Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
The reality of cybersecurity is simple – breaches will occur – and reactivity will always be the losing strategy. Having a cyber resilience framework shifts the focus from preventing attacks to ensuring readiness, mitigating impact, and driving a swift return to operations.
With the average data breach costing millions – like it or not – cyber resilience is no longer optional.
But how do we translate ‘cyber resilience’ into actionable steps? It starts with a framework.
A cyber resilience framework provides a structured approach for organizations to prepare for, manage, and recover from cyber threats.
Traditional cybersecurity approaches often focus solely on preventing breaches. In contrast, a resilience framework recognizes that attacks are sometimes inevitable. It builds on preventative measures with a comprehensive focus on incident response and business continuity planning.
A solid cyber resilience framework ensures that an organization can minimize the impact of a cyberattack, swiftly return to normal operations, and meet regulatory requirements.
The components of a cyber resilience framework include: Risk prevention, Risk management, and Employee training.
The benefits of a well-structured cyber resilience framework are: Minimized disruptions, Reputation protection, Streamlined compliance, and Competitive advantage through customer trust and confidence
A tailored cyber resilience framework is your ultimate risk management tool. The following steps will guide you in identifying risks, preventing potential security issues like secrets leakage, how to implement safeguards – and ultimately – lowering your organization’s overall cyber risk profile.
Every organization is different. Having a tailored cyber resilience framework that meets your needs is crucial. Here are the five steps to building one.
A cyber resilience framework shifts your approach from reacting to threats to anticipating them. This first step lays the foundation for implementing targeted, preemptive security measures within your personalized cyber resilience framework.
Asset Identification for risk assessment is not just servers and code. Knowing your digital crown jewels means a comprehensive view of:
Utilize:
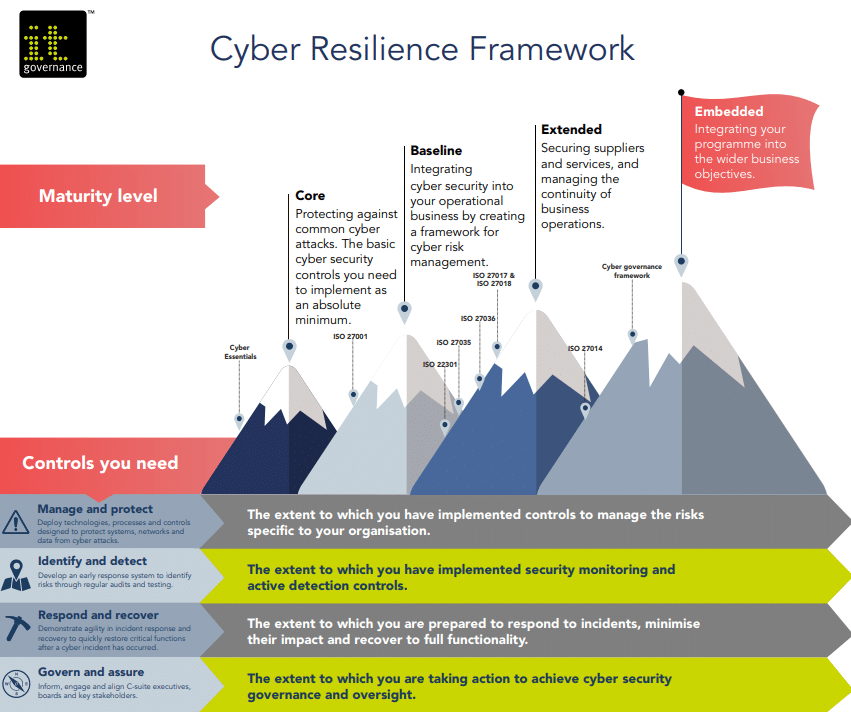
Use frameworks and regulations to help with your risk assessment. Here are two frameworks that can increase your cyber resilience.
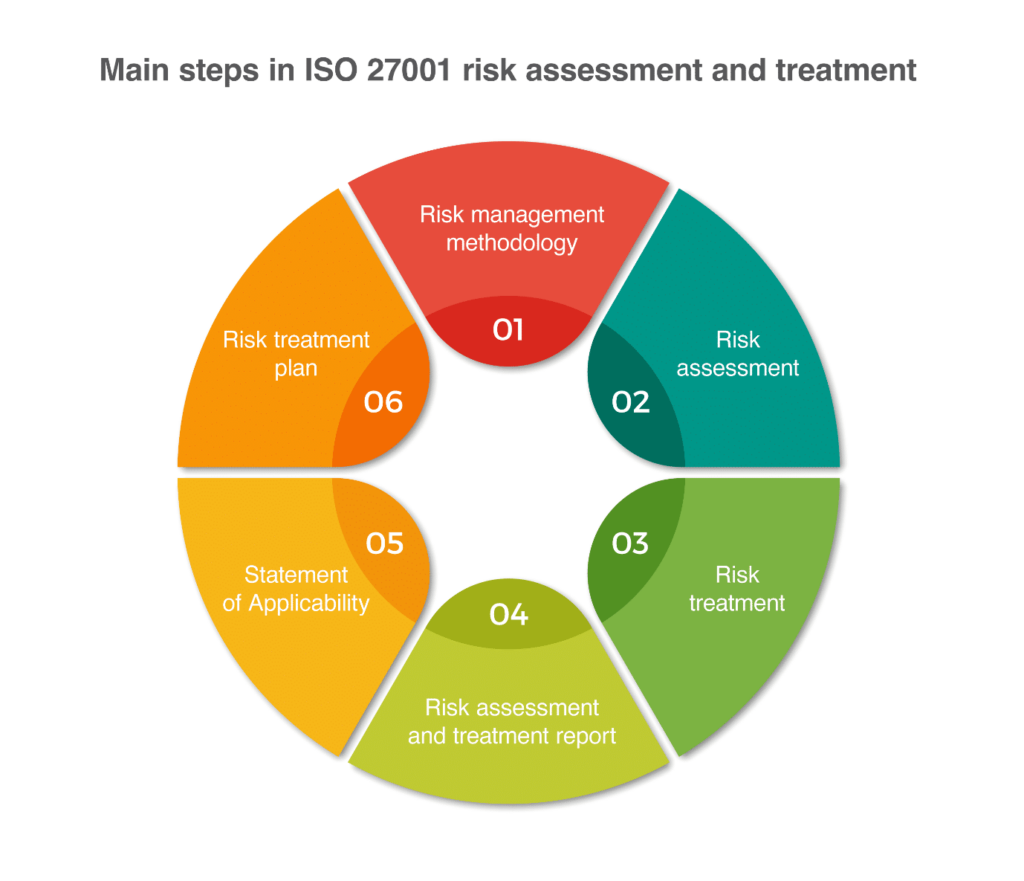
Your risk assessment exposed potential vulnerabilities across your systems and processes. Now, let’s address those weaknesses proactively.
Here are the security controls and tools that you need.
A comprehensive risk assessment goes beyond identifying assets and vulnerabilities. To further understand your defenses through the attacker’s eyes, integrate the MITRE ATT&CK framework into your process. Mapping your security controls against this structured catalog of known adversary tactics and techniques offers a crucial perspective on your cyber resilience framework’s effectiveness.
Many industries have specific security benchmarks or standards (e.g., PCI DSS for payment data). Use them as guidance on critical controls to ensure your cyber resilience framework demonstrates compliance for business continuity.

Alerts without action are meaningless. This step will help you find the processes that aid your response when you see something suspicious. Building actionable plans around your monitoring tools strengthens your framework.
Here are the tools you can use for visibility and action.
Prevent risks like secrets leakage from ever emerging with seamless CI/CD security checks. With tools like Spectral, developers can scan without leaving their workflows, enabling early remediation and stronger secure-by-design practices.
From monitoring to mitigation, you should also keep these in mind:
Robust incident response playbooks are far more than generic plans. Craft detailed step-by-step guides outlining precise actions for each incident stage: containment, eradication, recovery, and analysis. Having this pre-planned approach minimizes frantic decision-making when seconds count.
Since not all threats are equal, develop clear response hierarchies to streamline vital triage and focus efforts on the most critical alerts. Define clear roles, responsibilities, and communication channels upfront, designating who handles breach response. This ensures the right people are swiftly engaged, empowering rapid, orchestrated reactions when needed.
Finally, prioritize your security logging practices:
In the inevitable event of a breach, your response speed and a structured process dictate the outcome. A cyber resilience framework focuses on bouncing back as swiftly as possible to minimize downtime, financial loss, and disruption to core operations.
Here’s how to develop a comprehensive response plan for your cyber resilience framework.
Your employees often represent either a strong defense or a significant vulnerability. They are your human firewall. This step is about turning your entire workforce into active participants in cyber resilience.
Here are the top awareness methods you can incorporate into your resilience framework.

Expose staff to realistic simulations of common attacks like phishing emails and spear-phishing. Training staff to identify these schemes turns users from victims into early warning systems.
Educate on robust password creation and multi-factor authentication. Train teams against social engineering tactics, ensuring staff are less likely to be deceived into giving up their credentials.
Promote secure data handling practices, secure remote working habits, and emphasize safe web browsing, including how to spot suspicious sites or downloads.
Establish straightforward, non-punitive ways for employees to report potential incidents or suspicious activity. Encourage a “see something, say something” culture to catch risks early.
Additional important considerations:
A culture of security starts at the top. Ensure executives communicate its importance and actively reinforce best practices to all teams.
Also, include partners or suppliers with access to your systems. Educate and monitor their security practices as part of your cyber resilience framework.
A comprehensive cyber resilience framework pays dividends. Beyond protecting critical data and systems, it minimizes disruptions, safeguards reputation, and streamlines regulatory compliance. It also transforms your security posture into a strategic asset, fostering adaptability and minimizing the impact of ever-evolving threats.
Hardcoded credentials, API keys, and other secrets embedded in code provide pathways for determined attackers. Spectral can help you tackle this head-on. Our AI-driven platform offers deep visibility into these potential risk areas, empowering you to take preventive actions and neutralize leaks before they become damaging breaches.
Ready to build resilience that pays dividends? Sign up today with SpectralOps and take the first step toward transforming your organization’s cyber resilience with powerful intelligence and actionable insights.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions