Top 12 Open Source Code Security Tools
Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open
As a developer or member of a DevOps team, you probably know the stress and satisfaction of pouring your heart and soul into developing a groundbreaking cloud-native application. But without proper protection, your hard work could be compromised in seconds. That’s where CNAPP comes in, revolutionizing how we can ensure the security of our applications.
As the world increasingly relies on cloud-native technologies and microservices, up to 45% of breaches are cloud-based. CNAPPs are designed to help address this with a comprehensive platform for securing cloud-native applications. CNAPPs simplify application protection at every stage of their lifecycle from a wide range of threats and inbuilt vulnerabilities, including malware, DDoS attacks, cloud misconfigurations, and data breaches. Let’s take a closer look at how this works.
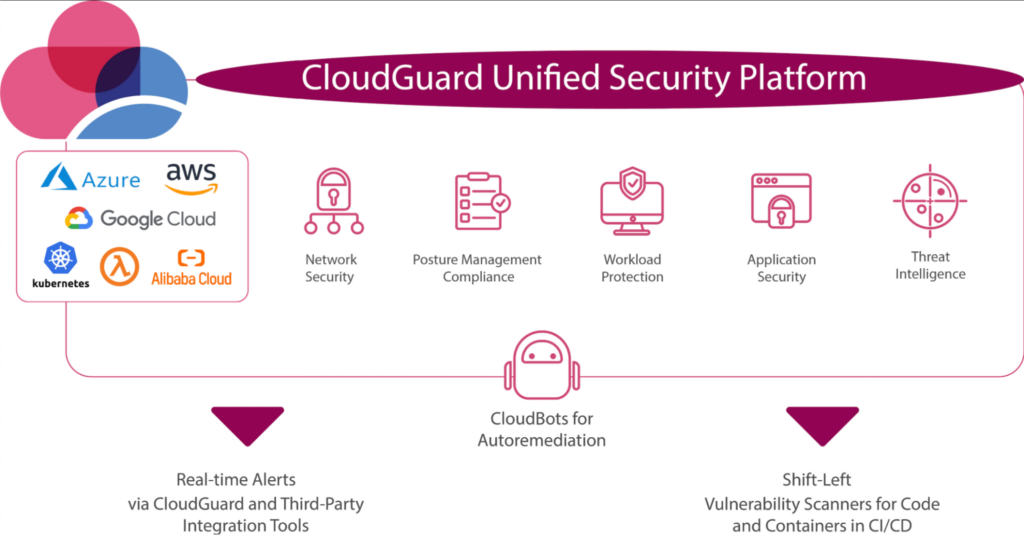
CNAPP (cloud-native application protection platform) streamlines the process of monitoring, identifying, and responding to possible security threats and vulnerabilities in the cloud. It is designed to work seamlessly with container orchestration platforms like Kubernetes and provides a range of security features, including vulnerability management, intrusion detection, and application layer security.
At its core, CNAPP is all about providing comprehensive security coverage for cloud-native applications. It addresses many challenges developers face when working with these technologies, including visibility, scalability, and flexibility.
When selecting a CNAPP solution, it’s important to look for the following:
Core capabilities:
Recommended capabilities:
Optional capabilities:
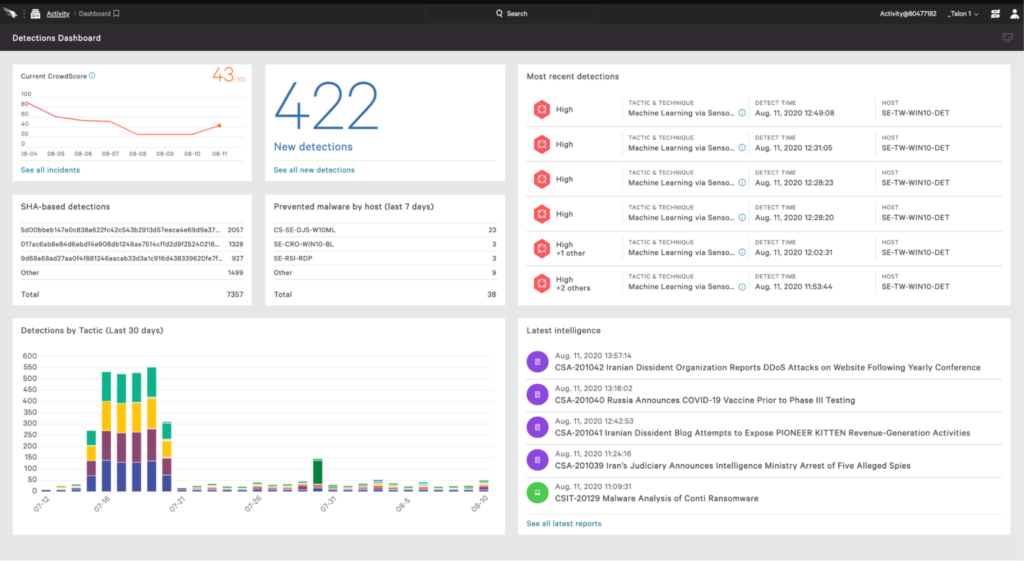
Price: Annual plans start at $299.95 for a minimum of five devices.
