Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Modern companies are rapidly adopting cloud applications and services due to scalability, cost savings, and faster time to market. DevOps teams and developers must deliver fast, secure code while protecting secrets and log files, creating a growing concern over the security risks of this digital transformation.
According to a recent report, more organizations are adopting security as code (SaC) practices, with 62% of respondents citing it as a priority. This figure shows the importance of implementing security as code in today’s digital landscape.
In this blog, we will explore the concept of security as code, its benefits, and how to get started implementing it.
Security as code is an approach to integrate security measures into the software development life cycle (SDLC). It involves automating security checks and tests into the development process to catch potential vulnerabilities early and prevent them from being deployed into production environments. This practice ensures that security is not an afterthought. Instead, it is built into the development process from the beginning.Security as code is not just for security teams but also for developers and operations teams. It provides a common language and set of best practices for all parties involved in the SDLC. By integrating security into the development process, teams can work collaboratively and address security issues proactively, reducing the likelihood of security breaches.
Security as code consists of four main components:
To effectively implement security as code, it is crucial to understand the secure software development lifecycle and evaluate how to integrate security into your DevOps environment. Here are some steps to improve your understanding of the Secure SDLC:

The Software Assurance Maturity Model (SAMM) is a framework for tailoring a software security strategy to an organization’s specific risks. While some find it complex to execute, there are simple questions that can help quickly evaluate the security component of a DevOps process, covering each stage of the development cycle. For example, here are some of the questions:
Answering these questions allows you to decide the maturity level of the organization’s security efforts. If the answers are negative, you need to make necessary changes right away to avoid unforeseen costs and effort.
Automation is an essential step in embedding security into an agile sprint. Here is how you can make it happen:
You can establish a dedicated DevOps pipeline to automate security checks and tests at various stages of the development process, including code scanning, vulnerability assessments, and configuration checks. For example, you can use Jenkins, GitLab CI/CD, or Azure DevOps to automatically perform security checks like SAST (Static Application Security Testing) and DAST (Dynamic Application Security Testing) during the build and deployment stages.
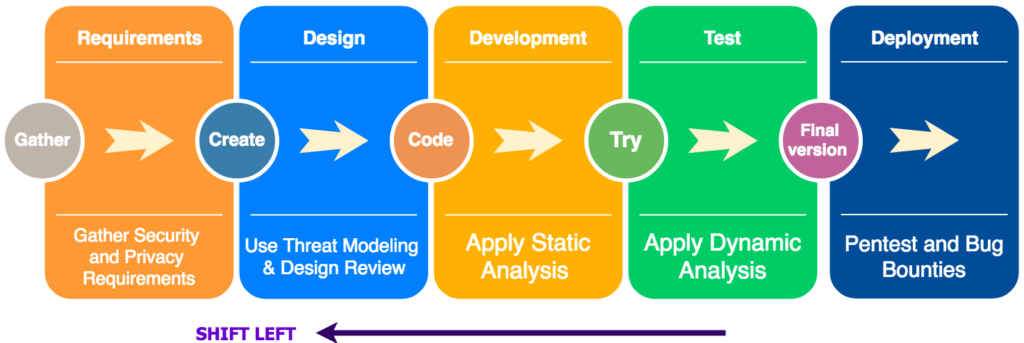
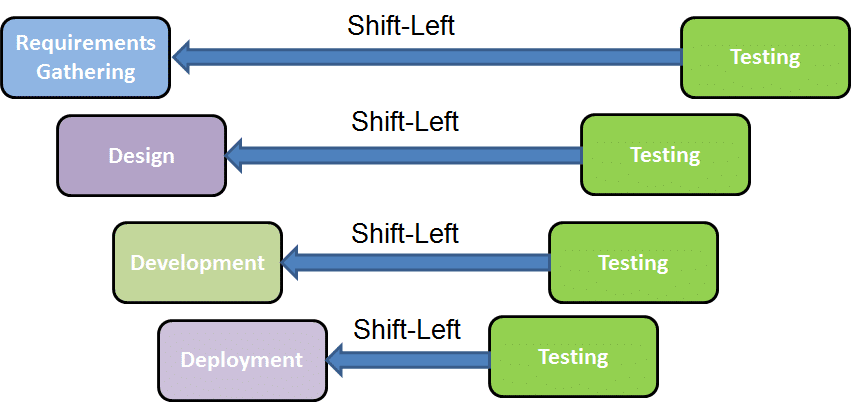
‘Shift-left’ is the concept of incorporating security practices early in the software development lifecycle. It helps you identify issues early and reduce the risk of vulnerabilities propagating into production. For example, using code analysis tools is one of the easiest ways to get immediate feedback on security vulnerabilities while developers write code.
You can use IaC to enforce the same security configurations and best practices across all environments. Tools like Terraform or AWS CloudFormation are popular options for defining infrastructure resources and security controls in code.
Identifying security requirements early in the SDLC allows organizations to embed security into their development practices while reducing costs effectively. Here are some actions you can take to achieve this.
You need to define specific security requirements at the beginning of each sprint. For that, you can use resources such as the OWASP Application Security Verification Standard (ASVS) 2.0 to guide the identification and definition of security requirements. It provides a specific checklist of security controls and conditions for your project.
Transforming identified security requirements into actionable security stories allows developers to prioritize and implement them alongside functional requirements. These stories should include security objectives, acceptance criteria, and expected outcomes. If your team lacks experience in this area, it is always best to consult security professionals to ensure that stories are well-defined, granular, and measurable.
The OWASP Proactive Controls lists essential security practices that can help developers build more secure applications. Organizations should encourage developers to use these controls in development to ensure security is considered.
You can utilize SAST/DAST tools to enhance the security of your build process by regularly integrating the results of these scans into your sprint bugs list. If there are frequent changes in the code, consider adjusting how you use SAST testing since many false positives can emerge when there are significant code changes.
SonarQube, Checkmarx, Veracode, OWASP ZAP, and Burp Suite are popular security scans and dynamic security testing tools. If you can’t afford these tools, try open-source alternatives like the OWASP Dependency Check.
The least privilege principle is a fundamental security concept that states that users should only get the permissions necessary to perform specific tasks assigned to them. Get started and implement the least privilege principle using these actionable tips.
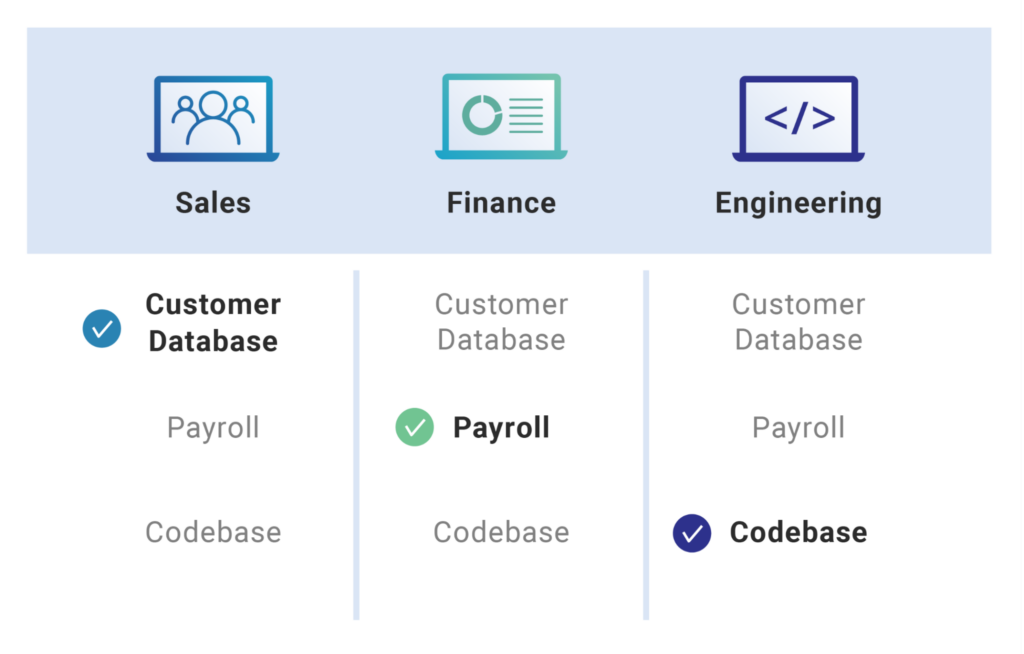
Rather than giving the same access to everyone, you can group users based on your roles and assign different permissions to those groups. This strategy is mainly for developers who are working on the system, and there are specialized tools you can use for this.
For example, if you use AWS resources like EC2 and S3, every user does not need access to your EC2 instances. You can group users who require EC2 access and others to another group using AWS Identity and Access Management (IAM). Similarly, Azure Active Directory (Azure AD), Okta, and OneLogin are other popular tools.
Multi-factor authentication adds an extra layer of security by requiring users to enter a unique code generated on a separate device alongside the password. With MFA, you can prevent unauthorized persons from accessing the systems even if they obtain the passwords illegally. Google Authenticator, Duo Security, and hardware tokens are popular ways to implement MFA.
Code reviews are a crucial part of software development. It helps developers to identify and address security vulnerabilities before going into production. Here’s how you can implement effective code reviews for enhanced security.
Spectral ensures your code is high quality, which supports developers in building secure applications while maintaining velocity. Spectral automates code scanning to help devs catch issues earlier in the development process, then provides actionable remediation insights for vulnerability management. Request a demo to start stopping leaks at the source.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of