Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Security is the biggest threat facing organizations that strive for faster software delivery. Organizations are witnessing increasing attacks due to application code gaps and security weaknesses.
According to a Forrester report, software security flaws accounted for cyberattacks in about 47% of organizations. Scary enough, a Positive Technologies report also claimed that hackers could attack 9 out of 10 web applications tested for vulnerabilities through theft of credentials, malware injection, and phishing attacks.
As a result, experts believe organizations have yet to take security seriously. Many lack basic adequate protection practices like multi-factor authentication.

As attackers develop sophisticated methods to exploit web application vulnerabilities, developers need to concentrate on implementing security efforts throughout the software lifecycle. In this article, we understand the importance of Web Application Security (Web AppSec) and what developers can do differently to protect their web applications moving forward.
Web AppSec is a software security paradigm that enforces security controls to protect websites, web applications, and assets from cyber threats. It demands that developers build resilient applications that can withstand sophisticated cybersecurity attacks.
Like any instance of software, web applications contain defects and bugs. One primary source of such security risks is the software supply chain, where developers use open-source and third-party code, which may have vulnerabilities. These vulnerabilities can expose your web servers and applications to cyber threats. Web applications are at risk because users must interact with the application network and servers. It could be emails, video streaming, or online shopping.
Any kind of security lapse can prove fatal if it is too easy to manipulate web apps with malicious intent. Although testing plays a critical role, testing alone just doesn’t cut it. You will have to implement strict security measures throughout the SDLC to ensure that you address every flaw in your app.
With software development moving to the cloud, web applications have become the norm for businesses. However, this also introduces new security challenges. Developers tend to overlook aspects related to security. According to Wakefield Research, a shocking 70% of organizations tend to forget or skip at least one security step. The modern software development approach enables you to infuse security into all the phases of SDLC.
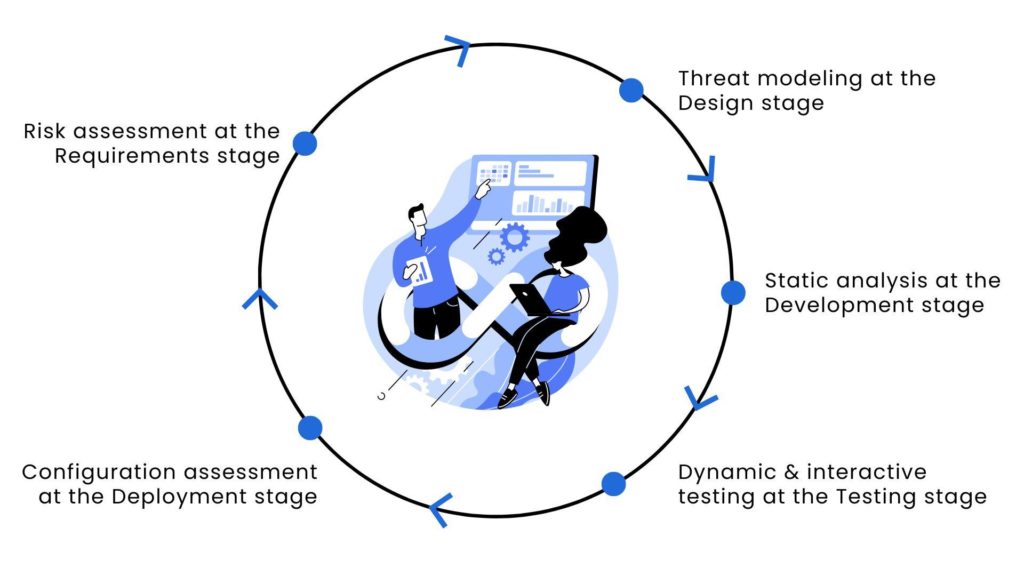
When you’re outlining your software requirements, it is necessary that you also consider security specifications—identifying risks and their sources, analyzing the harm they can do, and defining a remediation strategy. It helps you understand the criticality of assets that need to be protected and determine policies to avoid confidentiality and integrity breaches.
You must review the design when selecting application frameworks and architectures to avoid flaws and defects. Through in-depth software architecture analysis and functional specifications, you can implement strategies like threat modeling to weed out unsecured designs and risks.
Embedding security best practices includes applying secure coding guidelines to ensure the creation of high-quality code and conducting code reviews through automated static analysis. Watching out for the security risks from open-source libraries and dependencies is also critical.
While the code analysis begins in the development stage, the testing stage is the most critical section of the SDLC to ensure security-first software development. Through dynamic and interactive testing, you can effectively identify vulnerabilities that may have slipped past the development stage.
Web application security doesn’t end at the testing stage. It goes well into the deployment stage, where you must perform periodic assessments to evaluate system configuration and security controls. You can use strategies such as penetration testing, vulnerability scanning, and red teaming.
For many developers, security testing is restricted to the testing stage of the development pipeline. But as we discussed earlier, it can start well into the development stage and extend until the application is shipped. For robust website AppSec, four types of testing approaches are recommended:
DAST is an AppSec testing methodology where you assess a web application from an ‘outside-in’ perspective; i.e., you scan the application and its associated structures without any visibility into source code, technologies, or frameworks. Also known as ‘black box security testing,’ DAST helps you identify security threats like SQL injections and cross-site scripting. This security testing method allows you to prioritize risks and plan remediation strategies to reduce AppSec risk.
It is a crucial security test method because DAST attempts to find exposed vulnerabilities and lets you understand how they can be exploited so that you can plug those holes.
Unlike DAST, SAST will scan your application’s source code, bytecode, and binary code through an inside-out approach. With static analysis, you can access frameworks, design, and implementation methodology, but you don’t have to run the application. Known as ‘white box security testing,’ SAST is a developer-centric AppSec strategy. You can implement early in the SDLC to identify existing and third-party vulnerabilities before the code is added to your software. It provides real-time feedback, which makes incorporating best security practices easy.
SAST enables you to implement remediation against risks faster through an automated workflow for continuous code scanning. It allows you to find defects on the go, making fixing vulnerabilities relatively less expensive.
Penetration Test is a type of Web AppSec testing practice where you simulate a cyber attack to identify application weaknesses. The attacks can be triggered against servers, protocol interfaces, or other critical application systems. Penetration testing can identify security threats such as authorization issues, business logic loopholes, and workflow gaps. It is executed in five stages:
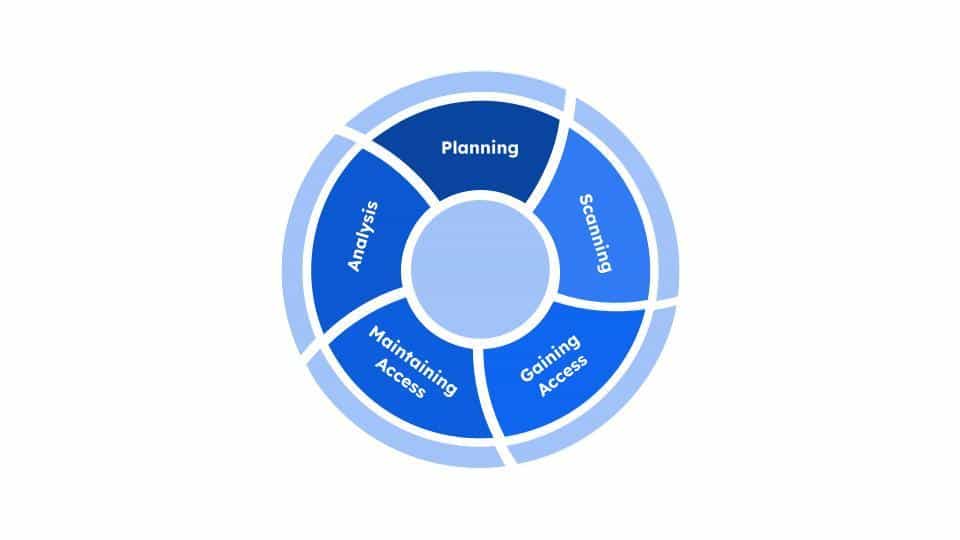
Penetration testing helps you build a resilient web application to tackle security challenges when implemented with a mix of manual and automated approaches.
RASP is a security tool that runs with the application in the runtime environment to validate incoming requests to ensure Web AppSec. It continuously monitors application behavior and provides an essential layer of security around the application. RASP can raise alarms when a threat is detected and protect the application even when the network is compromised by terminating the user session.
However, the challenge with RASP is that it could potentially lead to lazy security practices with increased confidence in self-protection.
In the current market weather of an increasing number of cyber attacks, being proactive in security is necessary. You can’t wait for an attack to occur because the consequences don’t just involve financial loss but also reputational damage, which may take even longer to recover from. Through Web AppSec, you can be a step ahead in identifying vulnerabilities, improving the security posture, and designing strategies to remediate before a breach causes damage.
Below are some examples of common attacks listed by OWASP (Open Web Application Security Project), a non-profit institute that works towards improving software security:
Quite a few organizations fail to implement programs to secure sensitive data like authentication credentials, passwords, and credit card details. Such confidential data can allow malicious agents to steal identities and data and commit financial fraud.
You can avoid exposing sensitive data by implementing HTTPS and PFS (Perfect Forward Secrecy) for incoming requests to your sites. It is also essential to disable data caches that store secrets.
Some security misconfigurations developers commit are outdated codebase, unpatched software, unused web pages, and insecure directories or libraries. They facilitate hackers to gain access to your web applications.
Updating your software regularly is a simple method to avoid misconfigurations. Automating the process will help you in preventing a hassle.
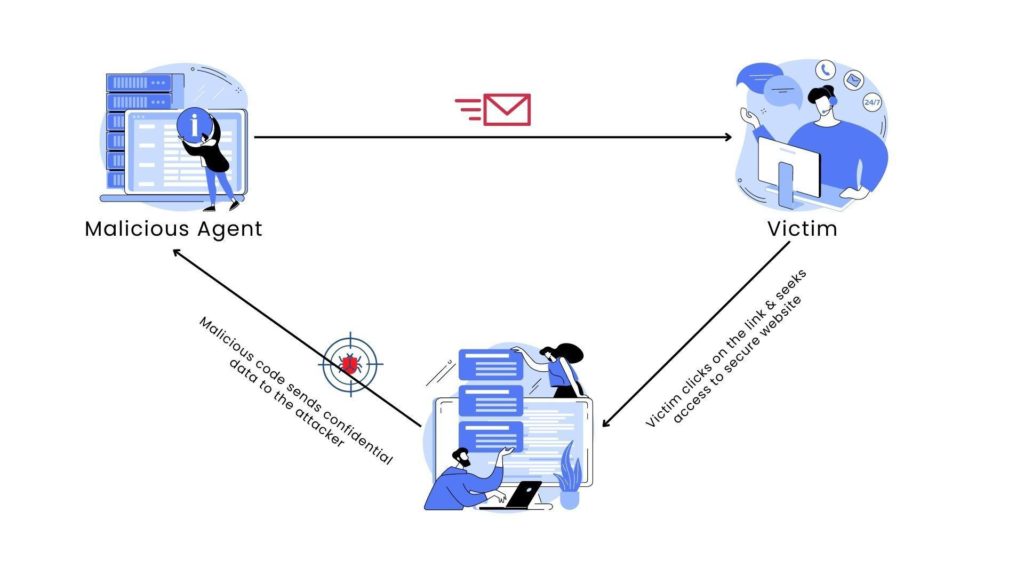
Attackers often lure people into clicking on malicious links that end up injecting hostile code through a process called cross-site scripting. Leveraging XSS vulnerabilities, hackers can access your microphones, webcam, location, and confidential data stored on your device.
You can effectively prevent malicious code from entering your system by validating user input.
SQL and LDAP injections are the two most common injection flaws hackers utilize to breach your databases or directories. They trick you into executing commands to access critical data by sending flawed data using a command query.
Using filters to variable protocols for all the query inputs can help keep injection attacks at bay.
Attackers can use multiple methods to gain access to your system and steal data by exploiting improper authentication practices like password stuffing, password leaks, and other vulnerabilities. Once inside your application, they can carry out any action that a genuine user can.
Multi-factor authentication is the best way to secure access to your web applications, alongside creating strong passwords, setting time-outs, and implementing strong identity governance practices.
You can avoid a great deal of nuisance by properly implementing security tests for the below features. Any lapse in doing so can generate vulnerabilities that can give attackers a potential crack to exploit.
Securing web applications is fast becoming a business goal for organizations as data breaches can create long-term repercussions. Web AppSec is a tremendous practice for you to protect your websites, databases, and applications. It involves developers taking charge of application security by continuously monitoring and testing their systems. Spectral empowers developers to simplify Web AppSec and make it a part of their everyday tasks.
Our developer-first tool seamlessly integrates with your existing CI systems to continuously scan and track known and unknown assets to stop data breaches before they happen, keeping your applications secure. The solution to preventing costly mistakes is now just a click away.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of