Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
95% of cloud security fails are due to internal slip-ups. One wrong password, one sloppy permission, and your sensitive data are out in the open.
Thankfully, AWS gives you tools to fight back. IAM lets you control who does what, down to the finest detail. And IAM PassRole? It prevents sneaky permission grabs that put your data at risk.

IAM PassRole is a permission within AWS Identity and Access Management (IAM) that allows IAM entities (users, groups, or roles) to delegate permissions to AWS services. It allows permissions by assigning an IAM role to an AWS resource or service. Doing so lets you precisely define the actions the resource or service can perform based on the permissions attached to the role.
While powerful, using IAM PassRole effectively requires careful attention. Mistakes can cause issues that are easily detected by API penetration tests.
Here are some common pitfalls:
Cloud risk management incorporates processes to identify and remediate these risks before they become incidents.
In simpler terms:
IAM PassRole is often used with AWS CloudFormation.
AWS CloudFormation lets you build your setup (servers, databases, etc.) using code called templates. Sometimes, these templates need permissions the user running them doesn’t have. This can cause the deployment to fail.
Attaching an IAM role using PassRole gives the permissions needed to do its job. Aligning with DevSecOps Maturity Model (DSOMM) best practices can streamline this process, improving efficiency and mitigating security vulnerabilities in your workflows.
Here’s an example.
Here is an IAM policy that grants IAM:PassRole permission.
{
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Action": [
"iam:GetRole",
"iam:PassRole"
],
"Resource": "arn:aws:iam::<account-id>:role/CloudFormationServiceRole"
}]
}
In this policy, specifying the exact role instead of using a wildcard (*) in the resource ARN is critical to prevent privilege escalation.
Messy IAM PassRole settings are an open invitation for trouble in your AWS setup. Attackers can sneak in and upgrade their permissions above what they should have. A breach could have widespread consequences if those permissions aren’t carefully restricted to specific AWS Regions or Availability Zones.
Mitigation Strategies
Here’s an example.
Your developer needs limited access to sending emails, right? Sloppy PassRole permissions could let attackers upgrade themselves to full AdministratorAccess on that EC2 instance.
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:RunInstances",
"iam:PassRole"
],
"Resource": [
"arn:aws:ec2:*:*:instance/*",
"arn:aws:iam::<account-id>:role/SESEmailSendingRole"
],
"Condition": {
"StringEquals": {
"iam:PassedToService": "ec2.amazonaws.com"
}
}
}
]
}
Creating and setting up IAM PassRole is straightforward. Here’s a detailed guide to help you through the process.
First, sign in to the AWS Management Console and navigate to the IAM service.
Select Roles on the left-hand side menu and click Create role.
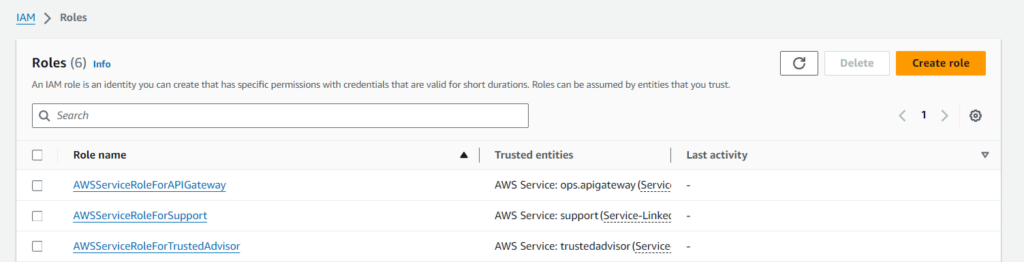
Select the service using this role (e.g., EC2) and click Next.
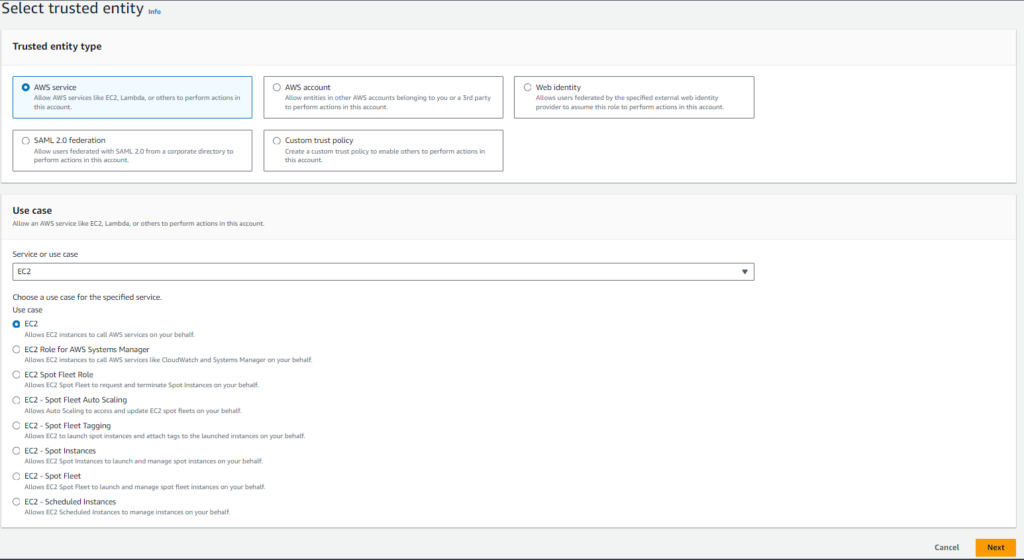
Search for and select the policies you want to attach to the role. Follow the principle of least privilege and attach only the permissions necessary for the role to function correctly. Once you’ve done this, click Next.
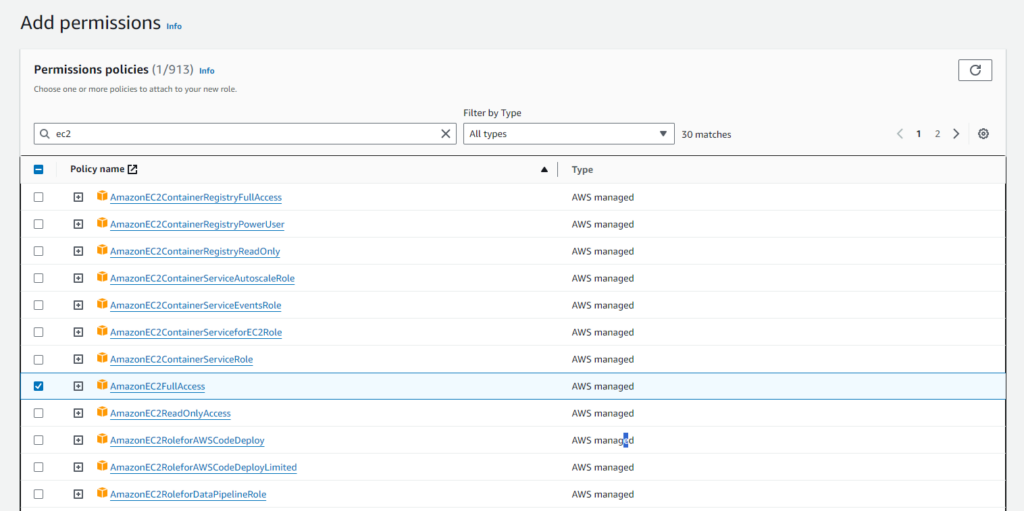
Review the role settings and permissions. If everything looks good, click Create role. You’ll then have created your role with the specified trust relationship and attached policies.
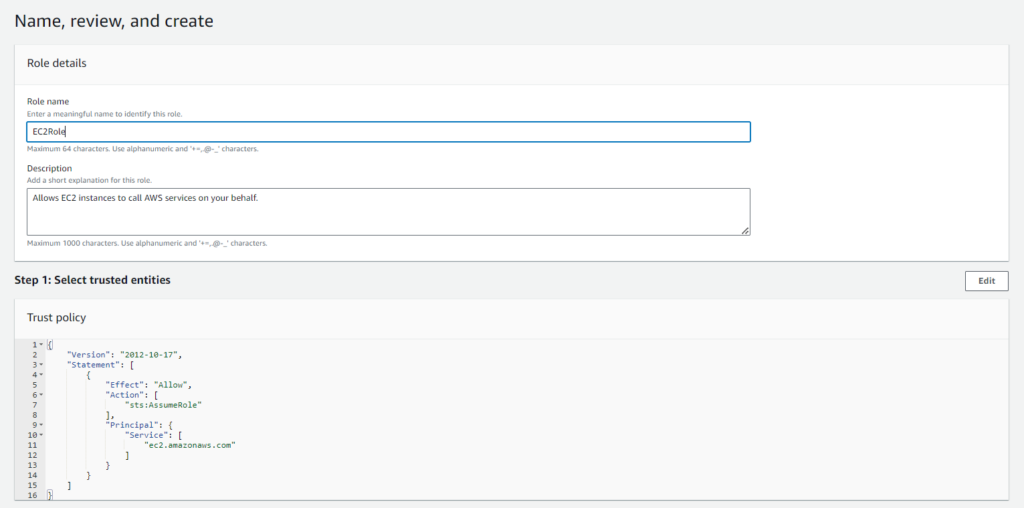
By default, AWS sets the trust relationship for you. However, if you need to modify it, go to the Trust relationships tab of your role, click Edit trust policy, and update the policy document accordingly.
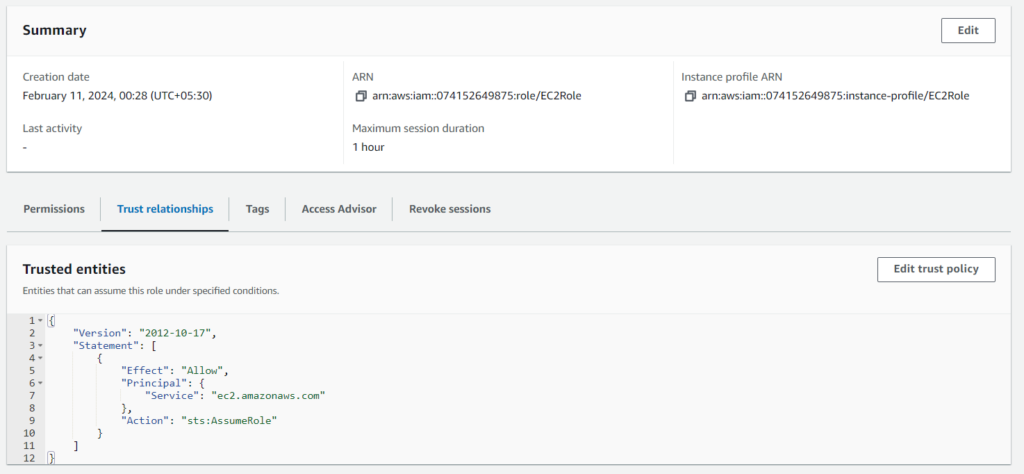
{
"Version": "2012-10-17",
"Statement": {
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
}
Select the Policies tab on the left-hand sidebar on the IAM dashboard and click the Create policy button.
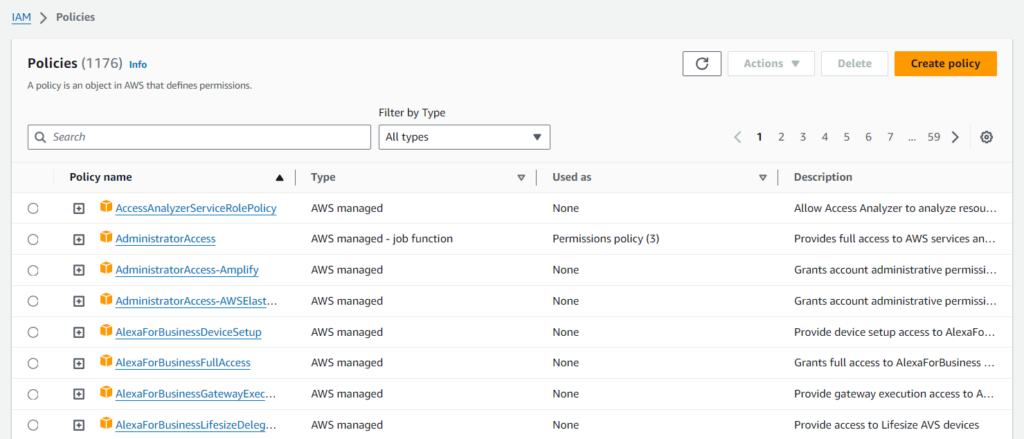
Go to the JSON tab. Enter the following policy (replace role-arn with the actual ARN of the role you created):
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "iam:PassRole",
"Resource": "arn:aws:iam::074152649875:role/EC2Role"
}
]
}
Review the policy settings, and if everything looks good, click Create policy.
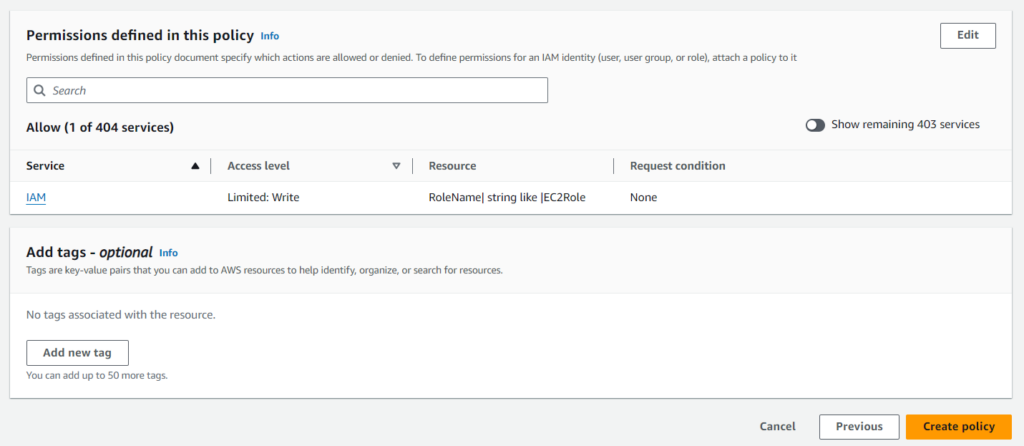
To attach the policy to an IAM user, click Users in the IAM dashboard and select the user who needs to pass the role.
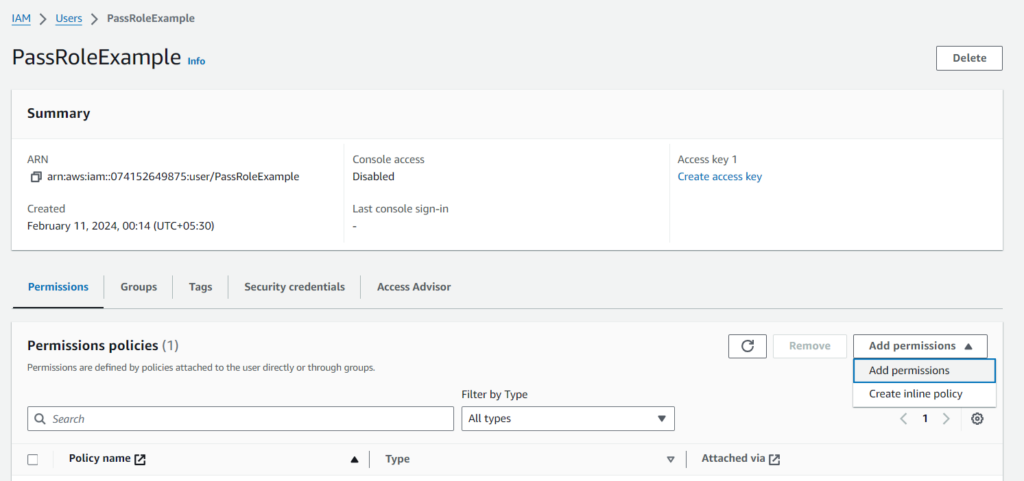
Click Add permissions and choose the Attach policies option. Then, search for your created policy and select it.
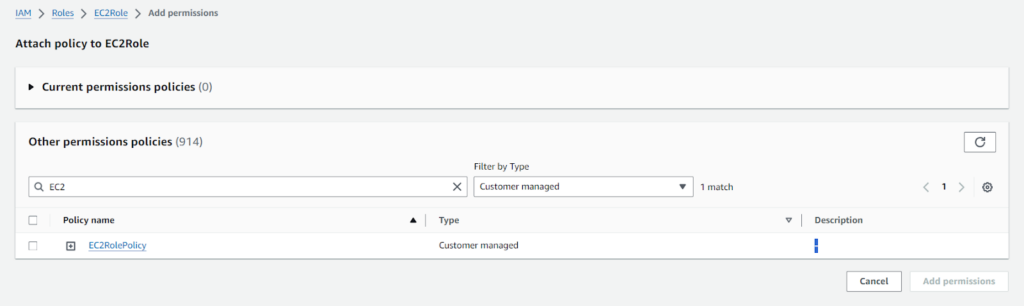
Finally, click the Add permission button to save the policy assignment.
How to test Role functionality:
SSH into the instance and use the AWS CLI to test assuming the role.
aws sts assume-role --role-arn <role-arn> --role-session-name TestSession
This command should return a JSON object with temporary security credentials (Access Key ID, Secret Access Key, Session Token).
How to validate Role Permissions:
Extract and export the temporary credentials from the JSON response. You can do this manually or by using command-line tools like jq. Set these credentials as environment variables:
export AWS_ACCESS_KEY_ID=<Temporary Access Key ID> export AWS_SECRET_ACCESS_KEY=<Temporary Secret Access Key> export AWS_SESSION_TOKEN=<Temporary Session Token>
Now, using these temporary credentials, test the permissions granted by the role. For instance, if the role is supposed to grant read-only access to S3, you can list the S3 buckets:
aws s3 ls
Monitoring and auditing PassRole activities are crucial for ensuring security compliance within AWS. Using tools like AWS CloudTrail, you can track API calls from IAM users, federated users, and AWS services. This log provides insights into who, when, and the permissions involved during each session.
AWS enables CloudTrail by default, but you can customize it with specific configurations.
Here’s an example AWS CLI command to create a new trail:
aws cloudtrail create-trail --name MyTrail --s3-bucket-name my-cloudtrail-logs
This command creates a trail named ‘MyTrail’ that stores logs in an S3 bucket my-cloudtrail-logs.
You can set up a CloudWatch alarm to monitor specific CloudTrail metrics. Here’s an example AWS CLI command to create an alarm:
aws cloudwatch put-metric-alarm --alarm-name "PassRoleActivityAlarm" --metric-name "EventCount" --namespace "CloudTrailMetrics" --statistic Sum --period 300 --threshold 1 --comparison-operator GreaterThanThreshold --evaluation-periods 1 --dimensions Name=EventName,Value=PassRole Name=ResourceType,Value=AWS::IAM::Role --alarm-actions arn:aws:sns:region:account-id:my-sns-topic
This command triggers an alarm if the ‘PassRole’ event occurs more than once in five minutes.
You can use AWS CLI commands to list policies and roles. For regular audits. Here’s an example to list all IAM policies:
aws iam list-policies --scope Local
And to list roles:
aws iam list-roles
Consider tools like Prowler and Cloud Custodian for an additional layer of scanning, particularly for vulnerabilities related to privilege escalation in AWS.
IAM PassRole lets you get super specific about permissions, which is fantastic for AWS security. But those settings can get messy. And as your cloud setup gets bigger, it’s too easy to miss those little permission slip-ups that attackers love.
Spectral makes this process dramatically easier. The platform continuously scans your environment using advanced automation, flagging potential issues like overly broad PassRole permissions and many other configuration risks. Simplify your cloud security with Spectral. Get started in minutes.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions