Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
In February 2023, LastPass, a leading password manager service, disclosed a security breach that reminded us just how severe SaaS breaches can be. The intrusion involved a targeted attack against a DevOps engineer accessing the corporate vault, underscoring the consequences of inadequate access controls and security practices.
While Software as a Service (SaaS) offers immense operational benefits by freeing DevOps teams from infrastructure management, it also presents a unique security challenge due to the shared responsibility model. SaaS providers secure the underlying infrastructure, but customers are accountable for securing their applications, data, and configurations within the service. Misconfigurations or vulnerabilities on your side can expose your systems and data to potentially devastating attacks.
This shared responsibility for security is particularly relevant for DevOps teams who operate at the critical intersection of development and cloud operations. DevOps teams must ensure security is baked into their processes and tools as they rapidly build, deploy, and manage cloud-based applications. Understanding the risks associated with adopting SaaS is crucial in building and delivering reliable systems.
The rapid adoption of Software as a Service has often outpaced security considerations, leading to overlooked risks. While SaaS provides immense operational benefits, understanding the shared responsibility model, often outlined in SaaS security best practices, is crucial. The SaaS provider secures the underlying infrastructure, but you are still responsible for securing your service.
In a continuous integration and deployment world, misconfigurations can propagate into production environments as quickly as new features. A Server-Side Request Forgery(SSRF) vulnerability in your SaaS integration could allow an attacker to coerce your application into sending crafted requests to unauthorized internal systems.
Similarly, broken authentication flaws might enable an adversary to temporarily or permanently assume the identity of legitimate users. Many applications consume APIs that rely on other third-party APIs, creating a chain of potential vulnerabilities and security threats attackers could exploit to access sensitive data or disrupt business workflows.
The intuitive nature of SaaS can also lead to shadow IT scenarios where unknown apps bypass security reviews and enter workflows, compounding risks. These could include unapproved third-party plugins, add-ons, or integrations that need proper security vetting—introducing such unknown applications, whether third-party integrations or unsanctioned plugins, can undermine your security posture without proper risk assessments.
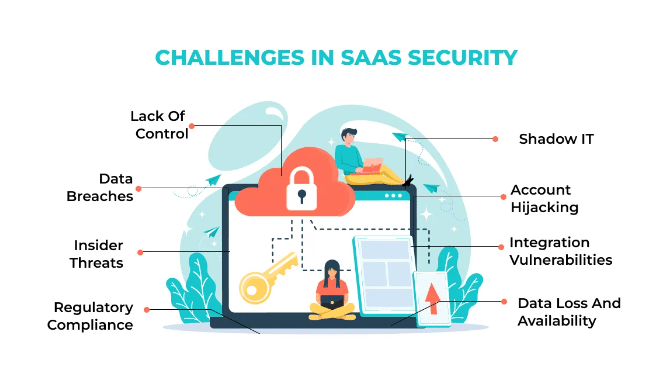
As teams rapidly build, deploy, and manage cloud-based applications, it’s essential to prioritize security practices across several key areas. The following are key areas to focus on in SaaS security:
Identity and access management are the foundations of securing your SaaS environment. Implementing robust authentication mechanisms like multi-factor authentication (MFA) and single sign-on (SSO) can prevent unauthorized access to sensitive data and systems. Enforcing the principle of least privilege minimizes risk exposure by granting users only the necessary permissions to perform their roles.
Automating user provisioning and de-provisioning processes becomes crucial in dynamic environments where teams and roles constantly evolve. It simplifies identity lifecycle management, ensuring timely access revocation for departing employees or role changes and reducing the risk of misusing orphaned accounts.
By combining strong authentication, least privilege access controls, and automated identity governance processes, the key here is to account for the built-in IAM support for your SaaS provider and ensure you’re maximizing it.
Understanding and adhering to data security policies is crucial for DevOps and development teams. While SaaS providers typically implement encryption for data at rest and in transit, if you’re lucky, reviewing their specific practices is essential to ensure they align with your organization’s security requirements.
Depending on the sensitivity of your data and applicable compliance regulations, you may need to implement additional data protection measures beyond what the SaaS provider offers. Client-side encryption, where data is encrypted before it reaches the SaaS platform, can provide an extra layer of security for your most sensitive information.
Implementing data classification and handling processes based on sensitivity within your applications is a best practice. It could involve encrypting certain data elements, enforcing stringent access controls, or implementing data loss prevention (DLP) measures.
APIs are the glue that connects SaaS applications to your internal systems, making them a critical security consideration for DevOps teams. Common vulnerabilities like Broken Object Level Authorization and excessive Data Exposure Rate Limiting are imperative to pay attention to, as attackers can easily exploit them.
DevOps teams must prioritize secure API development practices to mitigate these risks and leverage threat intelligence. Deploying API gateways can provide a centralized control point for enforcing security policies, rate limiting, and threat protection. By using security-first development practices, API gateways, continuous testing, and continuous monitoring, teams can significantly reduce the risk of API-based attacks on their SaaS integrations.
Misconfigured settings can have severe consequences, exposing sensitive data, introducing vulnerabilities, and violating compliance mandates like HIPAA and GDPR. For teams, managing SaaS configurations is not just a security imperative but also a crucial compliance requirement. Under HIPAA, protected health information (PHI) is safeguarded with strict controls when leveraging SaaS solutions.
It includes access controls, audit trails, and encryption measures. Similarly, GDPR stipulates that the personal data of EU citizens must be processed securely, with appropriate technical and organizational measures in place.
Failure to properly configure SaaS applications in adherence to such regulations can result in costly penalties, legal repercussions, and reputational damage.
Ingrain SaaS security into your DevOps processes from the start. By proactively weaving security practices throughout your workflows, you can identify and remediate risks early, drive efficiencies through automation, and ensure preparedness for potential incidents.
Embracing a “shift left” mindset is crucial for catching security issues before they propagate downstream. It involves incorporating vulnerability scanning and threat modeling early in the development lifecycle. Integrating these security gates into your CI/CD pipelines, adhering to DevSecOps principles, allows you to identify and address vulnerabilities or misconfigurations as part of your delivery processes. Mastering the DevOps toolchain and achieving DevSecOps maturity can help in achieving this.
For many organizations, automation is not negotiable; manual security tasks quickly become bottlenecks. Automating identity and access management, configuration checks, compliance audits, and security monitoring is essential for maintaining a secure SaaS environment. Infrastructure as Code (IaC) practices enable you to define and enforce secure SaaS configurations across all environments programmatically.
Automating identity and access management, configuration checks, compliance audits, and security monitoring with a mature DevOps toolchain is essential for maintaining a secure SaaS environment.
Despite your best preventive efforts, the possibility of a SaaS security breach cannot be ruled out for your DevOps. Proactive incident response planning is vital for minimizing the potential impact. Define clear communication protocols and collaboration procedures with your SaaS providers’ incident response teams. Regularly review and test your incident response playbooks to ensure your teams are prepared to act swiftly and effectively in the event of a security incident.
Securing your SaaS environment begins with a crucial first step – selecting the appropriate providers. Here are some things to consider when selecting a provider.
SOC (Service Organization Control) reports are your best friend when evaluating SaaS providers. These independent third-party audit reports provide valuable insights into the provider’s security controls and compliance posture. SOC 2 reports, for instance, assess the provider’s non-financial controls related to security, availability, processing integrity, and confidentiality.
Transparent communication from vendors is equally crucial, as security is not a one-way street. Providers should be open about their security practices and promptly disclose vulnerabilities or incidents that may impact your systems. If you leverage the provider’s data storage, understand their data handling and encryption methods thoroughly. Ask questions about encryption practices and data residency (where your data will be physically stored).
Contractual safeguards are also vital. Service Level Agreements (SLAs) should clearly define availability and performance commitments. Incident response expectations must be explicitly outlined, such as notification timelines and the provider’s responsibilities. Liability terms should protect your organization in case of security breaches or service disruptions caused by the provider.
While SaaS providers handle the heavy lifting of infrastructure security, your teams should firmly take responsibility for securing your inputs—the code and sensitive credentials powering your applications.
Even the most vigilant SaaS provider can’t prevent vulnerabilities introduced through insecure coding practices or accidentally leaked credentials in version control. It is where proactive measures like Spectral Code Scanning come into play.
Spectral helps identify and mitigate risks such as exposed API keys, tokens, and other sensitive information that could be exploited by continuously scanning your codebase. Integrating seamlessly into your CI/CD pipelines, Spectral provides an added layer of security, catching potential vulnerabilities before they reach production and ensuring your code remains secure throughout its lifecycle.
Safeguard your codebase today with Spectral’s proactive scanning. Start today and experience firsthand how Spectral can fortify your SaaS environment.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions