The Complete Guide to the Yelp API
Part of the Spectral API Security Series Yelp.com is one of the most influential crowdsourcing sites for businesses. The company is worth just over one billion
If you read the news, you’ve encountered the term “Magecart” multiple times in recent years. The term refers to several hacker organizations that use online skimming methods to steal personal information from websites, most frequently customer information and credit card details on websites that take online payments.
E-commerce platform Magento, which offers checkout and shopping cart capabilities for store websites, served as these groups’ initial target, which inspired the name. Its codebase is still an alluring target for hackers trying to scrape credit card data, steal personal data, or cause significant harm to various organizations.
If a Magecart group steals administrator and user login information, they may extend the attack and infect further websites. For instance, a Magecart group compromised not just the primary site but also the retail sites of seven European countries during the Vision Direct intrusion in November 2018.
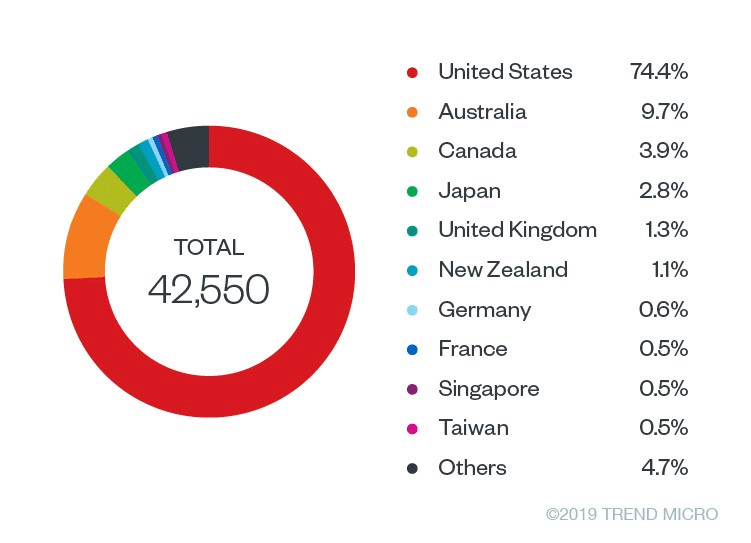
Thousands of customers’ personal information, including payment card numbers, expiration dates, and CVV codes, were exposed due to that attack. An exploited critical vulnerability, CVE 2016-4010 is well described in NIST database.
British Airways also suffered an attack of the same type during a public campaign that cost the firm more than $1B to recover from. The UK authorities have fined it £20M. Examples abound of why today’s website developers must take preventative steps to safeguard against card skimming attacks. Let’s have a look at how they can do that.
Based on ImmunWeb studies, at least 20 distinct Magento extensions were discovered to share a common vulnerability in October 2018, and Magecart was targeting all of them. The malicious code was inserted thanks to a PHP Object Injection attack that took advantage of the unserialized() function in PHP.
A similar vulnerability existed within the Magento platform, resolved by switching out the PHP unserialize() function for json_decode(). Sadly, the extension’s creators did not follow suit.
At the time of disclosure, researcher Willem de Groot was aware that 20 extensions were under attack, but he was unsure which ones. He had only found two. The Webcooking_SimpleBundle Magento extension was the first, and it was reported to the creator and corrected within hours. The author had given up on the second, TBT_Rewards, months before. It must be replaced because this cannot be repaired, exposing the serious issue with legacy software.
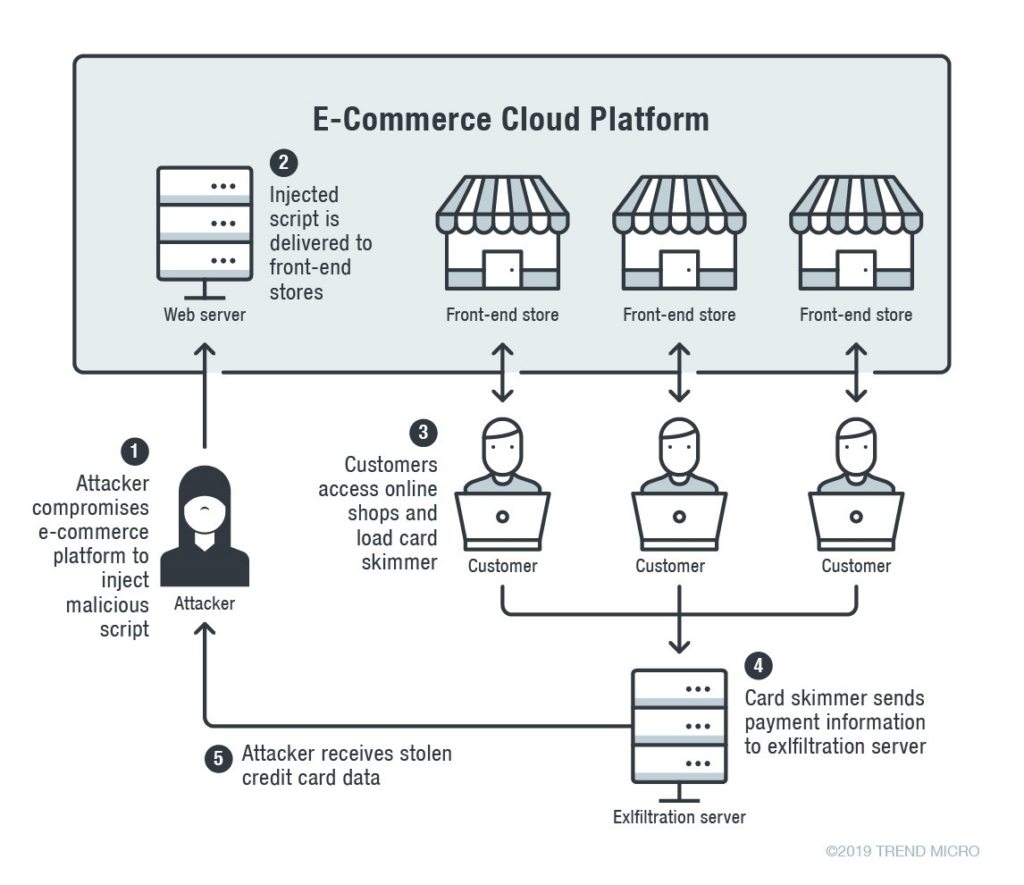
A similar object injection technique was comprehensively reviewed in October 2019 by Trend Micro. A skimmer used the flaw to exploit the store front end by copying its complete payment form, including the victim’s name, address, phone number, e-mail address, and credit card information (number, cardholder name, expiration month, expiration year, and CVV number).
The skimmer serializes the copied data into a string and encrypts it using Base64 after getting credit card information. The encoded string is then subjected to a character permutation to ensure it cannot be immediately decoded using Base64 decoding.
There was a 26% increase in Magecart assaults between 2021 and 2022, with 5.5 million attacks total registered in 2022 alone, according to a new analysis by RiskIQ. Statistics for 2022–2023 reveal a considerable rise in their prevalence. As long as thieves continue to target unprotected websites that handle payment information, this trend is anticipated to last through 2023 and beyond.
Businesses and customers alike may suffer serious consequences due to these attacks. Attackers can steal financial information, including credit card details, from unwary customers by inserting malicious code into a website’s checkout page. This may result in monetary loss, identity theft, and harm to the reputation of the company and the client.
For website developers, this means putting strong security measures in place, frequently checking their websites for suspicious behavior, and keeping abreast of the most recent trends and dangers in the field of cybersecurity. If they don’t, their firm and clients could suffer severe consequences.
Any web application that manages financial transactions must secure payment and credit card information. The following are some best practices for protecting web apps from payment data and credit card scam attacks:
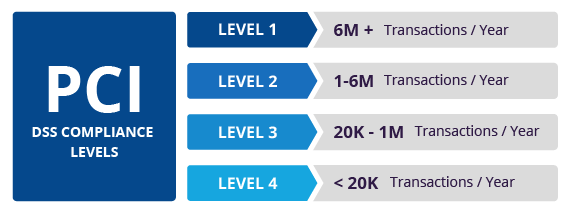
Several libraries can help developers achieve PCI DSS compliance in their applications:
Here is an example in Python evolving Flask-Security lib.
Step 1: Install Flask-Security and its dependencies using pip:
pip install Flask-Security
Step 2: Define a User model that inherits from Flask-Security‘s UserMixin class:
from flask_security import UserMixin class User(db.Model, UserMixin): id = db.Column(db.Integer, primary_key=True) email = db.Column(db.String(255), unique=True) password = db.Column(db.String(255)) active = db.Column(db.Boolean()) confirmed_at = db.Column(db.DateTime())
Step 3: Configure Flask-Security by setting the required options in your Flask application’s configuration:
app.config['SECURITY_PASSWORD_HASH'] = 'bcrypt' app.config['SECURITY_PASSWORD_SALT'] = 'my-salt' app.config['SECURITY_CONFIRMABLE'] = True app.config['SECURITY_EMAIL_SENDER'] = 'noreply@example.com'
Step 4: Initialize Flask-Security by creating an instance of its Security class:
from flask_security import Security, SQLAlchemyUserDatastore user_datastore = SQLAlchemyUserDatastore(db, User) security = Security(app, user_datastore)
Step 5: Add authentication and authorization to your Flask application’s routes using Flask-Security’s login_required and roles_required decorators:
from flask_security import login_required, roles_required
@app.route('/dashboard')
@login_required
def dashboard():
return 'Welcome to your dashboard!'
@app.route('/admin')
@roles_required('admin')
def admin():
return 'Welcome to the admin area!'
Step 6: Use Flask-Security‘s forgot_password and reset_password views to implement password reset functionality:
from flask_security import forgot_password, reset_password
app.add_url_rule('/forgot', 'forgot_password', forgot_password)
app.add_url_rule('/reset/<token>', 'reset_password', reset_password)
Step 7: Implement multifactor authentication using Flask-Security’s two_factor extension:
from flask_security_two_factor import SMSFactor, EmailFactor
app.config['SECURITY_TWO_FACTOR'] = {
'SMS': SMSFactor,
'Email': EmailFactor,
'default': ['SMS', 'Email']
}
In order to protect the stored cardholder data, you should first install, configure, and maintain a firewall. Make sure your environment is set up with a VPC (Virtual Private Cloud) and that public DMZs and private subnets are properly segregated.
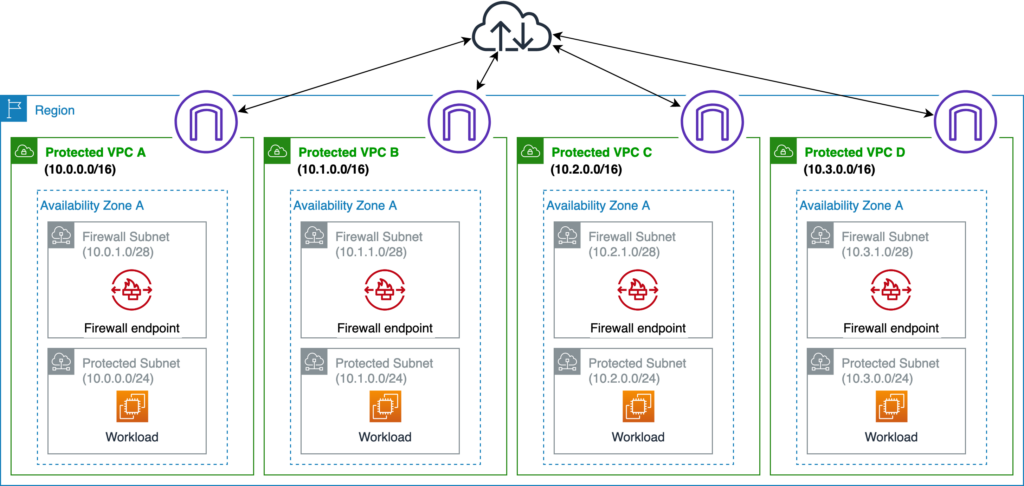
Additionally, for an additional layer of security, you can use Unified Threat Management (UTM) solutions in the public subnets, otherwise known as DMZ. A systematic process must be followed before any adjustments to the configuration of the network or any tool can be made.
The default password provided by a service provider or vendor should be immediately changed if you are using their services. A service should request a password each time it is restarted. It is necessary to remove unwanted scripts, packages, and services from the instances. You must ensure that each instance you use supports just one function before using it.
There are two components to this step: physical access and virtual access:
Physical security is a key aspect of information security, regardless of how effective the established security controls or approaches are. A cutting-edge security system, for instance, serves no purpose if it is installed on the street in front of your business. A strong physical security system is required to protect technical systems. More than half of the work is already done because your application is based on AWS and is already PCI-DSS compliant.
Strict identity and access management (IAM) policies must be put in place for virtual access in order to provide access to only a few people who need it to complete their job.
In the PCI DSS QuickStart reference implementation, “firewalls” are equivalent to security groups and “networks” are represented by Amazon VPC subnets. Consequently, the security group list, the security group rules, and the subnet configuration might all be used as proof of the segmentation borders.
The accounts that have access to your AWS management console should be properly defined in an IAM policy. An IAM policy should have the following clauses:
Ensure CloudTrail is enabled for logging. It should be enabled and configured with at least one multi-Region trail.
We’ve discussed how skimming attacks occur, their consequences for businesses and customers, and best practices for protecting web applications–from using SSL/TLS encryption and implementing PCI-DSS compliance to avoiding storing payment information on servers and regularly performing vulnerability assessments.
As for developers, they should have two strong weapons in their arsenal to prevent their web apps from being used by malicious actors: One is a strong knowledge of specialized libraries for popular programming languages in web development and the ability to apply their classes and methods in practice. The other is an automated way to monitor, classify, and protect your code, assets, and infrastructure for exposed API keys, tokens, credentials, and high-risk security misconfigurations in a simple way, without noise. Request a demo and get started now.

Part of the Spectral API Security Series Yelp.com is one of the most influential crowdsourcing sites for businesses. The company is worth just over one billion
Unity is by far the most popular game development engine out there. Its user-friendly world view lets you add objects to the game scene and immediately

Git and GitHub are almost synonymous when it comes to code repositories and version control. However, the majority of developers under-utilize these two tools and just