Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Did you know that the household data of 123 million Americans were recently stolen from Alteryx’s Amazon cloud servers in a single cyberattack? But the blame for this cannot fairly be laid at the feet of Jeff Bezos. No – the origin of this theft, and many other cybersecurity crimes began long before this data was uploaded to any cloud server. In another high-level cyberattack, financial data on 47,000 Americans was exposed on an S3 bucket from the US National Credit Federation in 2017.
Both of these cyberattacks were the result of their company’s lack of attention to identity risk management.
In this post, we’ll discuss the function of Identity Governance and Administration (IGA) and its role in relation to the branch of DevOps that is responsible for system and data security—DevSecOps.
If you work as an IT or development specialist, and unless you’ve been living under a rock for the past 10 years, you will be familiar with the term DevOps. This is the area of business that combines both software development and IT activity. Its aim is to shorten the Systems Development Life Cycle, or SDLC, bringing Continuous Integration and Continuous Delivery (CI/CD) to fruition. DevOps works hand-in-glove with Agile development methodology.
DevSecOps is an offshoot of DevOps, which enables the integration of security into the DevOps process. There has been a trend away from placing security within the IT realm and placing responsibility for this activity on the shoulders of development teams. This process has been colloquially termed, “shifting left.” Dev teams are then given security control of their own development deliverables.
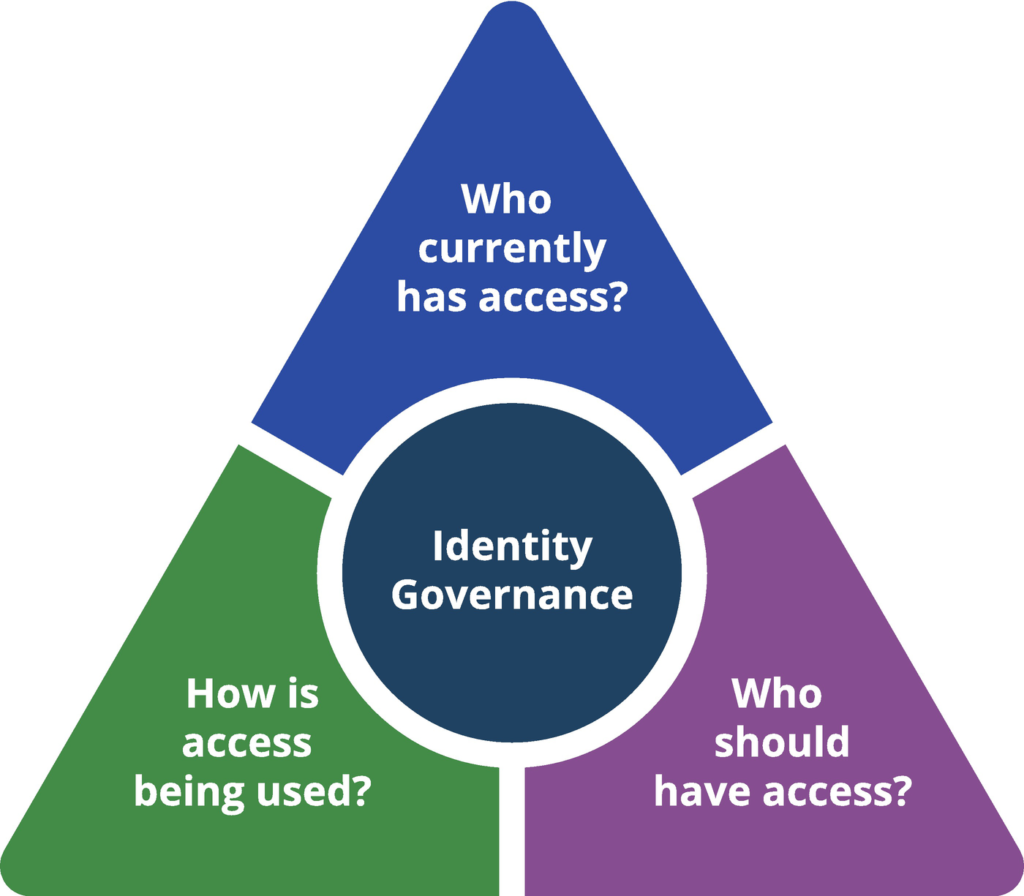
So, what is IGA? It is a methodology employed by software development companies to manage their internal and external access control and identity management.
Following US government legislation such as the Health Insurance Portability and Accountability Act (HIPAA), which was signed into law by President Bill Clinton on August 21, 1996, and the Sarbanes-Oxley Act (SOX) of 2002, companies are now required to optimize their data management, to enable greater transparency and accountability.
IGA extends functionality of identity control beyond that provided by standard Identity and Access Management or IAM that was traditionally employed for this purpose. IGA also supports system auditing and regulatory requirement reporting.
A key requirement of IGA is that it assists in the automation of the development workflow process, enabling and empowering developers to complete their tasks according to schedule without any annoying interference from DevSecOps. This is particularly relevant during COVID times with the necessity for remote working.
The governance aspect of IGA reflects the delineation of roles, reviews, reporting, and analytics that are part and parcel of a developer’s daily activities. The administration aspect reflects the management of account and credential access involved in the management of system and data access.
IGA is focused on a number of discrete system access and control functionalities. These include:
IGA comes down to identity risk. Its function is to spot weak spots in an organization’s technical workflow, plug them, and make sure they don’t occur again. All while concurrently complying with regulatory data security legislation.
In addition to following the regulatory guidelines, DevSecOps must also ensure that the rules they put into place in their company do not interfere with the System Development Life Cycle (SDLC). Providing any IGA legislation enhances and facilitates the SDLC then it is likely to be supported by the guys at the coal face—your development team.
Good IGA will focus on system and data access control, which in turn will result in greater workflow automation. This will improve the company’s bottom line, which will also make management happy. Shorter Agile sprints will produce faster product time-to-market, which, along with greater regulatory compliance, will make everyone happy!
However, there is the issue of scale. Smaller organizations will be able to implement IGA best practices quickly. For larger organizations, it’s more of a challenge. However, with the meteoric increase in identity theft, there seems no way of avoiding the inevitable—”change gonna come.” The sooner every organization makes provision to implement IGA and comply with government requirements, the better.

Yes, of course, your company could just ignore IGA. If you haven’t had any major cyberattacks or data leaks yet then maybe you’re just flying below the radar. Why go to all of that expense and trouble? Well, aside from ignoring the demands of your regulatory authorities, which will inevitably cost your company time, money, and business in the future, why not be more positive? Just look at the benefits to your business if you implement a comprehensive IGA policy.
For a start, you’ll be able to sleep at night without worrying about exposed cloud access vulnerabilities. Next, you can rest assured that nobody in your company has access to data they are not supposed to. It is not unheard of for disgruntled employees to steal their former company’s treasures when they depart their employment, for whatever reason.
Another big plus of a secure IGA policy is enablement. During the great COVID-19 pandemic, many workers were encouraged to work from home. This has created enormous challenges for companies who had to ensure the security of their employees’ remote access to data, systems, and architecture.
Another advantage would be placing automation as the focus of your company’s workflow. The more flexible, adaptable, and secure your company’s SDLC is, the greater benefits your company will reap in terms of competitiveness and profitability.
The IGA solution supplied by Spectral ticks all of the boxes mentioned in this article. Their Fast Code Security for Code and Cloud product will:
Spectral takes minutes to install—
Yes, it’s that simple! So, if you think it’s time for your company to move forward with IGA, then get in touch with Spectral.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Part of the Spectral API Security Series Yelp.com is one of the most influential crowdsourcing sites for businesses. The company is worth just over one billion