Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
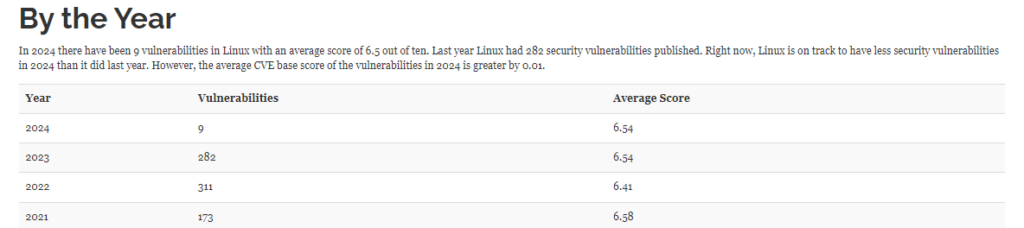
As you step into 2024, do you have absolute confidence in the security of your Linux systems? The stakes have never been higher, and the risk landscape for Linux is constantly shifting – which presents an ongoing challenge to your system’s security.
In 2023 alone, 282 Linux-specific vulnerabilities were added to the Known Exploited Vulnerabilities (KEV) Catalog by CISA. Employing an advanced vulnerability scanner is the next step to protecting your systems from these and other potential risks.
Vulnerability scanners are sophisticated tools that methodically identify and evaluate potential security vulnerabilities in your systems and networks. They not only scan but also provide key insights for remediation.
More specifically, vulnerability scanners designed to work with Linux environments – are adept at navigating the open-source nature of the platform. Such scanners are indispensable, given Linux’s extensive use in enterprise networks and critical infrastructure.

Vulnerability scanners offer a suite of functionalities and features that bolster the defense mechanisms of Linux systems:
With real-time monitoring (RTM) and advanced Intrusion Detection Systems (IDS), you can continuously scrutinize network traffic and system activities. This means quickly detecting anomalies like unusual outbound traffic or unauthorized access attempts, critical in environments like banking systems or healthcare IT.

When vulnerabilities are detected, the capacity to automatically trigger patching sequences is a game-changer. This automation swiftly applies necessary fixes, easing the burden on your IT teams and keeping system maintenance smooth and up-to-date.
Due to the uniqueness of each Linux environment, the best vulnerability scanners provide a suite of customization options. Customization can range from setting specific scanning parameters, like depth and frequency, to choosing focus areas based on the organization’s infrastructure.
Other benefits include
Lynis is a sophisticated and nimble host-based vulnerability scanner for Linux and UNIX systems.
Medium to large enterprises focused on compliance testing and security auditing.
Lynis is available in a free version and an enterprise version. Contact Cisofy for pricing details for Lynis Enterprise.

SpectralOps stands out as a specialized security solution – uniquely designed to address the critical risks of secrets leakage and weak credentials management in Linux systems. Its focused approach targets the vulnerabilities often overlooked by traditional scanners, adding an essential layer of security specifically tailored to safeguard code integrity.
Software development companies and IT service providers handling sensitive data and looking to improve code security.
Contact SpectralOps for pricing details.
“Spectral has automatically identified and surfaced security flaws that our company was not aware of, it helped us be more secure and helped us avoid operational risks.”
Chkrootkit is a specialized, open-source tool tailored for Linux systems, designed to detect and identify hidden rootkits and backdoors.
Small to medium-sized businesses and IT professionals in sectors like web hosting, e-commerce, and data services.
Chkrootkit is freely available to all users.
Chkrootkit is an excellent choice for those seeking a dedicated tool to enhance their Linux system’s security. Its combination of extensive rootkit detection, integrity checks, and accessibility makes it a top recommendation for businesses looking to bolster their cybersecurity defenses.
Rootkit Hunter, a command-line utility, specializes in detecting rootkits, backdoors, and analogous security threats within Linux environments. Although it shares a common objective with Chkrootkit, Rootkit Hunter sets itself apart through its distinct scanning methodologies and user interface.
Well-suited for cybersecurity teams and system administrators within small to medium-sized companies, who prefer a command-line interface.
Rootkit Hunter is a free tool.
“Open source scanner for every kind of bad things happening in your system: backdoors, rootkits, local exploits, … Simple to use, thorough in its inspection, should be an everyday piece of work in your normal schedule.”

ClamAV stands as a flexible and open-source antivirus solution known for its proactive approach to detecting viruses, trojans, and an array of malware threats on Linux systems.
Educational institutions, non-profit organizations, and small to medium-sized businesses seeking a cost-effective antivirus solution.
ClamAV is a free, open-source tool.
ClamAV is a commendable choice for those in need of an effective, versatile antivirus solution for Linux systems. Its combination of broad file format support, advanced detection routines, and cost-effectiveness makes it an attractive option for educational institutions, non-profits, and small to medium-sized businesses.
This free and open-source malware scanner harnesses threat intelligence derived from network edge intrusion detection systems, endowing it with remarkable efficacy in pinpointing and mitigating malware threats.
Web hosting providers, digital agencies, as well as the retail or finance industries.
LMD can be downloaded and used without any cost.
Its integration with network edge intrusion detection systems, combined with advanced signature techniques, provides a robust defense mechanism.
Maltrail is a prominent free and open-source network security tool specifically designed to detect malicious traffic. With its real-time alerts and detailed insights, Maltrail equips Linux administrators to stay vigilant and respond swiftly to potential threats within their network environments.
Telecommunications, cybersecurity, and large-scale enterprise IT, where monitoring and securing network traffic is a top priority.
Maltrail is available free of charge.
Maltrail is an excellent choice for Linux administrators and IT professionals looking for a reliable and comprehensive network security solution. Its capability to detect a wide range of malicious traffic, combined with its flexible deployment options, makes it a versatile and powerful tool in safeguarding network environments.
OpenVAS, under the umbrella of Greenbone Vulnerability Management, is a comprehensive open-source solution for vulnerability scanning and management with over 100,000 tests.
Large enterprises, government organizations, and cybersecurity firms/managed security service providers that offer detailed security assessments and compliance audits.
OpenVAS is available to download for free.
“We struggled with protecting ourselves, but Greenbone helped us think like an attacker, which made us smarter. Sort of like when police hire a profiler to get in the mind of a killer to better understand where/when he might strike again.”
Nessus, a proprietary tool, is highly regarded in the field of vulnerability scanning. With an extensive library of plugins, it’s a top choice for conducting scans and compliance checks within Linux environments.
Medium to large-scale enterprises in sectors like finance, healthcare, and technology.
Contact Nessus for pricing details.
“Nessus is the state of the art on automating vulnerability scans for networks and infrastructure. It has lots of customization options and can be deployed locally to make an active scan on the internal infra or through the cloud.”
Nikto is an open-source tool that specializes in scanning web servers – focusing on detecting outdated software and hazardous files in web servers.
Digital marketing agencies, e-commerce businesses, and web development firms where maintaining secure and robust web server environments is critical.
Nikto is available free of charge.
Its focus on scanning for outdated software and hazardous files, combined with its comprehensive approach to testing, makes it a valuable asset in the arsenal of web security tools.
Navigating the complex world of Linux security can be daunting. At Spectral, your security is our top priority. We’re committed to providing you with the tools and expertise needed to keep your Linux systems safe. Don’t wait for vulnerabilities to strike.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions