Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Researchers forecast that, over the next few years, open-source code will reach an annual growth rate of more than 25 percent. With cost savings and increased return on investment as the key drivers for this trend, you can’t afford to miss out on the opportunity to open source your internal software.
By open sourcing your code, you achieve better overall security with access to a wider audience to examine every detail of your code. But before you do, you need to secure it.
How can you prepare your code for external contributors? And why?
People like open-source software and with good reason. At the forefront of every decision to use open-source software is security, innovation, and reach.

Open-source code is more secure than proprietary, closed-source software, because it’s transparent so that anyone can check its security. This transparency promotes trust in your product. It also enables users to alert you about potential weaknesses in your code. When you correctly set up the code repository, they might even fix the issue for you and make a pull request.
When you develop your project behind closed doors, you limit the scope of ideas no matter how innovative your developers are. By exposing your code to the public, you increase the number of perspectives on how your project might grow. Also, you might not need to develop newly suggested features because others might simply do it because they want to.
Allowing others to invest time and energy into your project makes them feel invested, and invested customers are your best customers. They’re less likely to move away from your project. To help your project grow, they’re apt to work on it or share it with their colleagues. Your invested audience wants to see you succeed, and they’ll help you however they can.
Before you upload your Git repository to a public one, such as GitHub or GitLab, or simply open a private one to the public, you should follow these tips to protect your code.
Secrets are the basis for software-with-software communication and protecting digital communication. Examples of secrets include credentials, authentication tokens, encryption keys, and API keys.
Secret management is a set of processes to manage and maintain your secrets to enhance their security. The key components to this process are rotation, revocation, safe storage, and tracking.
Before you open source your code to keep your secrets secure, develop your secret management processes. One type of secret of particular importance to manage in this process are the credentials used to access into your public repository.
Secret proliferation has many causes. The leading one by far is the rapid migration of software, infrastructure, and platforms to the cloud. As the world moves to more cloud services and organizations follow, it becomes crucial for you to protect your secrets from leaking.
When moving your code base to the cloud, secrets can experience several potential points of failure. The biggest one is when developers use shortcuts during the development process and don’t correctly store secrets. As a result, they end up hard-coding secrets in the code.
When you expose your repository to the public, you not only expose the current state of the project but also the entire revision history. Unfortunately, a human can’t begin to scan through all revisions ever made on your project to look for secrets. Therefore, to ensure that no secrets are exposed before you open source your code, you must employ a secret scanning solution.

When opening up your code to the public, you gain continuous crowd oversight. People will review your code, find weaknesses, and suggest fixes. But what happens when a malevolent party finds your weakness before a benevolent one does? They might use their acquired knowledge to access your data.
When you expose your code structure to the public, you lose protection by obfuscation. Hackers can easily determine how your internal communications and endpoints work. Therefore, before opening your source code, you must secure your endpoints.
If your data is encrypted, protect the encryption keys because, once they become public, your data is no longer protected.
Popular cloud-hosted Git repositories, such as GitHub and GitLab, might lull you into a sense of security. However, you must take these extra steps to secure these repositories beyond the control of git hosting services.
First, when your repository is on the cloud, you can no longer afford to have people accidentally upload a sensitive file. So, create a gitignore file to add file types that you don’t want to commit to the repository.
Second, a common practice is to grant every developer access to all repositories. Often, they don’t need it. It simply exposes you to more potential errors. Therefore, limit access to anyone who doesn’t need it.

Secure your Git repositories in every way possible.
Code injections are much easier to execute than you might think. They become significantly easier when you have complete knowledge of the software. Before open sourcing your internal code, ensure that your code is not excessively vulnerable to code injections.
That is, properly sanitize inputs to avoid LDAP injections. Escape special characters, such as –, ( ), !, |, &, and *. And, be careful about allowing command or shell injections, which allow attackers to run shell commands on the server that’s running your application.
SSH keys are a public/private key pair that allows public encryption and private decryption. Specifically, when using SSH keys to communicate with a server, a user submits the public key to the server, establishing a secure communication channel. The server encrypts information sent to the user that only they can view. In return, the user sends information to the server that it can confirm originated from the user.
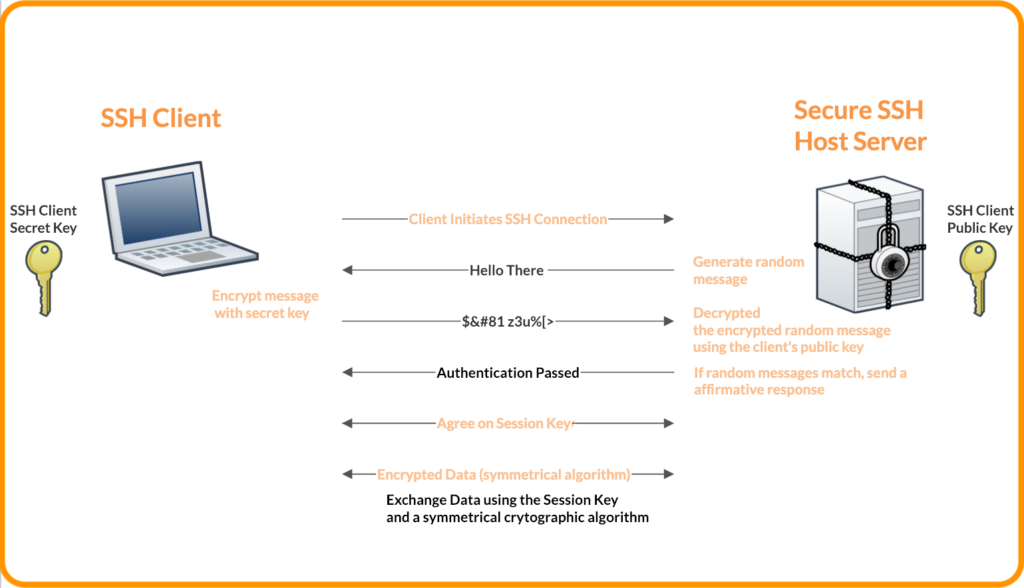
Using SSH keys for authentication with Git servers is more secure. And, once you move past the initial setup, it’s much easier than using usernames and passwords. Although you could pass around SSH keys between colleagues, it’s more involved than simply telling them your username and password, greatly restricting this harmful practice.
Manual code review is impractical for security purposes; only an automated solution can provide adequate security for your code. Although you might be tempted to implement an in-house secret scanning solution, such solutions produce a high number of false positives. These inaccurate results greatly reduce the effectiveness of automated security because humans must review every alert. Like the tale of the boy who cried wolf, if you have a lot of false positives, no one will trust the system. Soon, the alerts are ignored because they’ll be regarded as false positives, and you’ll lose the benefits of an automated system.
Automated tools can protect your entire SLDC when properly integrated into your continuous integration and continuous delivery (CI/CD) pipeline. A smart automated security solution provides real-time detection of commits and sanitizes your entire history, which is a critical step before you open source your internal code.
In conclusion, before releasing your code to the world, make sure it’s ready by following the tips in this post. You can implement some of them on your own, like using SSH keys and securing your Git repositories. But the more intensive tasks that require heavy lifting demand an automated solution.
An easy way to automate code secret security in your code is to connect SpectralOps to your CI/CD pipeline. Request a demo to see how easily you can get started and prepare your code for open source.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions