Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
DevSecOps – for many, it feels like a magical black box where code and sensitive digital assets go in one end, and a working piece of software comes out the other. Security practices within the development and operational phases can often get lost.
Organizations that haven’t adopted DevSecOps see half of their apps at risk of attacks, while those with a DevSecOps-first approach have only 22% at risk.
That’s why the core principles of DevSecOps are important. These principles are not just methodologies but also a mindset that encourages continuous improvement, collaboration, and a proactive stance toward security challenges.
But what are the core DevSecOps principles?
The first principle of DevSecOps, Enhanced Continuous Integration and Continuous Deployment (CI/CD), is a cornerstone in blending speed, efficiency, and security in software development.
For example, a company leveraging CI/CD can promptly implement security updates, staying ahead of potential threats. This rapid deployment is vital for upholding both system security and regulatory compliance.
The second principle of DevSecOps, Proactive Security Measures, is essential in embedding security within the software development lifecycle from its earliest stages. This principle advocates for a preemptive approach to security, a “shift-left” movement to ensure that risks are identified and mitigated before they escalate into significant vulnerabilities.
An example of a proactive measure is the integration of automated security testing tools, like SAST and DAST, into the CI/CD pipeline. These tools continuously scan for vulnerabilities, ensuring that security issues are identified and resolved promptly, thereby reducing the risk of post-deployment security incidents.
The third principle of DevSecOps, Enhanced Collaboration, and Communication, is critical for integrating various aspects of development, security, and operations into a cohesive workflow. This principle emphasizes the importance of effective collaboration and clear communication to ensure that security is seamlessly incorporated into every stage of the software development lifecycle.
One key example of this principle in action is the use of cross-functional teams. When developers, security experts, and operations staff collaborate closely, they can quickly identify and address security issues, leading to a more secure and efficient development process.
The fourth principle of DevSecOps, Automation of Security Processes, plays a pivotal role in enhancing the efficiency and effectiveness of security within the software development lifecycle. This principle underscores the importance of automating repetitive and time-consuming security tasks, thereby streamlining the security process and ensuring consistent application of security standards.
Automated vulnerability scanners continuously scan the codebase for known vulnerabilities, alerting teams immediately when issues are detected. This continuous monitoring allows for quick remediation, significantly reducing the window of exposure to potential security threats.
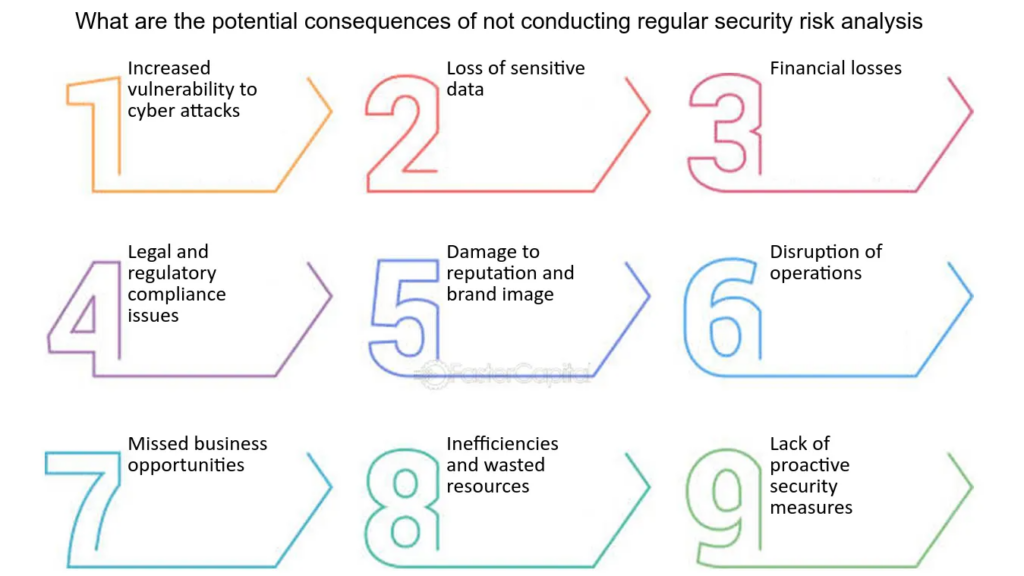
“Compliance as Code” refers to the practice of defining and implementing compliance and security policies as code. This approach allows for the automated enforcement and verification of compliance standards throughout the software development process. The benefits are substantial:
Failure to implement “Compliance as Code” can lead to significant issues. In regulated industries like finance or healthcare, non-compliance can result in legal penalties, data breaches, and severe reputational damage.
This principle focuses on the continuous observation and recording of system activities, enabling teams to quickly detect, diagnose, and respond to security incidents. The implementation of real-time monitoring and logging is essential, not only for identifying and mitigating immediate threats but also for maintaining the overall health and security of the system.
The absence of robust real-time monitoring and logging can have severe consequences. For instance, undetected intrusions or slow responses to security incidents can lead to extensive data breaches, system downtimes, and loss of customer trust.
The seventh and vital principle of DevSecOps is Regular Security Training and Awareness, which emphasizes the continuous education and sensitization of all team members about security. This principle recognizes that technology alone is not sufficient to ensure security; the human element is equally crucial. The significance of this principle lies in its focus on fostering a security-centric mindset among team members, ensuring that everyone is equipped to recognize and respond to security challenges effectively.

Neglecting regular security training and awareness can lead to severe repercussions. Without ongoing education, team members may become unaware of evolving threats and best practices, increasing the likelihood of security oversights or errors.
In an era where software development cycles are ever-accelerating and security threats are increasingly sophisticated, embracing the core principles of DevSecOps is not just an option—it’s a necessity.
Don’t let security be an afterthought. Make it the cornerstone of your development strategy with SpectralOps.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions