SAST vs DAST: Which one do you really need?
Security testing? Ain’t nobody got time for that. Or budget. Or the necessary skills to align coding practices with organizational and regulatory compliance efforts. Developers are
In October 2022, data center construction reached a record high, reflecting our reliance on collecting, storing, and securing data. This reliance permeates businesses across all industries and puts pressure on data centers storing and processing large amounts of data–much of which is sensitive.
Financial records, personal information, and intellectual property are some examples of sensitive data businesses are reluctant to hand over to a third party because falling into the wrong hands or becoming compromised in any way would have serious consequences for the organization and its customers. But as reliance on data increases, so does the cost of storing and managing it internally.
Meanwhile, data breaches continue to rise and even established organizations, such as Uber and Medibank, experience severe data breaches and lose data records. Understandably, 76% of corporate data centers are concerned about data security. Serving as the backbone of organizations’ IT operations means that any breach or disruption in data centers’ operations could hamper regular business and lead to financial losses. Maintaining a high standard of data center security standards is essential.

Data center security standards are the guidelines and protocols that guide how data centers function and how they protect users’ sensitive information. There are various standards, both official and unofficial, that data centers use to regulate their security practices and enhance efficiency of their data centers.
Each organization can individually select the standards it follows, depending on the specific industry or needs of the organization. One of the most popular standards used is the one developed by the National Institute of Standards and Technology (NIST), a non-regulatory government agency belonging to the U.S. Department of Commerce.
NIST’s standards cover information technology, supporting applications, and data center infrastructure, focusing on cybersecurity and information security. Other popular standards include the International Standards Organization (ISO) and the Telecommunications Industry Association (TIA). These organizations set the security requirements organizations must follow to upgrade or harden their security.
In this blog, we discuss some of these essential data center security standards. First, to appreciate their relevance, let’s look at some of the threats your organization’s data center may be facing.
Data centers play a key role in an organization’s internal and external operations by hosting applications, storing and processing customer and employee data, and including components for critical operations such as networking, computation, storage, and more. Data centers play a critical role in your organization’s infrastructure, and you need to be aware of the threats they face to provide the security posture they need. The main threats that put data centers at risk can be divided into two primary categories:
Data centers are composed of a complicated infrastructure that includes three components: computing, storage, and network functionality. Attacks that target this infrastructure impact the data center’s availability, performance, and security. To protect against these attacks, data centers are pre-designed with defenses against infrastructure attacks and vulnerabilities.
Part of the function of a data center is to host both internal and customer-facing applications, which can be targeted in a variety of ways, including:
Data center security standards are essential for any organization planning to maintain a high level of security within its data center. This is especially applicable to organizations that host and manage their own data center to support their operations, or organizations that use a data center to store vital information and sensitive data. In other words, these criteria cover almost all organizations regardless of industry since storing data on paper has been replaced by storing it in on-premises or cloud servers.
From financial organizations storing sensitive payment information to medical organizations storing patient health data, security is a priority across all industries. Even organizations using a cloud provider need to proactively ensure that their environment meets the latest security standards. In short, every organization that uses a data center should ensure its IT, DevOps, and security teams have a clear checklist and guidelines to ensure that their security is never compromised.
Security standards provide a clear set of guidelines your IT, DevOps, and security teams can follow to ensure your data remains secure. Following well-known and respected standards will give your customers the confidence to entrust you with their most sensitive data. In some cases, for businesses in the financial and medical industries, ensuring compliance with certain standards is a legal requirement, and a breach could result in legal action and costly fines.
Even when not mandatory, data security standards can help accomplish the following goals:
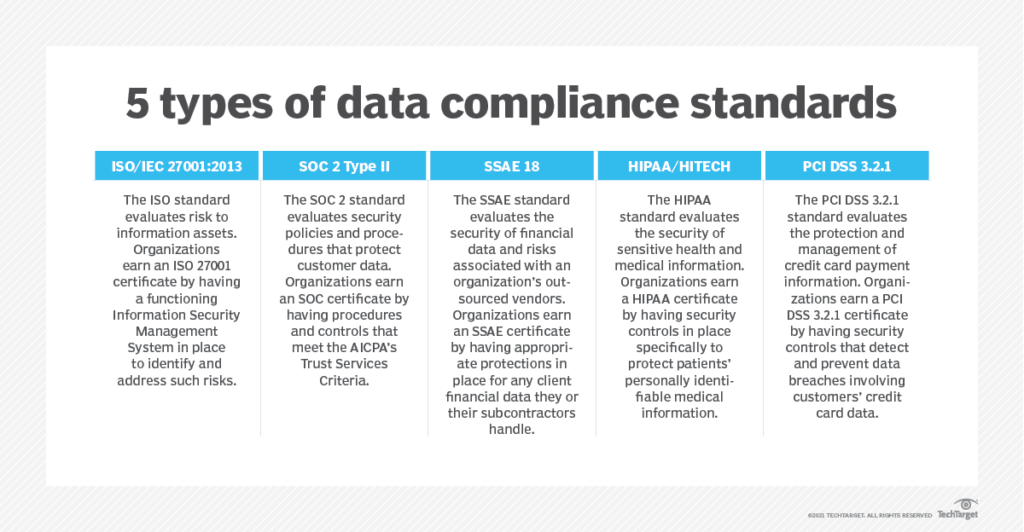
While the data center security standards you choose to follow may be individual to your organization or industry, several key security standards should be implemented to maintain a high level of protection. The standard you choose will vary based on regional and industry regulations, but some of the most common include:
This standard is used internationally to outline the best practices for implementing the world’s best-known information security management systems (ISMS) and their requirements. Additional best practice in data protection and cyber resilience are covered by 47 other standards in the ISO/IEC 2700 family.
The SOC standards are used for auditing that evaluates the current controls and processes used to protect the security, availability, and confidentiality of data in the data center. There are typically four types of SOC reports, although SOC 1 and 2 are the most commonly sought.
Finding out which SOC is relevant to your organization depends on the nature of your business. For example, the SOC 1 report is relevant for businesses operating in the finance sector, since it certifies their capability to efficiently and securely manage customers’ financial data. The SOC 2 on the other hand is more all-encompassing and could be relevant to most businesses operating online, since it serves as proof that the organization has procedures in place to ensure the security, integrity, and processing efficiency when dealing with sensitive customer information.
This set of standards applies to any organization that processes, stores, or transmits users’ credit card information. It includes various requirements on how to secure data centers and other components involved in managing payment card processing and information storage, and these requirements are frequently updated.

The NIST 800-53 set of standards are controlled by the NIST institute and include a 7-step process that any organization can use to manage information security and privacy risk for organizations and systems. It also links to a suite of NIST standards and guidelines to support the implementation of risk management programs necessary to meet the requirements of our next item, the Federal Information Security Modernization Act (FISMA).
Launched in 2014, this set of legal standards were an update to the Federal Government’s Cybersecurity Practices. They codify the role of the Department of Homeland Security in administering the implementation of information security practices of federal executive branch civilian agencies. In other words, they were designed to protect information and information systems, including data systems, that belong to the federal government.
This standard is specifically relevant for the medical industry and includes requirements for defending the integrity, confidentiality, and availability of electronically protected health information (ePHI) stored in data centers. It was launched in 1996 as a federal law in the U.S. to protect sensitive patient health information from being disclosed without the patient’s consent or knowledge.
Implementing data security standards is a must for avoiding the harmful consequences of data breaches, including financial loss, reputation damage, and potentially legal consequences. But simply implementing these standards once isn’t enough. As technology evolves, the methods attackers use to exploit system vulnerabilities and data centers also become more sophisticated. As a result, your security standards must be regularly reviewed and updated to ensure they remain effective against the latest security threats. This may seem like a massive undertaking, but it should be seen as a gradual, essential step to guarantee your security methods remain effective.Luckily there are automated tools that can help you manage this task. Spectral is a developer-first security solution that helps keep your data secure at all times, automatically. With hundreds of detectors constantly scanning and monitoring your environment for vulnerabilities, Spectral protects your data center infrastructure without slowing down your development process. Request a demo today to learn more.

Security testing? Ain’t nobody got time for that. Or budget. Or the necessary skills to align coding practices with organizational and regulatory compliance efforts. Developers are

Recently, Amazon accidentally exposed information on Amazon Prime Video viewing habits to the public. In addition, Thomson Reuters news and media company admitted that their servers

Adopting cloud technologies is one of the most common tech strategies followed by modern organizations. This may be due to various reasons depending on the nature