Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
If you prioritize long-term security and success, you should be analyzing your applications from the inside out. Enter Static Application Security Testing (SAST), a proactive method of identifying and addressing security vulnerabilities in an application’s source code before deployment.
SAST solutions analyze the source code of an application and use advanced algorithms and rule sets to identify potential security vulnerabilities, such as SQL injection, cross-site scripting (XSS), and buffer overflows. By running SAST tests at different stages of the development process, you can ensure that the applications you build are secure from the beginning. SAST tests should be efficient and accurate, designed for scalability, accuracy, and ease of use. Let’s dive deeper into how this works.
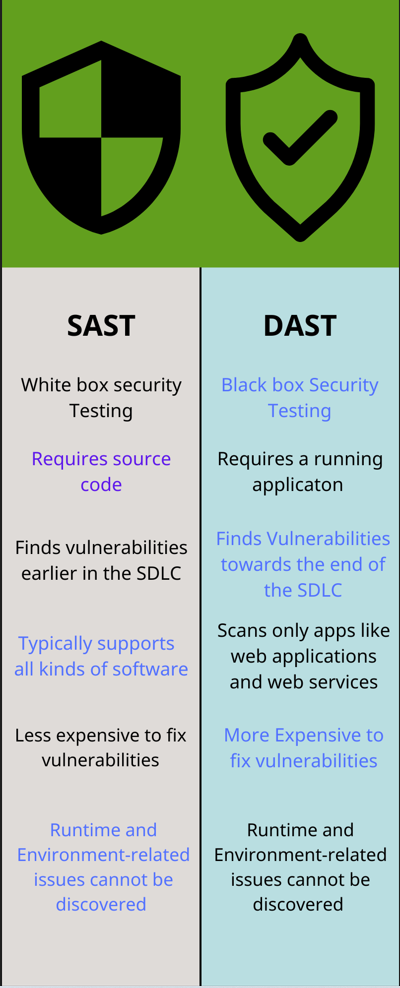
To understand SAST, it is important to distinguish it from other testing methods such as Dynamic Application Security Testing (DAST), which analyzes an application while running. DAST sends requests to the application to identify vulnerabilities in real-time. On the other hand, during SAST, code is scanned without actually executing the application. SAST tools analyze the code line by line to detect coding errors, security issues, and other potential vulnerabilities to prevent mistakes before the application is deployed into production. Both testing methods are often used together to provide a comprehensive assessment of an application’s security.
SAST should be performed at different stages of the SDLC to identify potential security risks and suggest best practices to ensure secure coding:

If you’re new to SAST, here are some key considerations before getting started and what to expect before, during, and after a SAST test:

Let’s look step-by-step at what these recommendations look like in practice. We’ll be using NodeJsScan, an open-source static security code scanner (SAST) for NodeJS applications. By following these simple seven steps, you can use SAST to quickly identify and prioritize security vulnerabilities in your NodeJS applications.
To install NodeJsScan, you need to clone it from the official GitHub repository. Download the latest release, then unzip the package to a directory of your choice. If you use the command line, then run the code below inside the desired directory.
git clone https://github.com/ajinabraham/nodejsscan.git
Using the command prompt, enter the following commands in order to create the virtual environment for the scanner.
cd nodejsscan python -m venv venv cd ./venv/Scripts pip install -r requirements.txt python manage.py recreate-db # Run once to create database schema
Run the scanner using the command below.
./run.sh
This will run the Nodejsscan web user interface at http://127.0.0.1:9090.
Alternatively, you could use the below Docker commands in the command line to run the application on Docker.
docker pull opensecurity/nodejsscan:latest docker run -it -p 9090:9090 opensecurity/nodejsscan:latest
Now you could either upload a zip file containing the NodeJS application or provide the git repository in the above web interface to scan for security vulnerabilities.
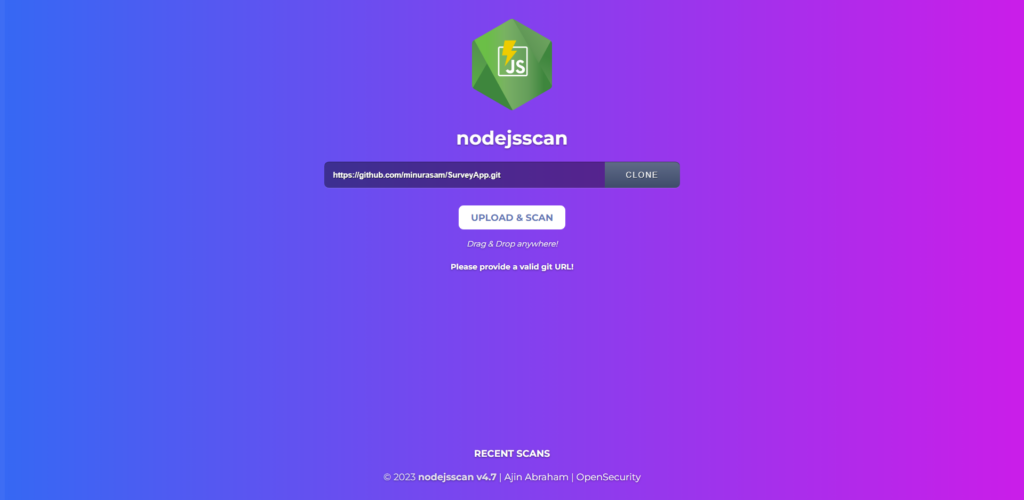
Here, we used a GitHub repository where the backend was built on NodeJS.
The tool will now begin analyzing the code in the repository. This may take a few minutes, depending on the size of the project. Once the analysis is complete, you will be automatically navigated to the analytics page.
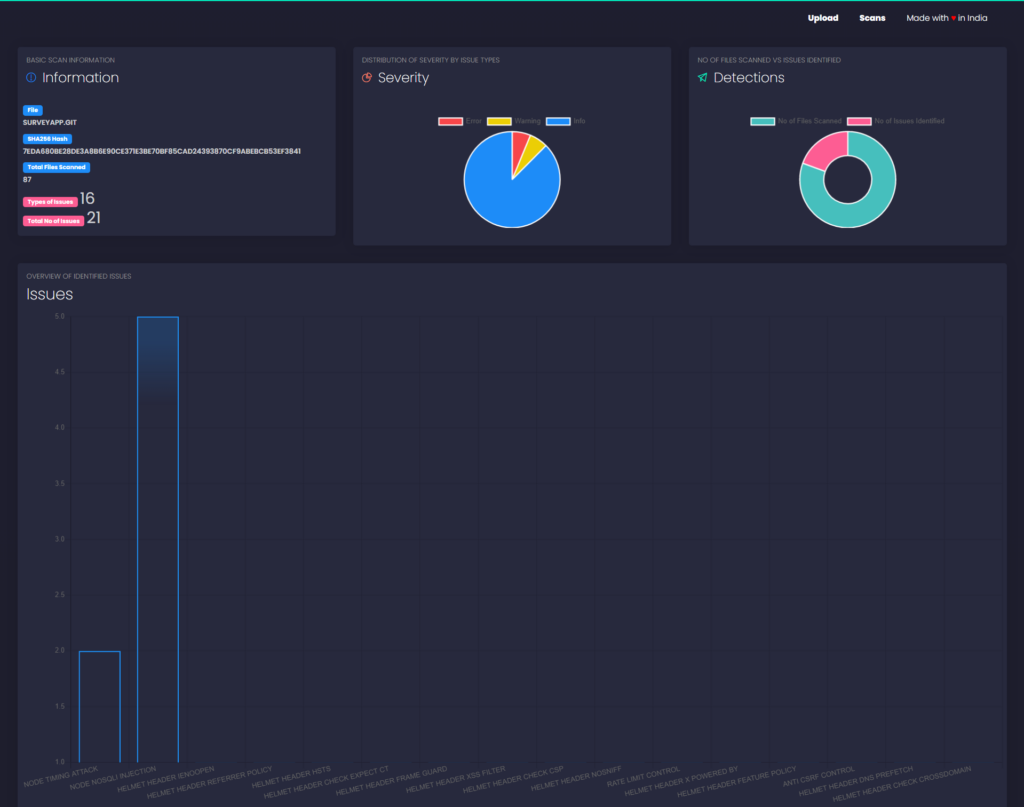
Here you can review what the tool has found, including the number of files scanned, number of issues detected, and the types of issues found in the repository.
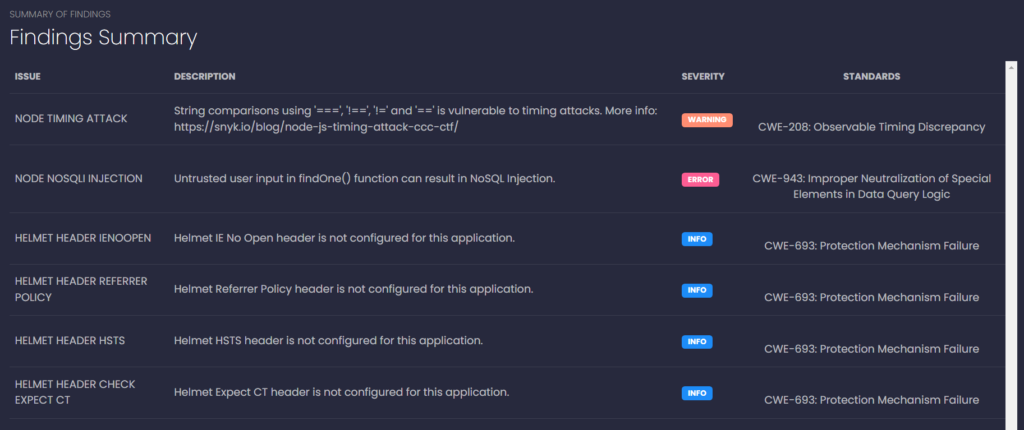
The types of vulnerabilities can be seen in the above image with a severity tag whether it’s an error, a warning, or just extra information for your reference.
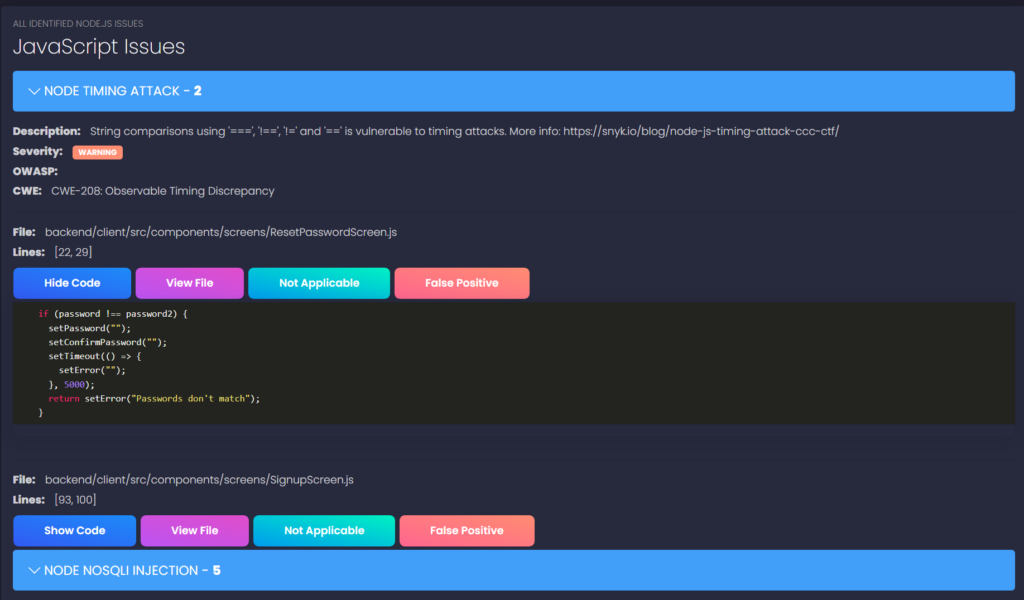
NodeJsScan provides a detailed description of the vulnerability and its impact on the application’s security. Clicking on the vulnerability type allows you to view details, learn more about a specific vulnerability, and view the code block that needs fixing.
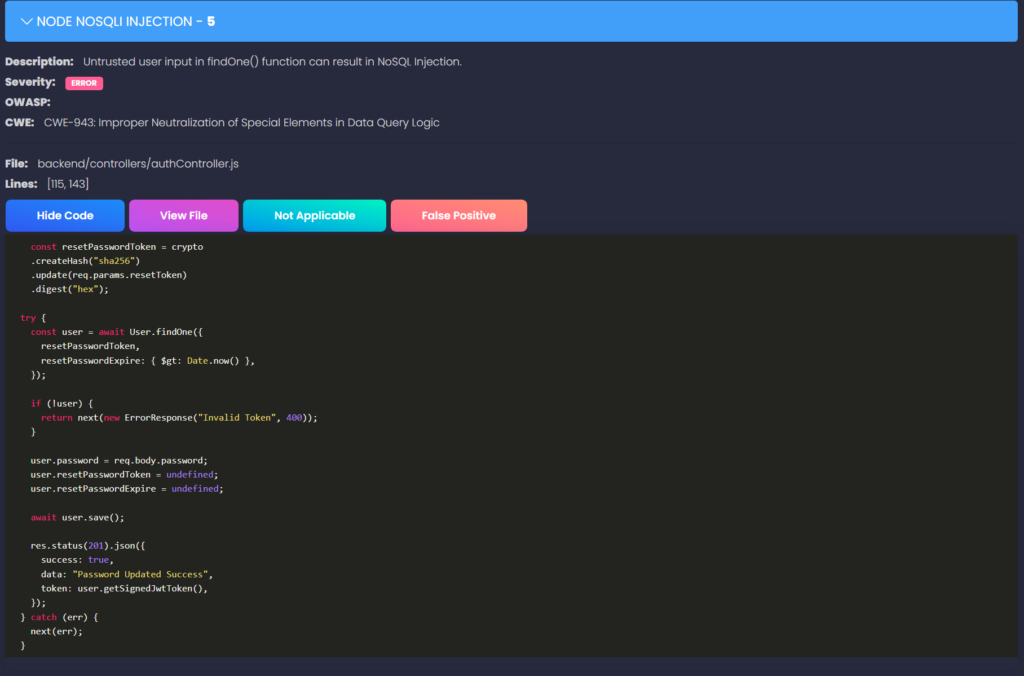
The detailed vulnerability description will include information about the data flow. Review the data flow to understand how the vulnerability can impact the application’s security. Note that SAST solutions do not perform runtime analysis, meaning that they can’t discern real threats from false positives. Flagged vulnerabilities must be analyzed to determine whether they represent real security risks.
Granted: SAST solutions enable developers to shift-left security by performing vulnerability analysis earlier in the SDLC, with real-time feedback on their code’s quality. But SAST is not a perfect solution.
NodeJsScan can only perform SAST scans on NodeJS applications, and it cannot scan applications written on other frameworks and libraries. Additionally, SAST solutions are not designed to analyze a running application, leaving them blind to configuration errors and runtime vulnerabilities. Scans need to be performed after every code update to help developers learn from mistakes and develop more secure code moving forward.
To further enhance the security of our CI/CD pipelines, we have developed specialized tools such as Spectral for CodeBuild Security, which continuously scans the entire SDLC for hard-coded secrets, keys, and misconfigured code that could lead to security vulnerabilities. Create a free account to learn more.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of