Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
The pressure to ship software faster to meet market demands is compromising security in a big way. As cyber criminals find ways to use the glaring disconnect between developers and security policies, companies consider security a necessity rather than a compliance measure.
As a result, 2022 studies show that 68% of companies are shifting towards security and making developers share responsibility for a secure software development lifecycle. Interestingly, building secure software goes beyond security–It mandates a systematic procedure for development, enabling teams to respect their timelines for developing software.
This article explores a secure software development lifecycle and its significance. We will also list a step-by-step process and best practices for achieving this approach.
In a single line, SSDLC means incorporating security in every stage of a software development lifecycle.
The SSDLC is typically a framework for including security considerations across the development process, from planning and design to building, release maintenance, and updates. It means that along with functional specifications, developers must also learn and implement security best practices when creating a product. This helps you identify and fix issues that could become a security nightmare in the earlier life cycle stages.
Specific tasks to undertake under each stage include:

Back when security testing took a long time to complete, enterprises would release the software out in the market before the IT security team could check the application’s security posture in a production environment. One challenge here is that when a security loophole is identified, it is already out in the open for everyone (who’s looking) to see and exploit. Besides causing reputational damage, this approach proved very expensive. A 2022 report estimates the cost of poor software quality to be $2.41 trillion.
Here are some of the most significant software attacks in recent times:
Now, companies are moving towards a secure SDLC instead of relying on security patches to fix vulnerabilities. By integrating security into your lifecycle, you improve your security posture and deliver higher-grade software.
But anytime you mention SSDLC, there is a pressing question: why is it needed when you have SCA and SAST tools tackling vulnerabilities? These new security checkpoints will complement the security team’s regular testing exercises. Today, hackers target CI/CD pipelines, public-facing assets, cloud spaces, etc. This calls for a holistic approach to security.
Here are some of the SSDLC benefits developers can enjoy:
Each phase of the SDLC needs to feature a set of security practices so that the software you ship will have a minimal risk surface for attackers to target. Further, SSDLC gives you layered security cushioning.
Let’s look at the steps in detail.
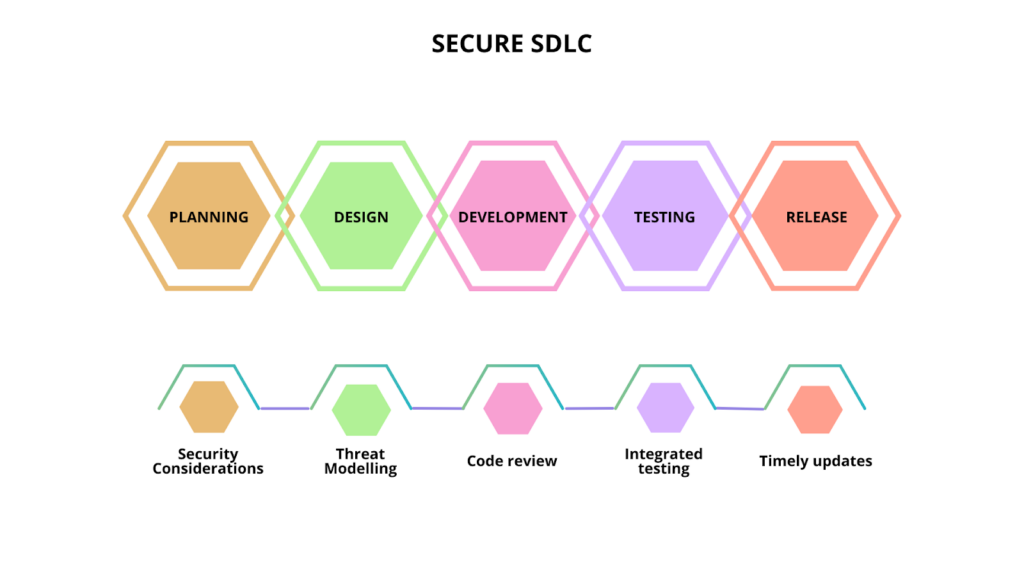
The first step of any software development lifecycle involves bringing together all the stakeholders, like a technical team, industry experts, and the sales department, to finalize a preliminary plan and draw up a list of requirements. These inputs are used to build the first blueprint of the project to conduct a feasibility study in terms of technical, operations, and financials.
The technical feasibility report outlines frameworks, languages, tools, and technologies. It is during this assessment that you consider security requirements. Some frameworks may need security trade-offs or compromises, so you must thoroughly evaluate all aspects of the project and their respective security implications.
Key points to discuss at this stage include:
In this stage, developers consider their software’s different components and what ideal architecture framework they can use to bind them together. The architecture should address your algorithmic requirements. Introduce security at this stage to avoid an extensive overhaul later. Once the architecture is defined and security incorporated, you will not have to shake up the basic structure of your software.
The designing stage is also critical for a secure SDLC. At this stage, decide which external systems your software will interact with and how, and outline how data will flow between the different components.
Key points to discuss at this stage:
All your plans and architecture specifications turn into code at this stage. You must follow the industry-defined coding standards and enterprise-level policies to ensure consistency and security. You also introduce open-source and third-party code blocks at this stage. Running code review exercises and testing practices is important to ensure no vulnerabilities seep into your source code.
With supply chain risks becoming one of the leading cybersecurity threats, secure SDLC holds significant importance. It helps uncover hidden security gaps and corrupted lines of code.
Key points to discuss at this stage:
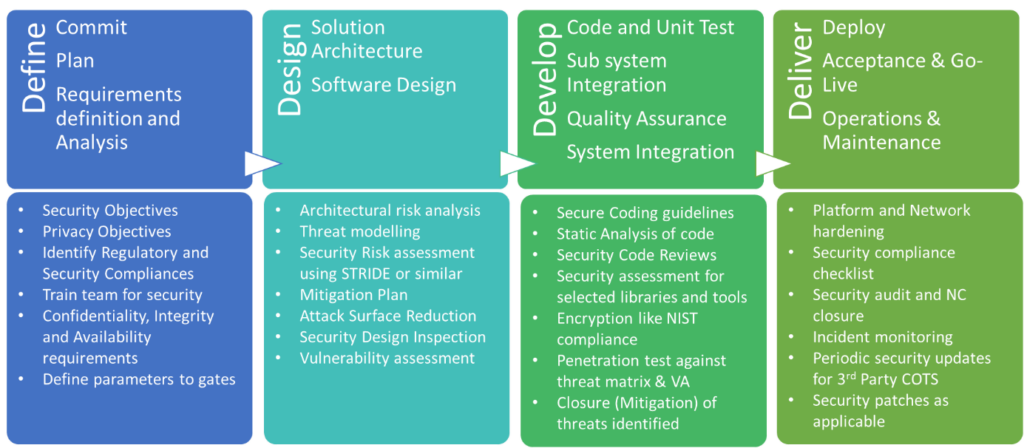
While code reviews and scanners look at the lines of source code, software testing is slightly different: It evaluates your software and its functioning before pushing it to production.
This is the stage where you find most of your defects, flaws in logic, and open spots that can be exploited. Software that goes through this stage is of high quality and secure. You can achieve this by fixing issues and re-testing deployment. This cycle should be repeated until the results exceed expectations.
Key points to discuss at this stage:
Once you release the application into the market, your litmus test begins. It is a test that will continue as long as your software is out there. This makes it essential to have a continuous security screening practice running in the background. Although you may have multiple testing strategies, reviews, and quality assurance tasks, there is a little chance of missing something.
Key points to discuss at this stage:
Software security is one of the biggest threats in the digital world. As attackers become more innovative, you must stick to your basics and be even more stringent about security. SSDLC helps with that by providing a methodical way to secure your software, optimize your entire lifecycle, and save costs.
Even better, use this framework alongside automated tools like Spectral–a security platform designed to let developers drive SSDLC by enabling teams to continuously scan, detect and track suspicious assets within your system. Spectral helps ensure your application can withstand any attempts to break in. Create a free account today.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions