Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Updated 03.2024
When it comes to developing software, secrets are necessary for connecting everything up in a secure manner. The verification of secrets is how servers know the source identity of the requests they get. Too often, the common practice is to keep everything in clear text and hope for the best.
But this isn’t the best practice. It exposes your software and applications to potential vulnerabilities through accidental code versioning commits. Moreover, it puts your code secrets, keys, authentication credentials, APIs, and tokens in a space that is easily viewable if it gets accidentally added to the codebase.
Secret management tools are created for this specific reason – to keep credentials and code secrets secure, organized, and accessible to the right people and machines.
Before introducing the top nine secret management solutions, you should know in 2024, let’s quickly review what secret management is and its benefits.
Secret management is a category of tools that allow developers to securely store sensitive data such as passwords, keys, private information, and tokens in an accessibility-controlled way.
For small applications, managing secrets doesn’t seem so complex. However, as teams and the software code base grow, so do the number of secrets in your app’s ecosystems. Tools, containers, microservices, and API connections require secrets to keep its contents secure.
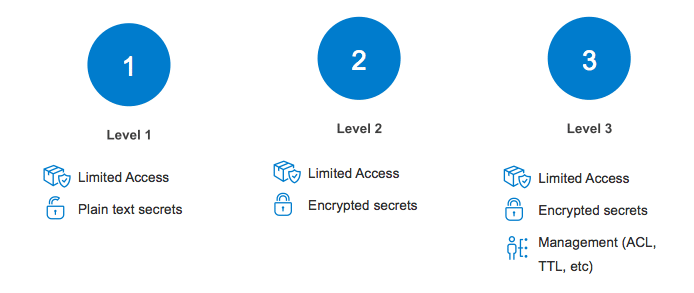
It’s not hard to lose a key or have it hard-coded into scripts or have access to superuser privileges that need to be managed safely and securely. Secret management has features that eliminate the need for hardcoded and embedded secrets, enforce password security, and apply privilege-based sessions on automation scripts, accounts, and individual users with logs to keep an audit trail.
While many frameworks and DevOps processes come pre-baked with security credentials, their default values are publicly available and easy to crack by malicious users.
Secret mismanagement is often present in tools like Jenkins, Ansible, Puppet, and Chef. Since they are designed for optimized speed and delivery, security issues often present themselves through automated configuration, in production, that requires secrets to access protected resources such as databases and SSH servers.
Mismanaging secrets is estimated to cost $1.2 million annually for companies. According to research by 1Password, “60% of IT and DevOps organizations have leaked secrets,” and 77% of former employees still have access to their previous workplace systems.
This is where secret management tools come in for your software development processes and stack. In addition to keeping everything secure and centralized, these tools also address security standards and externalize compliance to third parties and vendors specializing in best practices.
There is an abundance of secret management tools available. Here are the top 9 that you need to check out for your team, CD/CI processes and software development integration.
Infrastructure is no longer static and on-premise. Everything has mostly moved to the cloud, meaning multiple vendors and service providers. In addition to this, automation has ensured that digital assets scale dynamically with apps and servers growing and shrinking based on needs and demand. How security is implemented needs to match the unknown network perimeters and enforce identity verification safely and securely.
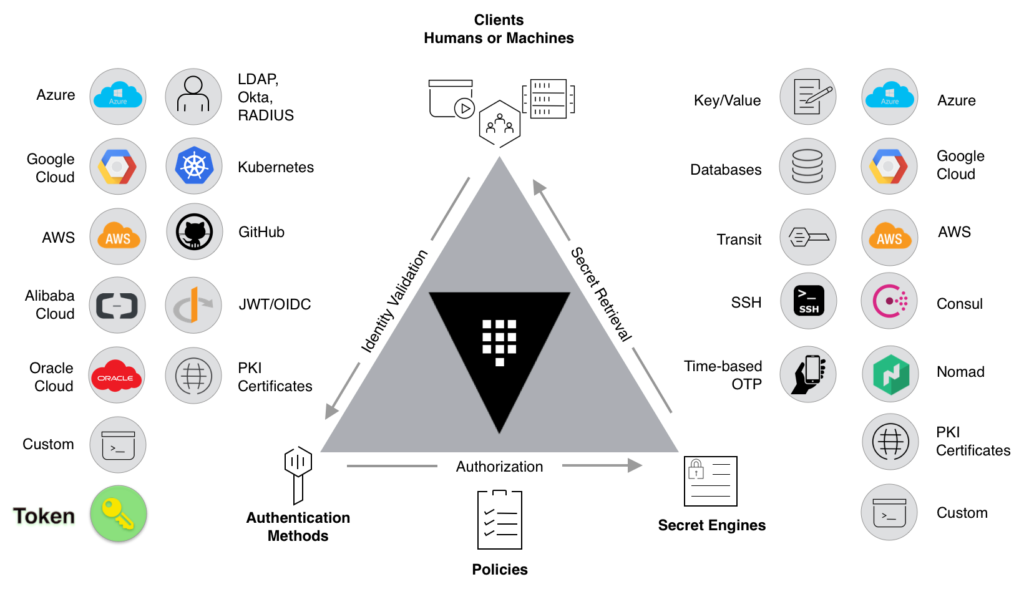
HashiCorp Vault lets development teams store, manage, and control access to tokens, passwords, encryption keys, and certificates. This is achieved through various access methods such as a user-friendly interface, the console, or via an API – making it easy to use for different types of users.
Secrets management tools are fantastic for keeping everything in one place. They provide development teams a centralized view of the secrets currently in use. However, one cannot rely on secret management tools alone. Secret scanning is a critical component of a secure SDLC to avoid leaks that secret management tools cannot detect.
Spectral Secrets Scanner is a secrets scanning tool that alerts you to any secrets or vulnerabilities within your software and infrastructure. It allows you to monitor, classify, and protect your code, assets, and infrastructure against exposed API keys, tokens, credentials, and high-risk security misconfigurations.
AWS understands the enormity of keeping secrets safe and under control. AWS Secrets Manager lets you rotate, manage, retrieve database credentials, API keys, and passwords with ease. If your software development processes and application are already inside the AWS ecosystem of services, then using AWS Secrets Manager is even easier to integrate into your workflow.
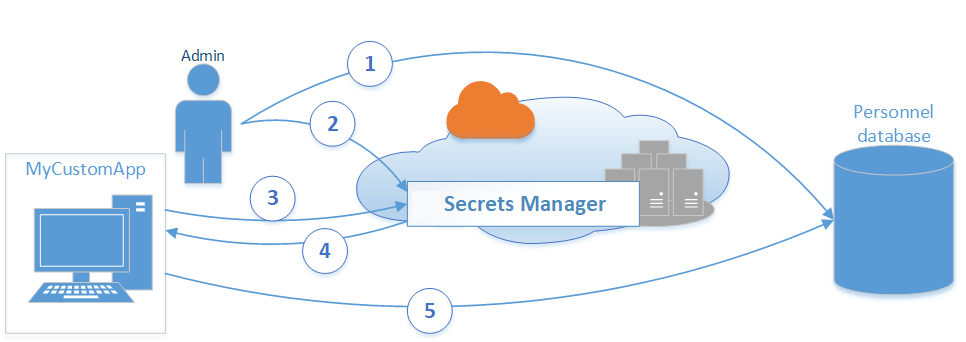
Features of AWS Secrets Manager include secrets encryption, Secrets Manager APIs, and client-side caching libraries. If an Amazon VPC is configured with endpoints, it also keeps the traffic within the AWS network.
Cloud Key Management System – or Cloud KMS – is Google Cloud’s version of secret management.
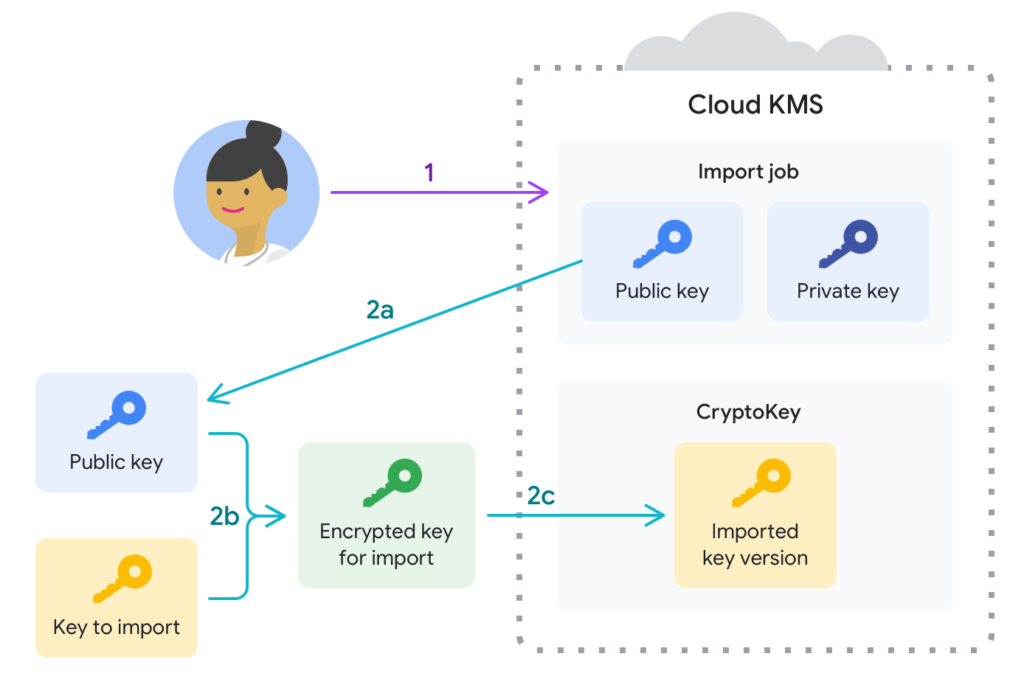
Cloud KMS aims to centralize key management in a scalable and ultra-fast way with a high degree of compliance, privacy, and security. Features of Cloud KMS include creating, rotating, and destroying symmetric and asymmetric cryptographic keys. There is also the option of creating automated security policies that lets you approve or deny access to keys.
If your software and applications run on Azure, Microsoft has Azure Key Vault to ensure that all your secrets are managed in a single repository. This includes keys, certificates, connection strings, and passwords. Similar to Cloud KMS, you can also create and import encryption keys into the Vault for management.
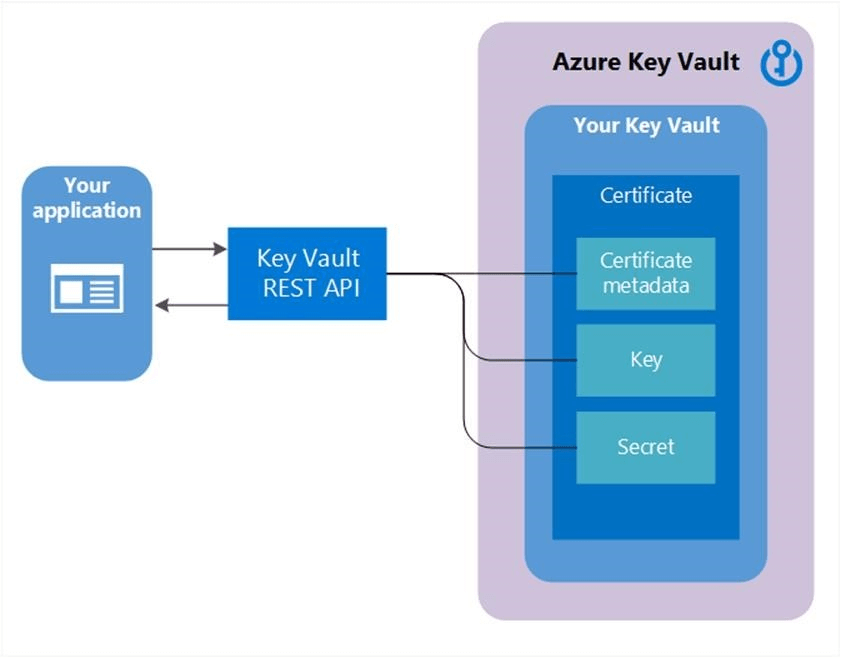
In addition, you can automate SSL/TLS certificate renewal and rotation so that your connection always remains secure.
Created by developers at Lyft, Confidant is an open-sourced secret management system that provides a user-friendly interface to deal with secure storage and accessing secrets.
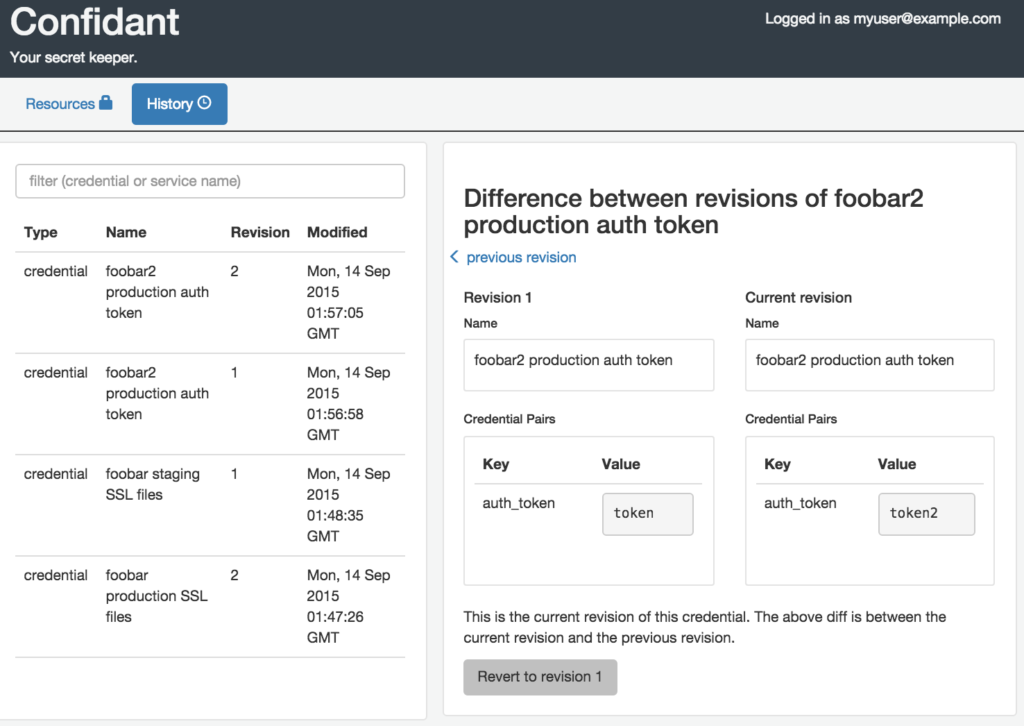
Confidant was created to solve and automate AWS KMS grants for IAM roles, allowing IAM roles to generate tokens for usage between service-to-service authentication. This means that encrypted messages can be passed between services with versioning availability through mappings and history of changes.
Keywhiz is a secret management and distribution system by Square. Being a financial service that processes over $9.49 billion in annual revenue, they understand the need for security, managing, and distributing secrets. Keywhiz is created to eliminate the vulnerable practice of putting secrets in config files and copying files to servers out of scope and band.
Leaked keys are hard to track. Keywhiz makes secrets like TLS certificates, GPG keys, API tokens, and database credentials easy to store, manage and access by suitable applications and users. Keywiz works by creating clustered servers in an encrypted and centrally stored database with automation APIs over mTLS.
Pinterest created Knox as a service for storing and rotating secrets, keys, and passwords. The idea behind Knox is to ensure that keys do not become compromised through the ability to easily rotate keys and keep them out of git repositories.
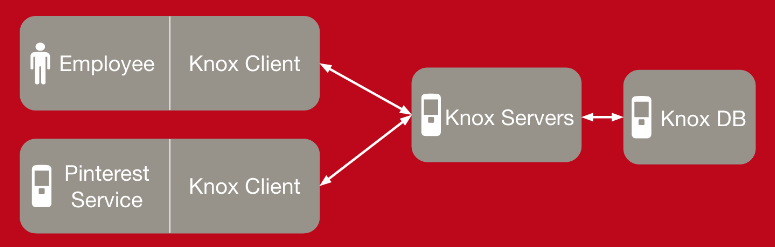
This enables developers to access to and use of confidential secrets, keys, and credentials without them becoming compromised. Key rotation also allows for safety mechanisms through invalidation processes and issuance of keys, in addition to keeping audit logs.
Open sourced and compatible with KeePass and Password Safe, Strongbox is a secure password management system for iOS and macOS. While it looks like a device-based password keeper on the surface, it also allows you to access tokens, private certificates, and encryption keys.
You can choose to store credentials locally or in cloud-based services such as iCloud, Dropbox, OneDrive, Google Drive, and WebDAV.
Secret management is an integral part of secure software development and infrastructure automation. For many organizations, code secrets are often neglected and kept in an insecure space such as config files or pushed to git repositories. Secret management tools help an organization keep its secrets a secret through a centralized system that does its best to mitigate plain view accessibility.
But slip-ups can happen, and they do happen. Secret scanning is as vital as secrets management as it adds another layer of protection through prevention. Secret scanning can help prevent vulnerabilities in critical components of a secure SDLC and avoid leaks through detection.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of