Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Cyber threat is soaring on the list of the gravest challenges plaguing organizations today. This is partly an outcome of developers including security in their development process as an afterthought. Although enterprises quickly realize the cyber threat risks to their businesses and reputation, they seem to be in a state of indecision.
Although organizations are planning to shift left to improve their security measures, they often don’t know where to start, seeing that the cyber threat landscape is evolving with emerging technologies while malicious actors get more creative. This calls for the widespread adoption of cyber threat intelligence tools.
The movement has already begun with the global cyber threat intelligence market touted to reach a valuation of $981.8 million by 2023 from $392.2 million in 2020, as reported by Statista.
This blog post will take a deeper look at cyber threat intelligence and how it affects an organization’s security posture. We will then go through the top 10 cyber threat intelligence tools of 2022 and the factors that make them stand out in the crowd.
Table of contents:
Cyber Threat Intelligence is a cybersecurity concept of gathering, processing, and analyzing data about security risks that severely threaten your organization’s assets.
Its primary purpose is to discern an attacker’s motives, behaviors, and targets to help you implement a proactive security posture to mitigate data breaches efficiently. It empowers you to identify, prepare, and tackle attacks by providing known malware signatures, data types that ransomware groups like to target, and device/network corruption signs to look out for.
Securing your organization against data breaches and ransomware is impractical without understanding security vulnerabilities, threat indicators, and inventive hacking practices. By drawing insights from this intelligence, developers or security professionals can build a robust security paradigm. You can accurately prioritize vulnerabilities, undertake root cause analysis, and devise other high-level security processes.
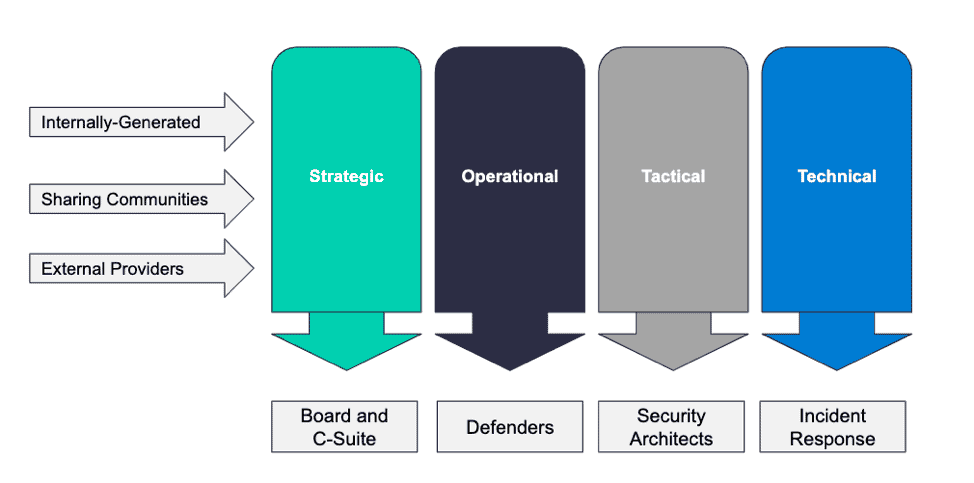
Threat intelligence can be depicted in multiple forms and formats depending on the information source, initial requirements and objectives, and the intended audience. The process of simplifying the complicated data processing and analysis is done by classifying the threat intelligence data based on its nature. The four types of threat intelligence most commonly used are:
Strategic: Prepared for non-technical users, it contains a high-level view of potential risks
Tactical: It features tactics, techniques, and procedures (TTP) used by attackers
Technical: this data apprises employees of signs to look out for both technical and non-technical users
Operational: It details technical information about possible threats and hostile campaigns (malware hashes, C2 IP addresses, etc.,)
Largely non-technical and comprising surface-level risks, strategic threat intelligence is prepared for decision-makers and strategists. It is created in a research report format taking data from several freely available sources, such as government-released policy documents, industry or compliance leadership mandates, and recommendations from security agencies.
Although access to such a variety of strategic data for free is helpful, processing the tremendous amount of information and preparing insights is an uphill challenge. You can use threat intelligence tools to scour through volumes of data and retrieve relevant information automatically.
Tactical threat intelligence notifies you of different kinds of TTP (Tactics, Techniques, and Procedures) that attackers employ to infect your system. This is intended for technical users like system architects and security professionals, who are actively involved in adhering to security policies. The data includes attack vectors, infrastructure, tools, and best practices to avoid or mitigate these threats.
Data to build tactical threat intelligence is usually pulled from reports published by security solutions providers and industry leaders. This report contains a use case of a specific threat group or attack campaign and details tactical information, from locations and industries targeted to attack vectors used.
Technical threat intelligence deals with technical information regarding an attacker’s tools and infrastructures such as malware hashes, C2 infrastructure IP addresses, registry keys from malware samples, text/content used in phishing emails, and malicious URLs. Technical intelligence of a threat highlights indicators of compromise (IOC).
Although a vast quantity of technical threat data is available for you to analyze and draw insights from, this form of intelligence is of short span. Therefore, it is crucial to distribute this data quickly for real-time actions. You should use a threat intelligence tool to maximize the value of the data.
Operational threat intelligence aims to identify the nature, motive, and timing of specific attacks before they happen. It is a common practice for organizations to track conversations on social media platforms, public and private chat rooms, open and dark web forums, and other such community platforms.
It is impractical or tremendously challenging to infiltrate threat groups and their discussions due to obstacles like legal boundaries, language barriers, and obfuscation practices. While monitoring open channels is fairly doable, you can also track real-world events that lead to cybersecurity issues that can prove to be useful.

Time-to-market plays a critical role in defining your success in today’s competitive market. To achieve exceptional development speed, developers often use open-source and third-party codebases in their software. This exposes your applications to several software supply chain vulnerabilities, which are presenting significant challenges across the globe. The US government had an ugly wake-up call to the seriousness of such threats with the SolarWind attack which involved a series of data breaches across global organizations and US federal government institutes. Therefore, the US government has released an Executive Order with cybersecurity mandates.
Data breaches and ransomware attacks are becoming more and more common, with security oversight for developers. This is why you invest in a cyber threat intelligence tool. It automates your security processes by flagging data leaks, security incidents, vulnerability detection and remediation, and third-party dependencies. Making threat intelligence an intrinsic aspect of your developer’s workflow can help raise awareness of the importance of secure coding and the impacts of its absence.
Threat intelligence tools are critical in enhancing your cybersecurity stance by managing risks using AI/ML. Although multiple solutions process data from various sources at scale, provide risk scores, and generate predictive models, you must consider the below features when picking a threat intelligence solution for your organization:
Ensure the solution integrates your existing security tools and mechanisms, including SIEM (Security Information & Event Management) and firewalls. This ensures you get a comprehensive view of your security posture by collecting data from all the relevant sources.
A single window dashboard facilitates faster decision-making regarding security policies and threats because it simplifies and accelerates the threat identification and remediation process.
One key characteristic of a threat intelligence tool is to pull information from many sources, process vast volumes of data, and present a detailed picture of an organization’s cybersecurity standing.
Let’s look at the top 10 cyber threat intelligence tools of 2022 and understand how they are equipped to secure your system from cyber threats.
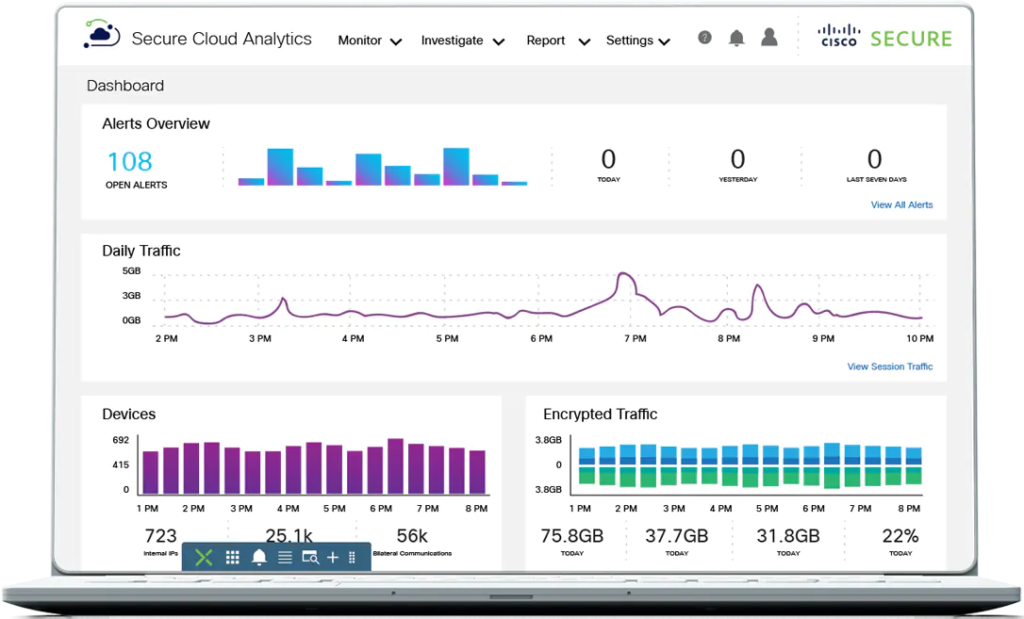
A unified security solution that protects your organization from cyberattacks leveraging its malware knowledge base. Earlier known as Threat Grid, it is a unified solution that informs you of malware activities, threat levels, and strategies to tackle them.
Key features:
Pros:
Cons:
Review:
“Cisco Threat Grid makes it easier and more efficient to investigate and figure out what’s wrong if there were to be a cybersecurity issue.”
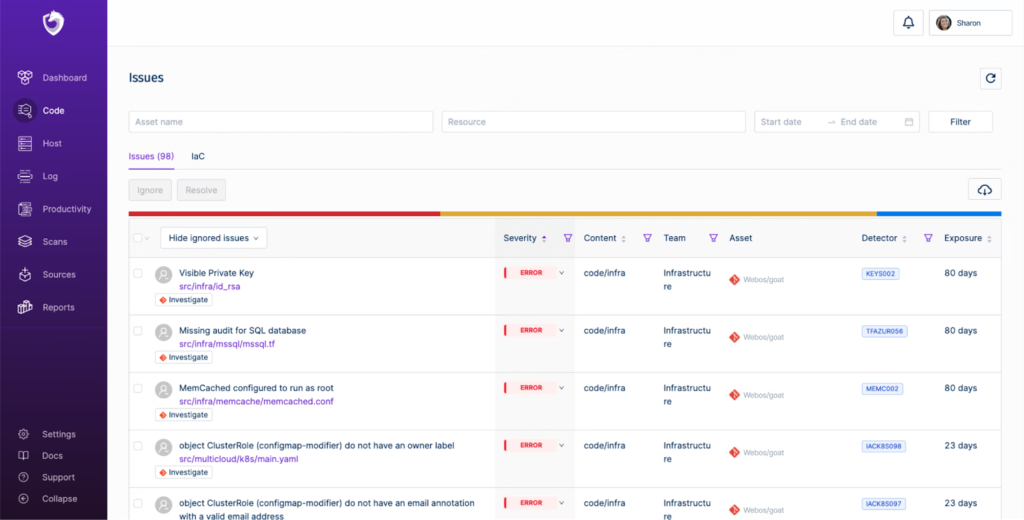
A developer-first cybersecurity solution that sits on top of your source code and assets to safeguard against security risks. It relies on AI models and detectors forming a hybrid scanning tool that gives developers the confidence to code without reservations as it takes responsibility for securing your system from high-cost coding mistakes.
Features:
Pros:
Cons:
Review:
“We’ve solved the issue of having zero visibility into our ADO environment with SpectralOps.”
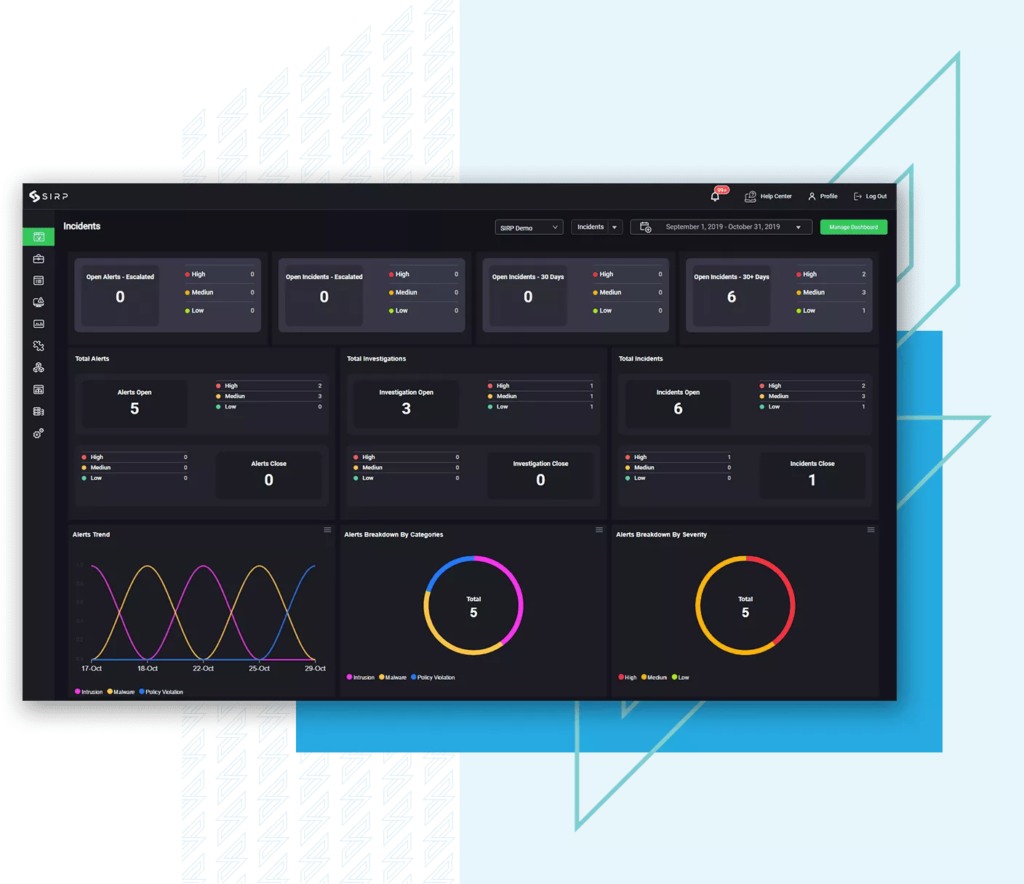
A risk-based cybersecurity solution, SIRP’s Security Orchestration, Automation, and Response (SOAR) platform gives a unified and single integrated platform for you to make security decisions with complete visibility and a prioritization approach.
Features:
Pros:
Cons:
Review:
“SIRP was an eye opener for us. We realized there is much more to the security incidents management than opening tickets and doing follow-ups.”
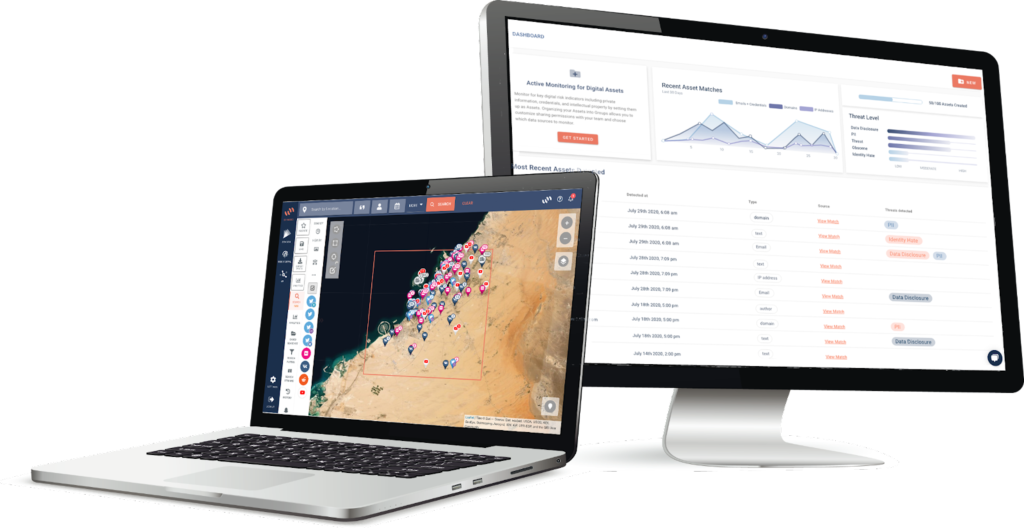
A specialist open-source intelligence (OSINT) tool that leverages social media, open community platforms, and the dark web to enhance your enterprise security. It collects publicly available data from 18 social media platforms, blogs, and news portals and contextualizes data critical and relevant to your organization.
Key features:
Pros
Cons
Review:
“The Echosec system is the most intuitive and user-friendly OSINT tool I’ve used for Social Media. The results render quickly, and the layout and operability are fantastic.”
A 360-degree cybersecurity solution that empowers you with real-time, actionable insights. It can either be used as a holistic cyber threat intelligence suite or as separate modules for threat investigation, risk analysis, and external intelligence.
Features:
Pros:
Cons:
Review:
“It is extremely flexible and can adapt to use cases like phishing protection, brand security, fraud detection, and data leak detection.”
As threats are evolving so must the threat intelligence landscape. Jit is not what most security professional would consider a threat intelligence tool. However, in encapsulates a complete cyber security envelope into one solution that is baked right into the code. With Jit, software development companies can find a healthy balance between deployment and security.
Features:
Pros:
Cons:
Review:
“I love the product! With Jit implementing product security is made super easy for the Dev team.”
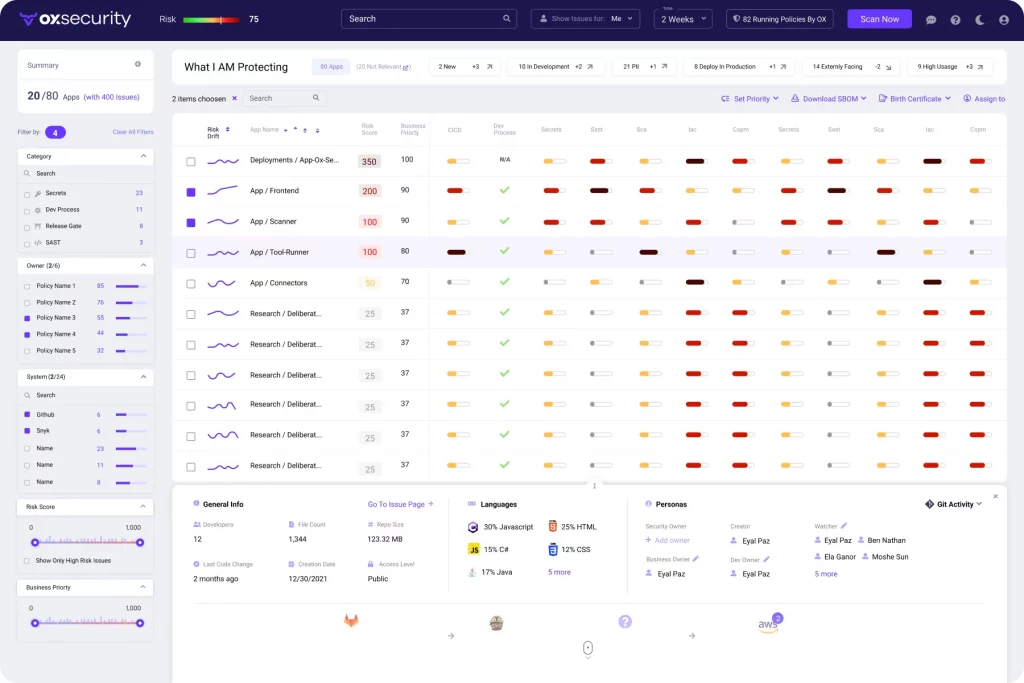
OX Security is another tool focused on protecting the software development lifecycle from threats. One of its key features is providing an automated, modern, and efficient view of dependency graphs.
Features:
Pros:
Cons:
Review:
“OX gives a complete and reliable snapshot of code security before deployment”

ThreatConnect claims to be the only threat intelligence tool to offer a unified solution featuring cyber risk quantification, intelligence, automation, and analytics. It breaks down complex data into actionable insights that help solidify your defenses against potential risks. Its recommendations are simple and can be understood by the entire team, including security leadership, risk and security operators, and incident response executives.
Features:
Pros:
Cons:
Review:
“ThreatConnect boasts it can stop any threat by joining your in-house virus software with a collaboration of threat data from others, and it does just that.”
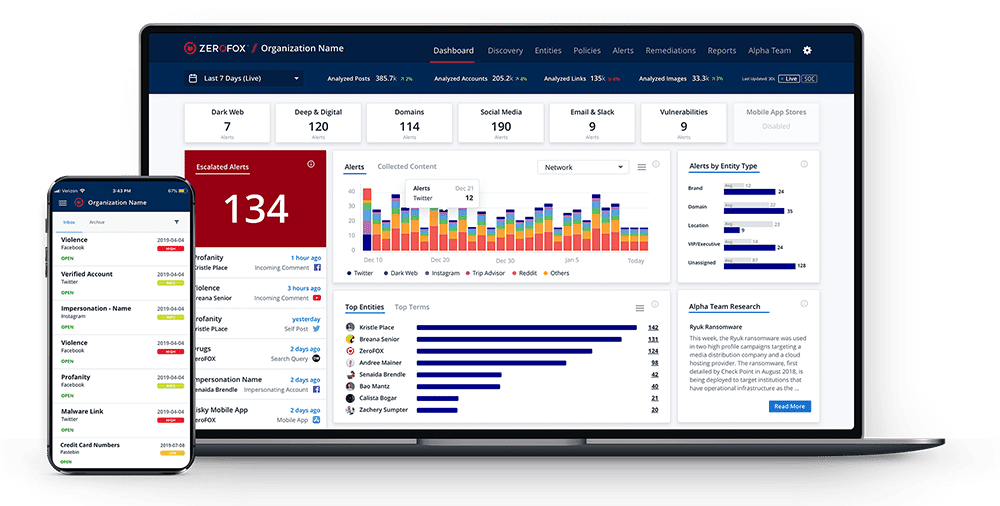
A cyber intelligence solution that safeguards your organization from fraud, hacking, and other online threats by managing social media and digital risks and bringing relevant data to your attention contextually.
Features:
Pros:
Cons:
Review:
“The service does a great job of providing alerts about online content across platforms that could pose a problem to the customer.”
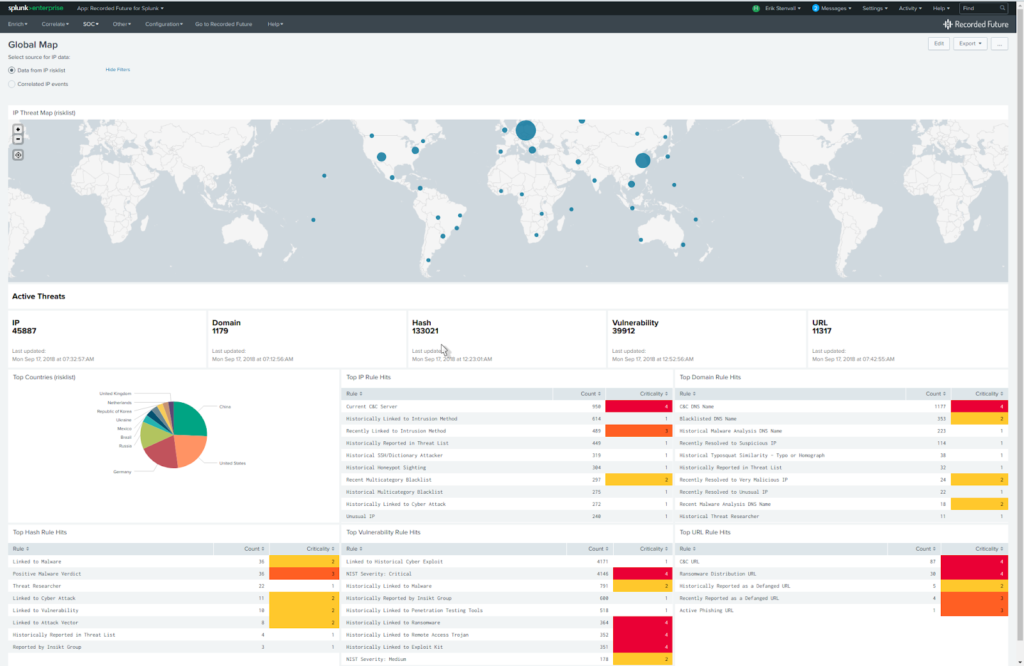
An intelligence tool that automates the collection, analysis, and reporting for you to understand your adversaries, infrastructure, and targets. It enables a proactive stance against cyber threats by giving you real-time visibility into your digital ecosystem.
Features:
Pros:
Cons:
Review:
“Recorded Future stores the best data and organizes it in a digestible and interesting way.”
Cyber threat intelligence tools add significant value to your business growth by identifying, predicting, alerting, and managing cyberattacks. These tools allow your developers to incorporate security best practices as a part of their development process. While the market is rich with several threat intelligence solutions and vendors, it could put you in a dilemma. In this article, we presented our top 10 picks for this year.
To further understand the role developers play in securing the underlying infrastructure of applications, check out our recent guide on serverless security next.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Continuous integration and delivery are necessary in any production level software development process. CI/CD are more than just buzzwords. Rather, it is a fully-fledged methodology of