Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
No single organization can master all trades, which is why their success hinges heavily on their vendors. And if vendors are crucial for your business operations, it’s necessary to manage them as if your success depended on it–because it does. Yet, until recently (2016), only a third of companies knew how many vendors accessed their systems each week.
Awareness of this topic is increasing, but so is the number of partners, vendors, contractors, and temporary workers who require access to companies’ networks. Poorly securing their access has resulted in horror stories you’ve probably heard, from Target’s leak of 40 million customer credit and debit cards, to Home Depot’s data breach resulting in 56 million stolen payment accounts.
More recently, a lawsuit was filed against the Pennsylvania Department of Health due to a data breach that impacted at least 72,000 patient records–all because their contact-tracing vendor used an unapproved collaboration platform. Why do similar things keep happening? Are companies placing too much trust in the vendors they work with? And if so, what can they do about it?
There’s a growing realization that decisions need to be based on more than blind faith in third-party services, which is where vendor risk management (VRM) comes in. It ensures that using third-party services doesn’t create an unacceptable potential for business disruption or a negative impact on your performance.
In this blog, we look at what VRM means in practice and what tools can help you put robust controls and checks in place to mitigate the security risk of vendors.
With vendors central to your organisation’s functioning, you must implement best practices to quickly identify and fix risks that arise due to your association with them. VRM requires evaluating the level of access you need to give a vendor to your sensitive information or your system. This way, you can secure your business from third-party vulnerabilities that can lead to serious legal, financial, and reputational ramifications.
The truth of the modern business ecosystem is that it is necessary to outsource some parts of your business to take advantage of niche expertise. However, this exposes your business information to security challenges. Your vendor can be a massive liability if you don’t set up a solid VRM program.
A VRM program is a documented set of principles of engagement between your organization and a vendor that primarily features access and service levels expected. It helps you contract new vendors securely and confidently. A VRM program includes the below-listed steps:
But there’s more to consider: With businesses moving towards cloud computing, cloud data has become increasingly vulnerable and risks are shifting towards cloud-based and code-based vulnerabilities. About 79% of organizations have experienced at least one cloud data breach in the last 18 months. Some of the common vulnerabilities and exposures (CVE) take various forms, including remote code execution flaws and privilege escalation such as ProxyLogon, Log4Shell, PetitPotam, and VMware vSphere, among others.
As risks shift, businesses move to the cloud, and attackers follow them on their heels, organizations must use vendor risk management software to manage these challenges and protect the SDLC. The list below features solutions focused on this modern risk landscape.

Although not exclusively focused on VRM Polar Security addresses some of the issues mentioned in this blog by mapping data flows to flag security and compliance risks. It prevents exposed data risks associated with unknown shadow data stores with public access and highlights the vulnerabilities and compliance violations within your system.
Polar’s vision is to secure data distributed across multiple cloud environments and transferred between workloads.
Pros
Cons
You can book a demo here.
A user says: In only a few minutes, we were able to deploy Polar and gain immediate insights about our shadow data.
SpectralOps is a developer-centric platform that identifies and manages potential mistakes such as security errors in code, misconfigurations, shadow assets exposed in public-facing repositories, and more. Its AI-powered scanning engine has more than 2000 detectors to uncover organizational blindspots, help developers to keep secrets secret, and support best practices such as secrets sprawl prevention by restricting API access to a minimal scope of daily operations to reduce the risk of exposure in case of secrets leaking.
Spectral empowers developers to release software quickly and with full confidence, while the tool monitors and protects your code and infrastructure from exposed API keys and security misconfigurations in real-time.
Pros
Cons
Visit this page to learn more about SpectralOps.
A user says: Spectral is easy to set up and use and provides valuable insights into sensitive issues.
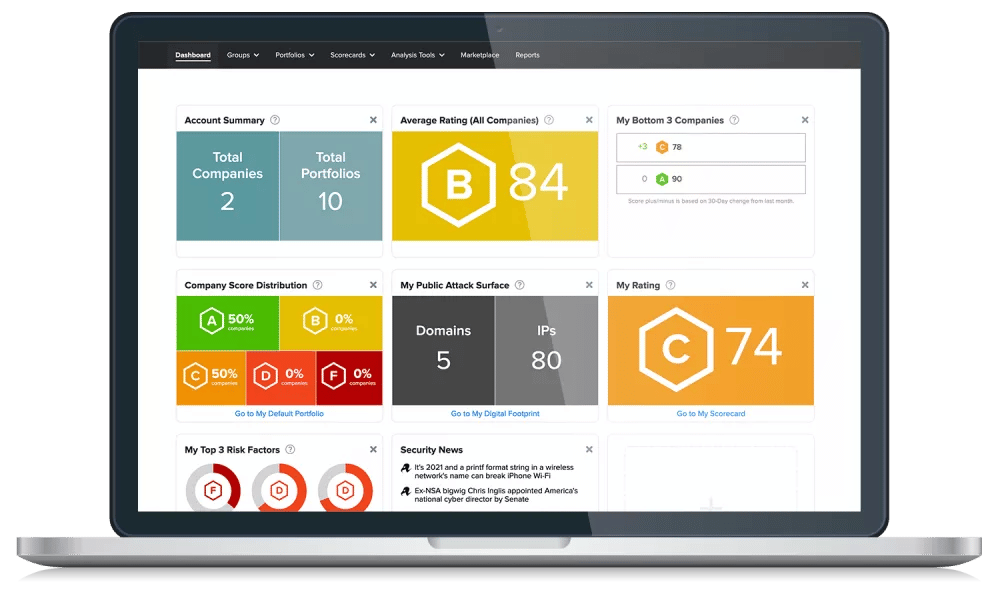
SecurityScorecard enables data-driven monitoring to help you gain a comprehensive view of your cybersecurity landscape. It uses a vast network of sensors to collect details related to your digital assets, such as IPs and domains, to identify vulnerabilities and other security threats.
SecurityScorecard is a highly-rated cybersecurity organization that continuously monitors your cybersecurity posture using commercial and open-source data points.
Pros
Cons
Demos can be requested here.
A user says: The overall platform is nice, but it is their way or nothing.
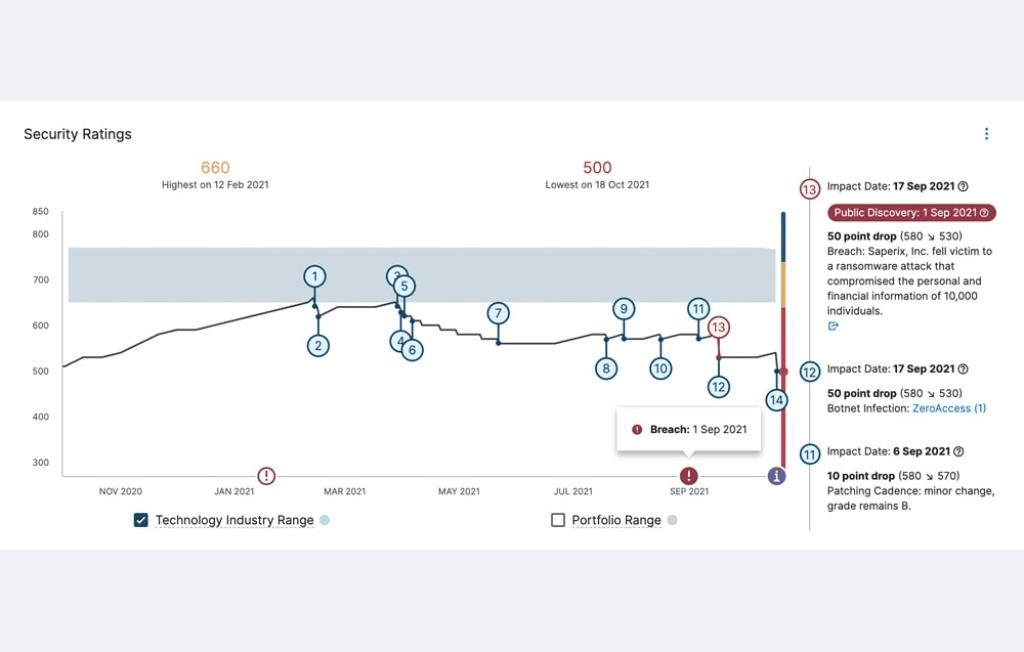
The BitSight Security Rating tool uses advanced algorithms to assign daily security ratings and aggregate risks to to third-parties, helping companies manage their risks.
BitSight is a global security standard that thousands of businesses and government agencies turn to for robust cybersecurity.
Pros
Cons
Free security rating and customized report available here.
A user says: BitSight conducts all of the legwork for me and then compiles the results into a risk score.
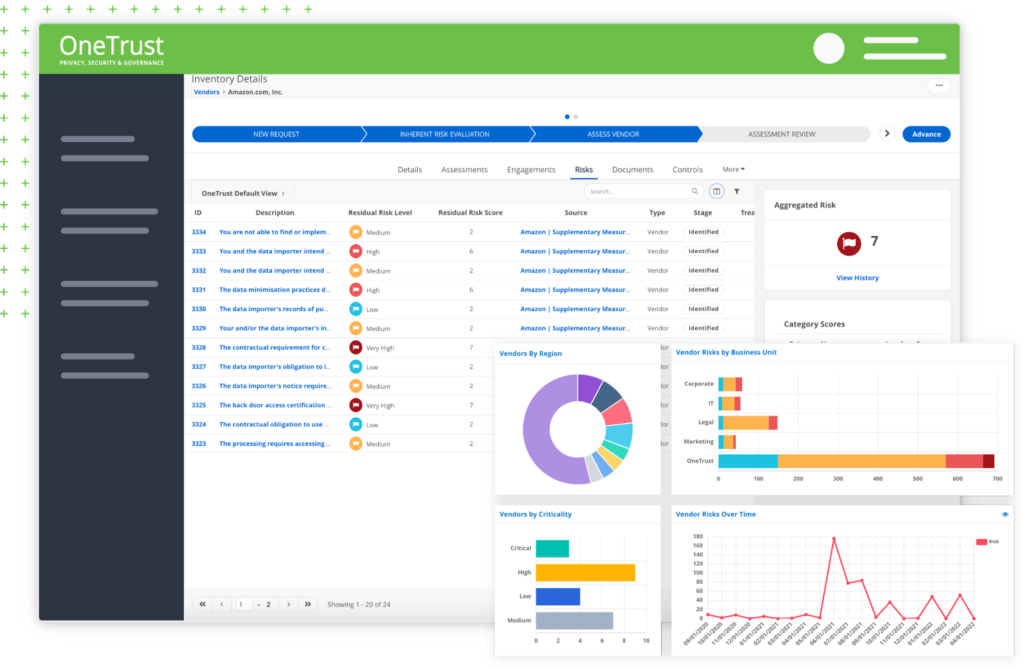
OneTrust‘s Third-Party Risk Management tool helps organizations to build strong cybersecurity posters by identifying, monitoring, and fixing risks at the enterprise level. It allows users to conduct vendor screening and compliance checks to reduce third-party risks through automated workflows.
Coming from well-known cybersecurity company OneTrust, this tool aims to help users build a trusted relationship with vendors by streamlining the end-to-end vendor management while maintaining oversight across the pipeline.
Pros
Cons
Where
1-to-1 demos with tailored advice for your team’s needs can be requested here.
A user says: Using Onetrust has been a good experience. The technical support is ok.
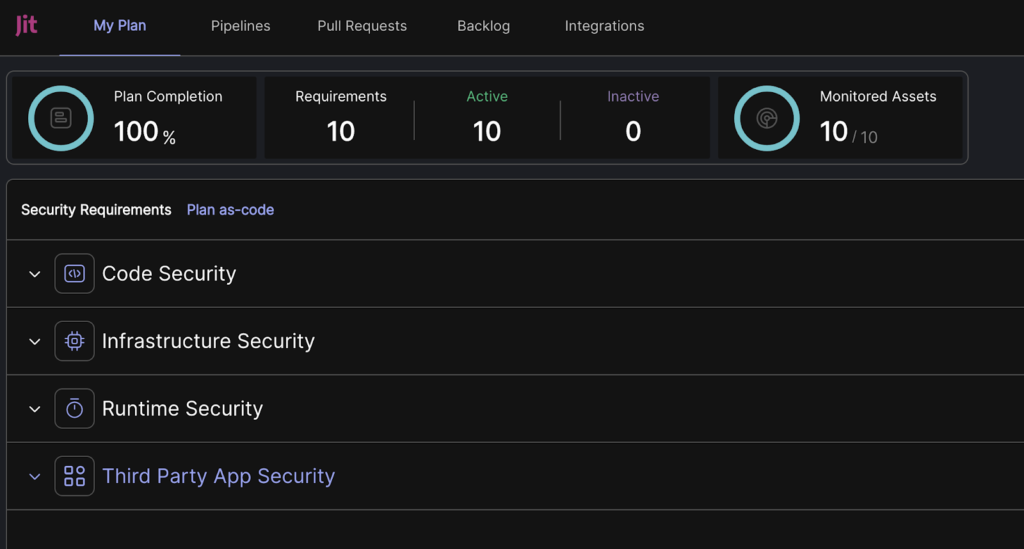
Jit automates product security for busy developers. It provides a continuous security platform that allows developers to focus on building quality software without diverting their focus on securing their cloud apps. Jit works on the concept of MVS (Minimum Viable Security), a declarative security approach that involves standardizing tools, frameworks, and processes across the development pipeline.
Jit offers a unified GitHub developer experience to empower developers to approach product security confidently.
Pros
Cons
Read the publicly-available Jit documentation to learn more about the platform.
A user says: Jit makes it simple to embed security controls across the DevOps workflow.
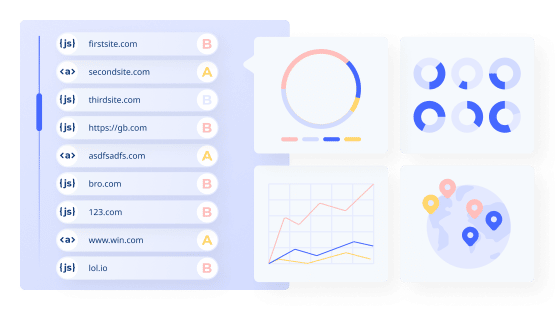
Reflectiz uses behavioral analysis to monitor network activities such as incoming requests from third-party vendors on users’ websites. The highlightings potential compliance issues and vulnerabilities originating from the client side to protect businesses from risks outside of their traditional security perimeter.
Who
The team behind Reflectiz is passionate about ethical hacking, and on a mission to help eCommerce and Financial Services companies to conduct business online while staying compliant with regional and industry regulations and preventing cyber-attacks.
Pros
Cons
Where
Try out the solution for free here.
A user says: It gives us more visibility into secrets in our code and helps to create awareness of security.
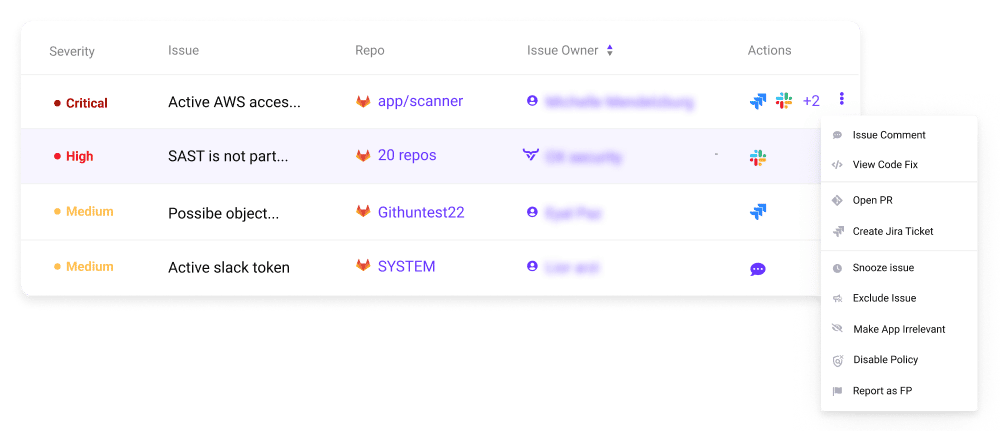
OX Security is a DevSecOps solution that automates cybersecurity monitoring across the software supply chain, enabling users to manage the security of every workload from a single platform.
OX focuses on reducing manual work for users, making it easier for them to secure CI/CD pipelines and mitigate supply chain risks like Solarwinds and Log4j.
Pros
Cons
New users can create a login to start using OX Security for free or book a demo first here.
A user says: OX gives a complete and reliable snapshot of code security before deployment.

IoT devices are a gateway for new forms of cyber attack against increasingly critical services. That’s why FirstPoint focuses on risks introduced by low-band IoT solutions. It enables IoT connectivity and security management, giving organizations complete control of the security of their IoT devices through capabilities like customized policies and rules.
FirstPoint is a niche cellular cybersecurity platform that protects cellular-IoT devices connected through SIM/eSIM from cellular network threats.
Pros
Cons
Request a demo here.
A user says: FirstPoint’s solution works to guard devices on private and public networks against security threats.
Undisputedly, vendors are one of the core tenets of a scaling organization. However, that shouldn’t make it a weak link in your cybersecurity approach. With a growing emphasis on protecting sensitive data, relaxing against security gaps could prove detrimental to your business. As an organization, you must offer your team the necessary tools for shipping the highest quality software by automating vendor risk management. With this exhaustive list of platforms to pick from, we hope you find the ones that can best address your needs to move forward with confidence.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Part of the Spectral API Security Series Yelp.com is one of the most influential crowdsourcing sites for businesses. The company is worth just over one billion