Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Amazon Web Services (AWS) provides a large suite of security tools to protect workloads, data, and applications running on AWS cloud infrastructure. Among the 25 AWS-native security solutions, it’s challenging to figure out exactly what your organization needs and why. This article helps simplify your decision by overviewing the top 12 security tools and services offered by Amazon and their uses.
Whether you’re tasked with AWS administration, running scalable and reliable cloud-based software, or you work in the AWS cloud as part of a DevOps team, security is critical for all cloud storage buckets, users, and computing instances. Some recent high-profile breaches were directly caused by poor AWS security:
AWS security tools help protect against similar incidents happening to your business. Furthermore, strengthening AWS workflow security with the best solutions mitigates against other threats, such as malicious insiders selling sensitive data or threat actors taking down mission-critical apps hosted in the AWS cloud.
AWS security tools and services protect workflows, resources, and data in AWS from unauthorized access, misconfigurations, and other threats. These tools and services cover the following core categories of cloud security:

Category: Detection and Monitoring
AWS Security Hub provides a unified overview for monitoring your current security posture across multiple AWS services and resources. These checks use prepackaged security standards, such as the AWS Foundational Security Best Practices. Security Hub also detects deviations from security best practices and provides automatic remediation capabilities.
Recommended Users: Anyone tasked with overseeing and validating the secure use of AWS cloud services and resources, such as cloud security analysts.
Pricing: Starts at $0.0010 per security check for the first 100,000 checks

Category: Identity and Access Management
AWS IAM provides vital identity management and access controls across every AWS service. In practice, this gives organizations fine-grained control over who has permission to access certain resources and services in their AWS cloud workflows. The identity management part of IAM simplifies creating, managing, and de-provisioning IAM users to avoid issues such as orphaned accounts.
Recommended Users: IT departments and cloud administrators responsible for providing appropriate levels of access to business resources.
Pricing: Free of charge — built-in as part of the AWS account management console
Category: Identity and Access Management
IAM Access Analyzer generates important findings about the level of access to AWS resources that different accounts have. As more users get granted permissions to access cloud resources, getting a clear picture of access patterns becomes more difficult without the data that IAM Access Analyzer provides. Ultimately, the ability to verify existing access levels are as intended and remove excess privileges positions you to implement the principle of least privilege for increased security in your AWS environment.
Recommended Users: Cloud administrators/security administrators
Pricing: Free of charge
4. AWS Secrets Manager
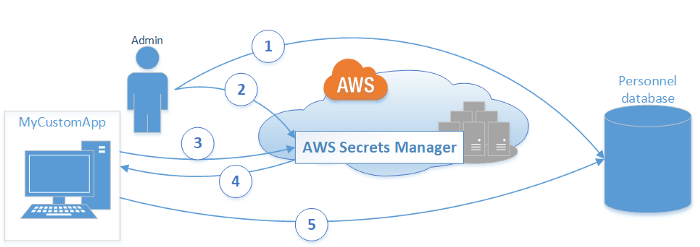
Category: Data Protection
AWS Secrets Manager lets you more easily protect the critical secrets required to access important services in AWS, such as databases for your custom applications. To retrieve secrets, users make API calls to the Secrets Manager API.
Recommended Users: Database administrators and development teams
Pricing: $0.40 per secret per month and $0.05 per 10,000 API calls.
Category: Infrastructure Protection
AWS Web Application Firewall (WAF) protects web applications hosted on AWS computing infrastructure against a range of common attacks. Threat actors regularly seek to exploit vulnerabilities in Internet-exposed web apps with attacks such as SQL injections and cross-site scripting (XSS). AWS WAF essentially sits in front of your web apps and APIs and gives you the ability to block or filter malicious traffic using pre-defined rules.
Recommended Users: Cloud, network, or security administrators.
Pricing: $5 per web access control list, $1 for each firewall rule on a given list, and $0.60 per 1 million web requests processed.
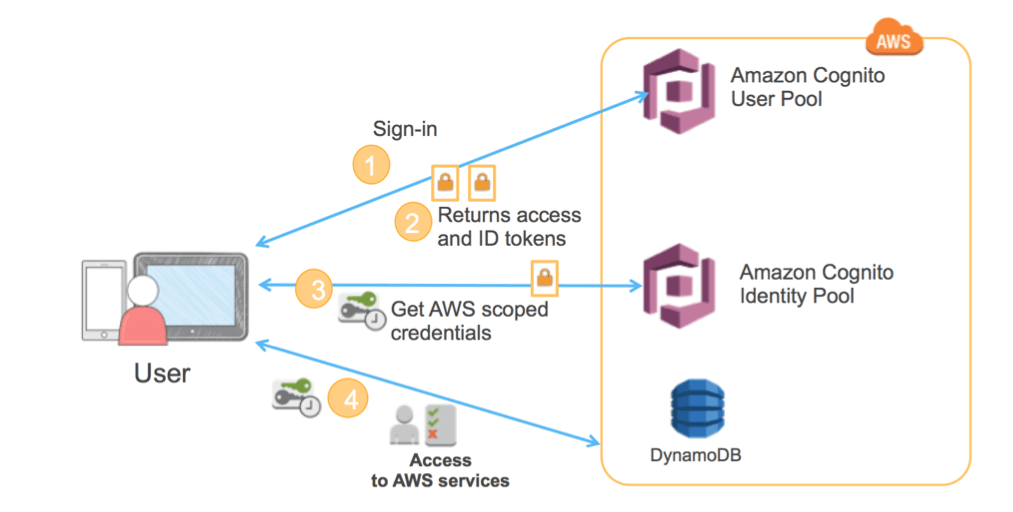
Category: Identity and Access Management
Amazon Cognito is a security service that handles authentication for web and mobile apps running on AWS infrastructure. The value-add here is that you can focus on building great apps while AWS handles adding user sign-up, sign-in, and access control to those apps. Cognito is standards-based, so it supports IAM standards, including OAuth 2.0, SAML 2.0, and OpenID Connect for authentication.
Recommended Users: Development teams, DevOps, DevSecOps
Pricing: Free of charge for the first 50,000 monthly active app users: prices vary per number of active users thereafter.
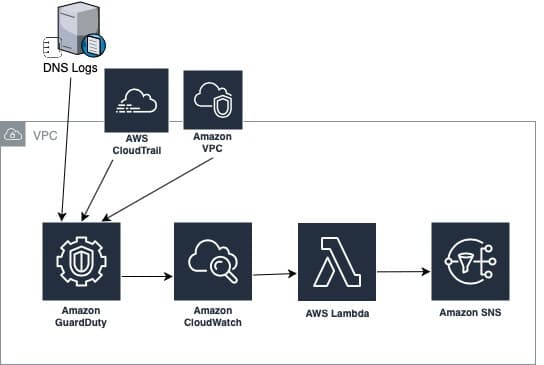
GuardDuty provides managed threat detection capabilities for your AWS accounts, stored data, and workloads. The service automatically analyzes DNS logs, event logs, and other network data at scale. Machine learning capabilities and integrated threat intelligence help to detect anomalies and provide detailed findings in a single console.
Category: Detection and Monitoring
Recommended Users: Security analysts, security operations teams
Pricing: Dependant on multiple factors unique to specific companies. The first 30 days are free so you can run it for a month to get an idea of the monthly costs for your business.
8. Amazon Macie
Category: Data Protection
Amazon Macie provides features to manage the security and privacy of sensitive data stored in Amazon S3 buckets. Macie automatically discovers sensitive data located in S3 storage buckets using pattern matching and machine learning. You get an inventory of unsecured unencrypted buckets and publicly accessible buckets along with alerts for sensitive data in those resources.
Recommended Users: Anyone responsible for compliance with regulations such as GDPR or HIPAA. Also, cloud security teams.
Pricing: $0.10 per month per S3 bucket evaluated for security and access controls (eg encryption), $1.00 per GB of data processed for sensitive discovery for 2 GB – 50 GB per month.
Category: Detection and Monitoring
AWS Config lets you monitor and record your AWS resource configurations and any adjustments to those configurations. You can also set rule sets for AWS resource configurations and receive notifications when those rule sets are broken. This service is particularly useful in mitigating the many types of cloud configuration changes that can expose organizations to cyber attacks.
Recommended Users: Cloud security admins, security analysts
Pricing: Dependant on a range of factors unique to different organizations and their AWS cloud deployments.
10. AWS CloudTrail
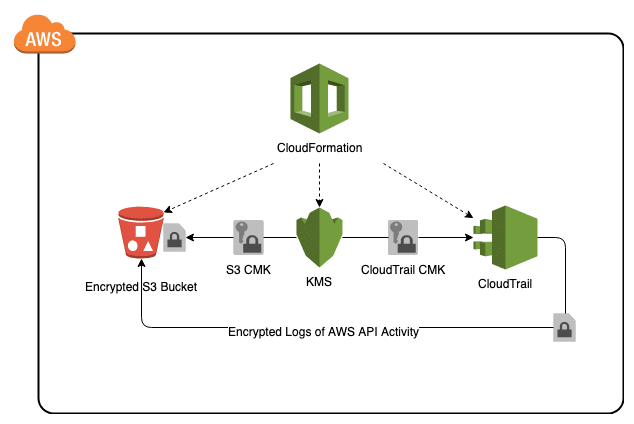
CloudTrail provides continuous monitoring of user account-related activities in AWS, including logins, resource access, API activity, and more. User activity data goes to S3 buckets where it’s possible to monitor and analyze the information.
Category: Detection and Monitoring
Recommended Users: Security analysts, governance, risk, and compliance teams, incident response teams.
Pricing: Highly variable because it depends on the type and number of events delivered for analysis.
Category: Detection and Monitoring
Amazon Inspector scans your AWS workloads for software vulnerabilities that could potentially lead to sensitive data compromise or attacks that take those applications down. The service automatically discovers all AWS workloads and uses a database of vulnerabilities to continually scan for weaknesses.
Recommended Users: Security analysts, DevSecOps
Pricing: $1.2528 per EC2 instance scanned and $0.09 per container image
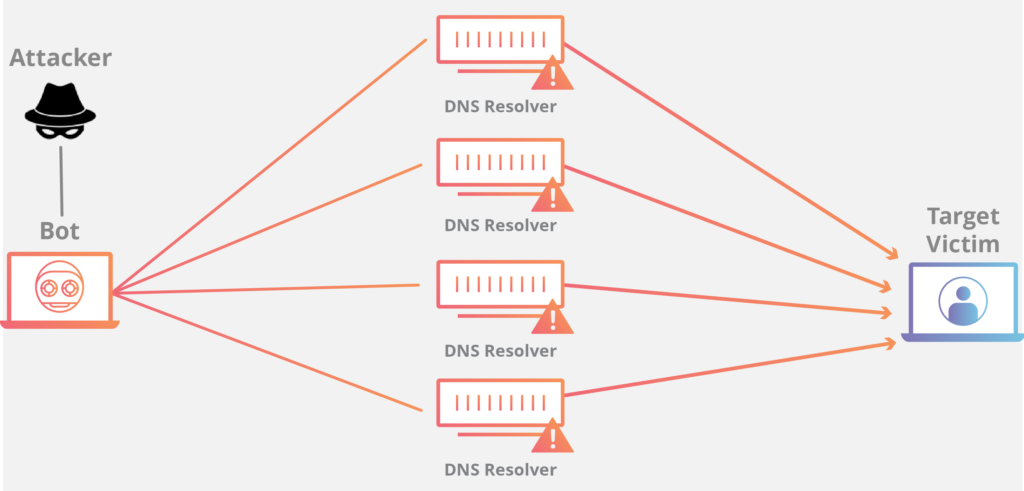
Category: Infrastructure Protection
AWS Shield protects all your applications running on AWS from DDoS attacks. This always-on protection minimizes application downtime and latency even during DDoS attempts.
Recommended Users: DevSecOps, cloud security admins
Pricing: AWS Shield Standard is free and protects against network and transport layer DDoS attacks. A paid option is available for more advanced attacks.
These 12 top AWS security tools meet a diverse range of security needs. Now that you know what they’re used for and their recommended users, you’ll have a better idea of what your organization needs. While AWS has good versatility in its security tools, there are some gaps that don’t meet the most pressing security concerns today.
Third-party DLP solutions can prove invaluable for plugging gaps in the coverage of existing AWS security services. One area that the top AWS-native tools don’t cover sufficiently is data loss prevention (DLP) for CI/CD pipelines.
DLP solutions help to detect and prevent data breaches, exfiltration, or unwanted destruction of sensitive data. Having DLP capabilities in CI/CD pipelines protects against threat actors who regularly seek to exfiltrate sensitive data from vulnerable applications.
SpectralOps is a unique DLP solution that works across all locations from on-premise to the AWS cloud. The solution uses static application security testing (SAST) to uncover shadow resources, misconfigurations, code errors, and other security blindspots putting your sensitive cloud-based data at risk during the software build phase. You can prevent problems before threat actors ever get the chance to exploit those vulnerabilities and steal your data.
It takes just one line of code to integrate SpectralOps with your existing AWS CI/CD pipelines. Start scanning your Cloud stack now

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of