Main Features:
Best for: Mid-size to enterprise corporations looking for a comprehensive, cloud-native solution.
Review: “Crowdstrike Cloud Security has enabled more profound insights and visibility into processes running within our cloud infrastructure.”
Price: Contact the company for a quote.
Main Features:
Best for: Large organizations seeking an advanced threat prevention solution to prevent sophisticated threats and assist with compliance.
Review: “It has several very useful report types; the features of each are very good, and any of the compliance team can view/generate a report.”
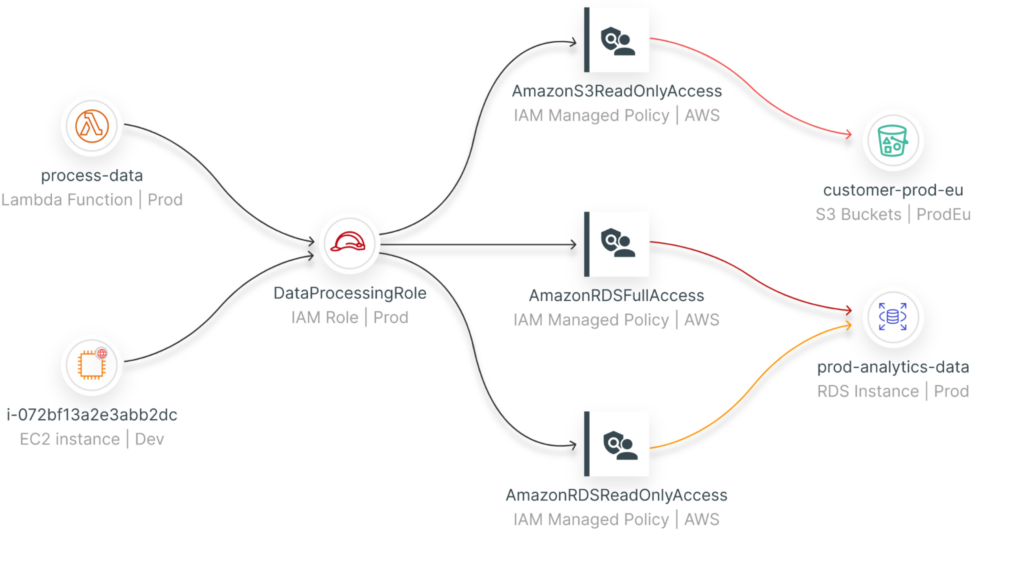
Price: Contact the company for a quote.
Main Features:
Best for: Mid-market to enterprise-level organizations that want to improve their cloud security policies
Review: “With Ermetic, auditing our AWS environment has become much easier. We can see exactly what entities have excessive privileges and where they come from.”
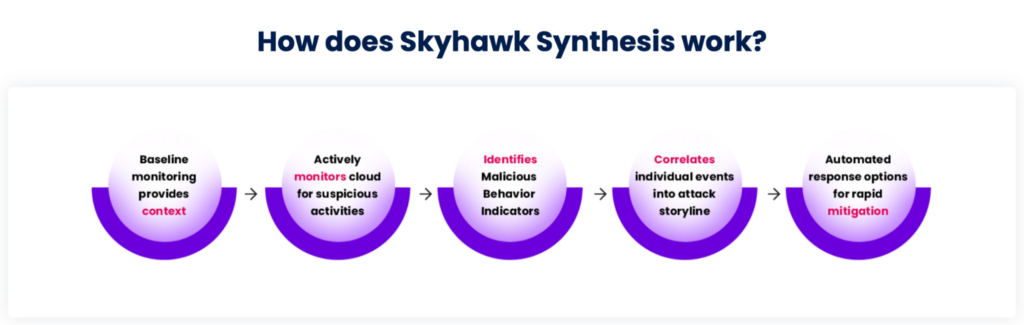
Price: Free demo available.
Main Features:
Best for: Established, fully cloud-based companies that struggle with alert fatigue
Review: “Excellent service, training, and technical support. The integration is very easy with zero unavailability.”
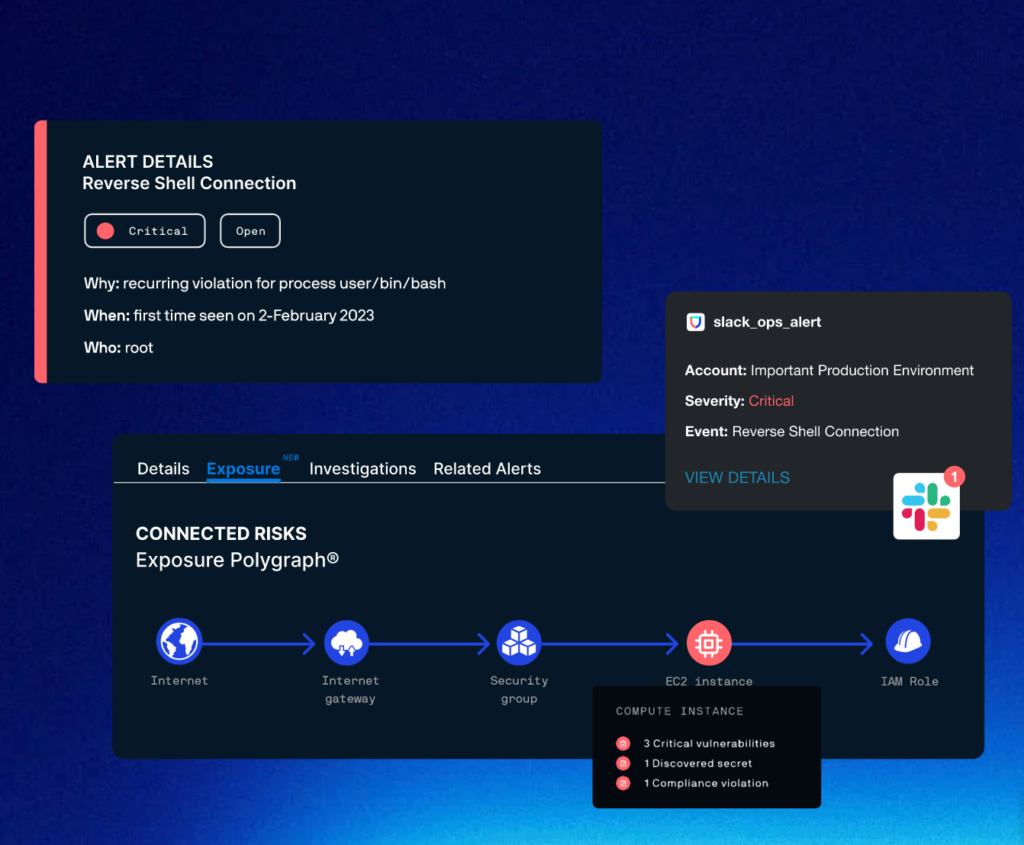
Price: Contact the company for a quote.
Main Features:
Best for: Mid-market organizations looking for a unified cloud solution to enhance visibility
Review: “Lacework as a tool has been really insightful as it has really brought about the transparency and visibility that we were looking for.”
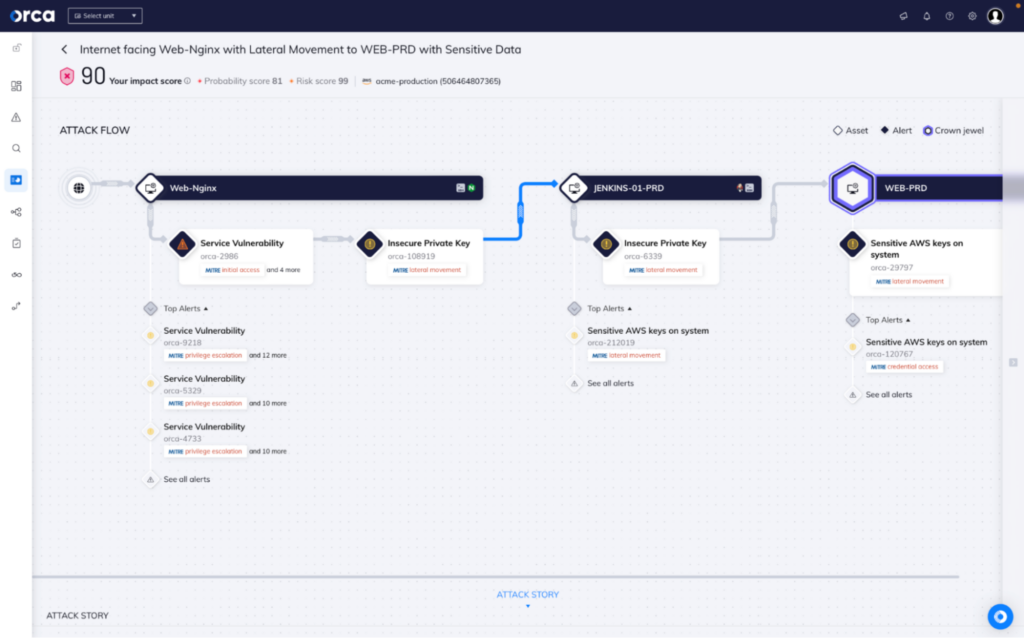
Price: Contact the company for a quote.
Main Features:
Best for: Businesses of all sizes looking to track vulnerabilities and security risks
Review: “Orca is an excellent platform for assessing the security posture of all your cloud accounts in a single interface.”
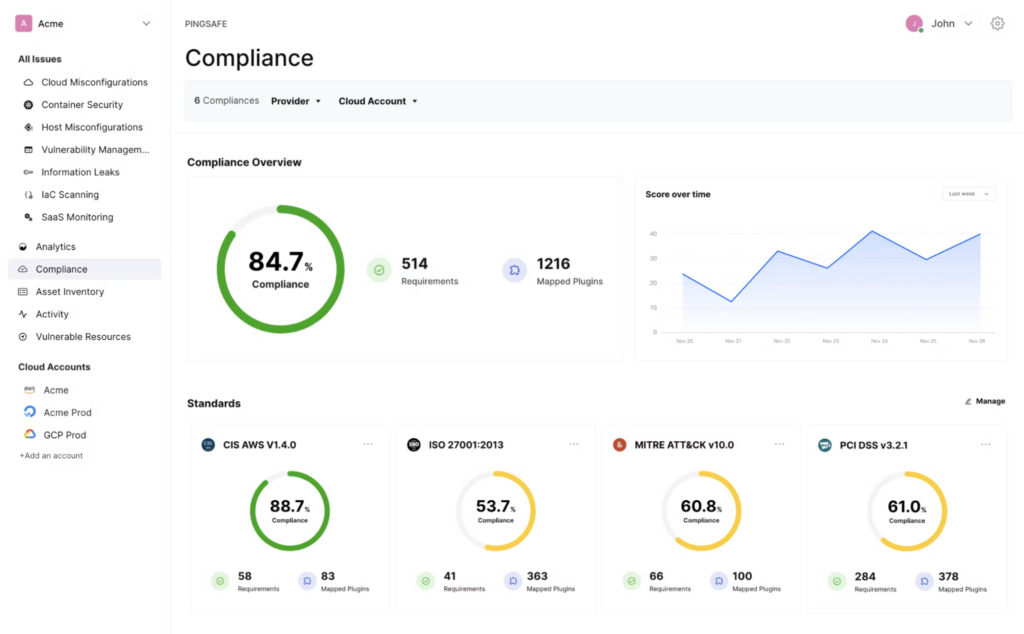
Price: Contact the company for a quote.
Main Features:
Best for: Mid-market organizations looking for a solution to supplement their security strategies
Review: “PingSafe helps us stay on top of potential misconfigurations in our cloud environment, giving our security team peace of mind.”
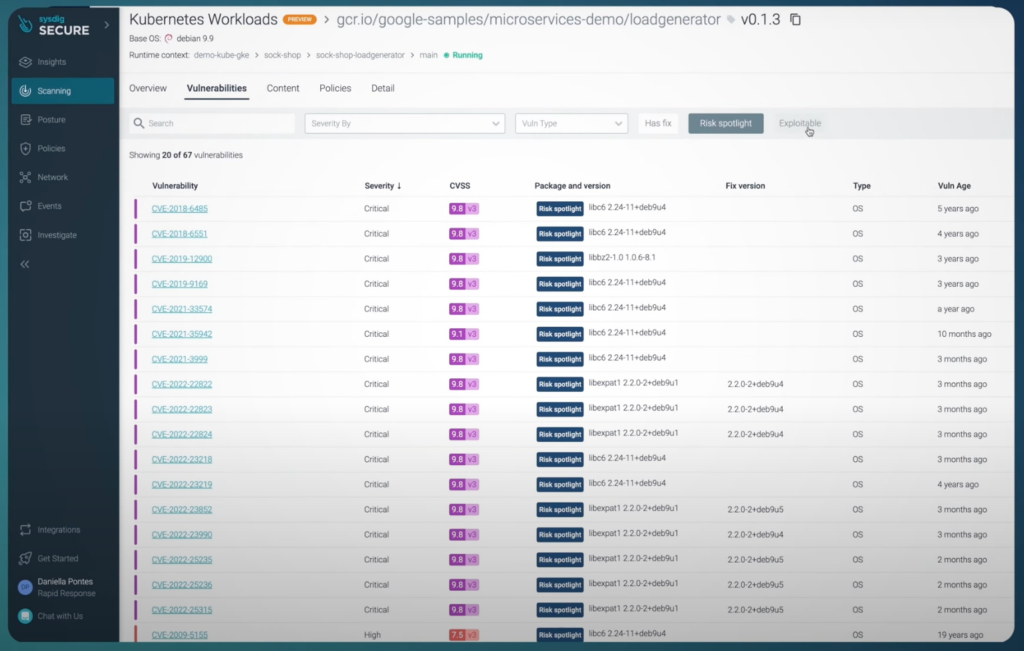
Price: Contact the company for a quote.
Main Features:
Best for: Enterprise-level organizations looking for a solution to help them monitor the security of their cloud assets
Review: “Sysdig is exceptional in runtime protection areas. From simple container and process monitoring until the point of the actual hardening.”
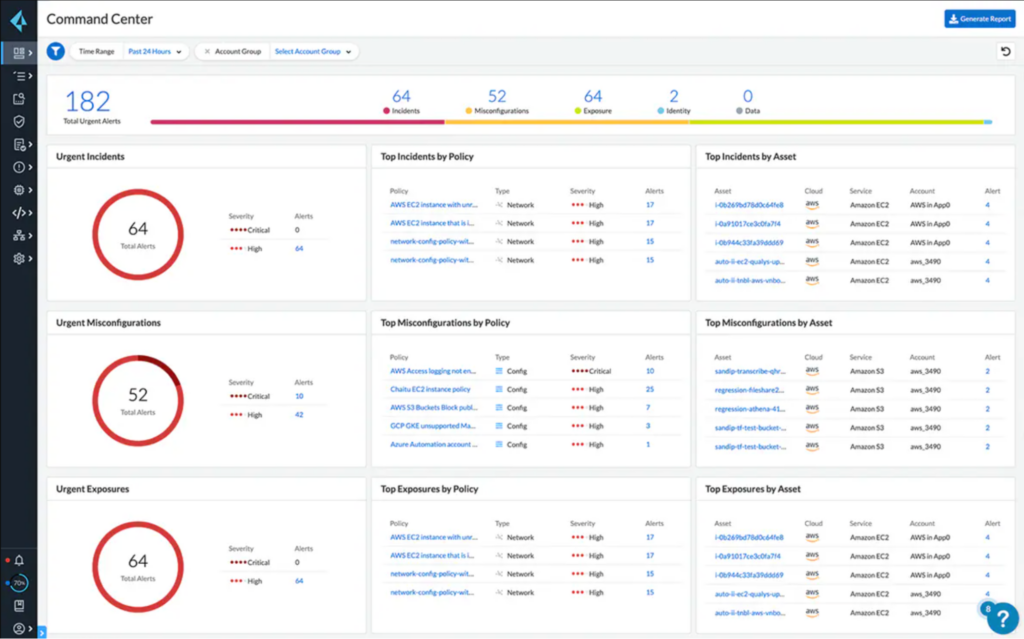
Price: Contact the company for a quote.
Main Features:
Best for: Enterprise-level organizations looking to enhance their cloud security
Review: “This is one of the best tools for security management, be it network or host security.”
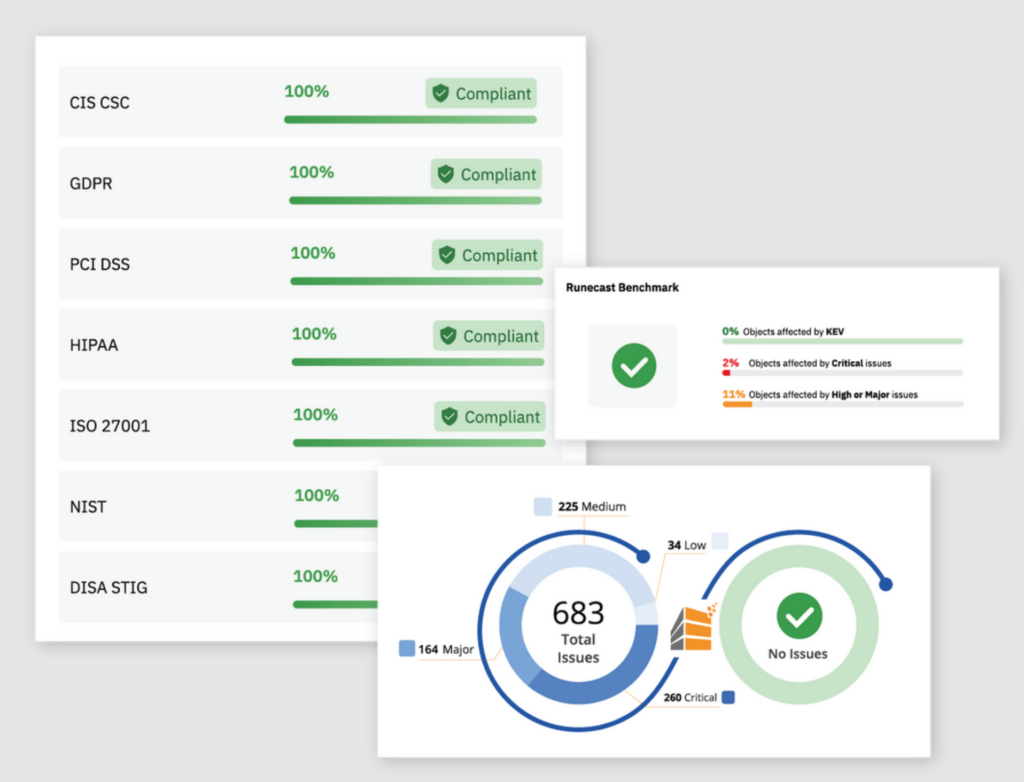
Price: Contact the company for a quote.
Main Features:
Best for: Mid-market to enterprise-level organizations looking to maintain compliance and best security practices
Review: “Runecast has a ton of security standards to help achieve easy audit ratification.”
Protecting cloud-native applications is crucial, and CNAPPs simplify that process. But no single solution fits all–when choosing a CNAPP, it’s essential to consider the capabilities you need to meet your organization’s unique requirements. Meanwhile, additional tools such as SpectralOps can help you cover your bases by providing comprehensive security for both traditional and cloud applications. Our developer-first solution combines AI and hundreds of detectors to protect code, assets, and infrastructure in real time, allowing you to avoid costly mistakes caused by security misconfigurations and exposed credentials. Schedule a free demo today.

Open source software is everywhere. From your server to your fitness band. And it’s only becoming more common as over 90% of developers acknowledge using open

It’s easy to think that our code is secure. Vulnerabilities or potential exploits are often the things we think about last. Most of the time, our

Experiencing a data breach is never pleasant. Just ask any of the hundreds of businesses that suffered a data breach in the past year, exposing billions