Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Knowledge is power. Power is money. In the context of information systems and applications, knowledge is ingested, processed, and used as data. Data theft or loss can be devastatingly costly to a business. Data is one of an organization’s most valuable assets, and must be secured and protected as such.
But protecting sensitive data is easier said than done, especially with an exponentially growing trend of storing and processing data in the cloud, and self-service infrastructure management capabilities (like infrastructure as code).
While approximately 89% of organizations host sensitive data or workloads in the cloud, 39% of businesses admit to having experienced a data breach of their cloud environment in the last year. With increasing regulatory compliance demands for data protection and privacy, there is a need for a framework to measure and enhance the overall security posture of organizations’ data management practices in cloud environments.
That’s where DSPM comes in to fill the gap.

Gartner identified Data Security Policy Management (DSPM) as an emerging and transformational technology. It was described as a set of tools and practices that “provide visibility as to where sensitive data is, who has access to that data, how it has been used, and what the security posture of the data store or application is.”
From a developer perspective, DSPM can be defined as a “data first” approach to protecting the organization’s data from potential threats. At its core, DSPM aims to help organizations establish, enforce, and maintain the controls and measures necessary to prevent data breaches, meet regulatory compliance demands, and reduce the risks that stem from data residing in unmonitored cross-vendor cloud data stores.
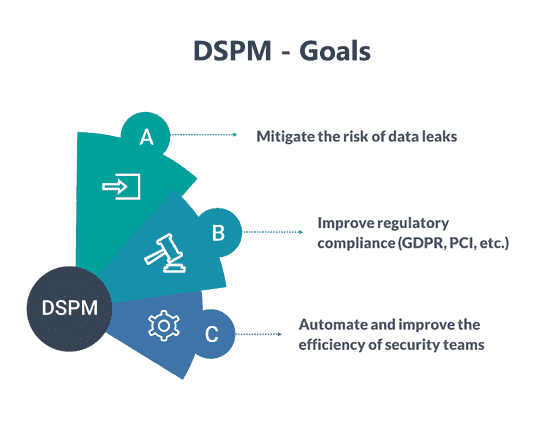
Unlike traditional information security approaches and measures, DSPM takes an inside-out approach to data protection, focusing on data – where it is stored, how it’s stored, who uses it, etc. – rather than on securing devices, networks, or application functions. The key components and stages of DSPM include:
You might already have CSPM to protect my multi-vendor cloud deployments. So why do you need DSPM as well?
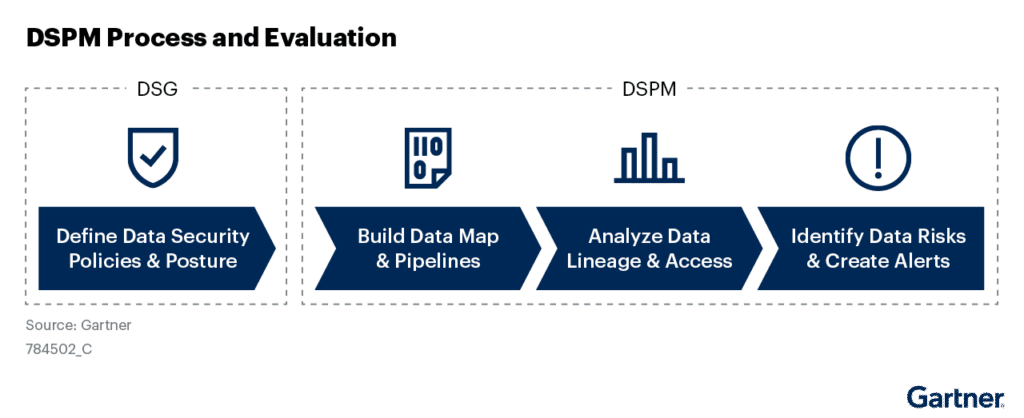
Cloud Security Posture Management (CSPM) solutions are focused on protecting the infrastructure and not the data it stores. It aims to secure the workloads, services, and networks managed by the public cloud provider, as well as data and applications hosted on the cloud without inducing dedicated and granular data-level protection.
DSPM, by contrast, is designed to secure and govern all the data that organizations manage regardless of its location – the cloud, on-prem servers, SaaS, or endpoint devices.
If you ask a CISO what the ultimate worst-case scenario is, there’s a good chance their answer will be data breaches.
It’s not surprising, especially if you consider the rising costs of data breaches, fueled by cybercriminals’ adoption of increasingly sophisticated ransomware systems. DSPM addresses the challenges of securing sensitive data in complex environments across multiple cloud vendors and SaaS providers in several avenues. Here are the top 4:
DSPM aims to secure critical data in the organization by automating a great portion of the manual labor entailed in identifying and managing potential vulnerabilities. These include misconfigurations, excessive access permissions, outdated policies, supply chain attacks, and other threats detected in real-time through monitoring.
DSPM can help you in your compliance journey by aligning your data security efforts with the demands of relevant regulatory frameworks like the Payment Card Industry Data Security Standard (PCI-DSS) in the finance industry, the Health Insurance Portability and Accountability Act (HIPAA) in the Health industry, as well as the General Data Protection Regulations (GDPR) in the EU, the California Consumer Privacy Act (CCPA), and The California Privacy Rights Act (CPRA). In addition, DSPM can streamline compliance auditing and preparedness in cohesion with your security and compliance tool stack.
Having a holistic view of your data stores and flows across multi-vendor cloud and SaaS environments lets you apply the policies and controls you need to reduce risk and strengthen your security posture.
Infosec and DevOps teams are already busy trying to keep up with the increasing complexity of multi-cloud environments in a dynamic threat landscape. DSPM employs automation throughout the processes of data discovery, classification, and of course – monitoring for issues as they arise and remediating them without manual input. This helps free your teams to focus on high-value business priorities without neglecting data security.

Integrating DSPM into your overall data security and compliance strategies introduces a number of benefits. However, before you invest more time and resources in DSPM, it’s worth checking if you even need it.
For example, that simple standalone web app someone in the company created to streamline lunch orders. There’s no login or profile, and the tiny site most likely collects only employee names and meals of choice, so it’s safe to say that it doesn’t need the data security envelope provided by DSPM practices. So when do you need DSPM? When you answer “yes” to one or more of these questions:
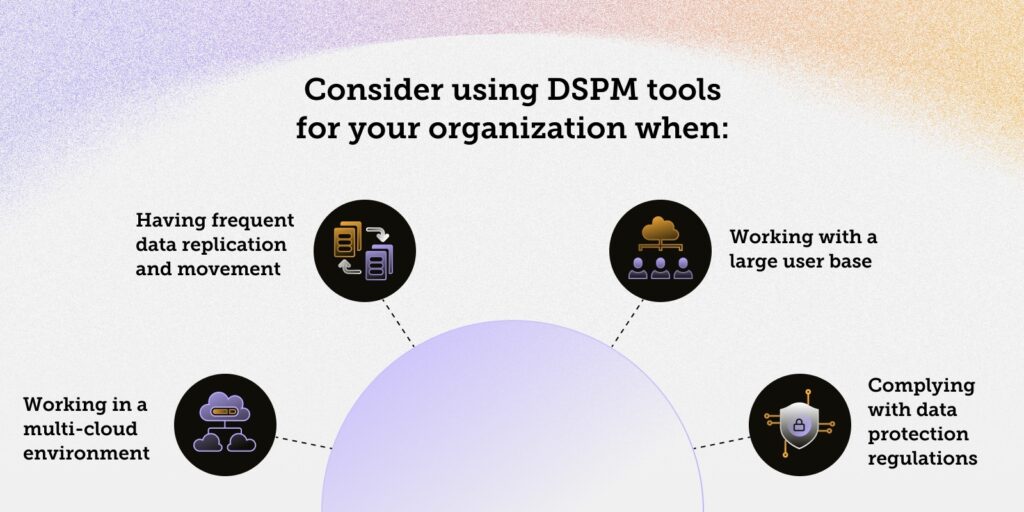
DSPM adoption is a process that requires collaboration between information security, compliance, and DevOps teams to plan and execute a DSPM strategy in a way that aligns with other practices, tools, and processes in the organization. When choosing the DSPM tools and services to cater to your needs, here are the top 5 things to keep in mind:
When discussing data security posture management, the types of data we tend to think about are payment details, medical records, and other personal information. However, one type of sensitive data that is still too frequently exposed in code and other assets in the development process are credentials and API keys. For example, in 450,000 public PyPI projects scanned, researchers found 4,000 unique secrets including Azure Active Directory API Keys, GitHub OAuth App Keys, various types of database credentials, Auth0 keys, SSH credentials and more.
For attackers, gaining access to such credentials and passkeys is a sure path toward data theft, ransomware deployment, or resource abuse. With SpectralOps by CheckPoint, you can rest assured no code secrets or passwords leak onto public-facing repositories or projects. With turnkey integration into your CI/CD pipeline and infosec stack, SpectralOps protects the keys to your datastores and repositories across services, development pipelines, and application infrastructure.
If you want to see how SpectralOps can help you protect your cloud environment, you can sign up for a free trial today.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions