Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Dirty COW, a seemingly light-hearted name, masks a severe Linux privilege escalation issue. This bug has affected many older Linux systems, which is concerning given that 41% of web servers run on Linux.
Despite widespread patches in distributions like Ubuntu and Red Hat, Dirty COW remains a threat, particularly to outdated systems. As a significant security flaw, it poses risks to various devices and servers even in 2024.
In 2023, this vulnerability was exploited in a notable cyber attack on Magento 2 eCommerce sites, showcasing Dirty COW’s continued threat to systems, especially those with outdated Linux kernels. More on this below.
Now to the critical question – are you at risk? If so, how can you protect yourself from Dirty COW?
Dirty COW (assigned CVE-2016-5195) is a privilege escalation vulnerability in some versions of the Linux Kernel that affects Linux and Android systems that run versions of the Linux Kernel predating 2018.
By exploiting the Dirty COW vulnerability, attackers gain write access to otherwise read-only memory mappings. This enables them to elevate their account privileges in the system by, for example, overwriting a user’s UID in /etc/passwd or making changes to existing setuid files to include instructions to elevate privileges.
Disclosed in October 2016, the Dirty COW vulnerability lurked in the code of the popular operating system core since 2007. At the time of disclosure, this vulnerability affected most Linux distributions and kernel versions. The distributions affected included:

One of the only privilege escalations exploits to be adopted by the community, the Dirty COW exploit derives its name from the kernel feature it exploits – copy-on-write (COW).
The vulnerability plagued the Linux kernel since version 2.6.22 (which was released in September 2007), but has been since patched in versions 4.8.3, 4.7.9, 4.4.26, and newer of the Linux kernel. That said, there is ample evidence of Dirty COW employed by malefactors in the wild to take over unpatched servers, even though the execution of the exploit in itself leaves no trace in web server logs. It also serves as a component in Android malware discovered in the wild.
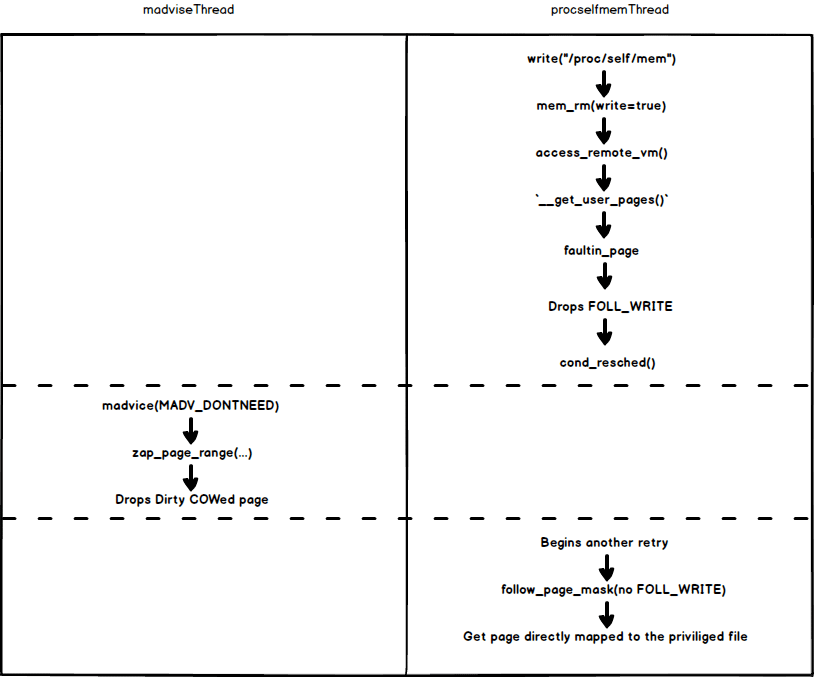
The Dirty COW exploit is a case of a race condition vulnerability exploitation. In this case, attackers took advantage of the root permissions the kernel gets when running and created the race condition that enabled the privilege escalation from a low-level user to a user with full root privileges.
When a running software program encounters multiple code paths that execute concurrently, it can “confuse” the software and create a “race” between the code paths, causing them to conclude in a different order than anticipated, thus resulting in bugs and unexpected application behavior.
In the case of the Dirty COW exploit, the race is between two operations: one operation writing to COW memory mappings and another continuously disposing of them. When these operations repeat non-stop, the kernel can be confused into writing data to read-only memory mappings instead of first creating a private copy of the data. Alternatively, the target system will crash.
If you want to dive into a blow-by-blow description of the exploit, Dirty Cow Demo offers a great visual explanation that details how Dirty COW tricks the kernel into letting it write to read-only memory mappings.
The basic “In the Wild” Dirty Cow exploit is a building block for multiple POCs you can download and test. With the ability to write data to read-only memory, you can:
Although it’s a patched Linux kernel bug, attackers continue to use it in their activities. This ongoing threat makes it important to be aware of Dirty COW, even years after its initial discovery and patching.
In mid-2023, Akamai’s security team found that attackers targeted eCommerce sites using Magento 2. The attack, named Xurum and traced to Russia, used the Dirty COW exploit for privilege escalation on Linux servers. This approach was effective on servers running outdated, unpatched kernel versions.
Cyberattackers often use a trial-and-error method to exploit known vulnerabilities, even if they’ve been patched. They focus on these weaknesses because unpatched vulnerabilities remain a major issue in enterprise IT and DevOps. These unpatched issues contribute to about 60% of all data breaches, highlighting their significance in cybersecurity.
The Dirty COW exploit is dangerous, but it’s easy to defend against, especially if you haven’t patched the vulnerability for a while, or practiced security hardening.
But how exactly do you defend against and prevent Dirty Cow exploit attacks? Here are the top 3 things you can do.
To protect against the CVE-2016-5195 vulnerability – aka Dirty COW – it’s vital to control server access and permissions. This exploit requires the attacker to have the ability to write and execute code on the system.
Ensuring that proper access controls and credentials are in place is a key defense. Problems like secrets sprawl – which is the uncontrolled distribution and exposure of sensitive information like passwords, API keys, and credentials across a system – can be the gateway for Dirty COW exploits to occur.
Tools that perform automated scanning for exposed secrets like Spectral can help mitigate secrets sprawl. How? Maintaining robust access controls and credentials management prevents unauthorized code execution and system compromise.
To safeguard containerized applications from Dirty COW exploits, it’s important to regularly scan your Infrastructure as Code (IaC) and containers. Dirty COW can modify read-only data even within containers. You can automate this process by checking the kernel version in your CI/CD security pipeline.
You can automate the discovery of servers and containers vulnerable to Dirty COW by simply checking the kernel version of the image file you intend to deploy as part of your CI/CD pipeline. If you use Tools like Ansible, offer scripts to check for Dirty COW vulnerabilities.
Automating kernel patching is key in responding to vulnerabilities like Dirty COW. Initially, manually patching affected systems as soon as a fix is available is essential. However, manual patching can be repetitive and time-consuming. The better approach is automated live patching. Many Linux distributions offer this service to their enterprise customers.
For example, Ubuntu’s Livepatch service automatically applies security patches without rebooting the system. This method ensures your systems are always up-to-date, reducing the risk of security breaches.
The Dirty COW may be old, but that doesn’t stop malefactors from trying to milk it for privilege escalation execution on compromised systems. Moreover, it has inspired and served as a base for countless POCs and other dangerous exploits like Dirty PIPE.
The story of the Dirty COW vulnerability, its severity, and the length of time it spent lurking in the shadows of the Linux kernel code before it was fixed make one thing crystal clear: scanning your code and infrastructure for third-party vulnerabilities is vital to the delivery of secure code and applications.
Spectral detects the Dirty COW and other exploits that may be present in your systems and provides a centralized and contextual view of all the vulnerabilities that may impact your application and infrastructure. The Dirty COW exploit detection script is just one of over 2000 customizable vulnerability detectors that come bundled into the Spectral platform, empowering your DevSecOps teams with auto-remediation and actionable mitigation suggestions. Request a demo today.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions