Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Software developers face a constant barrage of cyber threats that can compromise their applications, data, and the security of their organizations. In 2023, the cyber threat intelligence (CTI) market is worth approximately $11.6 billion, and it’s projected to surpass $21 billion by 2027. Why?
The rising number of cyber-attacks driven by remote and hybrid work environments, along with the development of cloud computing, have reshaped the threat intelligence market – particularly by increasing the attack surface, as many employees now use their own devices for work purposes cumulated with the fact that they have less secure home connections.
To effectively safeguard their systems and maintain a robust cybersecurity posture, developers must equip themselves with a comprehensive understanding of cyber threat intelligence (CTI) and the tools and techniques employed by adversaries.
This practical guide delves into the six essential components of a Near Perfect CTI (Cyber Threat Intelligence) Framework, providing software developers with the knowledge and skills they need to establish a robust and effective CTI program within their organizations. It serves as a roadmap to help developers transform their CTI capabilities, enabling them to anticipate threats, protect their systems, and foster a culture of cybersecurity resilience.
A Cyber Threat Intelligence Framework is a set of processes, tools, and practices that enable organizations to gather, analyze, and act on information about potential cyber threats. It is a proactive approach to cybersecurity that helps organizations identify and mitigate risks before they can cause damage.
A reactive approach to cybersecurity can have severe consequences for an organization. The average cost of a data breach in 2022 was $4.24 million.
The framework consists of three main components:
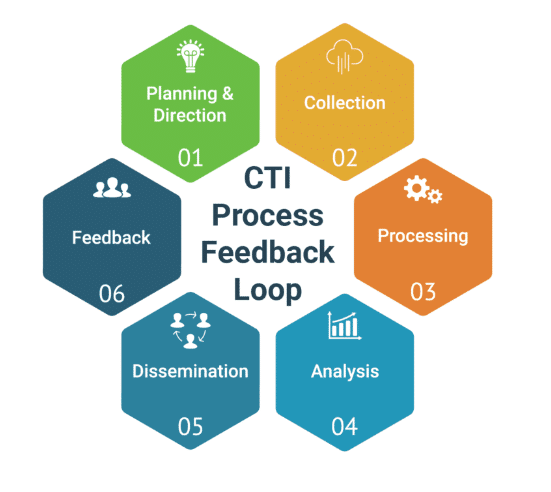
Assessing the digital threat landscape is foundational to building a robust cyber threat intelligence framework. It is essential to understand potential sources of cyber threats and collaborate with security experts to identify and prioritize potential risks. Microsoft Security Insights recommends starting with a comprehensive inventory of the data and systems that need protection and then setting specific goals for the threat intelligence framework.
The inventory should include all the hardware, software, and data that are critical to the organization’s operations. This information can be used to identify potential vulnerabilities and prioritize the most critical assets. Once the inventory is complete, the next step is to identify the potential sources of cyber threats. This can include external threats such as hackers and malware, as well as internal threats such as employee negligence or malicious intent.
After identifying potential threats, the next step is to collect actionable intelligence.
A comprehensive approach is necessary, combining various intelligence sources to gather relevant and timely insights. This includes open-source intelligence, human intelligence, and technical intelligence.
Here is a comprehensive rundown of how different types of intelligence impact your CTI.
Open-source intelligence (OSINT)
Human intelligence (HUMINT)
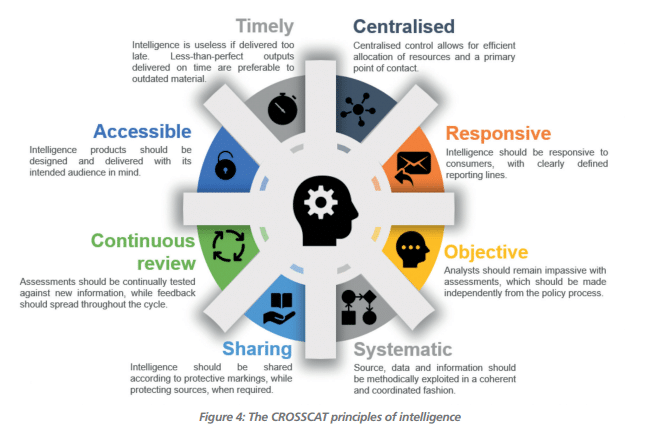
Interpreting and analyzing gathered intelligence is a crucial phase of building a robust Cyber Threat Intelligence Framework. Collaboration with multiple teams to gain diverse perspectives is essential, in addition to achieving cloud compliance.
Analytics tools can be utilized to derive actionable insights. These tools can help organizations to identify patterns and anomalies that are indicative of a cyber attack. Machine learning algorithms can be used to detect and prevent cyber attacks by analyzing large amounts of data. Artificial intelligence can be used to identify patterns and anomalies in network traffic, which can help to detect and prevent cyber attacks.
Here are some quick points on how to interpret and analyze your data.
Threat Intelligence Platform (TIP)
Multi-team Collaboration for Comprehensive Threat Understanding
Formulating adaptable security strategies based on derived insights is pivotal. Effective countermeasures and incident response plans must be developed while highlighting the need for continuous adaptation in response to evolving threats.
Continuous adaptation in response to evolving threats is essential. The cyber threat landscape is constantly changing, and organizations must be prepared to respond quickly and effectively to emerging threats. By demonstrating the value of CTI, organizations can secure the necessary resources to develop and maintain a robust Cyber Threat Intelligence Framework.
So, what can your team do to implement this?
Vulnerability and Risk Identification for Effective Cyber Defense
Executing devised plans and integrating innovative solutions is critical to building a robust Cyber Threat Intelligence Framework.
Seamless coordination between various teams is essential for integrating innovative solutions. This includes security teams, IT teams, and business teams. Each team can provide valuable insights into potential vulnerabilities and risks.
Here are some points that can be employed.
Risk Mitigation Through Effective Execution of Countermeasures and Incident Response Plans
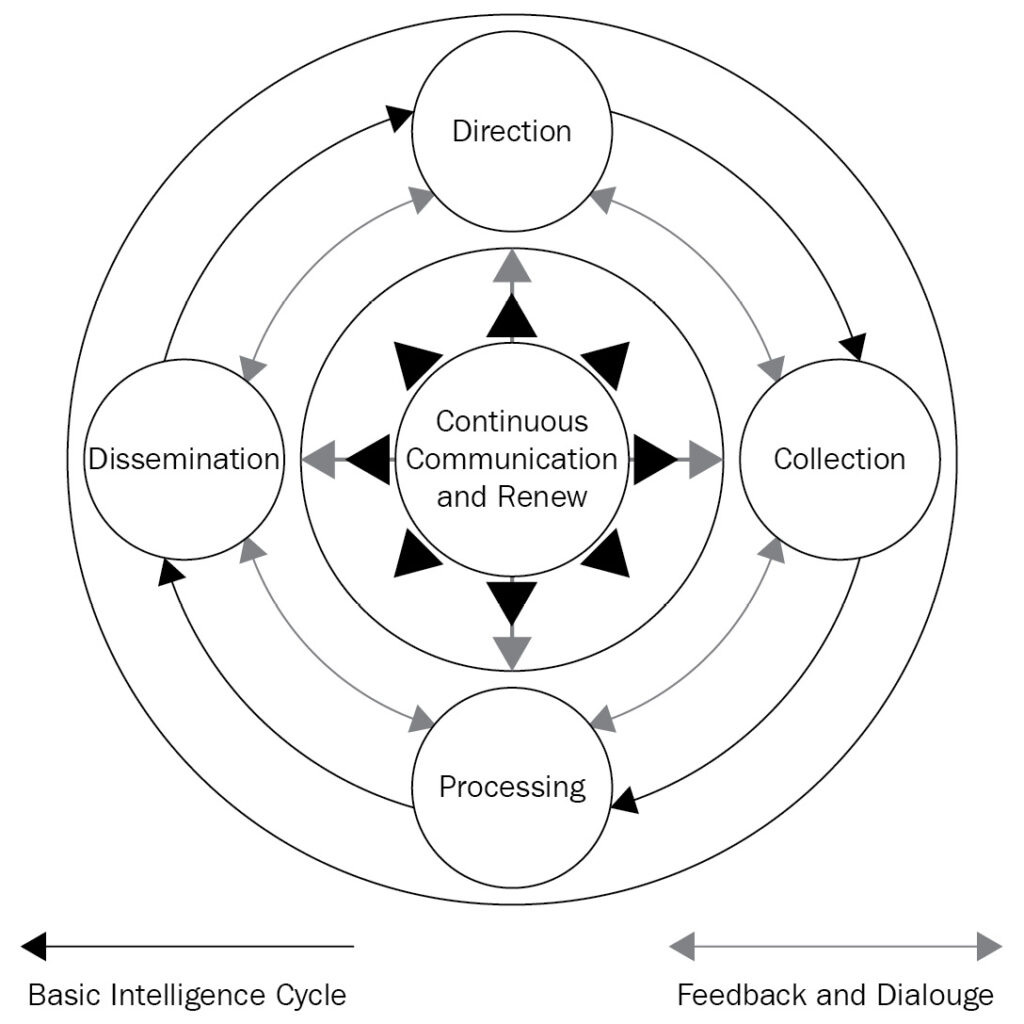
Continuous monitoring and enhancement strategies are necessary for response to the dynamic threat landscape. Regular evaluations and feedback loops are essential to maintain and enhance cyber defense capabilities.
This includes monitoring network traffic, analyzing gathered intelligence, and identifying potential vulnerabilities and risks. By continually refining cyber threat feeds, organizations can stay ahead of emerging threats and protect sensitive information from potential attacks.
Evolving Cyber Threat Landscape Demands Continuous Adaptation
Innovative solutions play an increasingly crucial role in addressing specific cybersecurity challenges. These solutions are designed to proactively contribute to a robust Cyber Threat Intelligence Framework.
SpectralOps is one such unique solution that is transforming the cybersecurity landscape. Its developer-first approach empowers developers to build and ship secure software with confidence. SpectralOps’ scanning engine combines AI and hundreds of detectors to help developers monitor, classify, and protect their code, assets, and infrastructure from exposed API keys, tokens, credentials, and security misconfigurations.
Machine learning, artificial intelligence, and blockchain technology are also being used to address specific cybersecurity challenges. For example, machine learning algorithms can be used to detect and prevent cyber attacks by analyzing large amounts of data. SpectralOps leverages machine learning to identify patterns and anomalies in code, configurations, and other artifacts in real-time, enabling developers to fix harmful security errors before they can be exploited.
In safeguarding digital assets and ensuring uninterrupted business operations, a well-structured Cyber Threat Intelligence Framework assumes paramount importance. Encouraging organizations to explore and integrate advanced solutions becomes imperative to fortify their cybersecurity defenses against the relentless evolution of cyber threats.
By embracing these strategies, institutions can proactively identify and counter threats, establishing a robust defense system that adapts to the ever-shifting cyber landscape.
SpectralOps is one such advanced solution that can help you stay ahead of the curve and protect your organization from cyber threats. Get started for free here.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions