Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
What happens when devices meant to make your life easier become tools for intrusion? Your smart TV could become a surveillance device, your fitness tracker could leak your health data, and your connected car could be remotely hijacked. In the world of IoT vulnerabilities, the technology designed to serve you could turn against you.
The Internet of Things promises convenience and connectivity. The risks of cyberattacks targeting these devices are growing exponentially. The first half of 2023 threw a curveball with a jaw-dropping 400% spike in malware attacks targeting IoT devices.
IoT protocols are standardized languages facilitating communication among IoT devices, servers, and cloud platforms. They are the backbone for seamless interactions within the Internet of Things ecosystem. Similar to how web protocols like HTTP enable data exchange on the Internet, IoT protocols offer these Internet-connected devices a way to communicate efficiently.
IoT protocols are uniquely designed to address the challenges posed by IoT environments, which are markedly different from standard computing environments. IoT devices usually operate under constraints like low power availability and limited processing capabilities.
Besides MQTT, other standard protocols IoT devices use include CoAP, HTTP, AMQP, Zigbee, Z-Wave, and Thread. Don’t worry if these acronyms seem like a bunch of alphabet soup right now—we’re about to examine these protocols and the vulnerabilities associated with each one.
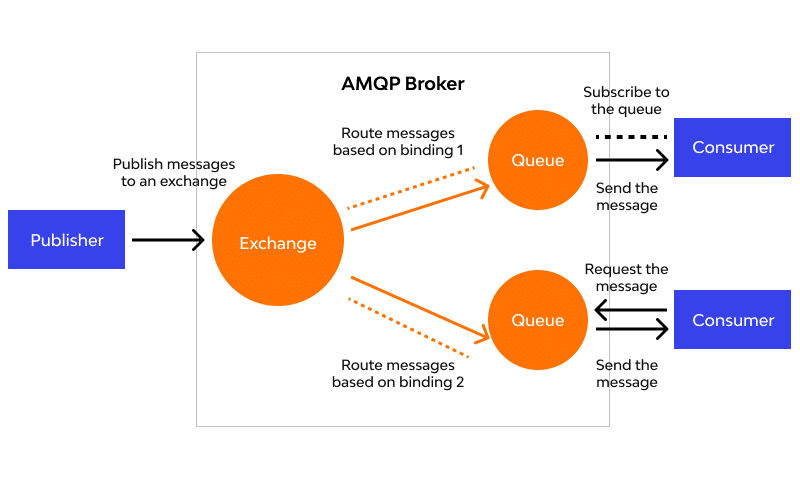
MQTT, or Message Queuing Telemetry Transport, is a protocol engineered to efficiently exchange messages in IoT environments, operating on a publisher/subscriber model. Devices publish messages to a central broker, which then distributes these messages to subscribers based on topic subscriptions rather than establishing direct connections between devices. This model significantly reduces bandwidth usage and power consumption.
Despite its strengths, MQTT vulnerabilities include:
It’s easy to forget that MQTT sometimes requires encryption, leaving sensitive data vulnerable. Always use TLS (Transport Layer Security) to protect data in motion, and adopt broader SaaS security best practices whenever your IoT devices interact with cloud-based components. Potential misconfigurations can be overlooked, or sensitive MQTT channels can be accidentally left unencrypted. MQTT’s capability to carry sensitive data necessitates encryption to shield it while in transit. The protocol, however, doesn’t inherently require encryption, posing a severe risk if it still needs to be implemented.
Employing TLS (Transport Layer Security) is non-negotiable. TLS encrypts data transmitted over MQTT, providing a secure channel that prevents eavesdropping.
Attackers may gain access to topics they shouldn’t, either by subscribing to them or publishing malicious messages.
Implementing stringent authentication and authorization processes is critical to ensuring that only authorized users can access or publish specific topics, safeguarding the network against unauthorized entry. Rigorous access controls prevent unauthorized users from subscribing to sensitive topics, helping to safeguard your data.
MQTT is vulnerable to DoS attacks, in which attackers overwhelm the broker with messages or subscriptions, disrupting service for legitimate users. Regular testing and monitoring can help you spot unusual activity that might signal an attack, allowing you to take proactive measures.
Applying DoS attack prevention techniques, such as rate limiting to control the flow of messages and anomaly detection to identify and mitigate unusual activity, can help maintain service stability and availability.
The Constrained Application Protocol (CoAP) is designed with a RESTful architecture, making it a preferred choice for simplified interaction between IoT devices in low-power and constrained environments. It operates over UDP (User Datagram Protocol), offering lower overhead than TCP. This design is particularly beneficial for applications such as in smart city infrastructures, environmental monitoring, and energy management systems.
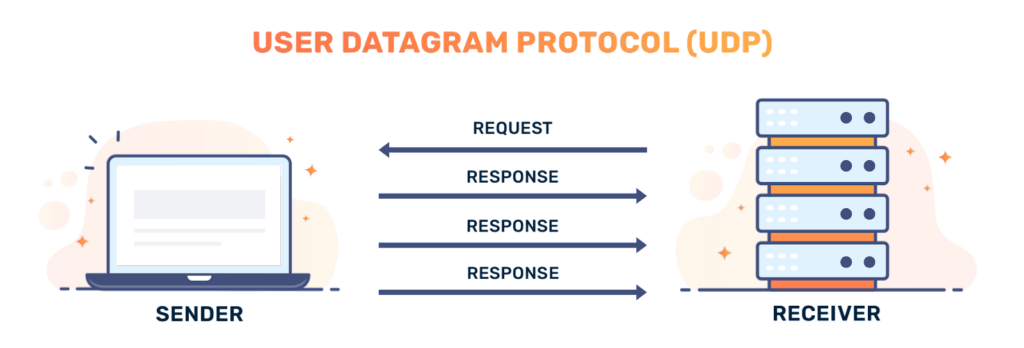
However, CoAP’s reliance on UDP and its operation in constrained environments introduces notable security challenges. The protocol is vulnerable to Man-in-the-Middle (MitM) attacks, where attackers can intercept or alter messages between devices. Using UDP also increases the risk of replay attacks, where attackers resend valid data packets to disrupt operations or gain unauthorized access.
