Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
As developers, we’re constantly under pressure to innovate at speed. In 2022, 60% of developers who responded to a GitLab survey acknowledged that code is moving to production at an increasingly faster clip–up to five times faster than in previous years. But juggling tight deadlines with ever-evolving security threats is no joke. When prioritizing speed, unsafe code eventually slips into production.

DevSecOps has taught us to incorporate security and compliance into building, deploying, and running applications. Add the power of automated DevSecOps tools, and we can not only test but enforce security policies and prevent threats without sacrificing agility. Let’s look at how this works, how to select the right solution, and what tools in the market can help you further harden your applications at speed, starting now.
In the fast-paced digital world, developing secure software efficiently is crucial. DevSecOps tools integrate security best practices throughout the software development lifecycle to bridge the gap between development, security, and operations teams, ensuring a seamless workflow and secure products.
These tools offer diverse solutions to enhance collaboration, automate processes, and embed security throughout the DevOps lifecycle. They help teams identify and remediate vulnerabilities early while accelerating development and deployment in various ways.
For example, popular categories include:
DevSecOps tools help developers in several ways, including:
By automating security testing and continuously scanning code, DevSecOps tools catch security issues early, preventing risks from reaching production environments.
DevSecOps fosters shared responsibility, breaking traditional silos between development, security, and operations teams. These tools facilitate better communication and collaboration.
DevSecOps tools automate tasks and streamline workflows, accelerating development, testing, and deployment processes, giving organizations a competitive edge.
Embedding security practices throughout the development lifecycle reduces the risk of costly security mistakes, like data breaches. Meanwhile, automating repetitive tasks saves developers’ time, lowering operational costs.
DevSecOps tools simplify compliance with strict security standards and regulations by automating checks and providing real-time insights into the software’s security posture.
Secure applications protect sensitive data and instill trust in customers. Using DevSecOps tools to build secure software increases customer satisfaction and loyalty.
When selecting a DevSecOps tool, consider your environment, team, and use case. Key capabilities to evaluate include:
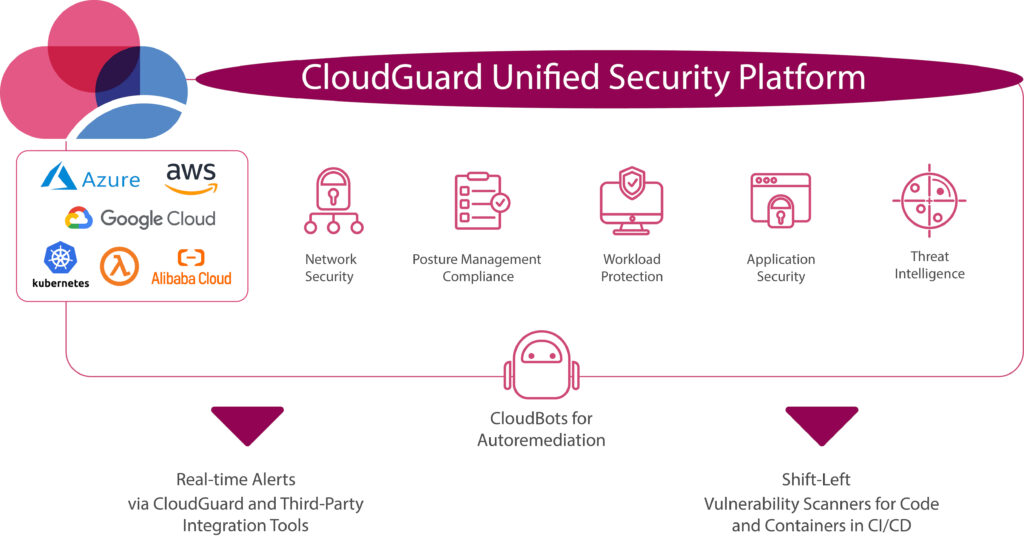
Check Point CloudGuard is a comprehensive end-to-end cloud security solution. CloudGuard is a SaaS platform that provides unified, cloud-native security across your applications, workloads, and network. You can use it to automate security, prevent threats, get compliance and manage posture for all popular cloud environments.
Review: “Capability of product seems to be there as the TCO of this product is excellent. This provides a single management solution bundling a broad spectrum of protection allowing the product to excel.”

Spectral is a developer-first security solution that automates the process of secret protection at build time, supercharging the CI/CD.
Main features: AI-powered scanning engine, detection of exposed secrets and security misconfigurations in real time, support for various code security use cases, and easy integration with CI/CD pipelines.
Best for: Developers and DevOps teams seeking a fast, modular, and developer-centric tool to ensure code safety and trust throughout the software development lifecycle.
Review: “One of the reasons we picked SPectral over other products is Spectral has low-false positive results, which gives us a high confidence factor and saves us precious development time.”
Jit is a security-as-a-service platform that can help speed up development by automating the process of selecting, implementing, configuring, and managing the application security toolchain.
Main features: Security knowledge codification, GitHub and AWS integration, customizable security plans, and an orchestration layer for various security tools covering code, pipeline, infrastructure, and runtime app security.
Best for: Progressive engineering teams in software companies, including Directors of Infrastructure, DevSecOps, Site Reliability Engineers, CTOs, and Product Security personnel looking for a comprehensive and developer-friendly security solution.
Review: “Very easy to onboard with this tool; You get a lot of points for the user experience. I like that the plan configuration corresponds to the code representation–very transparent.”
Snyk sees developers as the first step in building secure applications and infrastructure. It scans and secures components across the cloud-native application so developers can ensure security without impacting velocity.
Main features: Integrates with developer tools and workflow, constantly monitors for vulnerabilities, and suggests preventive measures.
Best for: Automated scans and fixed in code, open-source dependencies, containers, and infrastructure as code.
Review: “Snyk has really given developers the ability to start thinking about security as they’re developing code. It’s allowed them to be much more proactive in fixing vulnerabilities. Compared to our previous tooling, Snyk’s scanning is 2x faster and much more integrated to their tooling and processes. The developers are also quite happy that it’s a lot easier to navigate.”
SonarQube is an open-source platform for continuous inspection of code quality and security.
Main features: Static code analysis, detection of code bugs and security vulnerabilities, customizable rules, and quality gates.
Best for: Improving code quality and maintainability while enhancing security.
Review: “Helps us maintain our coding standards and avoid security risks in code.”
OWASP ZAP (Zed Attack Proxy) is an open-source web application security scanner and penetration testing tool.
Main features: Automated and manual scanning, proxying, and fuzzing capabilities, detection of common web application vulnerabilities.
Best for: Security teams and developers focusing on identifying and addressing web application security issues.
Review: “ZAP is a robust vulnerability scanner that has been very helpful in our web app security testing. Quite a few tools are available for this category, but ZAP is simple to use and has decent reporting features.”
Checkmarx is a comprehensive SAST solution that can help speed up development by identifying and remediating security vulnerabilities.
Main features: Code analysis, support for multiple languages and frameworks, integration with CI/CD pipelines, and compliance management.
Best for: Enhancing application security posture quickly.
Review: “Easy-to-understand interface and very user-friendly. Reduces the code using the cxsast plugin. It will scan code line by line and find most of the vulnerabilities. The vulnerability report is awesome.”
Aqua Security provides comprehensive protection for containerized and cloud-native applications, focusing on accelerating application delivery.
Main features: Container image scanning, runtime protection, vulnerability management, and compliance enforcement.
Best for: Organizations deploying containerized applications and seeking end-to-end security solutions for their container environments.
Review: “Aqua provided us with a zero-friction security and compliance solution for our entire container pipeline. With Aqua we can prove compliance of our cloud-native environment while staying agile and innovative.”
Cloud Foundry is purpose-built to deliver security for containerized environments and cloud-native applications by embedding security controls directly into existing processes, from pipeline to perimeter.
Main features: Container and Kubernetes security, cloud security posture management, container vulnerability scanning, and runtime protection.
Best for: Securing cloud-native applications and ensuring compliance with regulations
Review: “[With Cloud Foundry] we give developers the ability to push their apps and microservices locally and quickly, with no worries about the infrastructure.”
Sysdig is a cloud-native visibility and security platform designed for monitoring, troubleshooting, and securing containerized applications.
Main features: Kubernetes monitoring, security scanning, incident response, integration with existing DevOps workflows, and compliance management.
Best for: Visibility and security for containerized environments
Review: “The native integration in Kubernetes is quite simple and quick. The features are powerful, going from a comprehensive overview to a very detailed report of vulnerabilities affecting our workload and the infrastructure where they are running. The new Risk spotlight helps to prioritize vulnerabilities.”
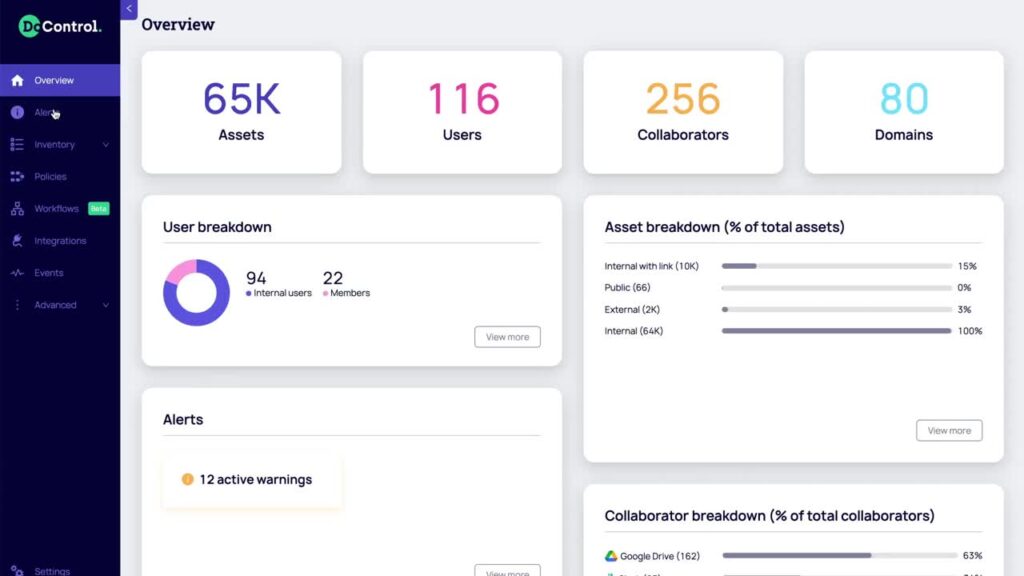
DoControl is a SaaS-oriented security tool that addresses user access privileges and profiling and manages data exposure. By using DoControl, you gain visibility of all your assets, users, and external collaborators. This tool automates data access controls while enabling security without compromising efficiency.
Main features: Preventive data access controls, service mesh discovery, SaaS service misconfiguration detection, and shadow application governance.
Best for: Organizations looking for a simple, self-service, and collaborative approach to managing security risk and Data Loss Prevention
Review: “The DoControl product is useful and helps us to manage our SaaS data more efficiently with excellent visibility and easy management capabilities. “
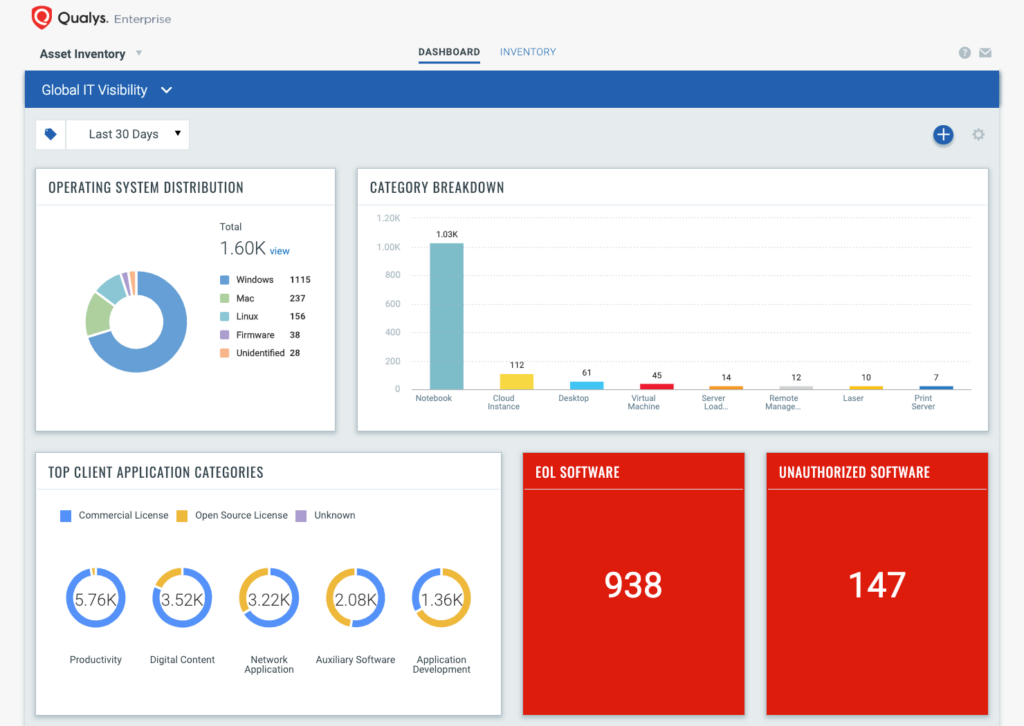
Qualys is a cloud platform with an accompanying cloud agent that provides a single platform for your IT, security, and compliance solutions. Its free Global AssetView app gives you instant visibility into all known and unknown assets across your hybrid cloud environment.
Main Features: Analyze threats and misconfigurations, prioritizes urgent vulnerabilities, and patch risks with a single click.
Best for: Any business sizes. Cabalibilites extend to extensive IP scans and audits per year.
Review: “Based on the experience I have with Qualys, it is very impressive to capture the vulnerabilities, this compiles a complete report of the risks that your infrastructure has, in addition the patches have very precise information that allows you to carry out the remediation very effectively. The analyzes are detailed and very complete, it works very well to carry out the compliance stages of PCI, CIS, etc… Providing a great guarantee that periodically your organization has an armored infrastructure.”
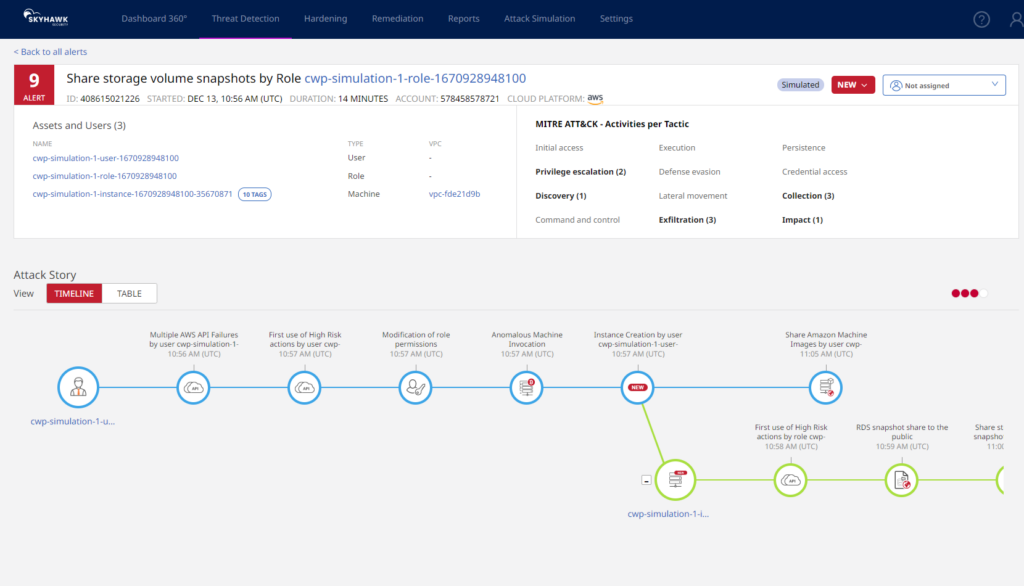
Correlating Cloud Security Posture Management (CSPM) with Cloud Detection & Response (CDR), Skyhawk Security’s Synthesis Platform helps uncover breaches across your entire cloud infrastructure in real-time. With their Realerts, solution teams can prioritize time spent on actual threats that pose a disruption to your organization. Skyhawk Security solves some significant pain points like Alert fatigue and Lack of visibility.
Main features: Static and dynamic activities, Runtime hub, and Threat detection.
Best for: Established, cloud-based companies looking to protect their cloud at runtime.
Review: “Superb experience with a great product and great support by OEM”.
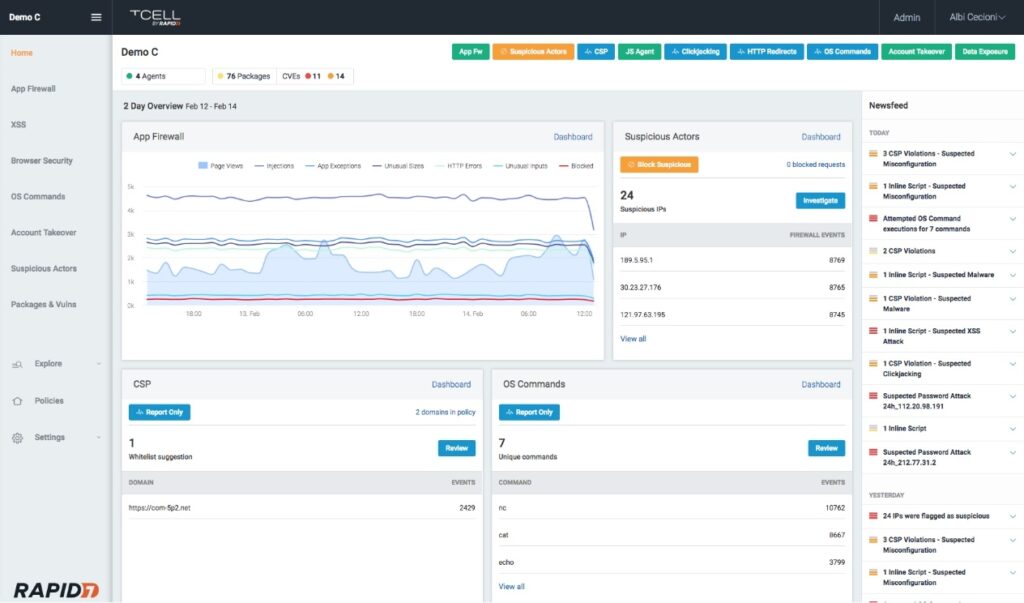
Rapid7 tCell is a next-gen cloud WAF and runtime application self-protection (RASP tool) that runs “security at the speed of DevOps.” tCell provides complete visibility into all your applications through real-time application monitoring. It offers multi-level web server and app server agents that automatically recognize and block attacks. Plus, it prioritizes alerts and sorts breaches that require immediate action from ones that are actively being blocked. This tool also allows applications to defend themselves from attacks in production.
Main features: Real-time application monitoring, web server and app server agents protection, and Application risk coverage.
Best for: Organizations looking for a holistic approach to application security.
Review: “The tool is good for performing quick scans on web apps and api to get an overall view of DAST security posture.”
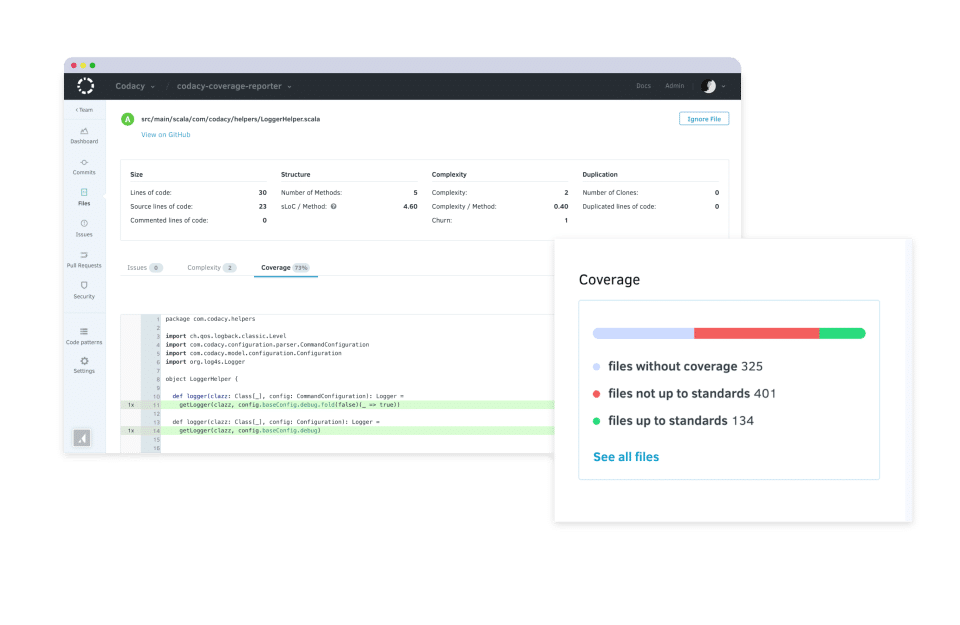
Codacy integrates into your development workflow to automate code reviews for commits and pull requests. It supports over 40 programming languages and provides instant visibility into your project’s code quality. You can also integrate your security policies to block merges of pull requests that violate quality conditions.
Main features: Customizable rulesets, Identifying problematic areas in your project, and actionable results.
Best for: Organizations with large development teams looking to streamline projects, standardize their code and save time on code reviews.
Review: “Excellent code coverage tool with great GitHub Integration.”
In a world of complex and fast-paced software development, DevSecOps tools are king. The tools above support developers in building secure applications while accelerating time to market. But there’s no such thing as a silver bullet when it comes to cybersecurity. Unfortunately, security is still the biggest threat facing organizations that strive for faster software delivery, with attacks on the rise due to application code gaps.Laying the foundations for a more secure future requires developers to continuously monitor and test their systems. Take advantage of our free resources to stay in the loop and simplify your AppSec by learning to make it part of your everyday work.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions