Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Like any chain, a software supply chain contains many links. These links consist of every actor involved in the development & deployment of your code in the Software Development Life Cycle (SDLC). An actor can be the developers, infrastructure components, and even repositories like GitHub.
A company might have a very secure supply chain. However, it will only be as strong as its weakest link. For example, in 2020, third-party software called Orion put over 30,000 organizations in a compromising position due to a supply chain attack on the SolarWinds system.
As the complexity of building software increases, as does its reliance on third-party components, more companies will have their supply chains vulnerable to these types of attacks.
Software supply chain risk refers to the potential threats and vulnerabilities at any link in your software supply chain. Any risk to the software supply chain is a possible risk to every system (software) that depends on that supply chain component.
Understanding supply chain risk is vital in software development because it encompasses the entire lifecycle of software creation, involving various third-party components, development tools, and external dependencies.
Modern software development relies heavily on interconnected ecosystems and third-party libraries. While beneficial, these dependencies can pose significant risks if they contain vulnerabilities, are compromised, or are poorly managed. Mitigating these risks often requires specialized knowledge and resources, making no-code security automation an attractive solution for organizations with limited security expertise.
The following are some types of risks to your supply chain:
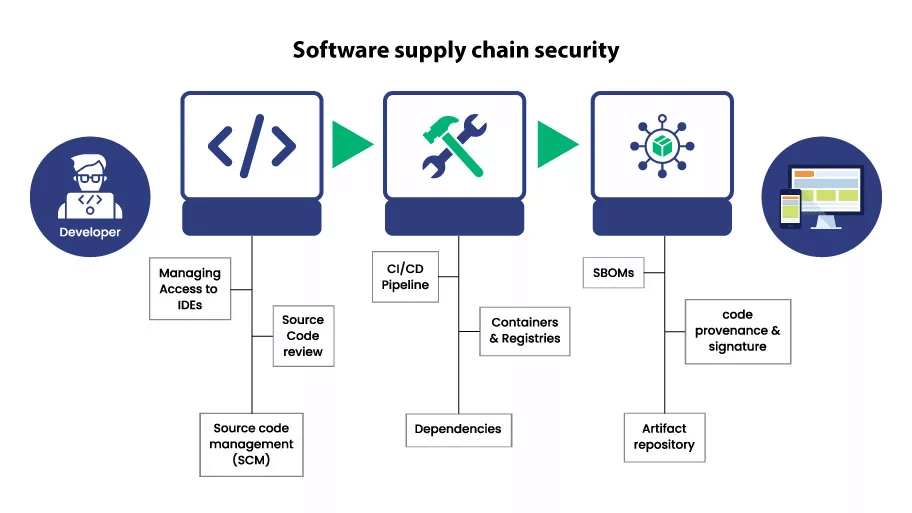
As complex as today’s software is becoming, developers might need to catch up on how many external components they rely on. Therefore, the first step to securing your software supply chain is to identify and inventory all components used throughout development. This inventory helps you understand every software element is crucial for managing potential risks or vulnerabilities.
Key inventory components include third-party libraries, open-source components, commercial off-the-shelf (COTS) software, and custom-developed code. Maintaining an up-to-date inventory can be challenging but achievable with a central repository accessible to all team members and continuous monitoring.
Automated tools like software composition analysis (SCA) solutions can assist by scanning your codebase and dependencies, providing a comprehensive list of all components.
After updating your software inventory, the next step is to evaluate the security practices of each supplier and vendor in your supply chain.
Conduct due diligence on potential suppliers and vendors before integrating any third-party components into your software. Look for specific security certifications, such as ISO 27001, which indicate stringent security standards.
Key aspects to consider include a vulnerability disclosure program, incident response capabilities, and references from other clients.
Once you have identified potential risks in your software supply chain, the next step is to analyze and rank them based on their potential impact and likelihood of occurrence.
You can use established risk assessment methodologies or the ISO 31000 standard. While carrying out risk analysis, some factors to consider include the criticality of the affected component, i.e., how essential the element is to your software’s functionality, the potential impact of a successful attack, and the likelihood of that attack occurring.
To prioritize these risks based on their severity, you’d want to implement a risk matrix that plots the likelihood of occurrence against the potential impact.
After prioritizing risks, you’d need to tighten your security to protect your software supply chain better. To do this, you’d need to implement multiple security controls and mitigations that make it harder for attackers to breach your system.
Some security measures you can implement include regular security-focused code reviews, the principle of least privilege, regular software patches and updates, and regular security testing. Additionally, adopting a zero trust architecture can significantly enhance your security posture by assuming that no user or device is inherently trustworthy, regardless of their location or network.
Continuous monitoring and improvement of your software supply chain is crucial. A proactive security stance enables real-time detection and response to threats, minimizing their impact.
Use threat intelligence feeds to stay updated on emerging vulnerabilities. Regularly review and update your risk assessment and mitigation plan to adapt to software changes. Schedule periodic audits to reassess risks and adjust security measures, including regular vulnerability assessments and penetration testing to proactively identify and address potential weaknesses in your system.
Foster a culture of security across the organization to inform all team members about best practices and ensure ongoing improvement and vigilance in your software supply chain.
A Software Bill of Materials (SBOM) is a formal, machine-readable inventory that lists all software components, including dependencies and their relationships. It’s a descriptive document of all your software supply chain components, including all third-party software and open-source libraries.

SBOMs offer multiple benefits for both software producers and consumers. To the producer, SBOMs indicate that they’re dedicated to security and compliance. Consumers can use SBOMs to make informed decisions about their software, understanding the potential risks and dependencies involved.
When planning to use SBOMs, you should rely on automated tools to generate them. Once you do, remember to continuously update your SBOM as new components are added or existing ones are modified.
DevOps is a set of cultural practices that aims to unify software development (Dev) and IT operations (Ops). Integrating security (Sec) practices into the DevOps workflow is called DevSecOps.
DevSecOps shifts security to the left. This means security considerations are integrated from the start rather than being an afterthought. The approach ensures that security is not just a final check but an ongoing process that is embedded into every stage of the software development lifecycle, aligning with the principles of information security controls.
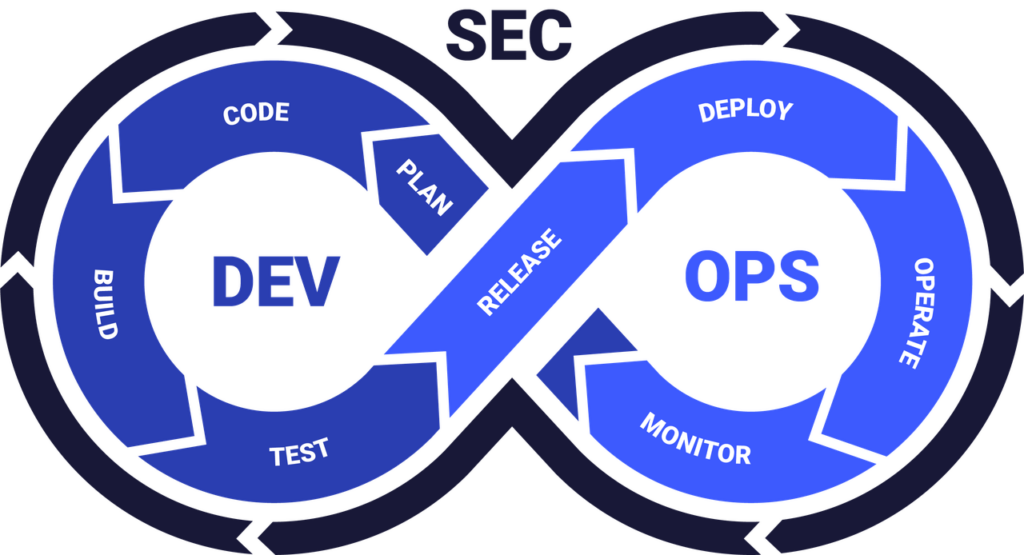
The easiest way to implement DevSecOps into your development workflow is to rely on automated security tools, such as SAST, DAST, and IAST tools. These tools offer security testing of your code at varying intervals.
If an attack happens, it’s essential to have a well-laid-out response strategy, which can be improved with the help of artificial intelligence and machine learning. A structured approach to responding to an attack ensures you can quickly detect, contain, and recover from any security incident, minimizing its impact on your organization.
There are some steps you must consider when creating this plan. They are:
Conduct regular incident response drills and exercises to ensure readiness. These simulations help your team practice and refine response strategies so everyone knows their role and can act swiftly during an actual incident.
Implementing these steps can be a pain in the ass, but that pain can become worse if you do it with multiple systems. SpectralOps allows you to implement all these steps all in one system.
With SpectralOps, you get automated vulnerability scanning, real-time threat detection, and comprehensive reporting, and it seamlessly integrates with popular development tools.
Your organization needs to choose a developer-first solution that’s easy to integrate and is trusted by several other companies. Sign up for your free SpectralOps account today and request a demo!

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions