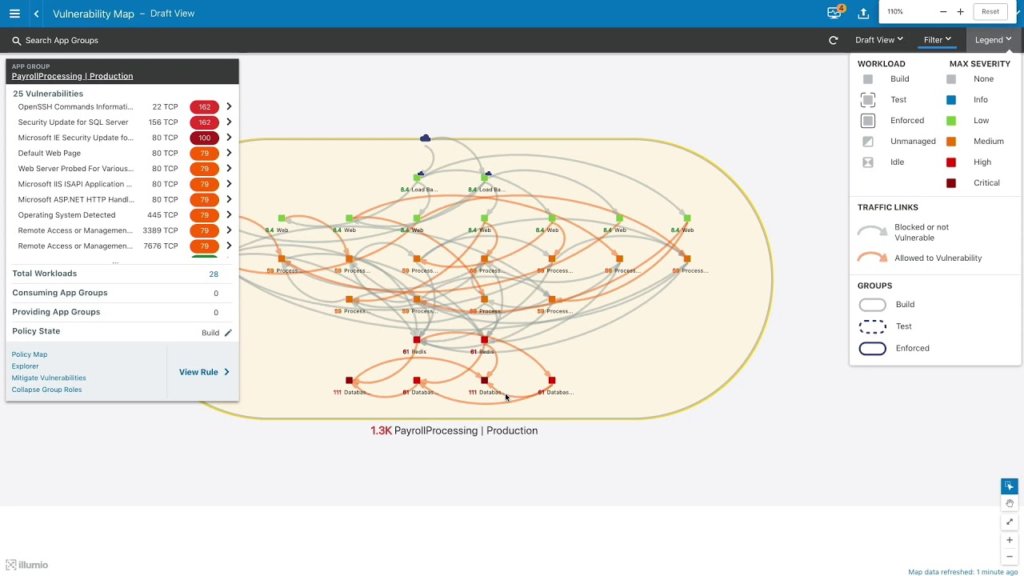
This includes how virtual and physical machines are communicating and accessing data and the cloud infrastructure overall. Illumio Core also provides segmentation policies that create optimized controls for each application and templates from already-tested setups.
Orca Security is a SaaS-based workload protection tool for AWS, GCP, and Azure-based cloud networks focused on removing security gaps and reliance on third-party agents.
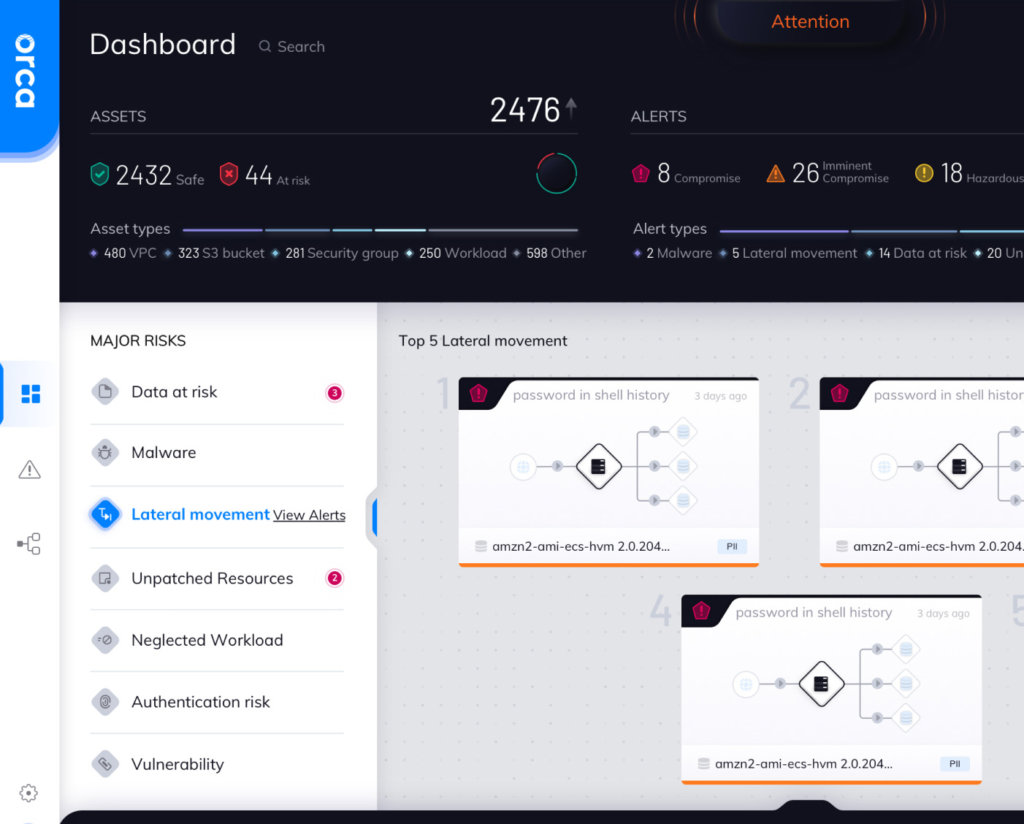
The SideScanning feature casts a wide net over potential vulnerabilities, misconfigurations, malware, problematic passwords, high-risk data, and lateral movement risks.
CIEM is a cloud security solution that excels at managing the complicated security situation that Identity and Access Management (IAM) creates.
CIEM tools are focused on the identity lifecycle and access governance controls, which are intended to reduce unnecessary entitlements and enforce least-privilege access for users across the cloud network. This also limits the need for intervention necessary to detect and remove over-privileged user access, which can be exceedingly time-invested.
These tools provide deep visibility into data access vulnerabilities and entitlement risks. Unlike other solution categories, which often offer a more broad, holistic view of an organization’s cloud network. Organizations struggling with data access complications and looking for complete management and control over multiple policy types would benefit most from CIEMs.
C3M Access Control is a CIEM solution that manages and enforces access privileges across the cloud infrastructure to prevent over-provisioned access and potential insider threats.
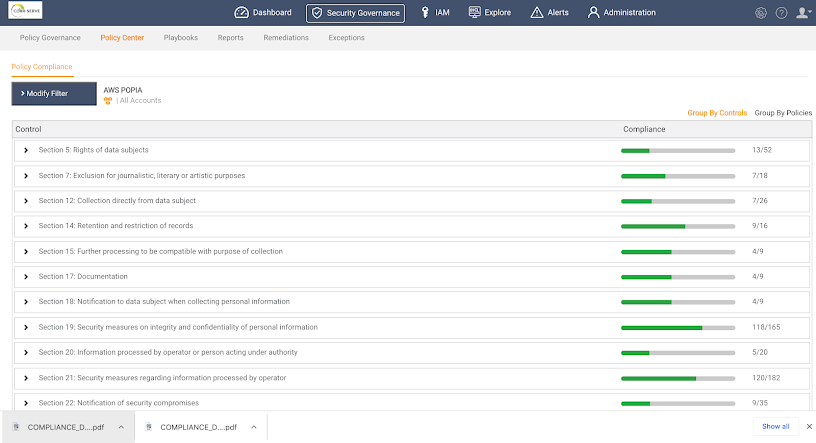
The C3M tool sorts through the identities on the organization’s network and highlights which cloud resources they have access to, which accounts have too much access, and which violate best practices. It can also remediate issues with unused account access to plug any potential vulnerabilities at the source.
CloudKnox is a quick and efficient CIEM tool for discovering who is doing what, where, and when across an organization’s cloud network.
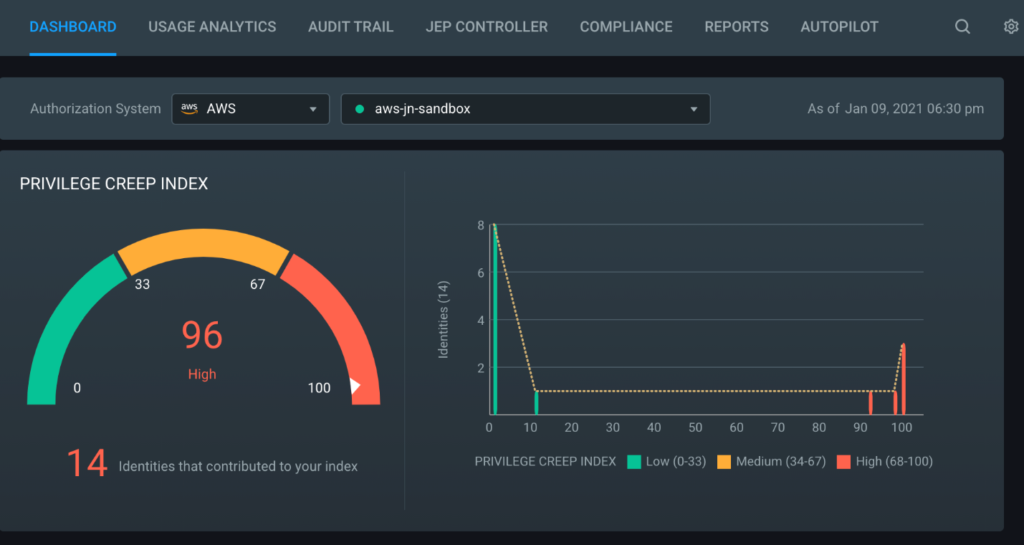
It offers cloud monitoring with real-time reporting of anomalous activity and management of least-privilege access policies and one-time access exceptions. CloudKnox also supports immediate threat response and the most popular private and public cloud platforms and services.
Cloud network reliance and usage are spiking to record levels as day-to-day business activity becomes increasingly dependent on a growing number of IaaS, PaaS, and SaaS cloud services.
This has thrust cloud security into the spotlight, along with the necessity for enterprises and public organizations to protect their cloud activities.
The slightest mishap in configuring your cloud infrastructure and reliance on cloud platforms’ built-in security to protect your cloud assets can lead to significant breaches. SAST is not a sassy acronym. It’s a vital security model that plugs organizational leaks. Tasty secrets such as Passwords, API keys, security tokens, and other secrets are just waiting to be exploited by malicious actors. And not unlike a leaky ship, leaking information can sink your organization.
This is why it is vital to invest in cloud security tools to proactively find and eliminate vulnerabilities in your infrastructure, both physical and virtual.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of