Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
If you’re an IT manager or business owner, chances are external security is always top of your mind. But lately, managing access control of documents for employees has become just as necessary to limit access to information and information processing systems.
While cybersecurity breaches are a menacing threat, internal security problems can be equally devastating, making access control measures necessary to mitigate the risk of access without authorization.
As organizations migrate to the cloud and employees heavily rely on mobile and cloud-based storage, access control is becoming increasingly complex. There are 2 major problems here: First, employees need access to files in real-time to do their jobs. This becomes a problem when tech gets in the way as they can’t have access to all the data in a certain directory.
And second, employees sometimes copy sensitive data from a company account to their personal accounts. As difficult as it may be to believe, over 45% of employees admit to taking documents from former employers. As a result, we have access-control-allow methods coming into play mainly to alleviate cybersecurity concerns.
In this post, we will dive deeper into access-control-allow methods in its for most prominent manifestations.
Access-Control-Allow-Methods is a header request that is responsible for allowing one or more HTTP methods when accessing a resource in response to a preflight request.
Now, a preflight request is essentially a non-simple CORS request that is sent by the browser to ask for the server’s permission to send the actual request and check whether it will be allowed.
But to comprehend it better, we first need to understand what CORS is. CORS stands for Cross-Origin Resource Sharing which is a system for browsers that enables controlled access to resources located outside of a given domain, thus adding flexibility to the same-origin policy (SOP). It’s important to note that a poorly configured CORS policy can provide the potential for cross-domain attacks.
The Access-Control-Allow-Methods header follows 2 syntaxes:
Access-Control-Allow-Methods: <method1>, <method2>, …
Access-Control-Allow-Methods: *
Where the methods are from a comma-separated list of HTTP request methods and ‘*’ (wildcard) counts as a special wildcard value for requests without HTTP authentication information or cookies. When such credentials are indeed present in the requests, the symbol is treated literally without semantics. Here are a few examples:
Access-Control-Allow-Methods: POST, GET, OPTIONS
Access-Control-Allow-Methods: *
Access-Control-Allow-Methods are compatible with the following browsers:
Internet Explorer, Safari, Firefox for Android, and Safari on iOS also support these methods with the exception of the ‘*’ (wildcard) directive.
Logical access control, used to restrict access to data on a virtual level, leverages various authorization, identification, and authentication protocols. Let’s take a look at some of the methods that help in implementing logical access control:
Access Control Lists (ACLs) can be thought of as a set of rules laid out to mitigate network attacks and control network traffic by filtering the requests. They are also used to specify which systems or users have been granted or denied access to a particular resource. ACLs can be installed in switches and routers from where they filter the incoming traffic offering the extra advantage of improved network performance. They can also be attached to objects (a document, for instance) where the system then either grants full access, read-only access, or denies it completely for that object.
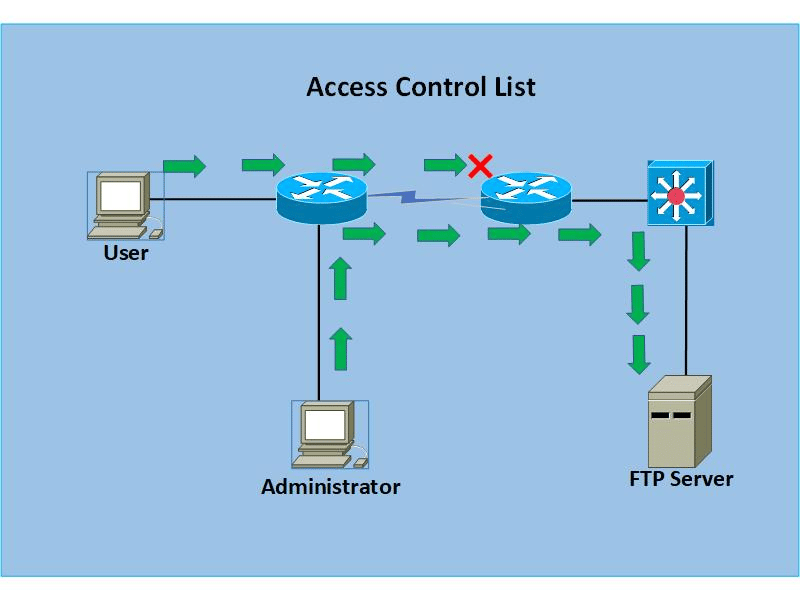
For various operating systems, ACLs are known as access control entry (or ACE) and are configured using four critical pieces of information. Namely: an access mask, a security identifier (SID), a set of flags for determining inherited permissions of the object, and another flag for operations that can be performed on the object.
As is apparent, ACLs have the potential to deliver extensive access control over networks and objects, but often they become complex when managing multiple objects.
Group policies, a part of the Microsoft Windows environment, make room for a centralized control point for managing access to a network of computers that use Microsoft Active Directory services. With centralizing, there’s no more need to configure access control for each system as these settings are cumulated as Group Policy Objects (GPOs) which make it convenient for the system administrator to configure and manage these settings.
Passwords are the most common logical access control methods and need to be complex enough to deliver essential access control levels. Common words are easy to crack and often subject to be done so by brute force attacks. To that end, it’s highly recommended to use secret management tools to store sensitive information and passwords.

Account restrictions serve as the fourth line of defense in the list of logical access control methods. While we now have tools to detect data leaks, account restrictions like the ones with a time-based cut-off and the ones with complete account expiration, time of day restrictions are prevalent because they limit access during certain hours, giving the admins the liberty to update the records without interference. On the other hand, account expirations ensure that old and unused accounts don’t get into the hands of cybercriminals.
Access control models are used to grant the right level of permission to individuals so they can perform their duties without hurdles, effortlessly. Here are four of the most widely used access control models:
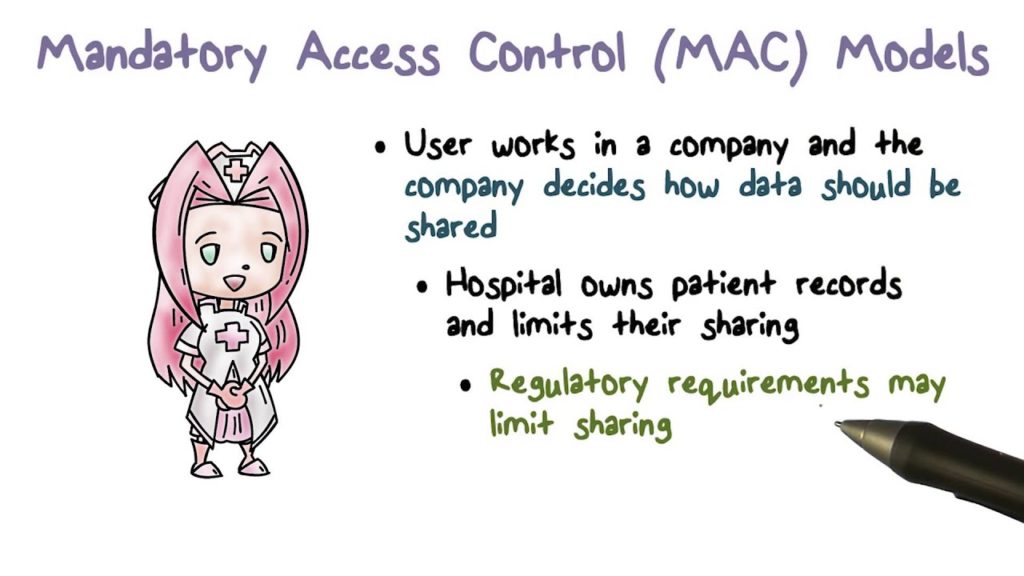
The Mandatory Access Control (MAC) model doesn’t offer the end user any control over the settings that set access privileges, giving only the custodian and the owner all the rights to manage the access controls.
We associate two well-known security models with MAC namely Biba and Bell-LaPadula. The Biba model is a system of data security policies for formal state transition that ensure data integrity. Here, data and subjects are ordered by their levels of integrity into arrangements or groups in a way that a subject doesn’t corrupt data in a level ranked higher than the subject’s and restricts data corruption at a level that’s lower. So, a user with low-level clearance can only read higher-level information but the user with high-level clearance can write for lower clearance levels.
The Bell-LaPadula model, on the other hand, focuses on controlled access to classified information and prioritizes confidentiality over integrity. Here, users at a higher level can only write at that level and not lower, although they have permission to read at lower levels. This model was originally developed for securing government and military facilities where individuals without correct clearance who also didn’t need to be aware of certain information, had no need to do anything with that information.
MAC has been time and again associated with a numbering system that assigns files and employees to certain levels, and the employees with a lower level than that of the document couldn’t access it.
Role-based access control (RBAC) model is used to provide access to individuals based on the position they fill in the organization. So, instead of giving each new employee new permissions, certain permissions are pre-assigned to the roles they occupy, making jobs much easier for system admins. But if the individual needs access to files other than what they already have permissions for, the security managers need to look for another manual workaround to give the individual access to the object.
Discretionary access control (DAC) is one of the most lenient of the 4 models in this list whereas MAC is the most restrictive. Organizations using DAC essentially allow individuals complete control over objects they own along with all the programs associated with those objects.

The end-user has complete authority to set security level settings for all the other users that have access to the same objects. This may lead to a disparity in access privileges. And again, the permissions that end-users possess are inherited into all the other programs they work with, making such programs prone to malware attacks. Issues such as these make DAC one of the weakest access control models.
Rule-based access control (or RuBAC) is used to dynamically assign access levels to users based on their roles as defined by the system admin or custodian. For instance, it’s the model to go for if the organization wants to set access controls based on the time of the day
As organizations adopt cloud services, managing access and permissions for employees has become overly complex. As a solution, in this post, we talked about how access controls can alleviate this issue. We covered what Access-Control-Allow-Methods are and their syntaxes talked about various logical access control methods and discussed the top four Access-Control-Allow Methods and their applications.
From Spectral’s suite of services, one that stands out is instinctive monitoring which looks for security misconfigurations and proprietary code assets across multiple data sources. Say, if some misconfiguration has slipped in while setting up Access-Control-Allow Methods, Spectral will detect it and alert the stakeholder to fix the issue at hand. Request a demo now to see how it works.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions