7 Steps to ensure compliance with the CJIS security policy
A high-profile case hangs in the balance. Suddenly, court systems are paralyzed. Evidence is locked away, replaced by a ransom demand. Every law enforcement agency’s nightmare
Logs tell the hidden story of your IT infrastructure – what’s working, what’s breaking, and what could be under attack. You’re left sifting through a chaotic stream of events, risking missed insights crucial for maintaining security and operational stability.
And the stakes couldn’t be higher. The average global data breach cost hit $4.45 million, with U.S. companies facing an even steeper $9.48 million per incident. Choosing the right log analysis tools can differentiate between a quick recovery and a multi-million dollar disaster.
Let’s look at the top log analysis solutions available, helping you decide which tool best aligns with your need for real-time monitoring, rapid troubleshooting, and robust security incident detection.

Automatically generated logs record the events happening within your systems. These structured data outputs capture vital details such as timestamps, event types, and contextual information – acting as your primary source of truth when identifying performance issues, tracking user behavior, debugging errors, and detecting security anomalies. Effective utilization of log data plays a crucial role in comprehensive cyber risk management strategies, enabling organizations to identify and mitigate potential threats proactively.
General log types include:
Log analysis is the process of taking all that raw log data, parsing it into something structured, and then running queries to spot patterns, correlations, and anomalies. It’s about turning a flood of disorganized log entries into searchable, organized data you can work with.
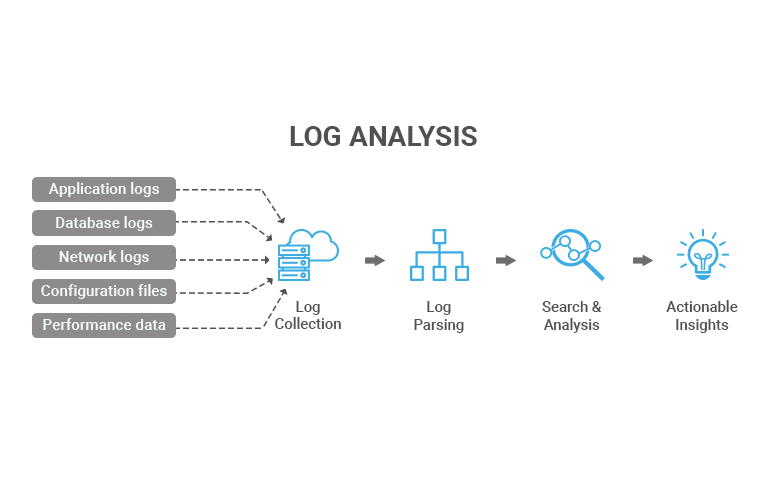
The concept of “shifting left” in security aligns well with the proactive approach that log analysis tools enable. The earlier in the development lifecycle that security considerations are addressed, the more effective and less disruptive the remediation process becomes.
Automated log analysis tools step in by handling the heavy lifting – processing data in real-time, integrating directly into your CI/CD pipelines, triggering alerts, and feeding into security dashboards.
As systems grow more complex, having the right tools to filter and secure critical information is vital. Efficient automation can significantly enhance the effectiveness of log analysis tools, enabling faster and more accurate identification of potential issues.
Here’s what to keep in mind:
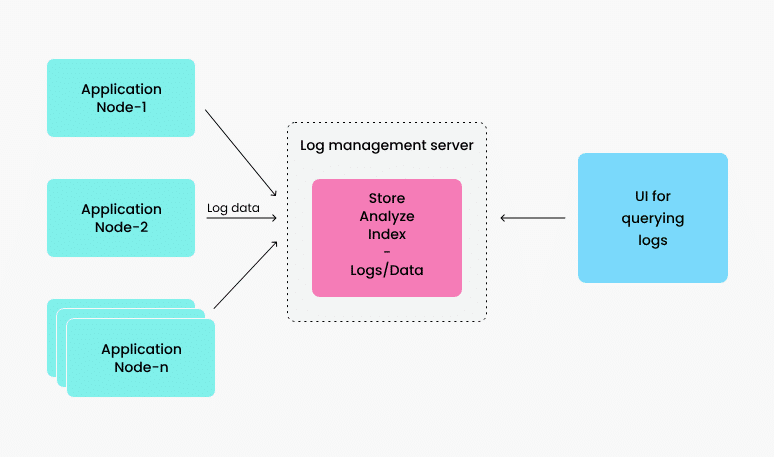
Log analysis tools generally fall into a few categories, often classified based on their architecture, licensing, and the problems they solve. Here are a few:
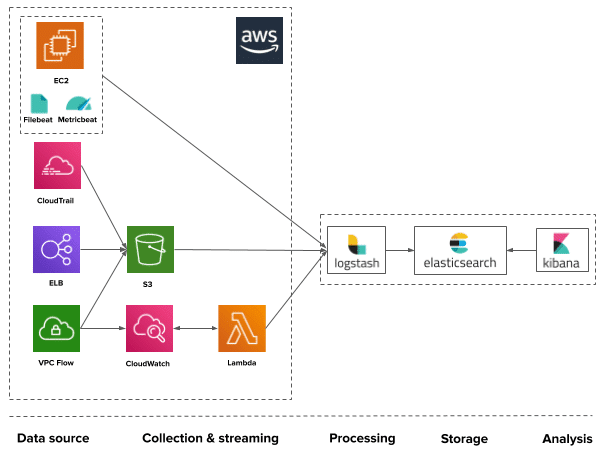
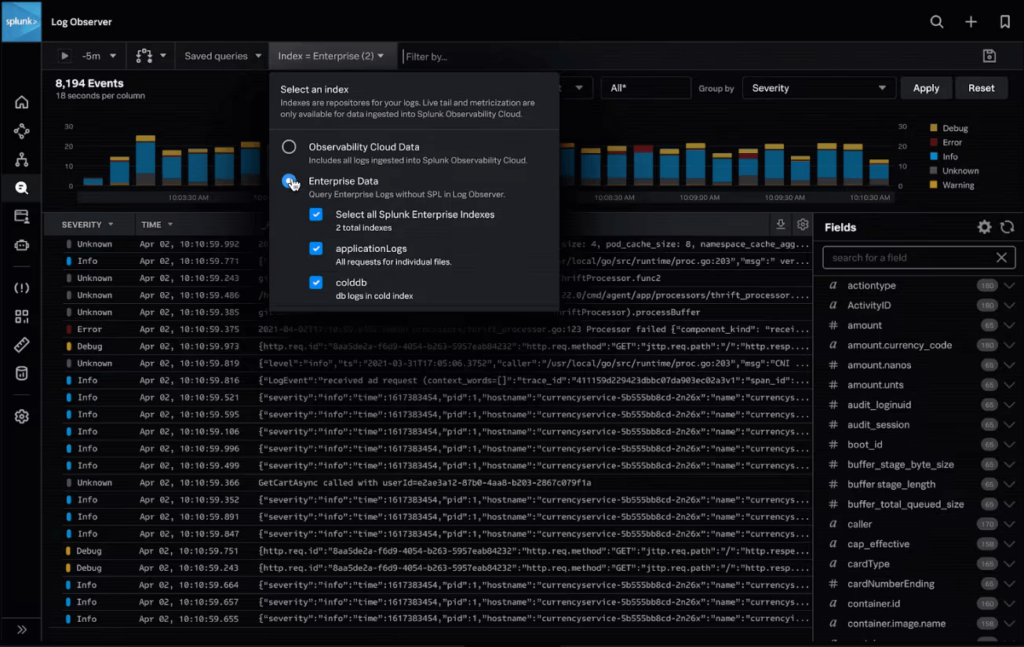
Splunk provides powerful indexing and search capabilities using its Search Processing Language (SPL) to dig deep into raw log data. Its distributed search architecture enables rapid querying across petabytes of data, which is crucial for time-sensitive investigations. The built-in machine learning toolkit automatically detects anomalies by learning patterns over time. With over 1,000 integrations, Splunk is highly adaptable no matter your IT stack.
Enterprises managing complex environments.
Subscription-based, with pricing depending on data ingestion volume; free tier available.
SpectralOps is a developer-centric security platform protecting the software supply chain by detecting hardcoded secrets, sensitive files, and infrastructure misconfigurations at every stage of development.
Teams focused on securing cloud-native environments, particularly those that must maintain strict compliance and prevent data sprawl in complex DevSecOps workflows.
Flexible pricing based on the number of monitored repositories, with options for both small teams and large enterprises.
Graylog is a log management platform built around real-time stream processing and rule-based log routing.
Teams that need granular control over log processing.
Free and open-source, with enterprise options starting at $1,250/month.
Datadog is a cloud-native platform for unified monitoring and log management with deep integration across cloud and container environments.
Large-scale SaaS enterprises with complex microservices architectures.
Pay-per-use for ingestion (GB) and indexing (per million log events).
Logz.io delivers a fully managed ELK Stack with added intelligence layers for log analysis that bolsters security and operational efficiency.
Growing enterprises and DevOps teams seek a scalable, low-maintenance log management solution.
Subscription-based, with pricing based on data volume. Free trial available.
Fluentd is an open-source log collector designed to stitch together log data from fragmented sources and route it to the correct destinations.
Small or mid-sized tech enterprises with globally distributed teams needing customizable log aggregation across multi-cloud environments.
Free and open-source. Managed cloud options available via Fluent Bit.
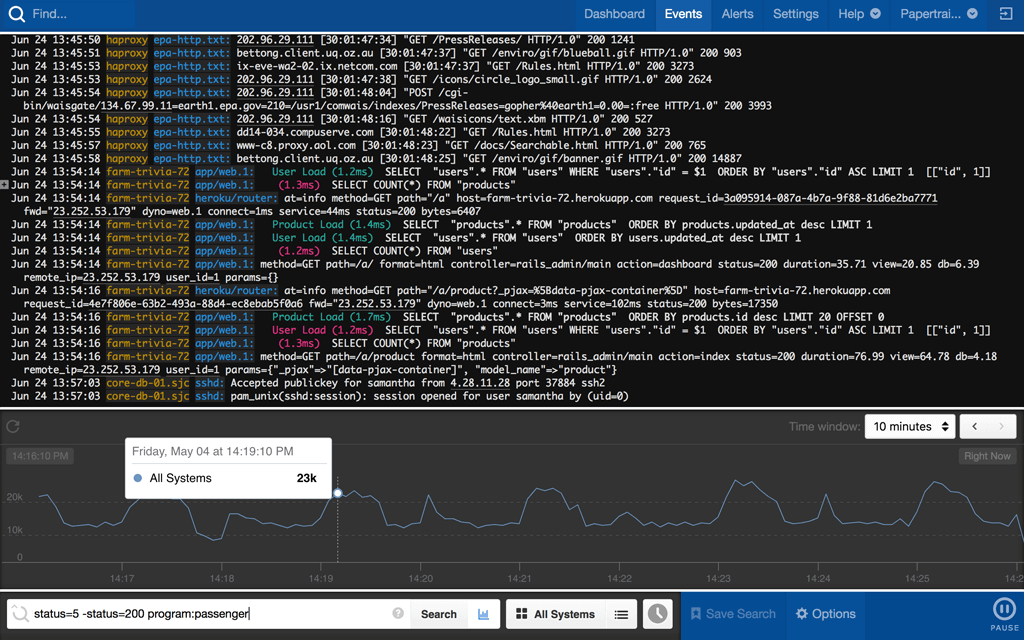
Papertrail is a log management service focused on quick setup and real-time search.
Small to medium teams with minimal setup needs.
Subscription-based, starting at $7/month with flexible pay-as-you-go options.
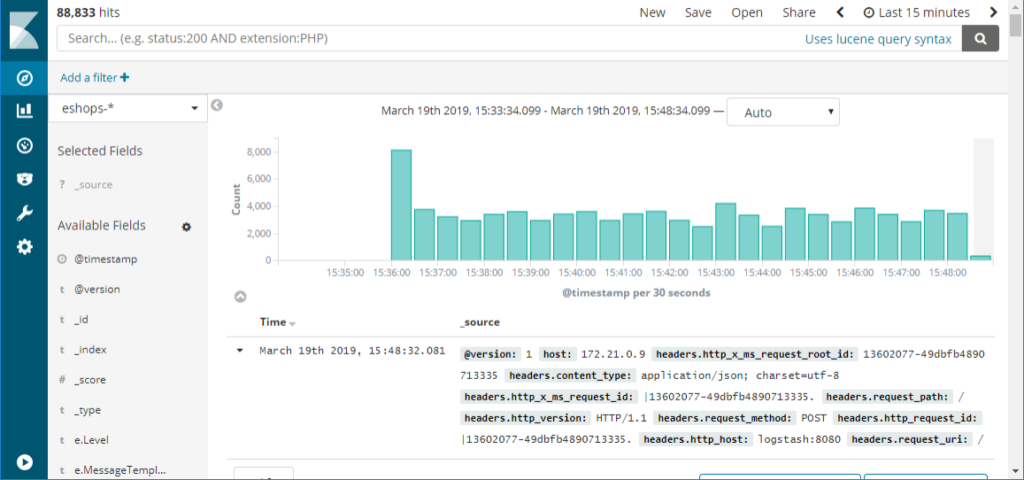
Elastic Stack (ELK) is an open-source log management solution that integrates Elasticsearch for search, Logstash for data processing, and Kibana for visualization.
Large enterprise managing self-hosted, large-scale log deployments that require granular control over data pipelines and visualizations.
Free and open-source, with paid enterprise support available.
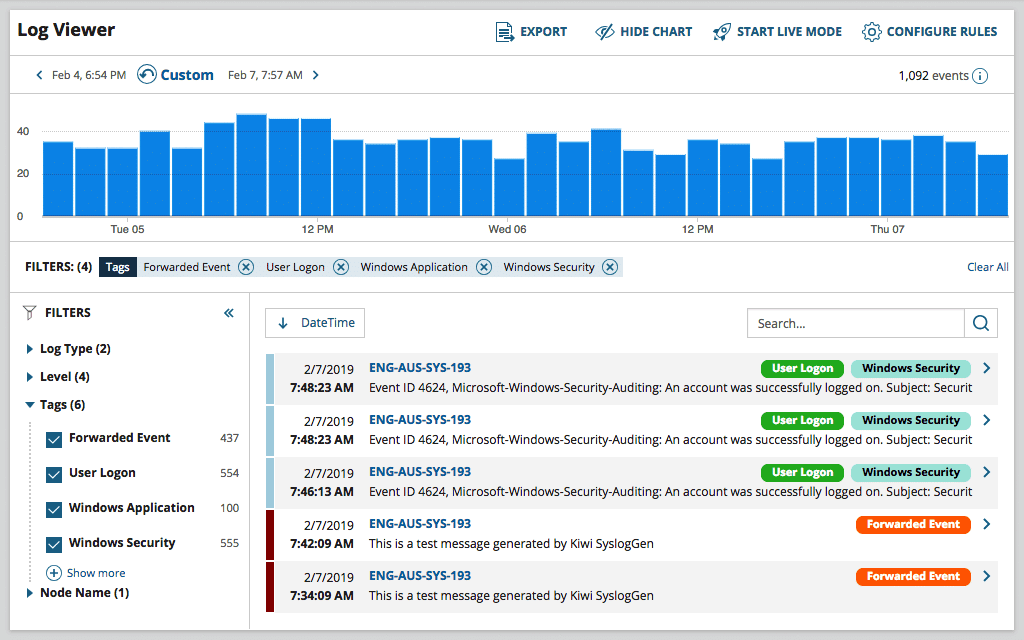
SolarWinds Log Analyzer is a centralized log monitoring solution that tightly integrates with the broader SolarWinds IT monitoring suite.
We are integrating log monitoring into an existing SolarWinds IT monitoring stack.
Subscription-based, starting at $986.
Log analysis is more than just sorting through data – it’s about making sense of all the noise to catch problems before they become crises. As systems grow more complex, having the right tools to filter and secure critical information is vital.
SpectralOps offers a unique solution by focusing on securing the software supply chain, with features like sensitive data detection in logs and advanced scanning capabilities that keep your code and configurations safe.
If you’re ready to level up your log security, explore Spectral and see how it can help avoid threats and maintain complete visibility.

A high-profile case hangs in the balance. Suddenly, court systems are paralyzed. Evidence is locked away, replaced by a ransom demand. Every law enforcement agency’s nightmare

Imagine a world where you can easily protect your company’s important data while ensuring compliance with strict security guidelines. ISO 27001:2022 promises just that. Because data

Have you ever built software without encountering a single vulnerability? Unlikely. Vulnerabilities are an unavoidable fact of DevSecOps life, and the stakes are higher than before.