To counter these security risks, implementing Datagram Transport Layer Security (DTLS) is recommended where feasible. For a structured approach to integrating security throughout your IoT development process, consider a framework like the DevSecOps Maturity Model (DSOMM). DTLS provides an encryption layer over UDP, securing the data in transit against eavesdropping and tampering. Secure key exchange mechanisms can guarantee that only authorized devices can establish communication, mitigating the risk of MitM attacks. Using timestamps or nonces can help defend against replay attacks by making each message unique.
HTTP, or HyperText Transfer Protocol, is ubiquitous and adaptable, making it a familiar choice for IoT applications due to its widespread use and support across web technologies. Yet, this adaptability has its challenges, especially considering the extra burden it places on IoT devices that often operate with limited juice. Automating your DevOps processes can ease the strain on these devices and streamline the deployment of essential security updates. The verbose nature of HTTP, with its heavy text-based headers, doesn’t do favors for low-power IoT gadgets, eating into their efficiency. Even turning to HTTPS for encrypting data, though vital, becomes a tough challenge for devices strapped for processing power.
In the IoT context, HTTP inherits web vulnerabilities such as Cross-Site Scripting (XSS) and SQL injection, which can lead to unauthorized access and data manipulation. The best option? Thorough input checks are required to fend off XSS and SQL injections, leaning on HTTPS for encryption whenever feasible and considering lighter, more energy-efficient alternatives like MQTT or CoAP as required. It’s crucial to sanitize all inputs and be aware of common web vulnerabilities that can be exploited in IoT devices.
AMQP stands for Advanced Message Queuing Protocol. This protocol emphasizes reliable message delivery and sophisticated queuing mechanisms, making it an excellent fit for complex IoT systems that require robust communication between many devices and services. Its design supports a variety of messaging patterns, including request/response and publish/subscribe.
However, the complexity that makes AMQP powerful also expands its attack surface. The protocol’s rich feature set can introduce security vulnerabilities if not properly managed, emphasizing the critical need for adherence to security best practices.
Central to securing AMQP communications is the deployment of TLS (Transport Layer Security), which ensures that data zipping through the network remains encrypted and out of reach from prying eyes. Establishing strict access controls, limiting system interactions to verified entities, and conducting regular security reviews of your AMQP setup are also crucial. Employing a robust threat intelligence lifecycle will further enhance your ability to identify and respond to potential threats proactively.
Thanks to their mesh networking capabilities, Zigbee, Z-Wave, and Thread are at the heart of the smart home and sensor network revolution. These protocols let devices chat directly or through others in the network, allowing messages to span large areas—perfect for everything from intelligent lighting to security systems across extensive IoT ecosystems.
However, their security vulnerabilities will likely grow as these protocols gain popularity. Issues could range from the dangers of not pairing devices securely to specific weaknesses within each protocol that might open the door to unauthorized snooping or access. It’s crucial to stay updated on common vulnerabilities, such as those outlined in the OWASP to defend against them effectively.
Protecting your IoT ecosystem extends to the data it generates. A comprehensive data security policy is essential for ensuring data integrity, confidentiality, and responsible use. By safeguarding sensitive information and ensuring its responsible use, you can mitigate the risk of data breaches.
In the world of IoT, it’s becoming increasingly clear that security needs to be a part of the development conversation from the get-go, not just a checkbox at the end. This is where the concept of “shifting security left” comes into play, urging the integration of security practices early in the development cycle. Develop a secure-by-design mindset within your team, where security is a foundational element of your IoT applications and devices. Implement regular vulnerability scans and go beyond with automated code and asset scanning that integrates seamlessly into your development workflow. This empowers you to find and fix issues early.
As your IoT projects grow in complexity, it becomes increasingly difficult to track every potential vulnerability, misconfiguration, and exposed secret, such as API keys or other sensitive credentials. Automated tools and robust data monitoring solutions can help streamline this process, providing deeper insights into device behavior and facilitating swift anomaly detection.
As IoT devices increasingly leverage the power of generative AI models, establishing specific security standards for these components becomes essential.
It’s a clear sign that as IoT networks grow, they’re also getting more attention from the wrong crowd. It’s time to take steps to stay ahead of the risks. With specialized security scanning tools, you can uncover blindspots and potential leaks in your codebase, configuration files, and even public assets. While protocols like MQTT, CoAP, and HTTP provide an efficient way for IoT devices to communicate, each brings a unique set of security considerations—which is highly under-focused at this time.
Proactive security testing and continuous monitoring can help you stay ahead of emerging threats and identify potential weak spots.
Don’t let your smart devices become security liabilities. Proactive protection is key. Spectral makes integrating robust security practices into your IoT development workflow easy. Try our free account today and start safeguarding your devices from the ground up.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions