Circle.ci vs Jenkins: Battle of the CI/CDs
Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of
When you think about hacking stuff, you probably don’t consider thermometers and pacemakers. But imagine the implications if that chunk of metal inside your body suddenly starts acting weird. From the humble thermometer to the sophisticated MRI machine, these gadgets are vital cogs in the healthcare machine and potential Trojan horses if not correctly secured.
Even the most basic medical devices are part of the Internet of Things, and 53% have a known vulnerability. As a result, global cybersecurity spending in the medical device sector will skyrocket to $1.2 billion by 2025. It takes more than just ticking off compliance checklists to bulletproof your healthcare network. It requires a robust, multi-faceted strategy that goes beyond meeting HIPAA standards.
This article will review medical device security, why it’s critical, and the steps you can follow to secure devices for good.
Medical devices are healthcare instruments, apparatuses, or machines used to diagnose, monitor, and treat conditions. Medical device security involves safeguarding the integrity, confidentiality, and availability of the data generated, transmitted, or stored. Given that these devices are increasingly connected to healthcare networks, their security is critical for patient privacy and their safe and effective functioning.
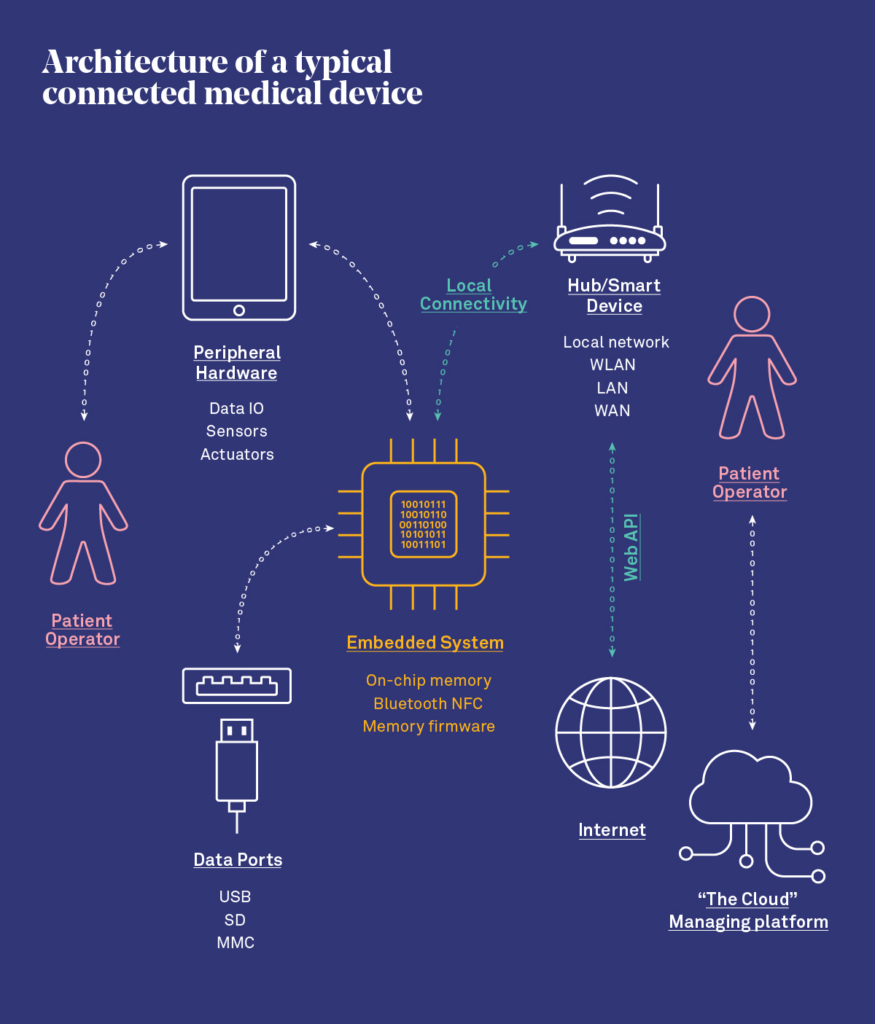
What it is: Creating a comprehensive list of all medical devices and categorizing them based on their functionalities, data they handle, and connectivity features.
Why you need it: Knowing what devices are on your network helps you prioritize your security efforts.
Implementation: You can create a device inventory by utilizing automated asset discovery tools that scan the network for all connected medical devices. These tools can identify devices by IP addresses, types, and other characteristics. Once you’ve gathered the inventory, devices can be classified and categorized based on their functionalities, the data they handle, data storage, transmission capabilities, and more. This classification helps prioritize security measures, as devices handling sensitive data may require more stringent protections.
What it is: A vulnerability assessment is a process of identifying, evaluating, and prioritizing vulnerabilities or weaknesses in a system, network, or application. The goal is to uncover security gaps where an unauthorized user could gain access, manipulate data, or otherwise perform malicious activities.
Why you need it: Understanding vulnerabilities allows you to anticipate possible threats, apply patches, or take other corrective actions.
Implementation: Create a vulnerability management program by first identifying all medical devices in your inventory, as you saw in step one. You can then use specialized vulnerability scanning tools for medical equipment to detect security weaknesses. These scans should be done in a controlled environment to avoid disrupting clinical operations. You can analyze the findings to understand the risk levels associated with each device, enabling you to prioritize patches and other security measures accordingly.
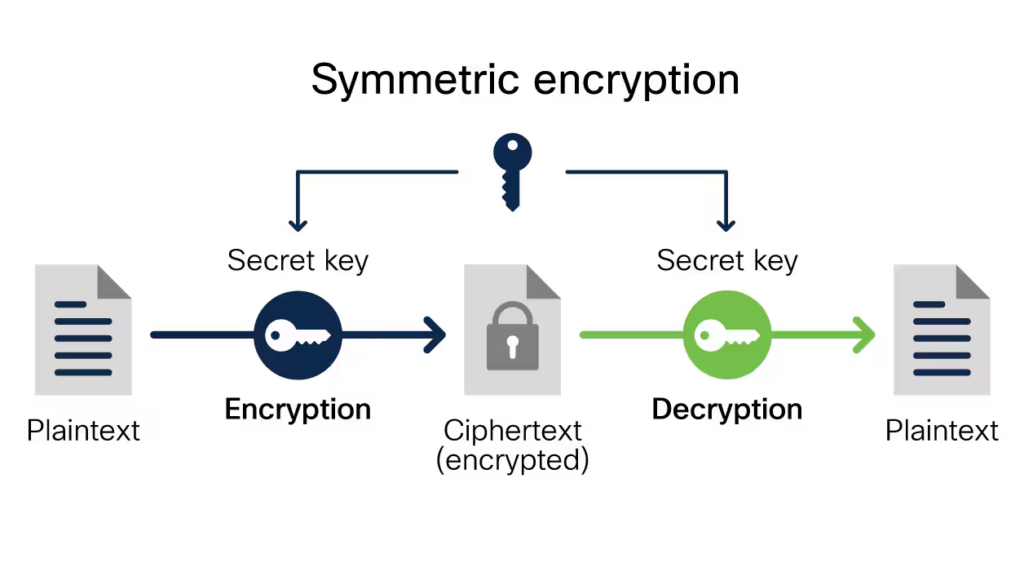
What it is: Data encryption is the process of converting plain text or other readable data into a coded form, making it unintelligible without the appropriate decryption key.
Why you need it: Encryption makes the data unreadable, thus protecting the information from unauthorized access.
Implementation: You can encrypt medical device data by implementing hardware or software-based encryption solutions designed to be compatible with the specific medical devices in use. It’s best to choose encryption algorithms that meet or exceed industry standards, like AES-256 for securing sensitive patient data at rest and TLS for data in transit. Once you’ve selected an encryption method, you’ll need to rigorously test it in a controlled setting to ensure it doesn’t interfere with the device’s primary functions before deployment.
What it is: Access control methods regulate who or what can view, use, or interact with a medical device.
Why you need it: Reducing the number of people who have access to medical devices decreases the likelihood of unauthorized or accidental data access and helps prevent secrets sprawl.
Implementation: IT professionals in healthcare can implement access control for medical devices by using a mix of role-based and attribute-based access control mechanisms. You can limit who can access, modify, or transmit sensitive data by defining strict user roles and permissions. Two-factor authentication can also add an extra layer of security, as well as advanced IAM policies like biometric scans and strict password policies. All access controls should be tested rigorously to ensure they don’t disrupt medical functions and comply with industry regulations like HIPAA.
What it is: Separating medical devices from the general network to contain potential risks.
Why you need it: Network segmentation isolates medical devices, reducing the risk of a broader network intrusion affecting these devices.
Implementation: You can implement network segmentation in the medical industry to isolate medical devices from general-purpose networks. This can be achieved using VLANs or firewalls to create segmented zones specifically for medical equipment. Devices with similar security requirements are grouped together to limit lateral movement of potential threats. Proper network security strategies like segmentation minimize the risk of unauthorized access and ensure that the impact doesn’t spread across the entire network if one device is compromised.
What it is: Software patch management is the practice of updating medical devices to address vulnerabilities, fix bugs, or add new features.
Why you need it: Software updates often include patches for known vulnerabilities, reducing security risks.
Implementation: You can manage software patches for medical devices through a centralized patch management system. If you haven’t already, you’ll need to inventory all devices, noting the current software versions. Vendors usually release security patches, which should be tested in a controlled environment before deployment – be sure to communicate with vendors to understand the device’s software lifecycle and get commitments on the frequency and support for updates. Automated patching tools can streamline this process, too. Regular audits, a well-thought-out patch management strategy, and timely application of patches are crucial to ensure these critical devices’ ongoing security and functionality.
What it is: A pre-defined plan detailing the processes to follow when a security breach occurs.
Why you need it: Having an incident response plan ensures a structured and prompt reaction to any security incidents, minimizing damage.
Implementation: To create an incident response plan for medical device security, you should first identify potential risks and vulnerabilities by following the steps above. Next, you can outline clear protocols for detecting, reporting, and responding to medical device security incidents. The plan should be periodically reviewed and tested through drills (e.g., tabletop exercises and simulations) to ensure effectiveness, and simultaneous staff training is crucial for quick identification and response. If there’s a worst-case scenario and an incident happens, you should document it and the subsequent actions for compliance and future improvement.
What it is: Cloud security for medical devices refers to the suite of policies, technologies, and controls deployed to protect medical device data and related applications hosted in cloud environments.
Why you need it: As medical devices increasingly connect to the cloud for data storage, analytics, and device management, safeguarding these interconnected systems becomes critical.
Implementation: The healthcare industry needs to secure complex multi-cloud environments thanks to the huge number of devices connected to the internet. After completing a risk assessment, you can select a cloud service provider that complies with industry regulations like HIPAA. You can then configure cloud-specific firewalls and Intrusion Detection Systems (IDS) to monitor traffic and flag anomalies. Finally, your team should conduct cloud security audits to identify and patch vulnerabilities and prevent data loss.
Each of these points offers a tactical way to enhance the security posture of medical devices in your healthcare organization. By taking a multi-faceted approach to security risk assessment, you comply with regulatory standards and add layers of security that can adapt to evolving threats.
Spectral helps you secure sensitive information, assets, and data from code to cloud by scanning your codebase for vulnerabilities and data breaches before they happen.
Get a free trial today.

Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of

Jenkins is the most used open-source CI/CD solution out there. Being a FOSS project usually means that there’s an ever-growing number of extensions and capabilities for
Code fast and break things may be a healthy approach when you’re rushing to present investors with a POC. However, when it comes to developing real-world