Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Compliance is something that developers dislike. Traditionally led by risk and information security teams, compliance standard enforcement in organizations is not something software engineers are trained to do. So when the words “PCI compliance” are tossed around, for many developers it mentally translates to limitations, guardrails, bottlenecks, and drastic changes to their workflows that impact productivity.
But that doesn’t have to be the case.
In reality, PCI compliance means greater attention to application and data security. It can provide a cross-division framework to execute the vision of fraud-free payments. As we delve deeper, we’ll get to know PCI compliance from a developer perspective, review PCI compliance levels and their meaning, and provide you with actionable tips on how to ensure PCI compliance throughout your SDLC.
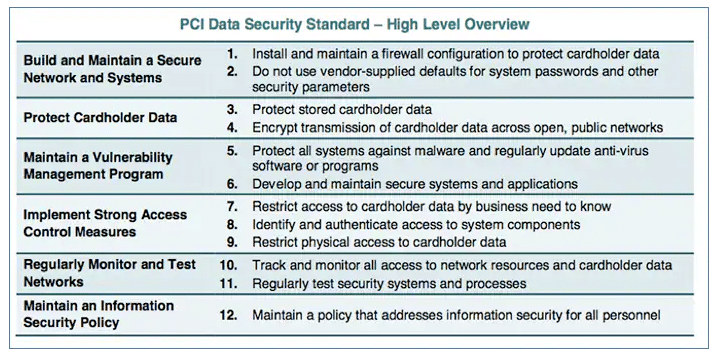
PCI compliance is often used as a shorthand for Payment Card Industry Data Security Standard (PCI DSS) compliance. The PCI DSS provides merchants and processors with set of highly technical guidelines on how to secure credit card and cardholder data. It aims to protect consumers, merchants, processors, and credit card issuers from data theft that results in fraudulent transactions and places heavy fines on businesses that handle credit card information but fail to comply with PCI DSS.
The global standard was created in 2001 through a collaboration between credit card companies to combat credit card fraud. The current and latest version of the PCI DSS, published by the PCI Security Standards Council (PCI SSC), is version 4.0, and it was released in March 2022.
PCI DSS includes a number of security controls that cover technical and operational practices for system components included in or connected to environments that interact with cardholder data. For developers, the relevant PCI compliance requirements to know are 3, 4, and especially 6 as they include guidelines for securing cardholder data at rest and in transit, managing access controls, and ensuring network security.
Before we discuss the role of developers in PCI compliance and the requirements you should be familiar with, let’s break down the levels of PCI compliance.

The guidelines in the PCI DSS have different demands for businesses of different sizes. Generally speaking, the more transactions your applications process, the more stringent measures you’ll need to follow.
This is the reason why many small businesses that handle large volumes of credit card transactions prefer to outsource payment processing features and applications to a trusted third party.
Level 1 of PCI DSS compliance is the highest level of stringency and applies to businesses that process over 6 million transactions annually, as well as businesses that have experienced a breach involving credit card information. To comply with PCI DSS Level 1 businesses must:
Level 2 of PCI DSS compliance is less stringent than Level 1, and it applies to businesses that process between 1 million and 6 million transactions per year. To comply with PCI DSS Level 2 businesses must:
Level 3 of PCI DSS compliance applies to businesses that process between 20,000 to 1 million transactions per year. The requirements for compliance are identical to those in PCI compliance level 2.
Level 4, the most basic level of compliance, applies to businesses handling fewer than 20,000 transactions per year. To comply with PCI DSS Level 4, organizations are required to:
PCI compliance isn’t just for security and compliance experts. Developers also play a big part in making sure credit card information stays safe when creating software and after it’s launched.
Simply put, PCI compliance means that when building software, developers should work closely with security and compliance teams. Together, they make sure credit card details are safe, whether they’re being moved around or stored.
To developers, PCI might seem like other rules they’ve heard of, like GDPR (which is about personal data privacy) or HIPAA (which is about health information). But PCI is special because it’s all about keeping credit card details secure.
It’s important for developers to understand this difference. They need to know the special rules of PCI and make sure they follow them when they write code, design software, or launch new tools. By thinking about these rules early on, they can build software that’s safe and follows the rules, without slowing down or losing creativity.
Developers have different levels of involvement with different requirements and sub-requirements in the PCI DSS, and the best way to explain their roles in ensuring PCI compliance is by looking at it as three key goals for software engineers:
For each above goal, there are different tools, some of which are tailored to the needs of software engineering teams. Let’s break them down to understand how to achieve each PCI compliance goal.
Protecting cardholder data from malefactors is at the heart of PCI compliance, and there are a number of ways developers can do that. But first, it’s important to understand what exactly is considered protected data under PCI DSS.
Cardholder or account holder data refers to information about the cardholder and the account itself and includes the card’s primary account number (PAN), the cardholder’s name, and the card’s expiration date, as well as the “full track” (magnetic stripe) data, the card verification code, and the PIN or PIN block.
To protect this data, developers should:
PCI DSS requirement 4 demands that all cardholder data is protected with strong encryption when traversing public networks. In a cloud-native environment, even traffic between microservices across clouds is technically traversing over a public network.
For developers, this means:
PCI compliance requires that application and code security are prioritized and addressed at every step of the SDLC, starting with the software requirement analysis for security requirements, and throughout the operational environment.
For developers, this translates into:
PCI compliance is not something you achieve and forget about. As you grow your business and expand the capabilities and features of your applications, it’s important to remember how these changes affect your PCI compliance posture. For example, a boom in business that dramatically increases your number of transactions may move you between compliance levels.
As noted above, the principles behind PCI compliance are not different from other privacy and security standards. They provide a set of technical guidelines for ensuring the security of credit card and credit card holder information, some of which mirror Secure Software Development Life Cycle (SSDLC) and DevSecOps best practices.
When it comes to detecting vulnerabilities and misconfigurations in your code, SpectralOps offers a developer-friendly solution that integrates seamlessly into your CI/CD pipeline to keep vulnerabilities out, and code secrets in.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions