How Does Infrastructure as Code on AWS work?
Imagine having to manually provision and configure every device in a large corporation. Then visualize the upgrade process. How about patching? Then, picture ensuring conformity on
Welcome to the world of Docker containers, where the power of isolation and portability meets streamlined application development. Whether you’re an experienced Docker user or just starting your containerization journey, effectively understanding and utilizing WORKDIR can significantly enhance your development workflow.
61% of respondents to a recent Statista survey said they use Kubernetes, putting Docker and Kubernetes among the most in-demand skills by software firms globally. Knowing how to use Docker and all its features will help your business and tech teams maximize its benefits and collaborate better.
In this article, we will look at the essential aspects of Dockerfile’s WORKDIR command, its use cases, and how to get started with it correctly.
Docker is an open-source platform that simplifies building, packaging, and deploying applications using containers. Containers are isolated environments that bundle an application with its dependencies, ensuring consistent operation across systems.
Imagine you’re a developer working on a web app with specific language versions and dependencies. Setting up the production environment to match the development can be time-consuming and error-prone. With Docker, you can package your app and dependencies into a self-contained unit, runnable on any system.

WORKDIR is a command that serves as a compass, directing subsequent instructions to operate within a specified working directory. Setting the working directory with WORKDIR establishes a solid foundation for running other commands like RUN, CMD, ENTRYPOINT, COPY, and ADD. It provides a structured environment for executing these instructions and organizes files, dependencies, and operations within the designated directory.
FROM ubuntu:alpine WORKDIR /app RUN pwd
The above simple example demonstrates the usage of this WORKDIR command. The WORKDIR /app command sets the working directory inside the container to /app. This means that any subsequent commands or file operations will be performed within this directory. Then the RUN pwd command is executed during the build process and prints the current working directory, which in this case it is /app.
WORKDIR /a WORKDIR b WORKDIR c RUN pwd
In this scenario, we have a sequence of WORKDIR commands and a subsequent RUN pwd command. There is a relative path in the first WORKDIR command and therefore the output of the final RUN pwd will be /a/b/c directory.
ENV DIRPATH=/path WORKDIR $DIRPATH/$DIRNAME RUN pwd
In the above example, we are using a value in the environmental variable file to set the WORKDIR. Therefore the final RUN pwd command will output /path/$DIRNAME.
When specifying a directory that does not exist in the WORKDIR command, Docker automatically creates the directory for you within the container. If the WORKDIR command is not explicitly defined in a Dockerfile, the default working directory is set to the root directory (/).
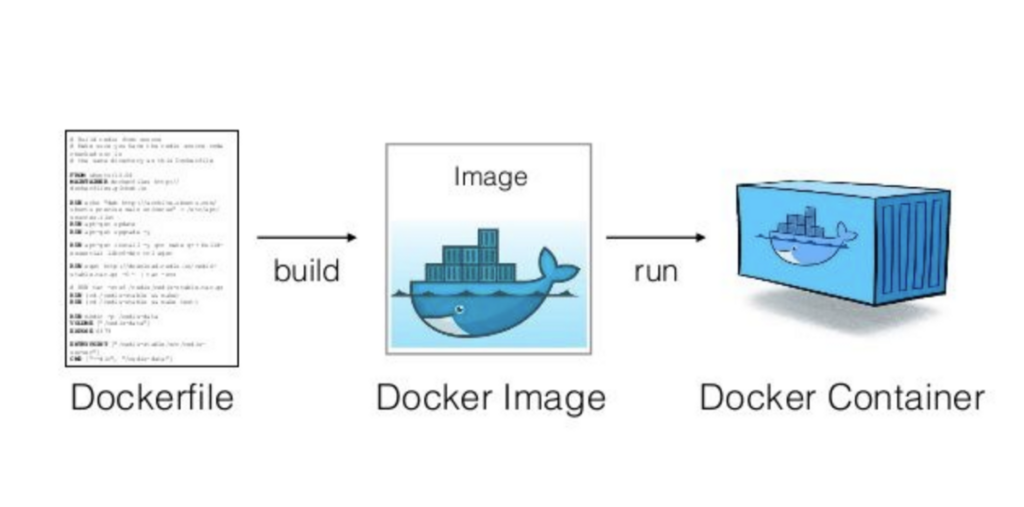
Dockerfile is a text-based configuration file that defines the steps and instructions for building a Docker image. It serves as a blueprint for creating containerized applications. With Dockerfile, you can specify the base image, install dependencies, copy files, and execute commands needed to set up the environment inside a Docker container.
The key difference between Docker and Dockerfile is that Docker is the platform or technology used for containerization, whereas Dockerfile is a specific file format used within Docker to define the build instructions for creating Docker images.
Optimizing the usage of Dockerfile WORKDIR is crucial for efficient and maintainable containerized application development. In this section, we’ll review seven best practices that will help both beginners and advanced users harness the full potential of WORKDIR.
Select descriptive names for your working directories to enhance the readability and maintainability of your Dockerfiles. For example, the below directory name indicates that myapp is a specific application within the /usr/src directory.
WORKDIR /usr/src/myapp
When specifying the WORKDIR, consider using absolute paths (the complete name of a directory or file from the root) to ensure stability and avoid potential issues with relative path resolution.
WORKDIR /var/www/html
Here, /var/www/html is an absolute path pointing to the directory where the content is located.
Set up your directory structure early in the Dockerfile to establish a clear code and avoid confusion in subsequent instructions. Basically, the point of this is to create all necessary directories at the beginning.
FROM ubuntu:alpine # Create the necessary directories at the beginning RUN mkdir /app RUN mkdir /app/src RUN mkdir /app/config # Set the working directory to /app WORKDIR /app # Copy package.json and package-lock.json to the working directory COPY package*.json ./ # Install dependencies RUN npm install # Copy the application source code to the src directory COPY src ./src # Copy the configuration files to the config directory COPY config ./config # Set the command to run the application CMD ["node", "src/app.js"]
Use environment variables to make your WORKDIR commands dynamic and flexible, allowing for easier customization and reuse.
# Define environment variables ENV APP_PATH=/app ENV CONFIG_PATH=/config # Set the working directory using variables WORKDIR $APP_PATH
When possible, group related commands and instructions within the same working directory to improve the logical flow and organization of your Dockerfile.
# Copy custom configuration files COPY nginx.conf /etc/nginx/nginx.conf COPY default.conf /etc/nginx/conf.d/default.conf # Set the working directory to /usr/share/nginx/html WORKDIR /usr/share/nginx/html # Copy the web application files COPY index.html . COPY styles.css . COPY scripts.js .
Minimize unnecessary changes to the working directory. Changing directories too frequently can make the Dockerfile harder to read and maintain. Instead, consider using multiple Dockerfiles or organizing your files in a way that minimizes the need for frequent directory changes.
Minimize the nesting of multiple levels of working directories within your Dockerfile. Excessive nesting can lead to longer and more complex file paths, which can make the Dockerfile harder to read and manage.
// AVOID WORKDIR /app WORKDIR backend WORKDIR subdirectory // USE WORKDIR /app/backend/subdirectory
Ensuring the security of containerized applications is paramount in today’s software development landscape. Here are some attacks that can occur due to container vulnerabilities:
Dockerfile WORKDIR plays a crucial role in creating clean and isolated environments for different application components, promoting reproducibility and consistency across various environments.
To mitigate these risks, it is crucial to implement Docker security best practices for container development, deployment, and runtime environments, including adopting a Secure Software Development Lifecycle (SSDLC). By following an SSDLC approach, organizations can integrate security considerations throughout the entire software development process, from design to deployment and maintenance.
Container scanning tools like Spectral offer robust solutions to enhance container security and mitigate vulnerabilities. Spectral uses advanced detection mechanisms to analyze containers for potential vulnerabilities, data leaks, and code integrity issues. With hundreds of detectors, Spectral helps safeguard your code, assets, and infrastructure, enabling you to proactively protect your containerized applications and ensure their security throughout the software development lifecycle.
Request a free demo today.

Imagine having to manually provision and configure every device in a large corporation. Then visualize the upgrade process. How about patching? Then, picture ensuring conformity on

In the world of Big Data, decentralization is king. Seeing that today’s data sets are so large and complex that traditional database systems cannot handle them,

Updated 03.24 Approaching any finish line in life can be exciting yet stressful. This holds especially true in software deployment. The deployment phase is the final