Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
What if your most personal chats, the very foundation of your digital existence, were exposed? Unfortunately, that’s precisely what happened with the Salt Typhoon Hack on July 2024, a terrible cyberattack that put big U.S. telecom companies at risk.
The scale of this intrusion has never been seen before. Malicious actors accessed sensitive data such as call logs, metadata, and even interactions with key political officials. This attack was more than a mere technological failure; it directly threatened our privacy and national security. With global cybercrime costs projected to reach $10.5 trillion annually by 2025, the urgent need for robust cybersecurity measures has increased.
The Salt Typhoon hack sharply reminds us that the risks in the cybersecurity arena have never been greater. This was a wake-up call for every organization around the world to develop stronger security practices, proactive monitoring, and resilient infrastructure to protect sensitive data and modern workflows.
The Salt Typhoon Hack is a cyber espionage campaign attributed to Chinese state-backed attackers. In July 2024, they targeted major U.S. telecom providers like AT&T, Verizon, and T-Mobile by exploiting unpatched routers, misconfigured switches, and outdated systems. These vulnerabilities allowed attackers to gain access to core networks and extract sensitive data such as call records, metadata, and encrypted communications.
The attack highlights the risks of overlooked misconfigurations and weak access controls, which often appear in CI/CD pipelines and developer workflows. Common mistakes like hardcoding credentials, using tools without proper security analyses, and using unpatched systems give attackers easy entry points. Addressing these gaps with automated scanning, secure coding practices, and real-time monitoring is essential to prevent similar breaches.
The impact of the Salt Typhoon Hack was massive. But, it was an eye-opener. Here are the key reasons why this attack stands out:
Telecommunications networks are the backbone of the modern digital world. Every government, business, and individual uses them in their daily work.
Targeting these systems allows attackers to disrupt a large number of essential services, such as healthcare systems and financial transactions, and expose flaws like unpatched routers, weak encryption, and open access points in these critical systems.
Furthermore, the scale of the Salt Typhoon Hack was a wake-up call for all industries that use interconnected systems to determine how a single breach can fail entire operations, disrupt economies, and compromise public safety. Hence, organizations must prioritize infrastructure resilience and adopt tools that continuously monitor and secure their networks.
The Salt Typhoon Hack highlights how insecure CI/CD workflows can become gateways for attackers due to overlooked dependencies, hardcoded credentials, and misconfigurations. Strengthening CI/CD security is vital to protect production systems.
For example, insecure configurations, overlooked dependencies, and hardcoded credentials are common mistakes when building a CI/CD pipeline. Once attackers exploit these weaknesses, they can attack production environments, manipulate code, or access sensitive data.
So, developers should always think of the security of their CI/CD pipelines by:
The Salt Typhoon Hack was not just about compromising data. Attackers collected valuable information on areas like politics, government operations, security and economics, posing long term risks like:
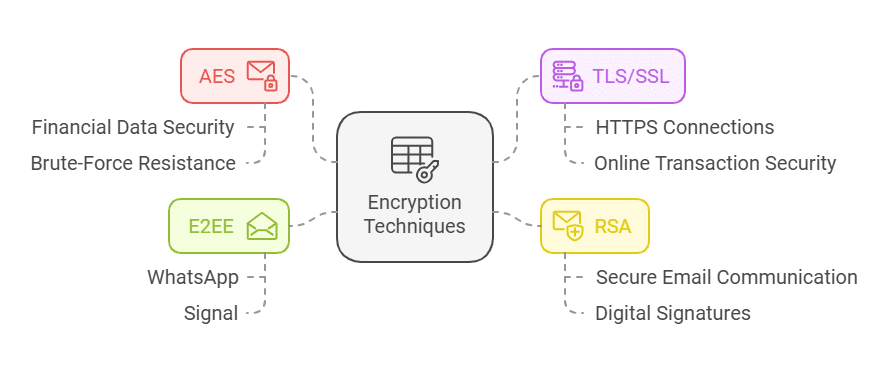
Hence, organizations should always prioritize protecting sensitive data and use robust encryption protocols like AES, TLS/SSL, RSA, and E2EE to encrypt data, secure communication tools, and comprehensive monitoring systems to detect unusual access patterns.
The Salt Typhoon Hack offers several actionable lessons for security teams and developers:
Spectral’s developer-first approach to security seamlessly integrates into pipelines, enabling real-time detection and resolution of issues that could otherwise be exploited in large-scale attacks like Salt Typhoon.

Preventing attacks like Salt Typhoon requires introducing security into every phase of the software development lifecycle. This shift-left security approach focuses on detecting and fixing vulnerabilities in the early stages to reduce the cost of fixing them.
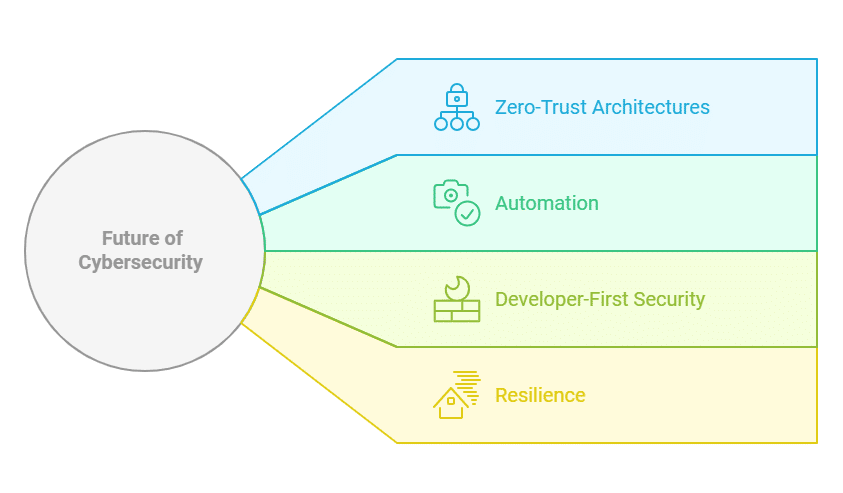
Cyber threats evolve daily, and organizations should also continuously look for new ways to make their systems resilient. Here are a few key trends shaping the future:
The Salt Typhoon Hack is a clear reminder of how even the most critical systems can be victims of cyber attacks. It exposed some of the most common gaps in modern IT infrastructure and CI/CD pipelines, such as exploited misconfigurations and overlooked vulnerabilities.
By integrating automated security tools into your development workflows, you can proactively identify and mitigate vulnerabilities before they can be exploited. Spectral provides developer-first solutions that seamlessly integrate into your CI/CD pipelines. Our AI-powered platform identifies and addresses security issues in real-time, ensuring your software remains secure without slowing down development.
Don’t wait for the next major breach. Start your security journey with Spectral today to stay ahead of modern cyber threats.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Quick announcement: with SpectralOps you can prevent data breaches by protecting your code from hard coded secrets and misconfigurations. You know how it goes: Every website,

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our