Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
As the basis of pretty much every consumer system available today, Discretionary Access Control (DAC) is everywhere and used by everyone. The files on your computer, the media and applications on your smartphone, and even your social media content. They all use DAC to manage permissions. That’s in part because DAC is easy to manage and understand. But DAC also has a few glaring issues when it comes to cybersecurity.
Not everyone is security-aware, which leads to people unwittingly granting strangers access to their systems, devices, personal data, and potentially to an entire organization. Unsurprisingly, trojan horses, which account for 58% of all computer malware, end up finding their way into people’s systems by way of DAC.
But how does DAC work? Is DAC right for your organization? Do the pros outweigh the cons? Can you shore up the weaknesses using other security principles or tools? Let’s explore the answers in this blog.
Discretionary means that access decisions are made “at the discretion” of the users that have access to the data. If a user has access privileges, they may bestow the same level of access privilege onto another user. Most commonly, each object has an Access Control List (ACL) that the owner manages. This fine-grained access control is intuitive and flexible, allowing fast data flow across organizations.
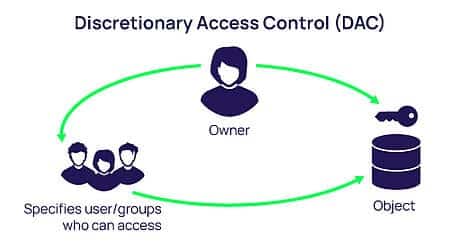
DAC works like life: If I have the keys to my house, I can let anyone I want inside. I can make copies of the keys and grant access to other people. Computer systems have evolved to allow the owner to revoke access rights, which is harder to do with keys. But the basis remains the same: the person with access can grant access to others.
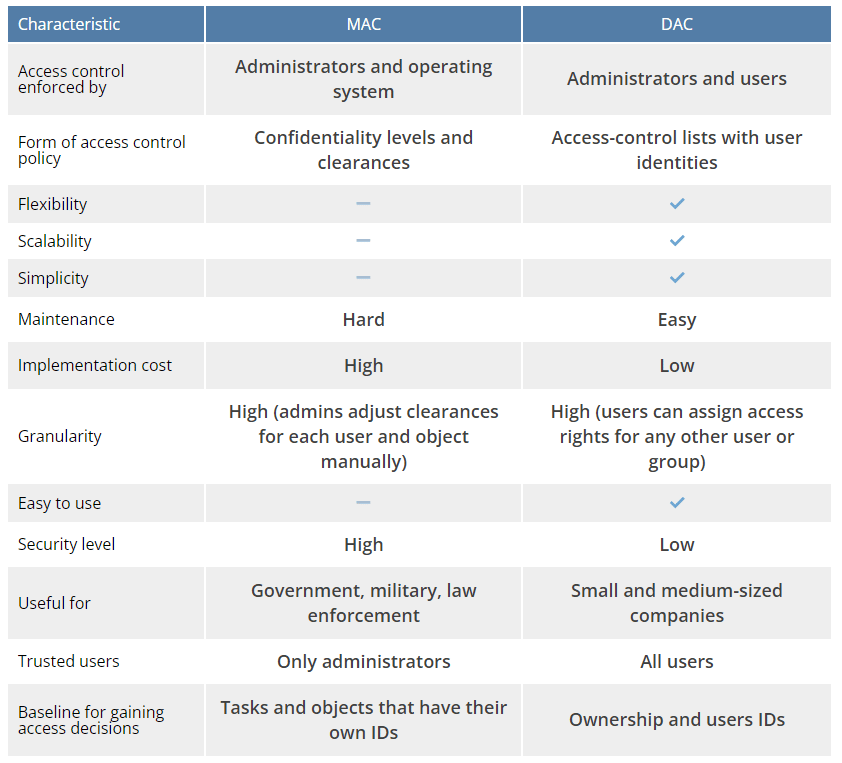
With this in mind, DAC contrasts against Mandatory Access Control (MAC), a form of identity governance based on a clearance level. A more strict form of Identity Access Management (IAM), MAC is straightforward and works like in the movies: An agent at a secure facility has a level 6 security clearance to access anything level 6 or lower. If they try to access a level 7 asset, they will be met with the dreaded “ACCESS DENIED.”
MAC requires the administrator to grant individuals security privileges and assign a security level to every asset. It is an administratively intensive security system that should be employed if security is critical.
Because DAC is a common form of access control, there’s no shortage of use cases that are relevant and helpful. There are many different ways to maintain and manage DAC, and you’re almost certainly familiar with some of the DAC systems listed below. Let’s go:
Many social media networks allow users to limit or regulate access to the content they create. Facebook’s friend list can be used like an ACL, essentially allowing anyone on the list to view content. The platform doesn’t allow users that see friend-locked content to share the data easily, so users with access to data don’t necessarily have the right to grant access to other users.
In social media networks, DAC allows the data owner to decide who can or can’t view it.
You can see Google’s DAC system in all their document creation services, such as Google Docs and Google Sheets. The owner and creator of the document can grant access privileges to the document on several different levels. Viewing permissions will not allow a user to modify the document, but Editor permission will allow the user to modify the content and to further grant access to the document to other users at their discretion. The original creator of the document can also transfer ownership of the document.
In each document, you can see the ACL and who the owner shared it with. The document owner can revoke user access but doesn’t have to manually grant permission to every new user unless they choose to maintain such control.
Computer file systems and UNIX, in particular, use the DAC model for read, write, and view permissions of files. Like many systems that use the DAC security policy, UNIX systems assume file ownership and allow the file owner the discretion of assigning permissions to the file.
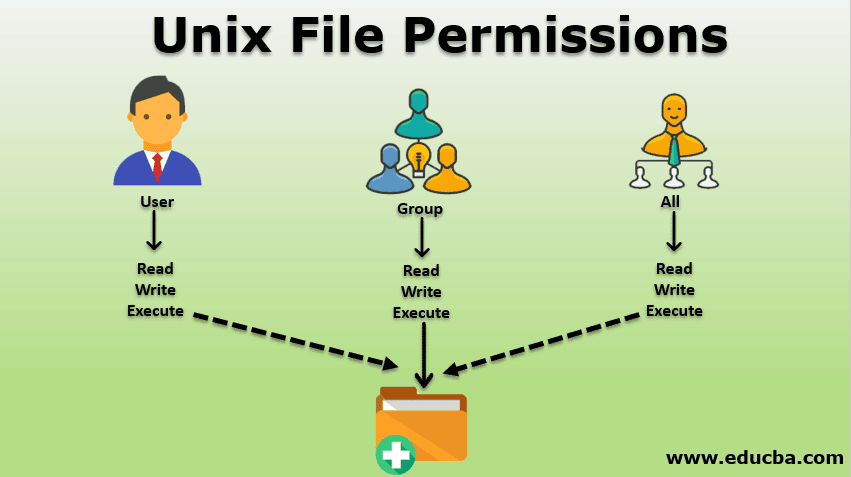
However, according to the TCSEC standard definition, ownership is not mandatory for DAC. You can have users with the relevant security clearance access and grant access to files regardless of the original owner.
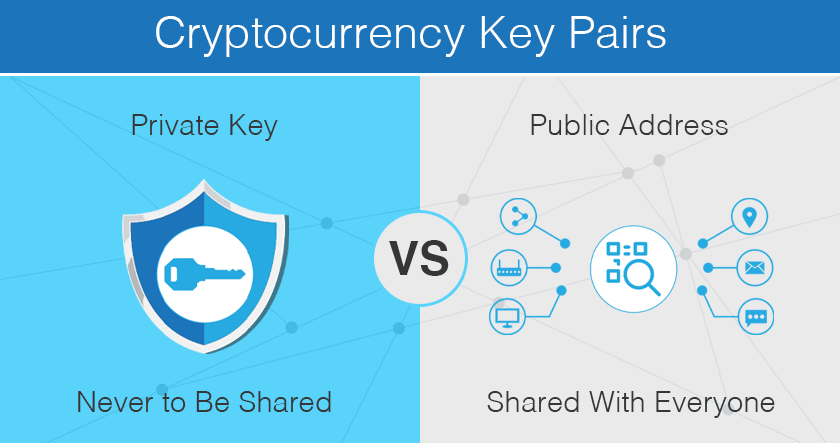
A capability-based system is a form of DAC without ownership designed to do away with the centralized ACL in favor of a decentralized solution. In a capability-based security system, the address of the object you refer to is also the key to accessing it.
The most common use today is cryptocurrency, where the private key to your wallet is the secret key granting you the right to transfer your currency to other wallets and the wallet’s address. The public key to your wallet, the address you can give out to people that wish to transfer money to you, is also a capability, but one that only grants access to sending money to rather than from.
Another example of capabilities is hidden URLs. When you upload an image to Imgur, Imgur will direct you to a private address that grants edit access to the image. The image URL will be different from the one used for editing privileges and will only give viewing privileges. If you save the editing URL, you can later access your editing rights to the image without signing in to Imgur.
You can also use capabilities to enforce the principle of least privilege (PoLP). When using a MAC security policy, anyone with the relevant level of security clearance can access everything at that level or lower. In contrast, capabilities allow for fine-grained access control, which upholds the PoLP.
Scripts are potent executables that can perform complex operations. The author of the script, known as a writer, sends the script to the user, known as the reader. The reader can then execute the script to perform the actions defined by the script. The obvious security concern is that the script is executed with the reader’s access privileges, which can compromise the reader’s files.
Scripts such as these were prevalent in the old days of the internet. They could be found in Excel Spreadsheets, Emails, web browsers, or even directly downloaded to perform a specific task, such as modifying a computer’s registry. Those scripts were run as trusted scripts, granting full access to the scriptwriter, and would often result in compromised systems. These days scripts are prohibited from any I/O outside of a specific public folder by default. This restricted I/O policy is known as untrusted script execution.
When combining the concept of DAC with script-based systems, you allow the user discretion over which permission to grant the script. For example, Excel’s access control is discretionary and let’s users decide if they can trust the script’s source. You can give an Excel spreadsheet different levels of permissions based on how much you trust the source.
A typical example of DAC that everyone is familiar with nowadays is smartphone applications. The application author must request permission to perform any potentially insecure operations, and the user must manually grant these permissions. If the application requires access to your location, contacts, or media folders, granting those permissions is at the user’s discretion.
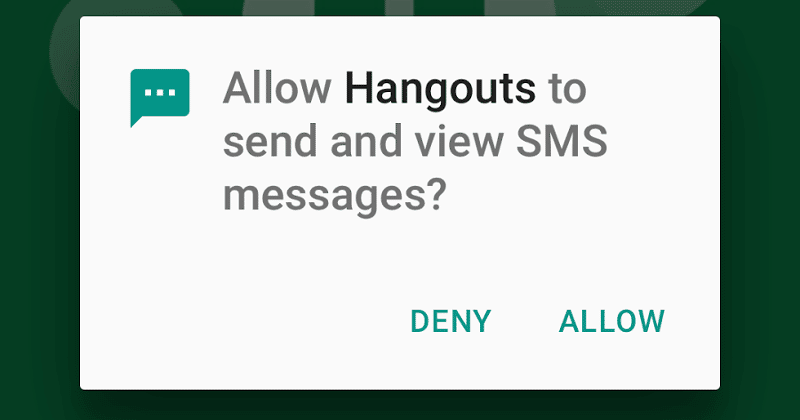
Applications that request permissions for operations that seem unnecessary to the application’s process can raise suspicions of malicious intent. Users can also manage the access control of applications after granting permission and revoking any granted access.
DAC is used for smartphone applications because it is easy to understand and manage. Most users intuitively understand how to operate ACLs on their phones, even if they aren’t technically fluent.
DAC is often the natural way to perform access management. It’s simple, easy to maintain, flexible, fine-grained, and user-friendly. DAC allows information to flow freely to whoever needs it without having to go through the process of granting credentials or verifying the security levels of new personnel. With this in mind, DAC makes data flow more easily than other systems, lending itself to be useful in the context of startups and small businesses that rely on fast and dynamic workflows where team members need easy access to information without causing headaches to administration.
But DAC may not be suitable for every organization as it has some glaring security flaws and doesn’t provide the high level of data protection many organizations require. Because DAC makes information flow easily, the security concerns of DAC are particularly relevant in large organizations where thousands of individual employees might be object owners.
Access management is challenging to govern due to the decentralized nature of ACLs. But all hope is not lost; you can maintain the benefits of DAC while shoring up the weaknesses with passive scanners. Spectral’s AI-driven scanner can protect your data from leaking into the wrong hands by ensuring attackers can’t easily find high-risk secrets in shared resources. Furthermore, Spectral can help prevent Trojan horses from finding their way into your organization via script. To start protecting your organization with a high-end scanner, try Spectral today.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions