Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
High-velocity software development today is close to impossible (and most certainly not sustainable) without DevOps. The migration to the public cloud, along with increasing regulatory demands, and other factors made application and code security as vital as DevOps. Thus were born the practices and frameworks of DevSecOps.
The value of DevSecOps is evident and clearly understood by technologists. As many as 76% of technologists believe that “a DevSecOps approach is essential for organizations to effectively protect against a multi-staged security attack on the full application stack.” So it’s not surprising that, according to the same survey, 43% of organizations have already started implementing a DevSecOps approach in their IT departments.
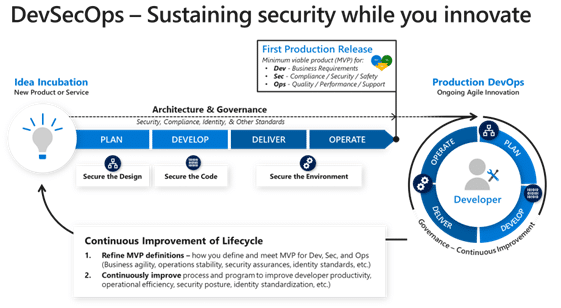
But what does DevSecOps adoption actually entail for developers and DevOps engineers? And how do you employ the OWASP DevSecOps Maturity Model to measure progress in your DevSecOps strategy?
DevSecOps, an evolution of Development Operations (DevOps), focuses on integrating cybersecurity seamlessly with software development. This approach signifies a higher level of DevOps maturity, emphasizing the integration of security into every phase of the Software Development Life Cycle (SDLC). It involves equipping development teams to create secure code and address security issues like common security misconfigurations promptly.
Key elements of DevSecOps include automation, cross-functional teamwork, and adopting “shift left” and “continuous everything” methodologies. Successful implementation hinges on the collaboration among security, IT operations, and software development teams, aiming to embed security scanning, testing, and validation throughout the SDLC.
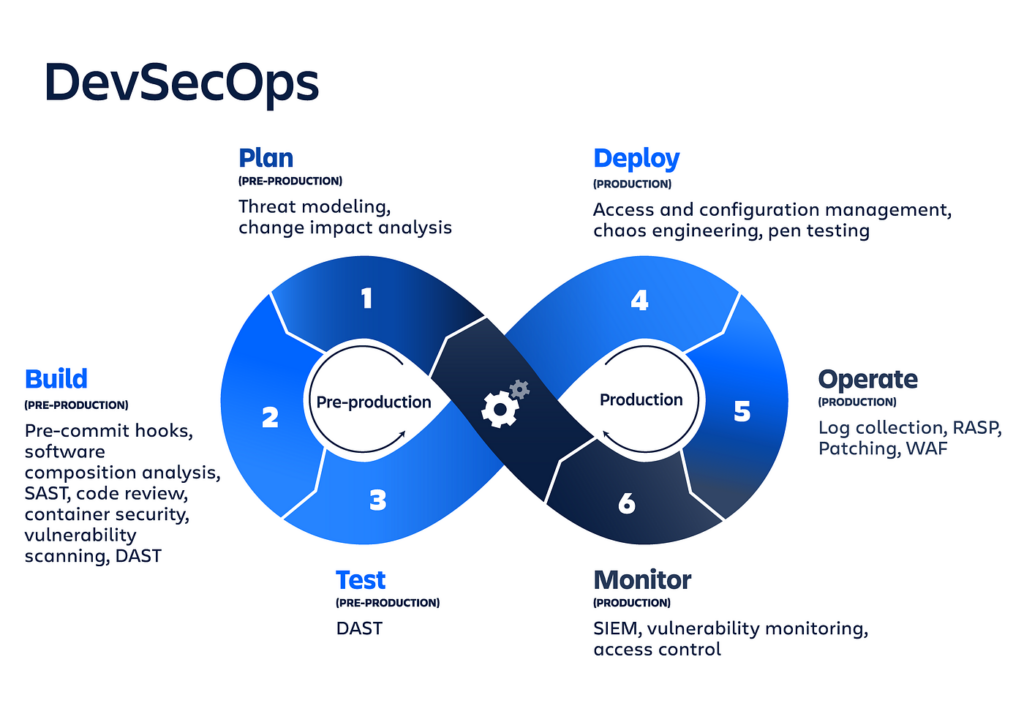
The DevSecOps Maturity Model (DSOMM) was introduced and developed by the OWASP foundation to serve as a set of framework for implementing code and application security measures by using familiar DevOps principles and strategies.
There are challenges and hurdles on the way to DevSecOps maturity. These challenges include fragmented and siloed toolsets and data, as well as numerous challenges in promoting accountability and the cultural shift left throughout the organization.
One of the reasons that the framework for integrating security into DevOps is designed as a maturity model is that maturity models are a concept that is familiar to executive management and non-technical stakeholders. As such, a maturity model presents a way to communicate the value of DevSecOps through a “story” featuring the key components of any application security initiative: people, process, and technology.

Adopting DSOMM offers several key benefits, central to which is the ability to measure and track progress in DevSecOps integration.
Key advantages include:
The OWASP DSOMM outlines key sub-dimensions for achieving DevSecOps maturity, blending foundational practices with advanced security integration:
Technical and operational aspects include:
Using the OWASP DSOMM’s interactive matrix, organizations can visually assess their progress in these areas, guiding their journey to integrated DevSecOps maturity.
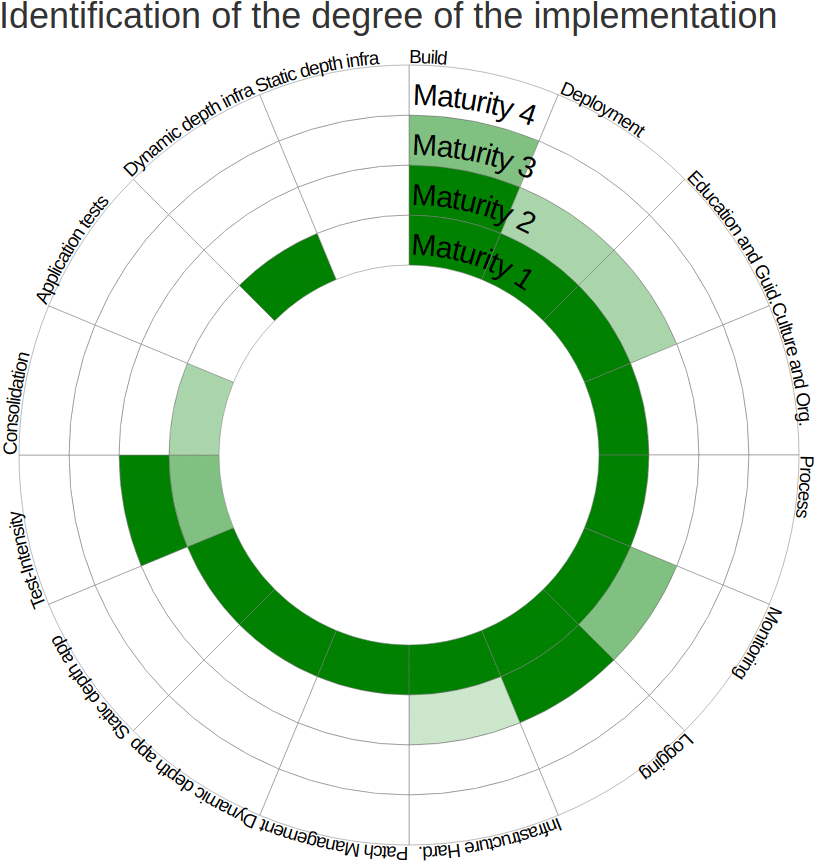
The DSOMM framework consists of four levels of DevSecOps maturity. Each level represents a distinct stage in the evolution of security integration, ranging from basic awareness and ad-hoc practices to advanced, fully integrated, and automated security processes. These levels provide a roadmap for organizations to systematically enhance their security posture within the DevOps framework.
Level 1 of the DevSecOps Maturity Model is where organizations start incorporating fundamental security practices into their development workflows. This initial stage features teams working independently with manual processes and a reactive approach to security, often addressing issues only after they arise in production.
This level lays the essential foundation for more sophisticated DevSecOps practices, integrating security into all development and operational stages.
In Level 2 of DSOMM, organizations begin to effectively blur the lines between security, development, and operations. This stage is marked by the adoption of standardized DevSecOps tools, significantly automating tasks that were once manual and neglected. Remediation processes become more efficient, and the adoption of practices like Infrastructure-as-Code extends DevSecOps across entire departments.
This progression signifies a deeper integration of security into the development lifecycle, enhancing the overall security posture of the organization and paving the way for more proactive security practices.
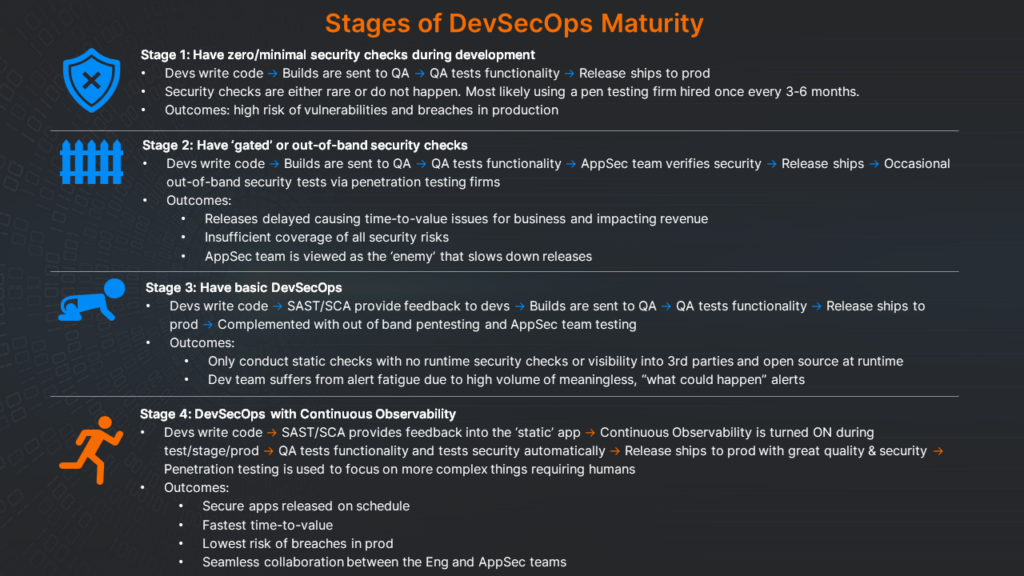
Achieving Level 3 in DSOMM signifies a pivotal shift in making DevSecOps a central organizational strategy, promoting enhanced team collaboration and a robust security culture. It brings comprehensive risk assessment, threat modeling, and security testing into every stage of the Software Development Life Cycle (SDLC).
At this level, organizations adopt a mature, proactive stance in DevSecOps, thoroughly integrating security measures throughout their software development and operations.
Achieving Level 4 in DSOMM represents the zenith of DevSecOps expertise, where security is a fundamental element of every stage of the Software Development Life Cycle (SDLC). Organizations at this level are distinguished as cloud-native innovators, extensively automating processes and integrating technologies like AI/ML to bolster SDLC security while adhering to strict data privacy and software supply chain security norms.
At Level 4, organizations exhibit a sophisticated, proactive stance, deeply embedding advanced security measures and practices across their development and operational frameworks.
The DevSecOps Maturity Model brings order to the chaotic process of integrating security into DevOps. With a leveled approach, and checklist-like structure, the model offered by OWASP can be easily customized to promote the maturation of DevSecOps in organizations.
One of the basic demands for completing the first level of DSOMM maturity is the integration of Static Application Security Scanning (SAST) and automated Secret Scanning of the source code and related assets. With SpectralOps, code secrets, keys, as well as cloud misconfigurations and bad security practices are stopped before they reach production environments, and resolved with a developer-first approach in a developer-friendly environment.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions