Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
SaaS adoption has skyrocketed, offering organizations undeniable advantages. But beneath the surface lurk overlooked configuration errors. Misconfigured SaaS settings create security gaps. Broad permissions, weak defaults, and forgotten accounts jeopardize your security. These issues act as open doors for breaches and unauthorized access.
The sheer scale of the problem is staggering – 70% of company software now resides in the cloud.
Traditional security measures struggle with these unique SaaS threats. SSPM (SaaS Security Posture Management) becomes essential.
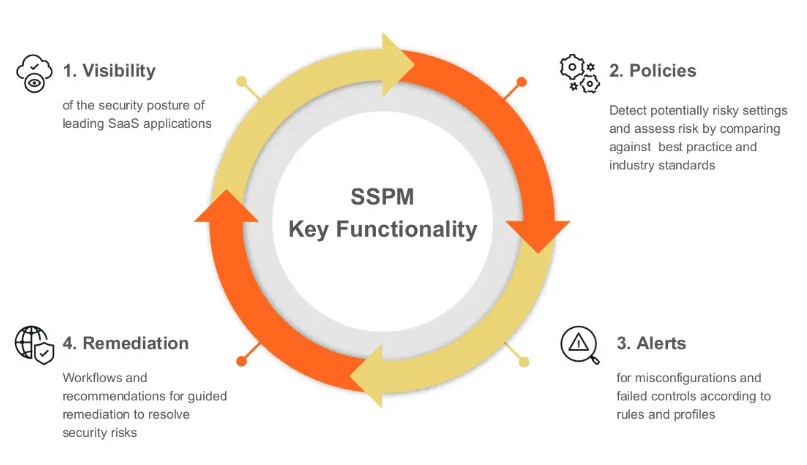
SaaS Security Posture Management (SSPM) safeguards your cloud-based (SaaS) applications. SSPM protects your SaaS applications by monitoring for vulnerabilities and configuration errors. This technology identifies risks, provides clear remediation steps, and prevents threats.
It’s easy to assume security for SaaS tools rests on the provider. Reputable companies invest in securing their software, infrastructure, and customer data, but the recent Cloudflare Auth Token breach highlights the risks users can unwittingly introduce.
SaaS providers safeguard their platforms, but that doesn’t eliminate security risks. SaaS misconfigurations leave you exposed. Weak settings, broad permissions, and how your team uses these tools pose risks. Don’t wait for a breach – address these vulnerabilities.
Here’s where risk surfaces:
SaaS misconfigurations create a range of dangers:
Even well-meaning employees can put data at risk. If they adopt SaaS tools without IT approval (“shadow IT“), this creates serious problems:
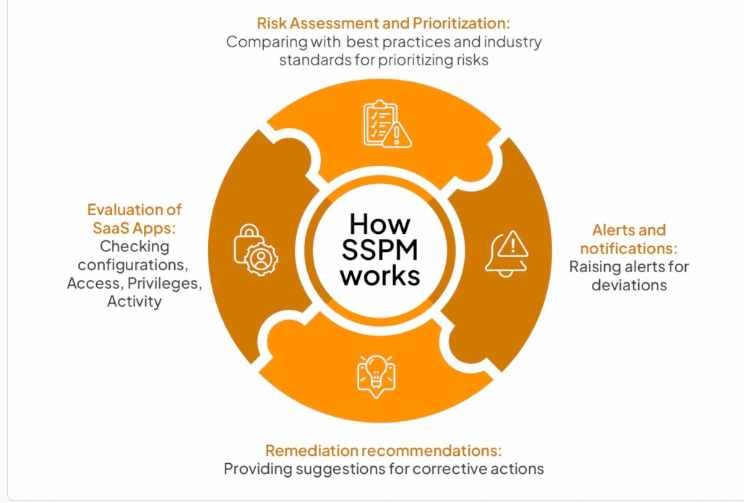
Tools matter, but usage matters more. Misconfigurations and employee behaviors can expose weak points attackers exploit. SSPM proactively finds these risks, protecting your cloud environment from becoming a liability.
SSPM helps you build a comprehensive map of your entire SaaS footprint.
SSPM pinpoints vulnerabilities stemming from misconfigurations before they have an impact.
SSPM secures your SaaS environment. Reduce your attack surface and enhance security settings with clear, actionable steps.
SSPM automates vigilance, catching early signs of risk and safeguarding your systems proactively.
With SaaS tools, it’s easy to fall into a ‘set it and forget’ mentality. Maintaining a secure and compliant posture takes an active approach.
Here are five questions for you to answer.
A decentralized IT model undermines security. Teams using different SaaS tools without coordination open you up to dangers.
Decentralized tool management harms everyone:
Without an inventory of your SaaS platforms and the data they hold, you’re flying blind:
Even well-intentioned adjustments made by authorized users can have far-reaching security implications. You can stay ahead of emerging weaknesses if changes are easily tracked and assessed for risk.
Regulations like GDPR and HIPAA mandate that sensitive data be secure throughout its cloud journey. You cannot adequately protect sensitive customer or internal data, including personally identifiable information (PII), from leaks and breaches.
SSPM makes sure you stay compliant through:
Well-intentioned adoption of unsanctioned SaaS solutions might simplify workflows, but it can introduce unforeseen security and compliance risks. Does your organization need strong oversight and guidance in this area?
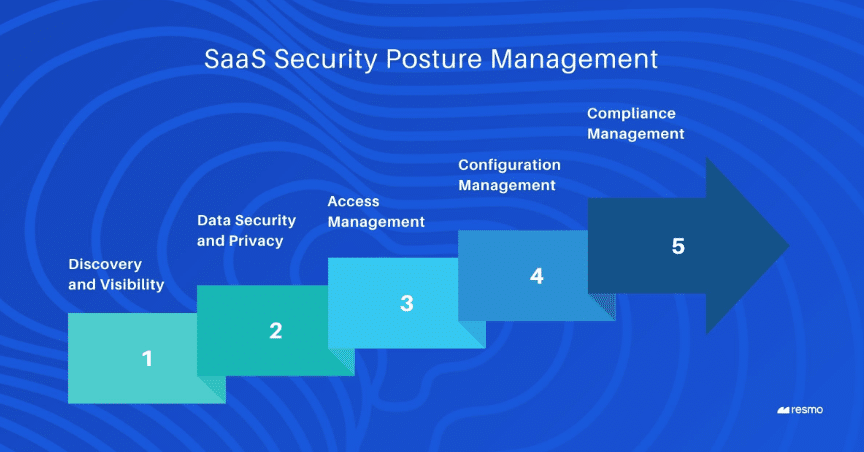
SSPM is essential for preventing SaaS-based breaches, offering even broader security benefits. It improves both security and organizational efficiency by:
SSPM actively improves operations. Through discovery, analytics, and automated actions, it reduces costs created by SaaS sprawl.
SSPM empowers your people to work smarter, not harder:
SaaS security doesn’t exist in a vacuum. SSPM offers two significant wins:
SSPM brings specialized benefits that complement your broader cybersecurity setup. This solution doesn’t replace your existing security. It amplifies it.
Here are three things SSPM can do for your SaaS security:
One key strength of SSPM is that it maximizes your security investment. An SSPM solution integrates seamlessly with existing tools, including advanced cloud threat detection and response (CTDR) platforms for even deeper visibility.
SSPM streamlines security with prioritized risk reports instead of complex configurations. Outdated tools bury teams in data, slowing response times and hiding threats. Quick response is critical. SSPM surfaces urgent SaaS risks and guides their immediate resolution.
Perhaps most importantly, SSPM enables a proactive approach rather than reactive scrambling. Harness the power of threat intelligence to make your SaaS environment stronger! SSPM reveals vulnerabilities specific to cloud apps. This data enables you to act and secure things on your terms before attackers exploit them. Address weaknesses proactively to prevent breaches.
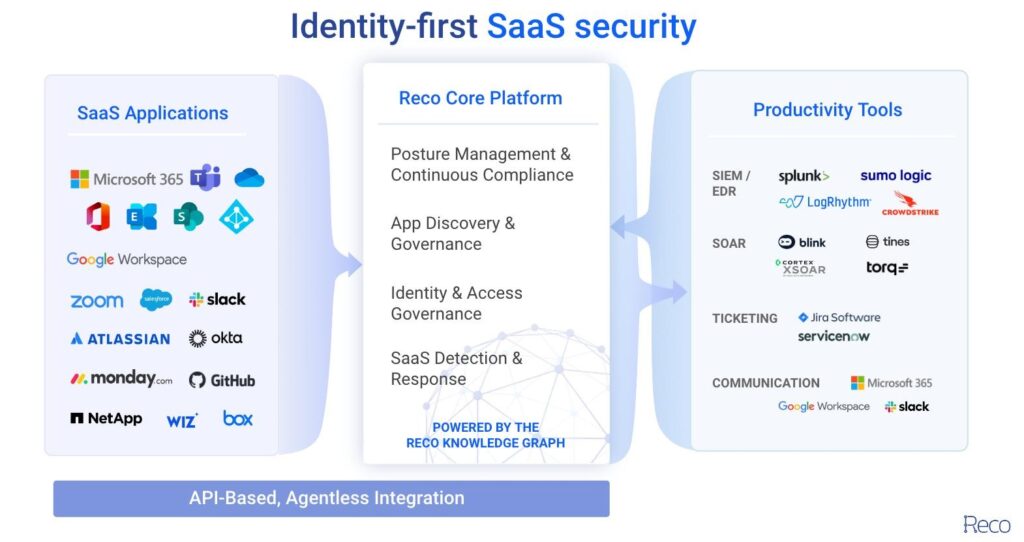
The evolving SSPM market offers a range of solutions to meet varied needs. When assessing platforms, prioritize these 7 factors:
Can the SSPM handle your specific mix of SaaS platforms? Don’t fly blind with incomplete SaaS security. Coverage gaps create exploitable weaknesses. Ensure your SSPM protects even niche tools critical to your industry.
How deep is the analysis? A thorough assessment should prioritize risks based on potential impact. Prioritizing fixes with the highest impact on vulnerabilities simplifies your team’s work.
Regulatory pressure isn’t going away. Does the SSPM streamline compliance reporting for standards like GDPR and HIPAA? Can it easily show the linkage between your SaaS setup and regulatory requirements?
Your tech evolves – your SSPM needs to keep pace. Outdated tools hinder growth, forcing costly migrations due to incompatibility. Choose cloud-native SSPMs that scale with you for peace of mind.
Maximize the value of what you already own. Avoid creating new problems when picking a security tool. SSPM integration is critical. Choose an SSPM that plays well with your existing tools! Look for easy integration with your SIEM, endpoint protection systems, and vulnerability scanners.
Don’t rely on yesterday’s security. An effective SSPM taps into vast threat data pools, which may include container-specific vulnerabilities for unmatched defense. Attackers evolve – and so should your security. The best tools offer defense against many threats. These range from simple automated attacks to complex strategies targeting SaaS weaknesses.
SaaS security isn’t static. When evaluating a solution, consider responsiveness to emerging threats. Additionally, does it have a long-term roadmap aligning with the ever-evolving cloud landscape? A solid vendor relationship offers security confidence.
A complex cloud footprint with a focus on risk-based security calls for SSPM. The ROI extends beyond breach prevention – it optimizes your entire cloud environment.
Hardcoded API keys, passwords, and sensitive data create significant security vulnerabilities. Traditional SSPM tools might only catch some of them. Spectral is your specialized “secret hunter” to safeguard critical assets from leaks and misuse.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions