Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
Trust is fragile in software, especially in the fast-paced complexity of cloud environments. Code signing reinforces that trust by digitally proving your software’s authenticity and integrity.
Breaches like the UnitedHealth Group incident remind us why this matters—compromised code has real-world consequences. The breach potentially exposed the sensitive health data of millions of Americans.
Your code, all the libraries it relies on, and even the infrastructure it runs on are all potential weak spots. Azure Code Signing is how you keep the trust.
Azure Code Signing (ACS) provides a mechanism to guarantee software integrity and authenticity by preventing unauthorized modifications and strengthening end-user trust.
Let’s break down how it works.
Azure Code Signing (ACS) is a way to digitally “sign” your software. This confirms its authenticity and verifies that it hasn’t been altered after release. ACS is particularly crucial in cloud environments, where the dynamic nature demands constant trust verification.
Here’s how Azure Code Signing works.
ACS relies on digital signatures and certificates, which act as a verifiable form of identification for your code. Azure Key Vault provides a secure storage and management solution for the sensitive private keys used during the signing process.
ACS incorporates timestamping for long-term trust assurance. Even if security standards evolve or certificates expire, a trusted timestamp in your code ensures its ongoing validity.
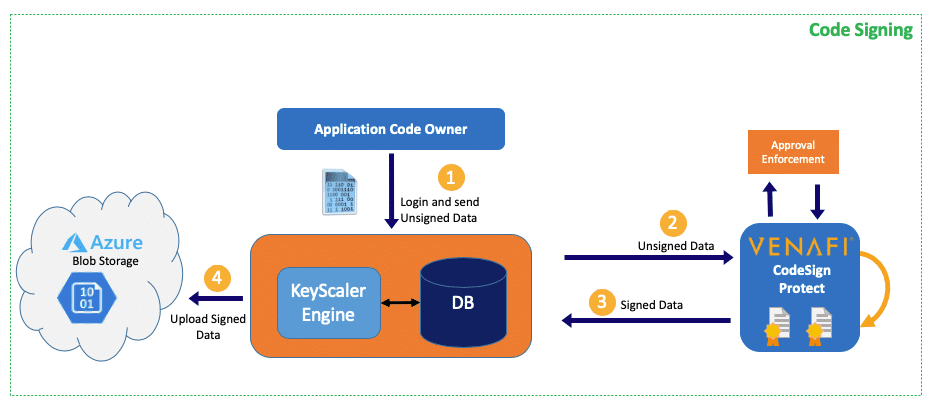
Here’s a quick breakdown of how Azure Code Signing is implemented in three easy steps.
For broader trust, procure a certificate from a trusted Certificate Authority (CA) or consider self-signed certificates for internal use. Key Vault streamlines certificate management.
Integrate signing into your build/deployment pipelines. SignTool (for Windows) or Jarsigner (for Java) will embed the digital signature into your code.
Deploy your signed code with confidence. Azure Code Signing helps verify the signature throughout the code’s lifecycle.
Azure Code Signing helps ensure your software hasn’t been altered after release. It uses cryptographic techniques to create a unique digital “fingerprint.” Any changes made to the code would break the fingerprint, immediately signaling that something is amiss. However, malicious actors or exploit vulnerabilities can find subtle ways to inject harmful code or exploit vulnerabilities without directly modifying your original files.
Advanced vulnerability detection addresses these risks, scanning your codebase for weaknesses like exposed secrets, misconfigurations, or outdated dependencies that could compromise your software’s integrity.
In a world where software origins can be unclear, code signing can prove your code’s authenticity. It relies on trusted Certificate Authorities to issue certificates that link your identity to your software.
Think of these certificates like digital passports for your code. With its secure integration with Key Vault, Code Signing provides robust storage and management of these certificates, strengthening the chain of trust.
Software today is built on a complex web of dependencies. A single compromised component can have far-reaching consequences. Code signing helps validate the integrity of each element within your supply chain, minimizing the risk of unauthorized changes or malicious code slipping in.
For maximum protection, consider extending code signing requirements throughout your software ecosystem, including third-party dependencies and external collaborators.

Demonstrating compliance with regulations like PCI DSS, HIPAA, and others often requires proving that your software is protected from tampering. Doing so contributes to a more robust cloud risk management posture.
Azure Code Signing provides a clear audit trail and timestamped signatures, simplifying compliance. Timestamping also helps maintain compliance over time, even if the cryptographic standards or certificates evolve.
Azure Code Signing acts as a stamp of quality for your software. Users see that you take security seriously, fostering greater trust in your products.
A commitment to security translates into a competitive advantage and contributes to a more secure and reliable digital environment for everyone.
As you integrate Azure Code Signing (ACS) into your workflows, let’s dive into the implementation details that maximize its effectiveness.
Implementing Azure Code Signing isn’t just about the ‘how’; it’s a cornerstone of secure Azure deployments. By carefully choosing certificates and automating signing, you bolster your software defenses and protect against code tampering threats.
Prerequisites:
Log in to the Azure portal.
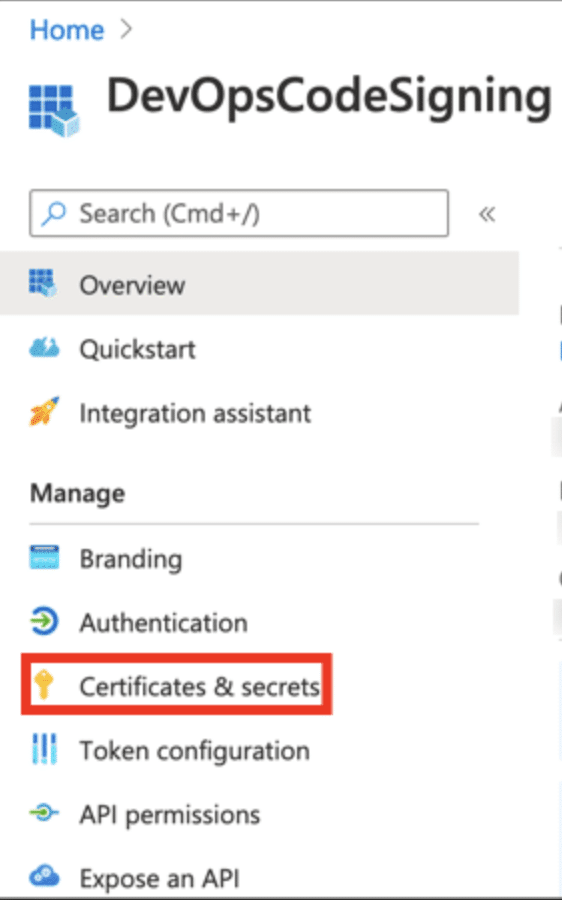
Navigate to your registered application’s settings. Look for a section called “Certificates & secrets” on the left-hand menu.
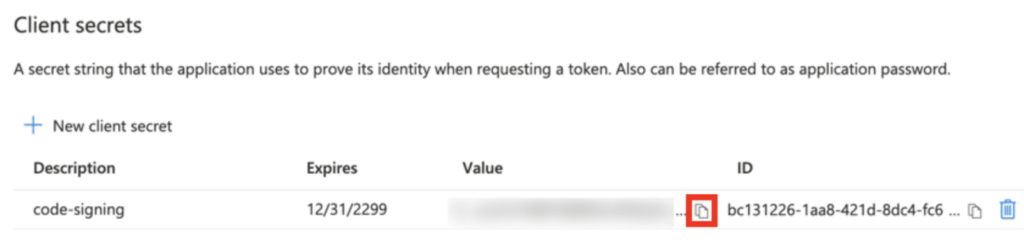
Click “New client secret”.
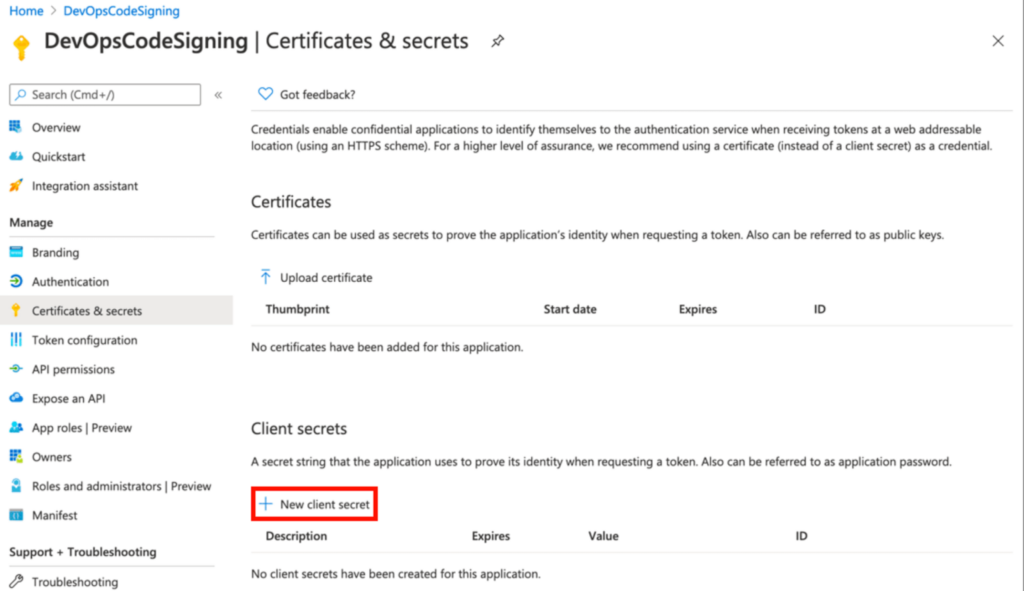
Click “Add” and immediately copy the generated secret. Important: This is the only time you’ll see it in full – save it securely.
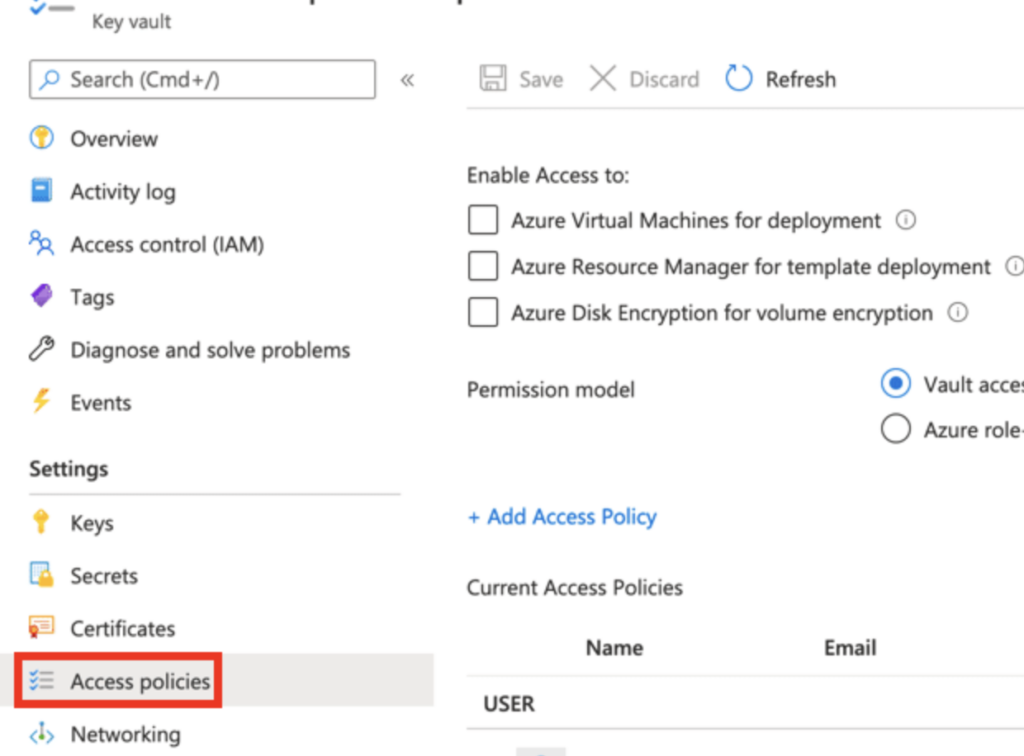
Make sure your application has the necessary access levels to your Azure Key Vault and other pipeline resources. Go to your Key Vault and click on “Access Policies”. Click “Add Access Policy”.
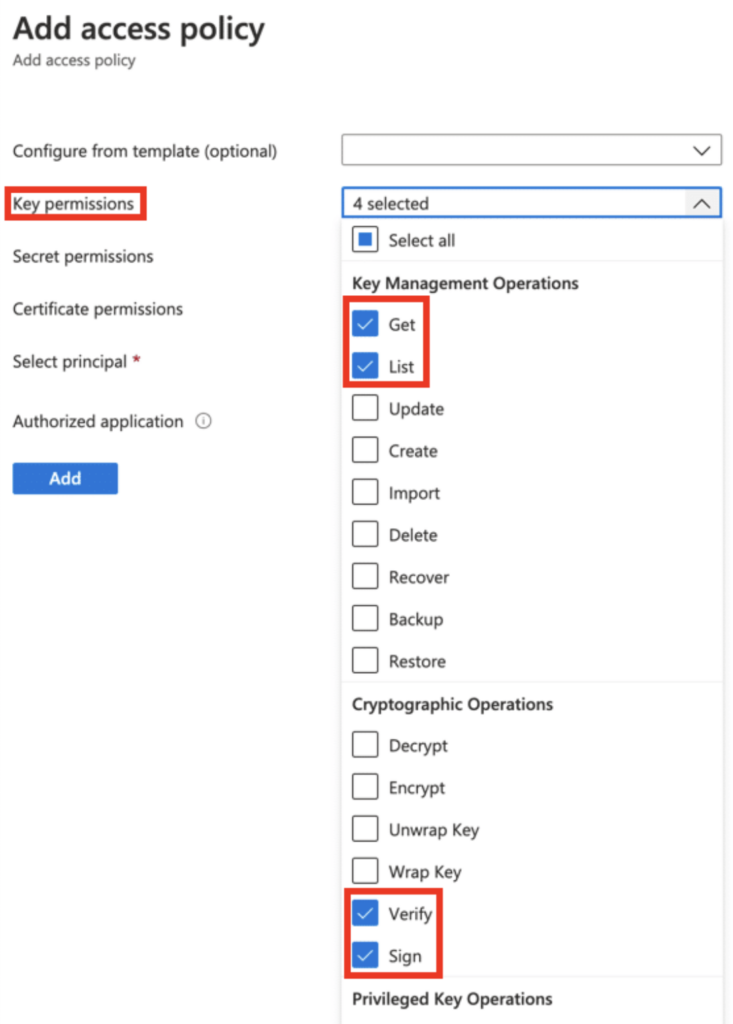
Under these sections, enable the following permissions:
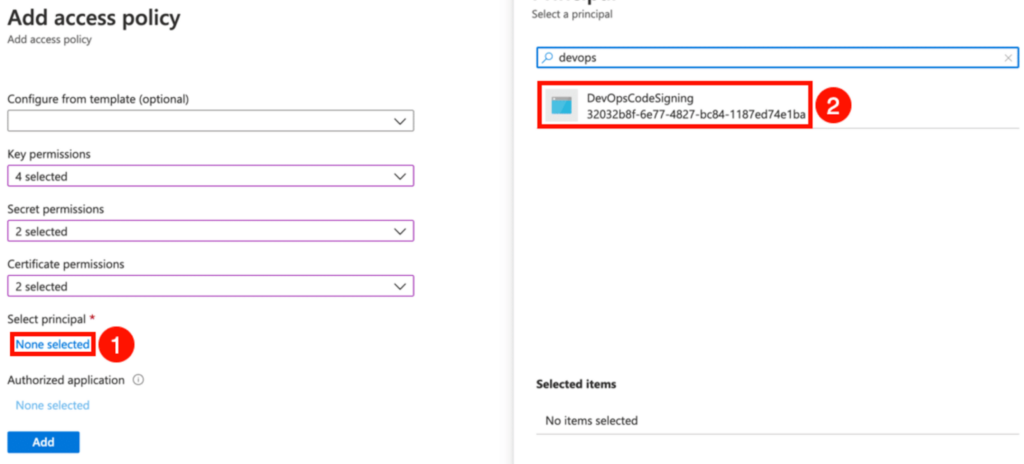
Under “Select principal”, find your registered application and add it. Click “Save”.
Add an Azure CLI task to your pipeline’s configuration file (usually a YAML file in Azure DevOps).
Here’s an example YAML configuration for a pipeline:
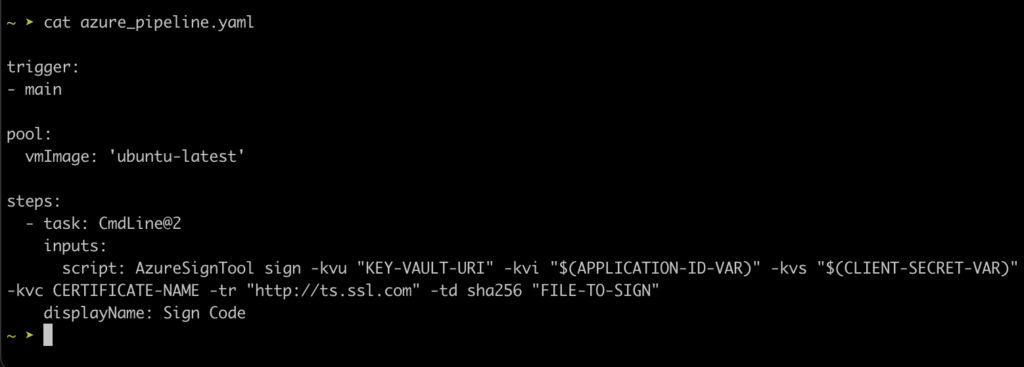
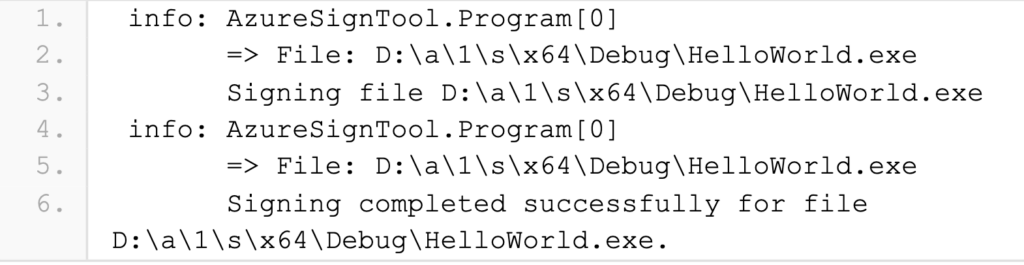
Run your pipeline. It will use the provided credentials to authenticate with Azure. Verify the output for any errors. Here is an example of successful Azure Code Signing.
Prioritize security throughout your Azure Code Signing implementation. Here are the top best practices and considerations.

Protecting your code with Azure Code Signing
Azure Code Signing is a powerful tool for ensuring code integrity, but it’s only one piece of the security puzzle. Prioritize robust key management within Azure Key Vault. Be prepared to revoke compromised certificates quickly, and choose Azure regions wisely for optimal signing performance.
Streamlining security into your development workflows is vital. Incorporate tools like Spectral directly into your CI/CD pipelines. With real-time alerts and comprehensive secret detection, Spectral offers a developer-friendly way to strengthen code security during the signing process.
Level up your security practices with a free Spectral account. Protect your code and streamline development with Spectral’s easy integration.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions