Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
It’s unsettling to think that our systems can betray us. With SSRF attacks, harmless-looking web requests turn into weapons for cybercriminals. They can exploit vulnerabilities from within our networks, and these attacks often slip under the radar, quietly compromising data, breaching security, and potentially leading to catastrophic consequences.
SSRF attacks have hit over 100,000 businesses globally since the end of 2022, and this number will rise due to the increasing use of web applications. But don’t fear – in this article, we will tell you everything you need to know about SSRF attacks, their impact, and how you can mitigate the associated risks.
Server-side request forgery, or SSRF, is a web security vulnerability where an attacker abuses the server functionality, causing it to read, access, or manipulate resources that would otherwise not be directly available to the attacker. SSRF took a backseat as the world scrambled to prevent common XSS attacks, but now it’s (unfortunately) right in the spotlight.
In SSRF attacks, attackers exploit the server’s ability to make outgoing requests to other systems, initiating a connection with internal-only services and reading internal resources not meant to be exposed on the internet. The result is data leakage, remote code execution, and other serious consequences like supply chain attacks.
SSRF attacks often begin with the attacker sending crafted malicious requests to the back-end server, usually as a URL or an IP address through an input field on the webpage. The server processes this manipulated input and then tries to request the provided URL or IP address. In doing so, the server behaves as a proxy for the attacker, unquestioningly forwarding the request and potentially exposing sensitive internal resources or inadvertently interacting with external systems, all under the guise of the server’s trust.
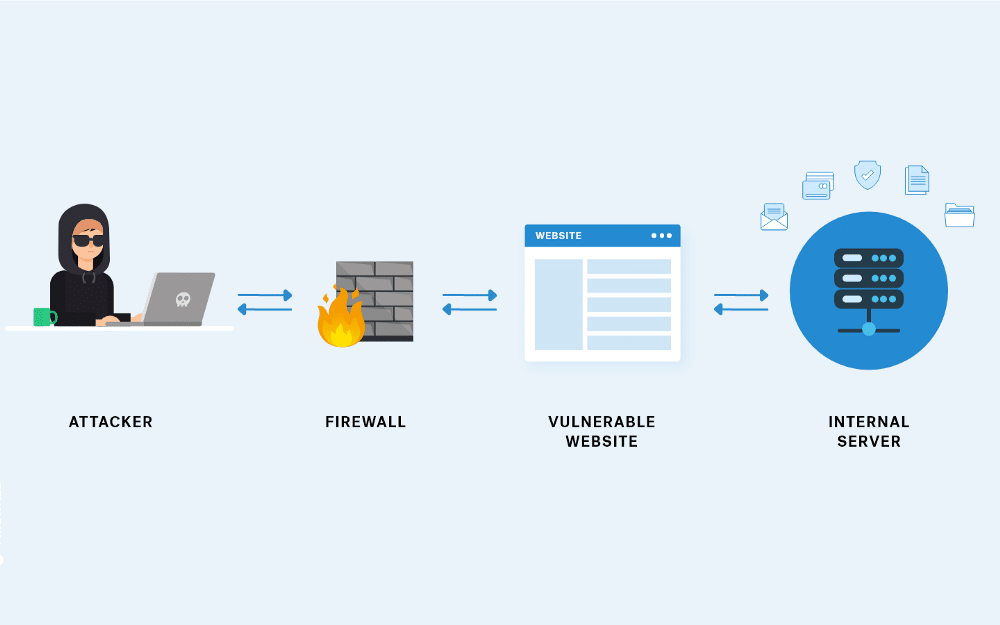
SSRF attacks can have a wide-reaching impact, often causing severe consequences for applications and organizations. These attacks exploit vulnerabilities in the system’s architecture, which can lead to various damaging outcomes, including:
In most organizations, the stakes are too high to fall victim to an SSRF attack. A successful SSRF attack results in the following:
SSRF attacks have plagued web applications for decades because they fly under the radar, bypassing traditional web application security measures and putting sensitive data at risk. Let’s see some examples of SSRF and find out how to protect against them.
In an SSRF attack that targets internal resources, malicious actors manipulate the web application to request sensitive resources within an organization’s internal network, typically off-limits to external users.
You must first implement rigorous input validation and sanitization for user-supplied URLs to protect our application from malicious actors looking to read internal data. This validation process ensures that the URLs conform to the expected format and do not contain malicious elements that can be exploited. In addition to SSRF prevention strategies, you can also deploy data loss prevention tools in your arsenal to protect internal resources.
A particularly concerning manifestation of SSRF attacks is its role in enabling port scanning attacks, which occur when threat actors can scan the server for its open ports. This activity allows the attackers to create a detailed map of the system, discover potential security vulnerabilities, and gain unauthorized access to its resources.
To defend applications from port scanning, you need to avoid using user-supplied input to construct URLs and rigorously validate URLs.
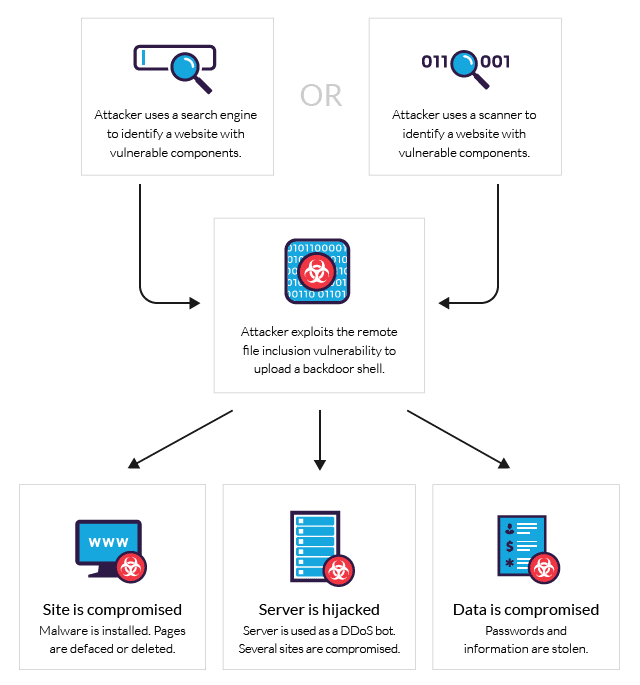
Remote file inclusion (RFI) involves exploiting vulnerabilities in web applications that dynamically reference external files or scripts. Using RFI, an attacker can manipulate a web application to include and execute a remote and malicious file. A successful RFI attack has far-reaching consequences on the web application, ranging from the disclosure of sensitive information to remote code execution, leading to a complete system compromise.
Prioritizing input validation and sanitization is the first step in securing data and organization from SSRF attacks. Additionally, you should maintain a whitelist of trusted file locations and external scripts, permitting only those explicitly trusted while rejecting any requests that haven’t been verified or might be potentially malicious.
Finally, you can implement security headers like Content Security Policy (CSP) to control external sources the web application can load.
Data exfiltration (sometimes called data extrusion, data exportation, or data theft) is an SSRF attack where an attacker leverages the vulnerability to access internal APIs or services, extracting sensitive data and sending it to an external location, compromising data confidentiality.
In addition to the steps discussed in previous sections for mitigating risks, you should take further measures to prevent data exfiltration. For example, you can enforce stringent access controls, encrypt sensitive data, and actively monitor outgoing traffic for any signs of unusual or unauthorized data transfers.
XML external entity attacks exploit vulnerabilities in applications that parse XML input. In these attacks, malicious actors manipulate XML parsers by injecting external entity references within XML documents, potentially resulting in data breaches, remote code execution, or denial-of-service incidents. An XXE attack occurs when a threat actor submits carefully crafted XML input, deceiving the server into making requests to external entities while exploiting a vulnerable SSRF feature.
You can protect data from XXE attacks by turning off external entity resolution in XML parsers, implementing strict input validation, and adopting whitelisting practices to control the scope of accepted XML content.
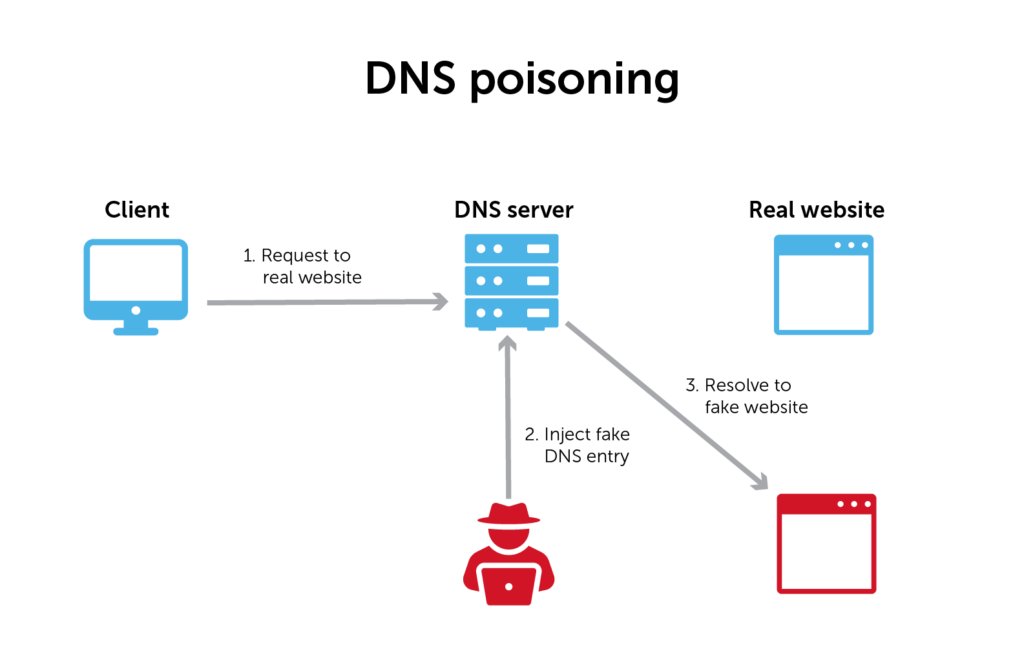
Server-side cache poisoning exploits vulnerabilities present in a web application’s caching mechanism. This attack is executed by inserting fake information into a domain name system cache or web cache to harm users.
To defend against server-side cache poisoning, you can do the following:
Cloud metadata API abuse occurs when an attacker can fetch and read sensitive information from the metadata of a cloud provider. These metadata usually hold crucial data like access credentials and instance details.
There are several steps you can take to defend against cloud metadata API abuse, including setting up firewalls and network restrictions to limit API access, using rate limiting and monitoring, educating teams on secure coding practices, and leveraging cloud provider security features like temporary credentials.
Server-side request forgery is a devastating threat prevalent in the cybersecurity space. As demonstrated in this article, SSRFs can manifest in different forms, from data breaches to remote code execution, putting organizations and their sensitive data at risk.
However, you can prevent the risks posed by SSRF by adopting protective measures and a proactive security posture. These measures include strict input validation, rate limiting, and security headers and tokens.
Additionally, you can use security tools like Spectral to perform regular security audits and enforce data access policies. Spectral helps you apply and enforce policies by enabling you to integrate your own playbooks, build your own detectors, and implement mitigation policies to secure the SDLC.
To try out Spectral, create a free account now and get started.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions