Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
There is an old joke among cybersecurity professionals that the only way to truly secure your data is to keep it on a machine without connection to power or the internet… oh, and put it in a sealed cave. And even then, it is not 100% secure. In today’s world, it’s a pretty safe assumption that none of our data is truly secure. Last year, researchers at the University of the Negev in Israel proved they could use radio signals from SATA cables to exfiltrate data even from an air-gapped computer.
The only logical way to keep information secure is to encrypt it. Cryptography is the practice and study of securing communication so that only the intended target of a message can understand it. The study of cryptography isn’t new – one of the earliest forms of encryption is known as the Caesar cipher because Julius Caesar used it for his confidential correspondence.
Encrypting network traffic is so ubiquitous that most people don’t even realize it is used regularly to encrypt the communication between web servers and the clients that connect to them in the form of the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols. In this article, we’ll explain network security and cryptography, some basic types of cryptography, their benefits, and their use cases.
Network security usually refers to all the measures taken to protect an organization’s computer network and information. The challenge is to keep the data on the network accessible to anyone who needs it while keeping it secure from prying eyes.
There are a large number of protocols, devices, and technologies designed to secure computer networks. Today’s network architecture is complicated, and it faces an ever-evolving threat environment and attackers who are constantly looking for and trying to exploit flaws in any number of places, including equipment, data, apps, and people. As a result, numerous network security management systems and programs are in use today that address regulatory issues and specific threats and exploits.
Cryptography prevents unauthorized access to sensitive information at rest or in transit by making it unintelligible without the correct key. It uses encryption to safeguard data transfer via networks, guaranteeing that only those with authorized keys can access encrypted data. Any cryptographic system involves both an algorithm (there’s a lot of math in cryptography) and a key. The trick is that the system should be secure even if everything except the key is public knowledge. You can define your organization’s cryptography requirements depending on the structure, security measures already in place, and overarching governance.
Just like the power grid, computer networks are everywhere and are not that hard to tap into – think of it like creating a pirated connection to the power grid, except that instead of stealing electricity, the bad guys are stealing data. Once connected to a network, you can access all the packages traveling on that network.
IBM started the ball rolling for encryption in the late 1960s with its “Lucifer” approach, which was later standardized as the first Data Encryption Standard (DES) by the US National Bureau of Standards. As the internet’s significance increased, the world required more and better encryption using various cryptographic techniques.
Although many different types of cryptographic algorithms are in use, they can all be divided into three groups:
Both the sender and the receiver use the same key to encrypt and decrypt messages. One common use for symmetric cryptography is to keep your hard drive secure – it’s usually the same user who is writing and reading from the hard drive, so there is no issue sharing the key with anyone.
Also called public key cryptography, asymmetric is where each person involved in the conversion has two keys: one public and one private. The public key can be shared with the world, while the private key should remain a secret. The two keys are linked so that messages encrypted by the public key can be decrypted with the private key.
With this system, only the intended target of the message (the one with the right private key) can decrypt messages encrypted with their public key. The system works as long as a public key is connected to the right identity. To ensure the connection works, you can use third-party systems like PKI (public key infrastructure) and trusted sources known as CA (certificate authority).
You can use one-way functions (aka. hash functions) to turn any length or type of message into a fixed length of encrypted text. The process is one-way – there is no way to reverse the encryption and get the original message back.
Hash functions are useful since the resulting hash is unique for each block of encrypted information. That means the hash can be used to verify the integrity of the original block of information – if anything about that information has changed, running it through the same hash function would result in a different hash.
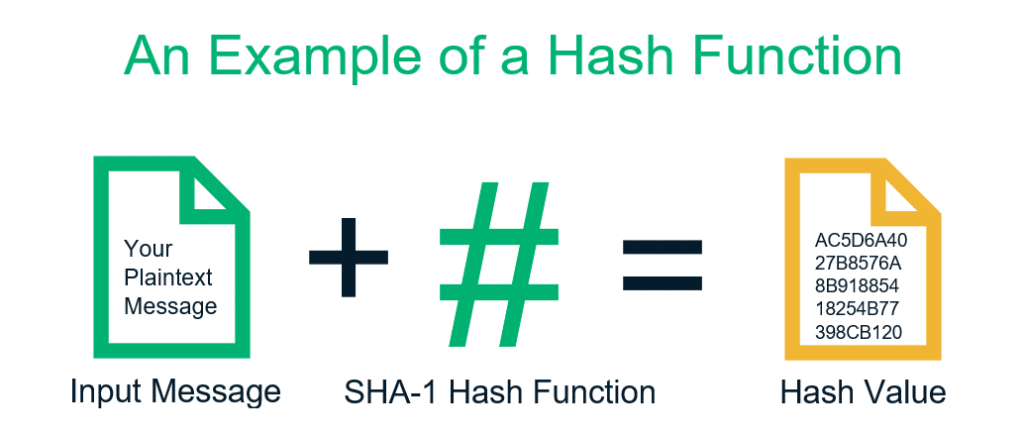
One simple example of the system’s usefulness is to save hashes of passwords instead of actual passwords. That way, even if you suffer a breach, all the hacker would find are useless hashes. When a user logs in with their password, you run it through the hash function and compare the result with what you have on file. A match would mean it’s the correct password.
Here are some less common uses you should consider when planning a comprehensive network security solution.
Most workplaces offer free WiFi to their employees, who regularly bring their own phones and computers to access the company network. With remote work still a common practice, most workplaces should consider adding BYOD (bring your own device) encryption to their network security implementation.
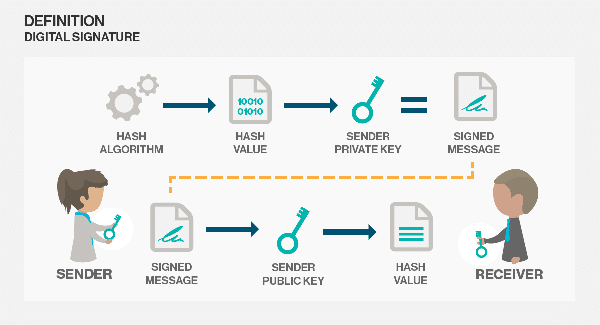
You could add digital signatures to almost any data created or shared on your network using a combination of public key cryptography and hash functions. It’s an excellent technique to add integrity and identity verification to sensitive information.
Using a passkey allows an individual to access an account by approving the login on an external device, with no password required. As user-password lists are inherently insecure, moving to a different method to prove who you are and what you’re allowed to access seems to be the direction in which cryptographic technology is heading. Apple, Google, and Microsoft are just some tech companies trying to encourage more users to use passkeys over passwords. You can read more about it in this article.
Quite a few encryption algorithms are known for being ‘unbreakable’ or ‘impossible to reverse-engineer,’ but that is only true if you consider the current technology. Once built and stable, a quantum computer would be leaps and bounds beyond anything we can do today, even on a supercomputer, meaning it could break pretty much any encryption we have. And quantum isn’t just a theoretical matter – governments and agencies worldwide are worried about what such technology would do to our networks’ private and sensitive information streaming. Last year NIST published its first group of encryption tools designed to withstand the assault of a future quantum computer.
Therefore, keeping on top of the ever-expanding landscape is advisable to secure your information. With the right system architecture and the right tools, it’s not beyond your organization to keep networks secure even in a future where computers can run more than trillions of floating operations per second (scary!). The best strategy is to pair cryptography with a scanning tool like Spectral, which scans your codebase and automates the process of secret detection to keep your data under lock and key.
Get a free trial of Spectral today.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions