10 Types of Vendor Related Risk Cloud Native Organizations Need to Manage
If you are a developer in the current cybersecurity climate, you already know your application’s security is paramount. But have you considered the risks associated with
Quick announcement: with SpectralOps you can prevent data breaches by protecting your code from hard coded secrets and misconfigurations.
You know how it goes: Every website, app, or service you sign up for in your private and professional life asks you to create a password and/or provide another identification method. It can be a lot to keep track of.
It should come as no surprise, then, that there’s noticeable growth in the adoption and use of free or paid personal password manager services, from 12% of US internet users using a password manager in 2017 to 23% earlier this year, based on survey results.
For example, one such service, LastPass, recently reached 25 million active users and reported survey results demonstrated that 23% of business employees worldwide use a password manager app on their smartphones.
However, personal password and account management aside, how do we, as developers or security experts and in the context of our professional responsibilities, protect the secrets our organization relies on during the development process?
Secrets are digital credentials that support both human-to-application and application-to-application access permission. There are several different types of secrets used in application-to-application access permission. Some examples are passwords, certificates, encryption keys, API keys, and SSH keys.
Below, we focus on the application-to-application secret management use case.
SSH key:
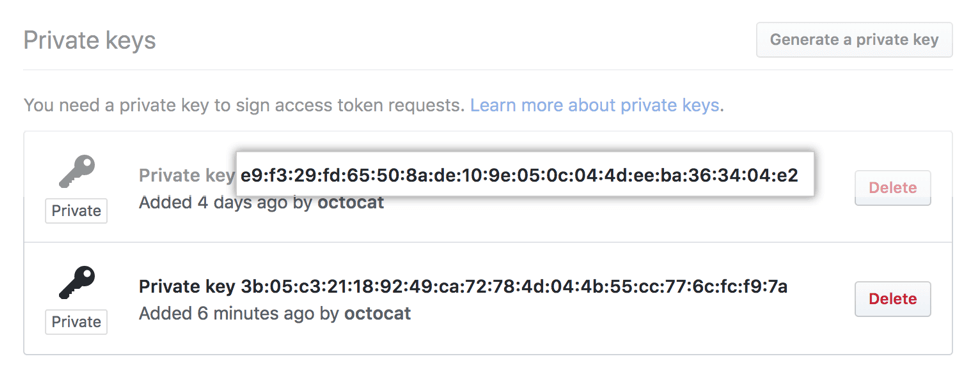
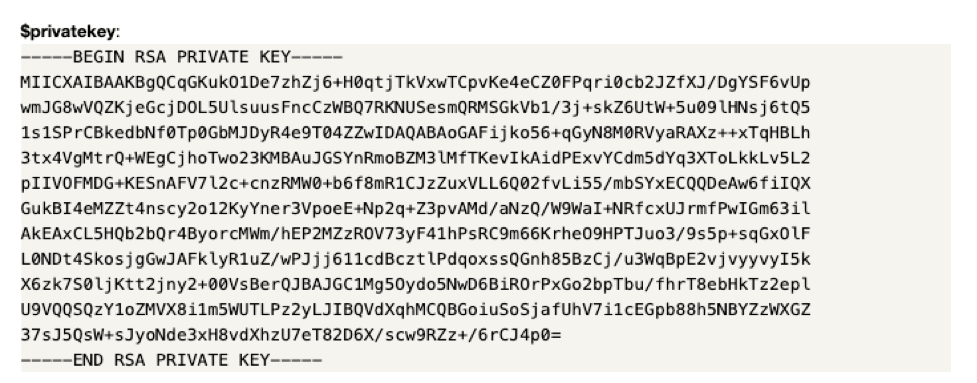
Secret management is a set of processes and best practices that comprise a mechanism to protect an organization’s digital assets from unauthenticated and unauthorized access. Secret management solutions provide a wide and deep range of use cases. The main capabilities of the security management mechanism are:
and role-based access control (See here for a deep dive.)
In a nutshell, it all comes down to software fatigue. Nine years after Marc Andreessen’s famous “Software is Eating the World” article in the Wall Street Journal, it is a given that the world is driven by code.
Today’s R&D organizations need to select and increasingly implement state of the art solutions to remain competitive and serve their customers well. Each new tech or tool added to the organization’s development, testing, and production environment needs to be secured—hence the secret proliferation phenomenon.
Secrets are everywhere: They’re used in every technology, are part of every step of SDLC, and support powerful automation processes.
Let’s take a deeper look at a few secret-proliferation drivers:
Cloud-native applications use many different kinds of services, such as computing (E2C, etc.), analytics (), database (MongoDB, memSQL, etc.), logging (ElasticSearch, Loki), and more. Secrets to such services need to be well managed to protect the organization’s (and its customers’/users’) data.
Each public cloud provider is different and good at addressing different aspects of business needs. Many businesses use multiple services, such as Amazon Web Services, Microsoft Azure, Google Cloud, and IBM Cloud, each of which contributes to secret profilieation.
The DevOps movement helps teams to develop, test, and deploy software in a much faster phase. To support that agility, they employ a wide range of services throughout the entire software development lifecycle, including vendors such as Jenkins, GitLab, Terraform, and more. The need to secure DevOps environments resulted in the creation of the DevSecOps field, where secret management is a very important pillar.
The use of microservices is the most popular way to build and manage services. Since each microservice is decoupled from other services being used, each might use a different provider, thus creating more secrets that need to be managed.
In the past, human interaction was the main mechanism for accessing an organization’s data. Modern software services have shifted to machine (and a lot of them, at that) identity as the key to connecting to machines, either inside the organization or between an organization and its customers (such as a service to record sales conversations that needs access to its customers’ calendars).
Incrasingly, organizations use ML based services, such as TensorFlow and Apache Spark, for example. Either as part of the organization’s product or the heart of the business value proposition, these types of services are experiencing exponential growth . This creates an additional data pipeline that needs to be protected, hence more secrets.
Many services in different industries (e.g., agriculture, manufacturing, distribution, and more) use IoT and embedded systems, and this trend will increase with 5G network adoption. New networks – additional endpoints that need to be securely connected (using vendors such as ThingWorx and Ignition), using certifications and encryptions, which also need to be managed properly.
On top of software fatigue driven by changes in technology, the ways in which people (within organizations) work have changed as well. Not only are there more secrets that need to be protected, but there are also more channels and places in which those secrets are likely to be communicated and stored outside of code development, testing, and production environments. Here are a few examples:
Secret Management Technologies
We’ve discussed secret management and the main technology drivers for secret proliferation. Now, let’s take a look at a few secret management technologies, both commercial and open source. A deeper overview of few and a more complete list can be found here:
https://stackshare.io/secrets-management
Commercial tools can be divided into two categories:
On the open source side, there are a few projects built by technology companies like Lyft, Pinterest and Square, and probably many others that aren’t publicly available. There are also open-source utilities built by companies in the field, as well as individual developers, such as https://github.com/fugue/credstas and https://github.com/codahale/sneaker.
When it comes to selecting technologies for secret management, ultimately it comes down to your organization’s needs and budget, the tools and technologies you use, and the team’s familiarity with secret management and availability/bandwidth to implement and keep such technologies and practices up to date.
https://docs.github.com/en/free-pro-team@latest/developers/apps/authenticating-with-github-apps
http://phpseclib.sourceforge.net/rsa/examples.html

If you are a developer in the current cybersecurity climate, you already know your application’s security is paramount. But have you considered the risks associated with

The trouble with allowing developers to deploy code directly to production is that security threats are often overlooked in the process. These vulnerabilities only show up

Rapid digitalization and increasing remote business operations place a significant burden on developers, who are continuously pressured to push out software faster. As a result, CI/CD